
Dark Web Profile: Akira Ransomware
Since its discovery in early 2023, Akira ransomware has evolved from a seemingly ordinary addition to the ransomware landscape to a significant threat affecting a wide range of businesses and critical infrastructure entities. This evolution, coupled with its unique aesthetic on its leak site and communications, has drawn attention to its operations.
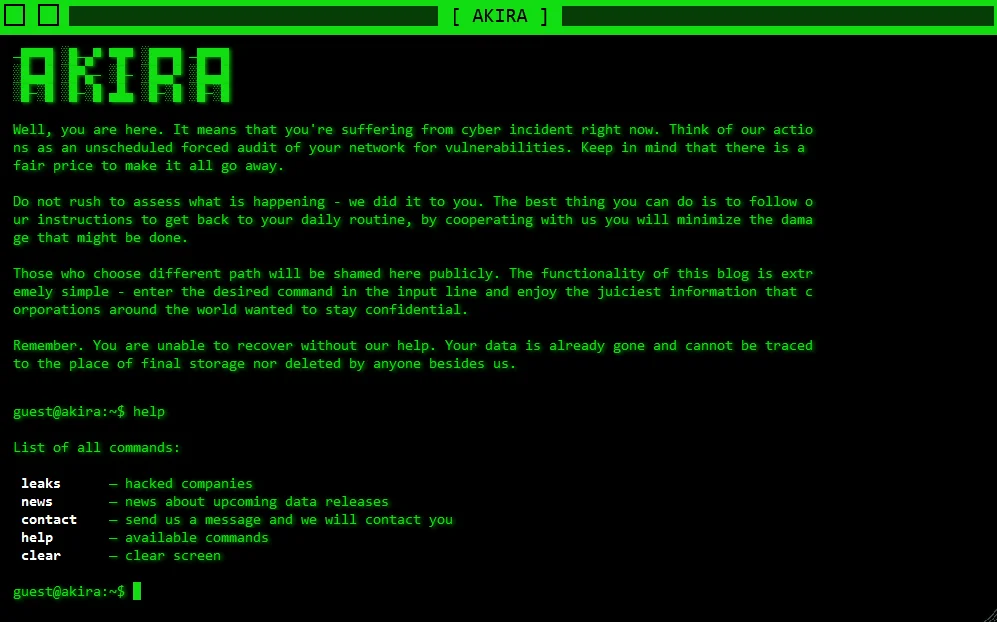
Akira’s data leak site, home page
As recently published CISA advisory claims, with over 250 organizations impacted and approximately $42 million (USD) in ransomware proceeds claimed as of January 1, 2024.
Who is Akira Ransomware
The ransom group employs a double extortion strategy, first exfiltrating data and then encrypting devices within the targeted network. Payment is then demanded not only for decrypting files but also for preventing the exposure of leaked data.
The ransomware’s name is believed to have its roots in a 1988 anime movie with a cyberpunk theme. In this film, Akira’s destruction of Neo-Tokyo is portrayed as a preventive measure against a malevolent force taking hold within the city.
This narrative parallels a common argument among ransomware operators who “claim” to perceive the world’s economic system as the source of evil. They often view themselves as modern-day Robin Hoods or Akiras, fighting against what they see as systemic injustices.

Akira (1998), the movie that probably inspired the ransomware group, popular culture is a widely common reference point among the threat actors especially since these kinds of cultural products grow in cyberspace -the internet. (Image: IMDb)
As suggested by CISA, Akira ransomware has impacted numerous businesses and critical infrastructure entities across North America, Europe, and Australia since March 2023. Initially focusing on Windows systems, the threat expanded in April 2023 to target VMware ESXi virtual machines with a Linux variant. As of January 1, 2024, the group has affected over 250 organizations and amassed approximately $42 million (USD) in ransomware proceeds.
Early versions of Akira ransomware, coded in C++, used a .akira extension for encrypted files. Starting in August 2023, some Akira attacks introduced Megazord, a Rust-based encryption tool using a .powerranges extension. The threat actors behind Akira have alternated between Megazord and Akira_v2 (identified by independent investigations) in their attacks.
