
Dark Web Profile: Termite Ransomware
The dark web, a hidden part of the internet, remains a source of growing cyber threats, with ransomware being one of the most prominent. Among these threats, Termite Ransomware has recently stood out due to its focused attacks and distinctive strategies. First identified in late 2024, Termite Ransomware is believed to be connected to Babuk, a ransomware group whose leaked source code in 2021 enabled the creation of many new and powerful variants. While Babuk’s influence cannot be ignored, Termite has taken a different approach, concentrating on exploiting specific system vulnerabilities.

Threat actor card of Termite Ransomware
Compared to earlier ransomware, Termite has gained attention much faster. It has been discussed widely on dark web forums, with researchers suggesting it might have links to well-known groups like Cl0p. If these connections are verified, they would further emphasize Termite’s significant position in the changing ransomware landscape. While Babuk’s history casts a long shadow, Termite’s presence signals how ransomware threats continue to adapt, presenting new challenges to cybersecurity efforts.
Who is Termite Ransomware
Termite Ransomware is a relatively new threat actor that specializes in data theft, extortion, and encryption. Emerging in late 2024, the group has already been linked to multiple high-profile cyberattacks that have disrupted operations across various industries.
Termite’s approach involves encrypting files and leaving behind ransom notes that guide victims to a Tor-based website for further communication. This website includes forms where victims are required to provide specific details about their organization, often including a support token. It is believed that Termite uses a modified version of the Babuk ransomware, adapting its code to suit its own operations.
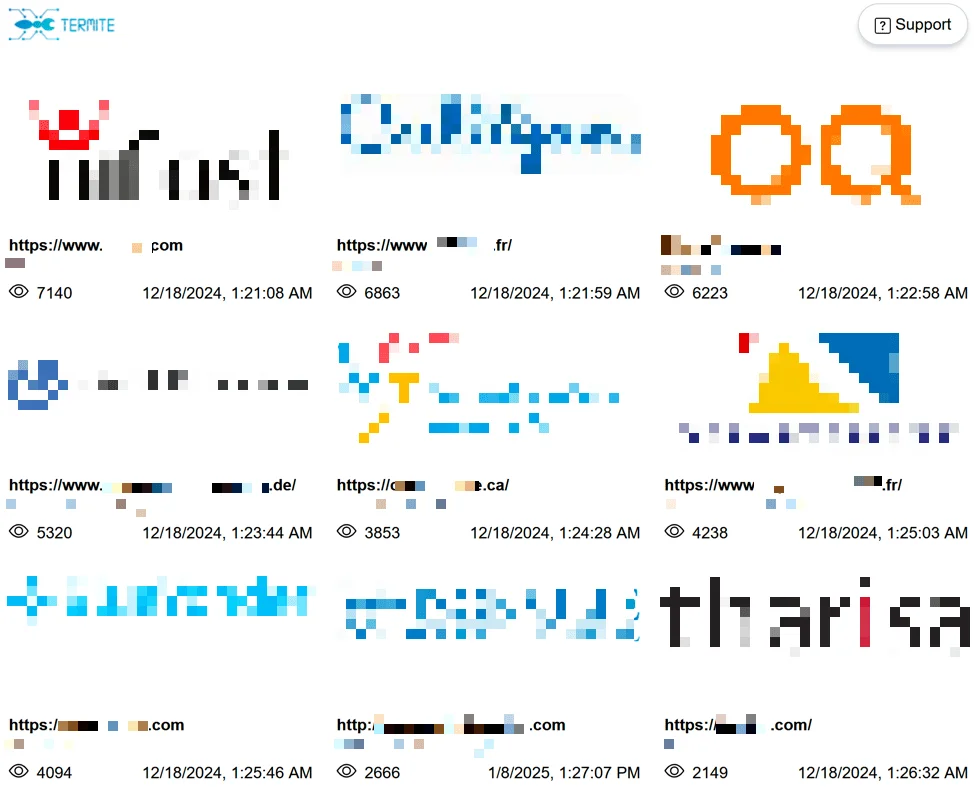
Termite Ransomware data leak site
One of the most notable incidents attributed to Termite was an attack on Blue Yonder, a supply chain vendor. This breach caused operational disruptions for several prominent companies and led to the theft of sensitive data. The group’s actions during this attack have cemented its reputation as an emerging and capable ransomware actor.
