Why Ransomware Groups Switch to Rust Programming Language?
By SOCRadar Research
The Rust programming language, which was released in 2015, became popular in a short time. Continuing to increase in popularity since the year it was released, Rust managed to become the most popular programming language on Stack Overflow, with 86% positive votes. In addition to the interest of the developers, businesses continue to post Rust Developer hirings and increase the salaries as well.
But this new favorite of developers has also caught the attention of threat actors. In 2022, we saw that much malware, especially ransomware, was written in Rust or transitioned to Rust.
Ransomware written in Rust, which first appeared with BlackCat in late 2021, affected more than 200 organizations just in 2022. Around this time, the Hive Ransomware group became the second group to follow this trend by transitioning ransomware strains from Golang to Rust. After that, Rust ransomware strains of Luna, RansomExx, and Agenda were detected in the wild, respectively.
Why is Rust Preferred?
Software languages such as Rust, which can be considered relatively newer, are designed to replace old ones. In this regard, they have some advantages:
- Memory Management: Rust is trying to provide better memory management via its unique storage in memory and compile time. Rust claims to be faster and more efficient than C and C++, and this seems to be accepted by many developers today. But these beneficial aspects are also of interest to threat actors, as malware tries to stay operational and efficient. Especially in ransomware, where memory management is critical, it is necessary to remain functional and not experience a crash to receive the ransom payment. It also has other prominent advantages when used in malware development.
- Evasion: New languages, such as Rust, are relatively fast and can evade the static analysis of many malware detection systems. Many security products have been designed for years based on the signatures of well-known and widely used languages, so signatures of a different language can make static analysis much more difficult. These situations can enable it to evade signature-based structures at the delivery stage and facilitate such maneuvers again within the system. After the malware is delivered, it uses evasive movements not to be detected by the security systems. Rust’s speed in this regard increases ransomware’s chance to move into the exploitation stage without being detected by many systems and security staff.
- Hard to Reverse Engineer: Rust stands out in ransomware because the reverse engineering required to extract the decryptor is more complicated. Rust compiler is relatively more complex and turns into machine-readable code, creating a more challenging task for many malware analysts. Decryptor generation becomes much more complex when reverse engineering becomes difficult, and the victim’s only option may be to pay the ransom. The inability to examine the attacker’s tools makes it too hard to take the necessary measures.
When Was it Began?
One of the first malware detected in the wild was a Linux-running trojan detected by Doctor Web researchers in 2016. A backdoor executed the commands it received over the IRC (Internet Relay Chat) protocol. On the system, it infected this backdoor trojan was listening to the specified channel via IRC and waiting for orders from its C2.
In 2017 a group named TeleBots was making disruptive attacks on Ukrainian companies with KillDisk malware in 2016. The group, which did not demand any ransom initially, later started to demand very high sums. However, the amount of ransom demanded showed that the group was not interested in money but only for harmful purposes. Security researchers observed that the TeleBots group wrote one of the backdoors they used during the infiltration process with Rust.

After this point, Rust-written versions of various malware have been encountered to this day, especially to evade signature-based detection. However, the situation started to get serious when ransomware groups started using Rust in late 2021.
Which Ransomware Groups/Strains are Using Rust?
Ransomware written in Rust, which we encountered with the BlackCat group that emerged at the end of 2021, continued to appear throughout 2022. As reported in a report by the FBI on BlackCat, the group’s high success rate was their use of a Ransomware strain written in Rust.
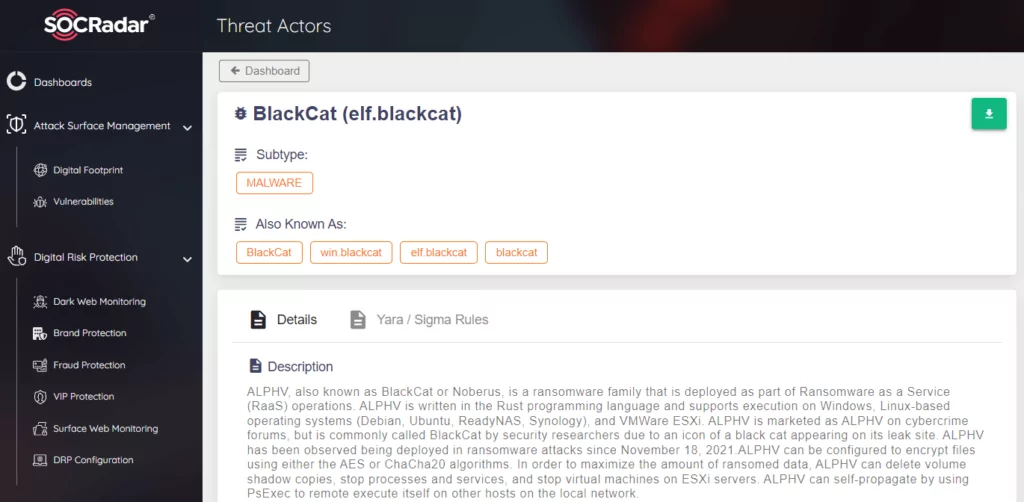
BlackCat
Also known as ALPHV, which had over 200 victim announcements recorded by SOCRadar since its emergence, it is the first ransomware written in Rust and has the most attack count. BlackCat is working with the RaaS model, but they have differentiated their business models like their variants by giving payouts up to 90% to be competitive in this cybercriminal space. For a detailed analysis of the group and its TTP, IoCs, see this article.