Victimology
The Akira ransomware group frequently demands hefty ransoms, primarily targeting large enterprises across North America, Europe, and Australia. Typically, the malware spreads through targeted threat campaigns using phishing emails or exploiting software vulnerabilities, focusing on industries such as education, finance, manufacturing, and healthcare.
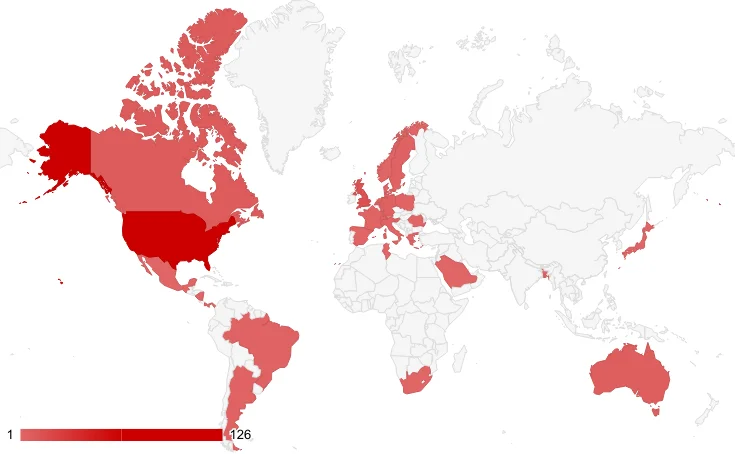
Target countries of Akira Ransomware in past year
The significant number of victims in the United States dominates the chart, extremely overshadowing other countries.
This targeted country list shows that the countries closely aligned with the United States, such as the European countries, account for most victims outside the US.
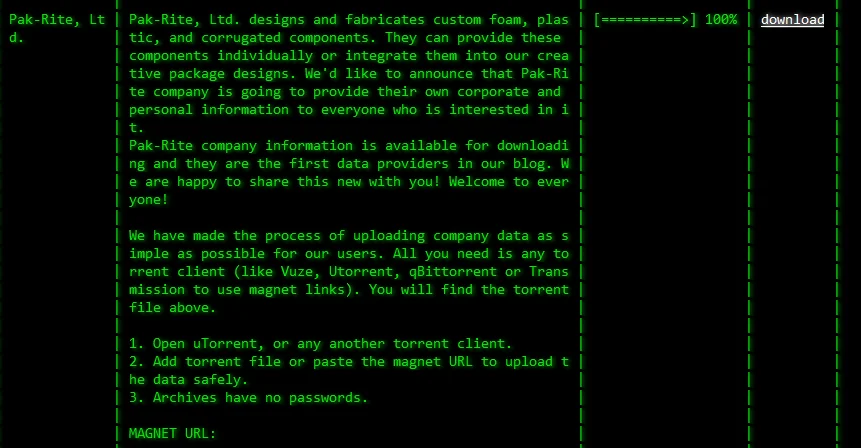
A victim listing of Akira Ransomware
In order to display the victims on the ransomware group’s homepage, which resembles a command line interface, guests must input the “-leaks” command. This command lists the victims in chronological order, starting from the first victim to the most recent.
The victims’ details are accompanied by a torrent magnet link to access the alleged files, along with information regarding the victim, the amount of leaked data, and the portion of data that has been made public.
Unfortunately, the design does not appear to contain any easter eggs
Again, the contact part is done from this interface. When the -contacts command is entered on the command line, the name and then the message are asked.
Modus Operandi
As specified in the CISA’s advisory:
Initial Access:
Akira threat actors primarily gain initial access to organizations through a Virtual Private Network (VPN) service lacking Multi-Factor Authentication (MFA), often exploiting known vulnerabilities in Cisco systems such as CVE-2020-3259 and CVE-2023-20269. Additional methods include Remote Desktop Protocol (RDP), spear phishing, and credential abuse.