Although Termite’s full operations and affiliations remain under investigation, its rapid growth and increasing activity suggest it is leveraging advanced tactics. Researchers have speculated that Termite might have links to other prominent ransomware groups, further demonstrating its ability to adapt and expand its reach.
To counter such sophisticated threats, organizations need tools that go beyond reactive measures. SOCRadar Operational Intelligence module steps in here by offering advanced profiling tools that provide deep insights into the operations of extortion groups like Termite. These tools allow organizations to monitor and analyze their tactics, techniques, and procedures (TTPs) effectively. By studying their attack patterns and typical targets, organizations can proactively strengthen their cybersecurity defenses and develop countermeasures tailored to the ever-evolving ransomware landscape.
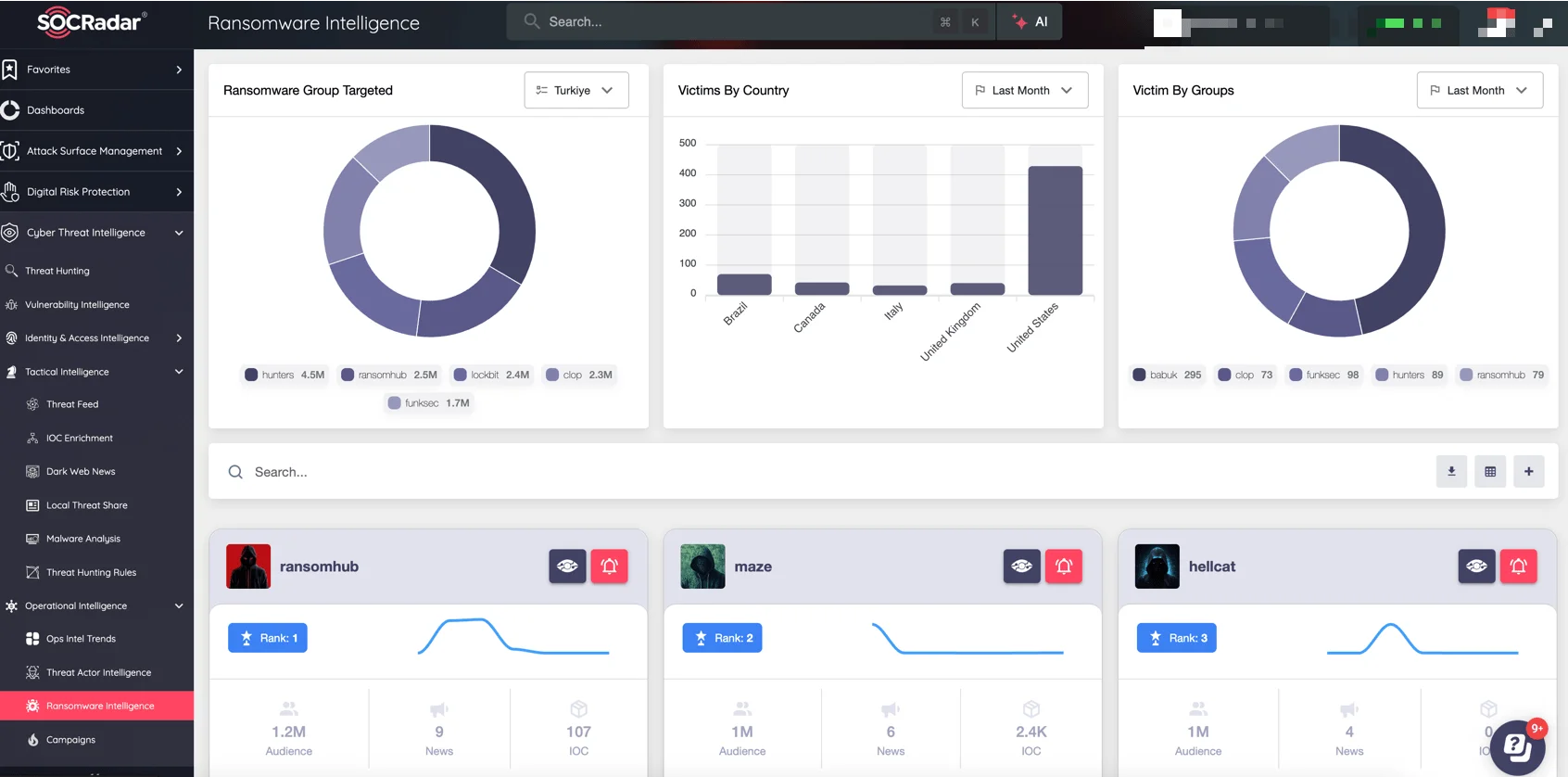
SOCRadar Ransomware Intelligence
How Does Termite Ransomware Operate? – The Modus Operandi
Termite ransomware’s operations demonstrate a blend of traditional ransomware techniques and modern strategies aimed at maximizing disruption and financial gain. Similar to other ransomware groups, Termite focuses on encrypting data and exfiltrating sensitive information to strengthen its extortion efforts.