Hive
Hive Ransomware works as RaaS and has been active since 2021. They appeared as the second strain that transitioned to Rust and announced nearly 200 victims on their leak sites in 2022.
However, US and international law enforcement authorities have taken action against the Hive ransomware group, including the seizure of at least two leak sites in January 2023. Check out our recent article for detailed variant analysis, TTP, and IoCs on Hive Ransomware group and RaaS services.

Luna
Kaspersky researchers discovered Luna Ransomware. It was advertised on the dark web for Russian-speaking affiliates. This malware, which can affect all Windows ESXi and Linux systems, was recorded in July 2022 as one of the significant strains written with Rust. Another feature that makes Luna different is that it uses x25519 and AES encryptions together, which makes reverse engineering even more difficult.
RansomExx
This strain, called RansomwareExx2 and belonging to the RansomwareExx group, was discovered in the last months of 2022. This string, which none of the VirusTotal results saw as malicious for two weeks after its first detection, once again showed how dangerous the strains written in a different language are.
Agenda
The Agenda or Qilin group was the group researchers observed to transition to Rust in the last month of 2022. Previously, there were strains they developed on Go and customized for each victim. This group, which works with RaaS, made ransomware attacks on various countries and sectors. The result that can be drawn from the transition from Go to Rust is that it has a lower detection rate than Go variants, and we can say that it is more difficult to reverse engineer.
What Organizations Should Do?
Ransomware attacks increased again in 2022, revealing how critical they are. Although the rate of attack growth has slowed down partially, it has increased in volume. Again in 2023, both the volume and the rate of increase can be expected to grow.
Many “as-a-Service” cybercrime models have been one of the rising concepts of this year. In particular, threat groups that have switched to the Ransomware-as-a-Service model can increase their attack volume to enormous sizes and target many different industries and companies of various sizes. In this context, the threat actors, who keep distributing their crime tools as a service, try to prevent their malware from being detected as much as possible or make an effort to make it challenging to reverse.
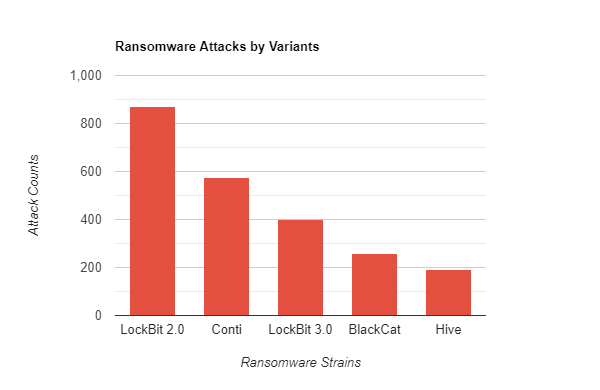
Ransomware strains written in Rust ranked 3rd and 4th, following the two most popular strains in 2022. Considering the current success of these relatively new strains, we can expect them to rank higher next year.