Persistence and Discovery:
After gaining initial access, Akira actors establish persistence by creating new domain accounts and utilizing domain controllers. They leverage post-exploitation techniques like Kerberoasting to extract credentials and use credential scraping tools for privilege escalation. Network scanning tools aid in reconnaissance and identifying domain controllers.
Defense Evasion:
Akira actors may deploy multiple ransomware variants within the same attack, disable security software, and terminate antivirus-related processes to avoid detection.
Exfiltration and Impact:
Tools like FileZilla and WinSCP are used for data exfiltration, while AnyDesk and Ngrok establish command and control channels. Akira utilizes a double-extortion model, encrypts systems, and demands payment in Bitcoin. They threaten to publish data on the Tor network to pressure victims.
Encryption:
Akira employs a hybrid encryption scheme combining ChaCha20 and RSA algorithms, targeting specific file types and sizes. They delete volume shadow copies (VSS) and leave ransom notes to communicate with victims.
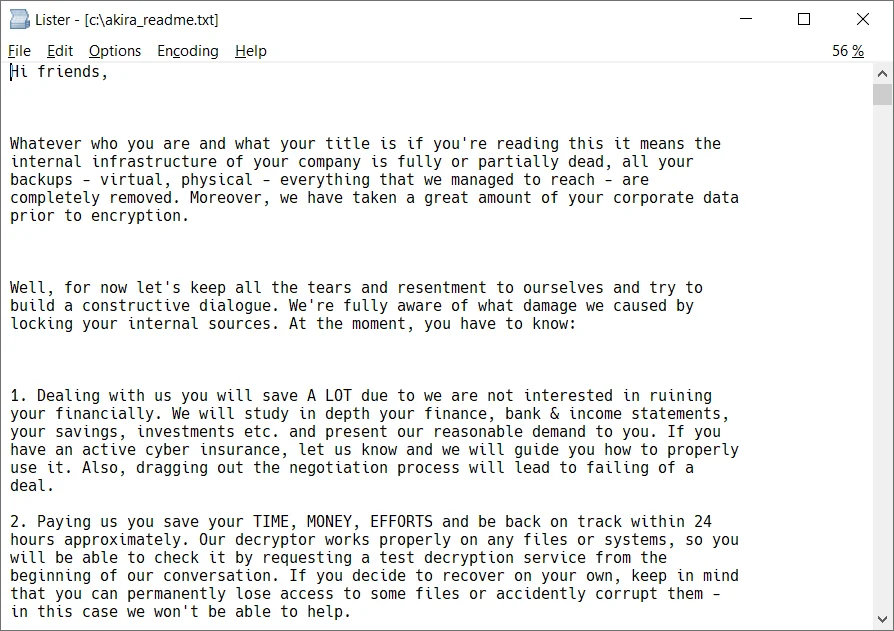
Akira Ransom Note (Avast Threat Labs)
Leveraged Tools:
Akira actors use various tools such as AdFind, Advanced IP Scanner, AnyDesk, Mimikatz, RClone, WinRAR, WinSCP, and PowerShell for reconnaissance, remote access, credential theft, exfiltration, and system manipulation.
This Modus Operandi highlights Akira’s sophisticated techniques from initial access to impact, showcasing their evasion tactics, encryption methods, and utilization of diverse tools for malicious activities. For the full details please visit CISA.