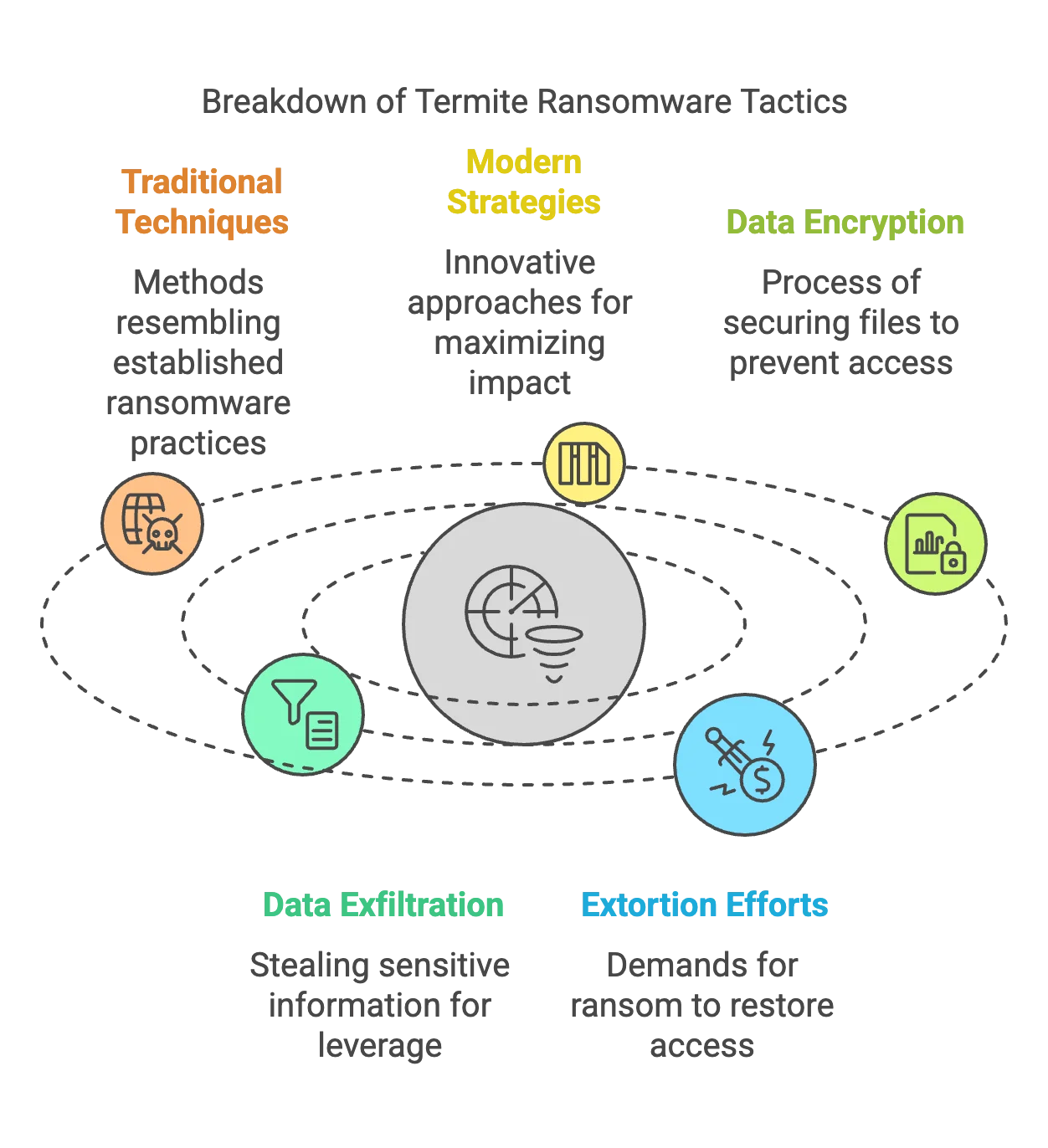
Breakdown of Termite Ransomware Tactics
Initial Access and Deployment
Researchers suggest that Termite may gain initial access to victim networks through common methods such as phishing campaigns, exploitation of software vulnerabilities, or the use of stolen credentials. Once inside, the ransomware establishes persistence by deploying tools to maintain control over the system.