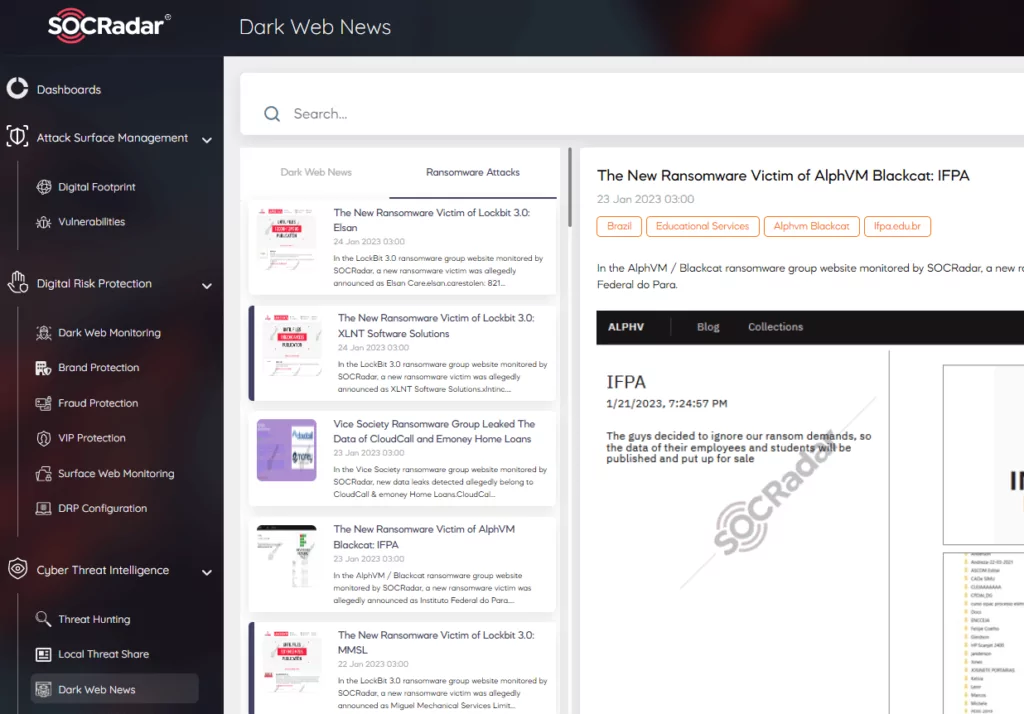
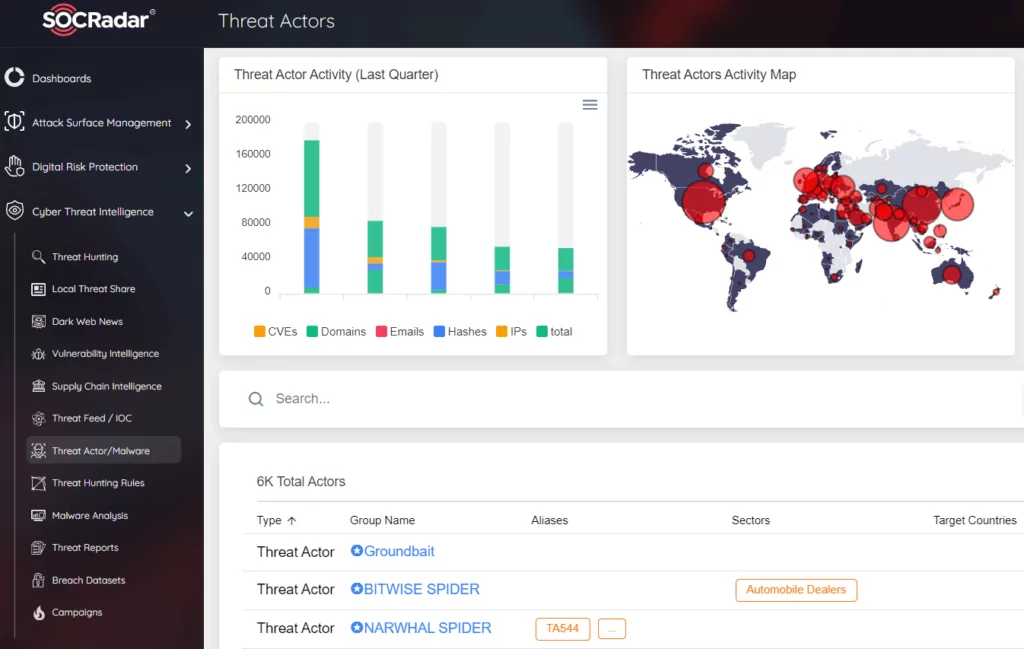
Traditional security products may not always be sufficient against these strains, which are cross-platform and are much more challenging to detect. One of the most fundamental benefits of Cyber Threat Intelligence is to be aware of such changes in advance and develop a proactive understanding of defense against the changing methods of attackers. You can use SOCRadar’s Dark Web News service to follow the most up-to-date threat feeds and get detailed analysis, TTPs, and IoCs about these groups from the Threat Actors tab.