MITRE ATT&CK TTP Table
| Technique Title | ID | Use |
| Initial Access | ||
| Valid Accounts | T1078 | Akira threat actors obtain and abuse credentials of existing accounts as a means of gaining initial access. |
| Exploit Public Facing Application | T1190 | Akira threat actors exploit vulnerabilities in internet-facing systems to gain access to systems. |
| External Remote Services | T1133 | Akira threat actors have used remote access services, such as RDP/VPN connection to gain initial access. |
| Phishing: Spearphishing Attachment | T1566.001 | Akira threat actors use phishing emails with malicious attachments to gain access to networks. |
| Phishing: Spearphishing Link | T1566.002 | Akira threat actors use phishing emails with malicious links to gain access to networks. |
| Credential Access | ||
| OS Credential Dumping | T1003 | Akira threat actors use tools like Mimikatz and LaZagne to dump credentials. |
| OS Credential Dumping: LSASS Memory | T1003.001 | Akira threat actors attempt to access credential material stored in the process memory of the LSASS. |
| Discovery | ||
| System Network Configuration Discovery | T1016 | Akira threat actors use tools to scan systems and identify services running on remote hosts and local network infrastructure. |
| System Information Discovery | T1082 | Akira threat actors use tools like PCHunter64 to acquire detailed process and system information. |
| Domain Trust Discovery | T1482 | Akira threat actors use the net Windows command to enumerate domain information. |
| Process Discovery | T1057 | Akira threat actors use the Tasklist utility to obtain details on running processes via PowerShell. |
| Permission Groups Discovery: Local Groups | T1069.001 | Akira threat actors use the net localgroup /dom to find local system groups and permission settings. |
| Permission Groups Discovery: Domain Groups | T1069.002 | Akira threat actors use the net group /domain command to attempt to find domain level groups and permission settings. |
| Remote System Discovery | T1018 | Akira threat actors use nltest / dclist to amass a listing of other systems by IP address, hostname, or other logical identifiers on a network. |
| Persistence | ||
| Create Account: Domain Account | T1136.002 | Akira threat actors attempt to abuse the functions of domain controllers by creating new domain accounts to establish persistence. |
| Defense Evasion | ||
| Impair Defenses: Disable or Modify Tools | T1562.001 | Akira threat actors use BYOVD attacks to disable antivirus software. |
| Command and Control | ||
| Remote Access Software | T1219 | Akira threat actors use legitimate desktop support software like AnyDesk to obtain remote access to victim systems. |
| Proxy | T1090 | Akira threat actors utilized Ngrok to create a secure tunnel to servers that aided in exfiltration of data. |
| Collection | ||
| Archive Collected Data: Archive via Utility | T1560.001 | Akira threat actors use tools like WinRAR to compress files. |
| Exfiltration | ||
| Exfiltration Over Alternative Protocol | T1048 | Akira threat actors use file transfer tools like WinSCP to transfer data. |
| Transfer Data to Cloud Account | T1537 | Akira threat actors use tools like CloudZilla to exfiltrate data to a cloud account and connect to exfil servers they control. |
| Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002 | Akira threat actors leveraged RClone to sync files with cloud storage services to exfiltrate data. |
| Impact | ||
| Data Encrypted for Impact | T1486 | Akira threat actors encrypt data on target systems to interrupt availability to system and network resources. |
| Inhibit System Recovery | T1490 | Akira threat actors delete volume shadow copies on Windows systems. |
| Financial Theft | T1657 | Akira threat actors use a double-extortion model for financial gain. |
For the existing IoCs you may also visit SOCRadar Platform.
How Can SOCRadar Help?
SOCRadar’s robust defense strategy is specifically designed to combat the ransomware threat. Our proactive approach to threat monitoring and intelligence solutions is customized to bolster your organization’s security posture effectively. Through our platform, you can actively monitor and analyze threat actors like Akira, gaining in-depth insights into their strategies, targeted vulnerabilities, associations, and signs of compromise. This proactive methodology empowers you to anticipate and mitigate potential threats efficiently, protecting your critical assets.
SOCRadar, Attack Surface Management module with Ransomware Check function
In addition, our Attack Surface Management module, featuring the Ransomware Check function, provides continuous monitoring of all potential attack pathways. This ensures that you receive real-time notifications about any suspicious activities linked to ransomware. By staying ahead of these threats, you can promptly respond and strengthen your cybersecurity defenses, reducing the risk posed by Akira ransomware and other emerging threats.




