File Encryption and System Manipulation
Upon execution, Termite ransomware prioritizes its encryption process to ensure maximum impact. The malware uses various APIs to disable running services and processes that could interfere with the attack. For example, it targets backup and database-related processes to prevent recovery options.
The ransomware deletes shadow copies and clears the Recycle Bin to remove any chance of restoring encrypted files. It also excludes certain system-critical files and folders from encryption to avoid disrupting basic operations, ensuring the victim can still interact with the ransom note.
Network Propagation
Termite demonstrates the capability to spread across a network, searching for shared resources and connected devices. By identifying and encrypting files on network drives and shares, the group amplifies the impact of its attack. This ability allows Termite to target not just individual machines but entire organizational infrastructures.
Extortion and Communication
After encrypting files, Termite leaves behind a ransom note directing victims to a Tor-based communication portal. The portal includes forms for victims to provide information about their situation, including organization details and unique identifiers provided in the ransom note. The group often demands payment in cryptocurrency and threatens to release stolen data publicly if the ransom is not paid.
Advanced Tactics and Targeting
Termite’s tactics reflect its evolution from earlier ransomware strains like Babuk. The group’s technical sophistication and strategic targeting indicate a deeper understanding of its victims’ environments. Reports suggest that Termite actively exploits vulnerabilities in widely used software, further enhancing its reach and impact. For example, the group has been linked to exploit activity involving zero-day vulnerabilities in file transfer software, which has enabled attacks on high-profile organizations.
By combining these tactics, Termite has rapidly established itself as a significant ransomware threat, forcing organizations to reevaluate their defenses and response strategies. To further mitigate these risks, SOCRadar’s Attack Surface Management module helps organizations identify and monitor all digital assets exposed to potential exploitation. By continuously tracking vulnerabilities, open ports, and weak points in your network, SOCRadar ensures that your attack surface is minimized and protected from unauthorized access.
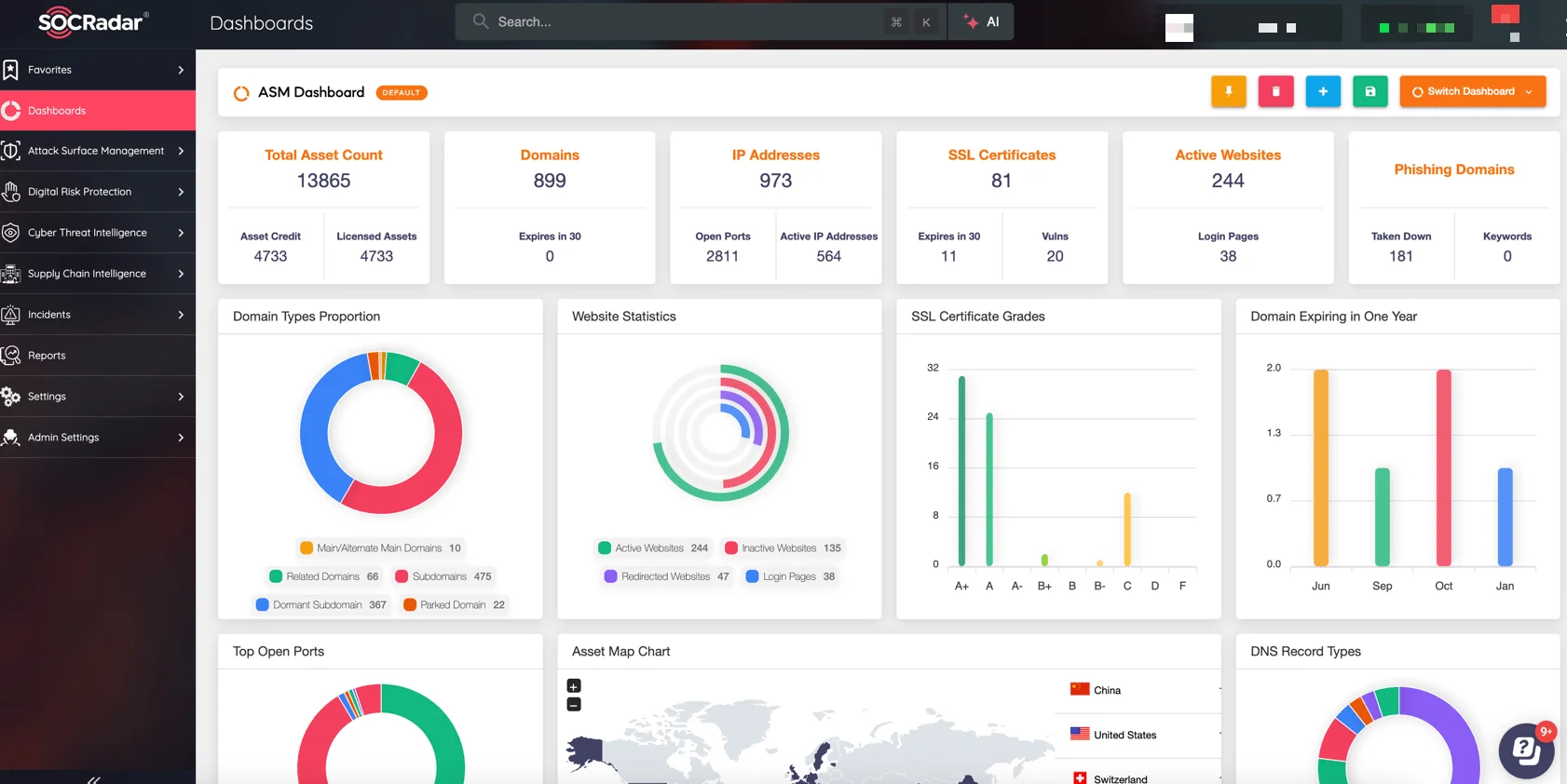
SOCRadar Attack Surface Management Dashboard
Termite Ransomware’s Victimology
Termite ransomware has quickly established a global presence, targeting organizations in the United States, Canada, France, Germany, Oman, and Cyprus. Its victims span various industries, reflecting the group’s ability to adapt its strategies to different environments and sectors.
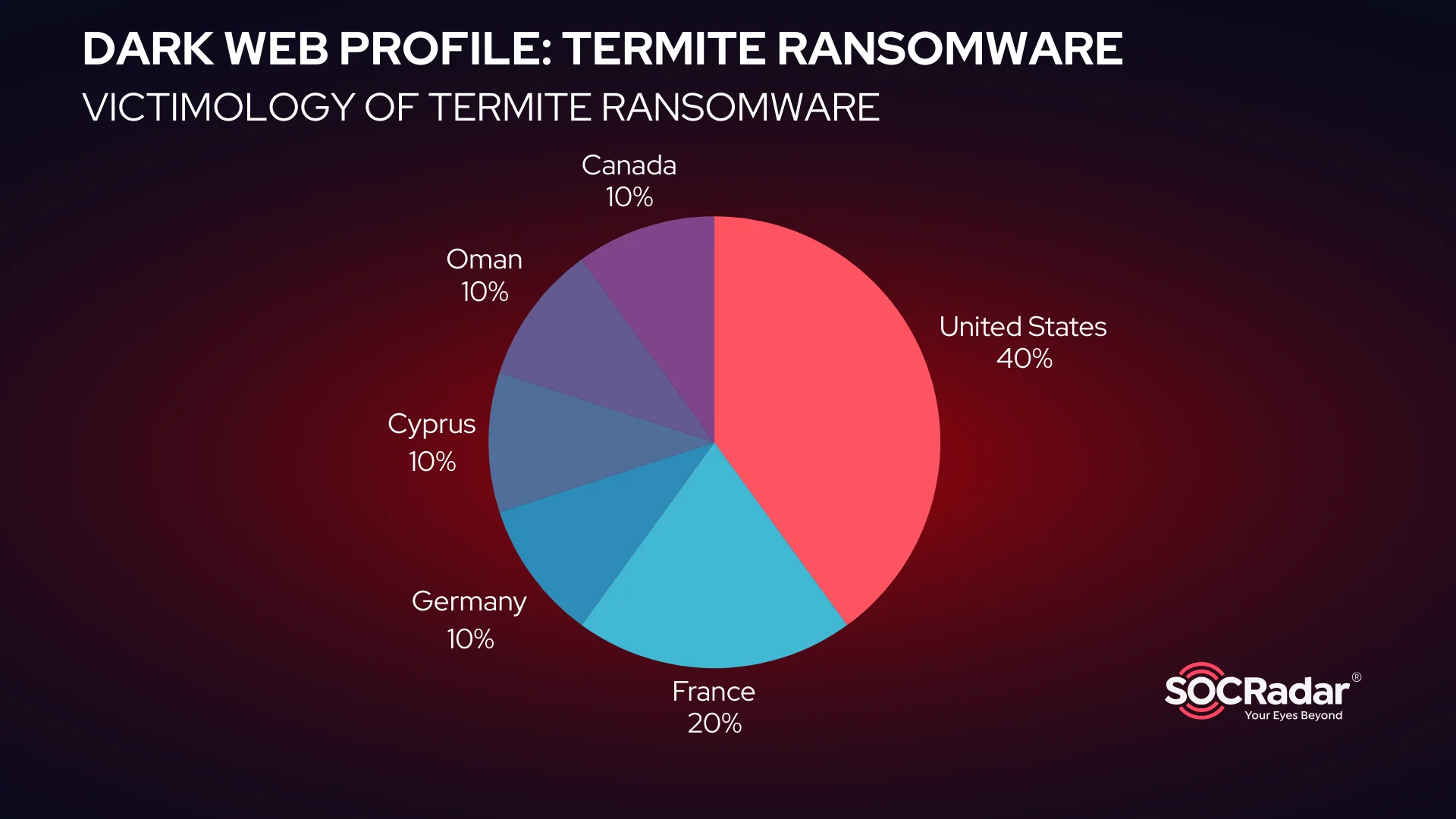
Termite Ransomware’s Victimology
The attack that brought Termite to prominence occurred in November 2024, when it targeted Blue Yonder, a major provider of supply chain management solutions. This high-profile incident disrupted operations for several major companies, disrupting operations across multiple regions, and demonstrated the significant risks posed by ransomware attacks on third-party service providers. Termite claimed responsibility for the attack on its dark web leak site, alleging that it had exfiltrated 680GB of sensitive data, including internal documents and database files.
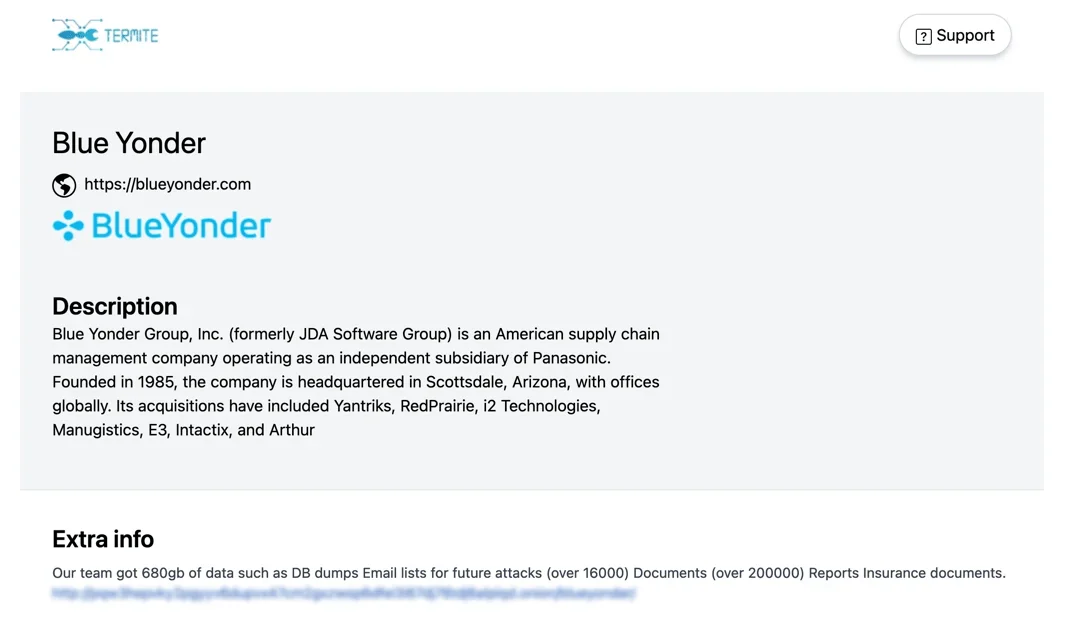
Blue Yonder was listed as a victim on Termite Ransomware’s data leak site
Interestingly, Cl0p, another notorious ransomware group, also added Blue Yonder to its list of victims, fueling speculation about potential connections or shared tactics between the two groups. Both groups’ involvement highlights the evolving complexity of ransomware operations, where multiple actors may exploit the same vulnerabilities or target similar organizations.
In addition to Blue Yonder, the exploitation of Cleo software vulnerabilities (CVE-2024-50623 and CVE-2024-55956) has drawn attention to shared tactics between ransomware groups. While Cl0p openly claimed the use of Cleo flaws for data theft, researchers have suggested that Termite may also be leveraging similar methods. These vulnerabilities in Cleo’s file transfer products allowed attackers to execute remote code and steal sensitive data from affected organizations, further complicating the cyber threat landscape.
The incident underscored the group’s use of double extortion tactics, combining encryption with threats to leak stolen data publicly. This approach not only increased pressure on Blue Yonder but also highlighted the interdependencies within modern supply chains. The attack revealed how a single breach could cascade across multiple organizations, disrupting operations and exposing critical vulnerabilities. Organizations are now left with pressing questions about the adequacy of their defenses against such sophisticated ransomware campaigns.
Blue Yonder later issued a critical statement addressing the claims by Cl0p regarding the Cleo software vulnerability. On Christmas Eve, Blue Yonder emphasized that there was no connection between the Cleo flaw and the November 2024 breach, which had already been attributed to Termite ransomware. This clarification underscored that the earlier disruption impacting services like Starbucks and BIC was unrelated to Cleo exploits, helping differentiate the incidents as separate attacks. Blue Yonder reassured its customers that ongoing investigations would provide further updates as needed.
Mitigation and Protection
- Regular Patch Management: Ensure all software and systems are updated with the latest security patches. Address known vulnerabilities, such as those in Cleo file transfer products, by applying vendor-recommended fixes promptly.
- Network Segmentation: Limit the spread of ransomware within infrastructure by separating critical systems from less sensitive ones.
- Backup and Recovery Plans: Maintain regular offline backups of critical data and test recovery processes to ensure data can be restored quickly after an attack.
- Email Security and Awareness: Enhance email filtering to block phishing attempts and conduct regular training to help employees recognize malicious emails.
- Advanced Threat Detection: Deploy Endpoint Detection and Response (EDR) solutions to identify and mitigate suspicious activity. Monitor for Indicators of Compromise (IOCs) related to Termite ransomware.
- Access Control: Enforce strict access controls and apply least privilege principles. Limit administrative privileges to reduce unauthorized access to critical systems.
- Incident Response Plan: Develop and regularly update a response plan, defining roles, communication strategies, and steps for containment and recovery.
By implementing these measures, organizations can strengthen their defenses against ransomware threats like Termite and minimize the potential impact of an attack. Proactive monitoring and collaboration with cybersecurity experts are crucial to staying ahead of evolving threats.
How Can SOCRadar Help?
SOCRadar offers a comprehensive suite of tools designed to help organizations mitigate the risks posed by ransomware groups like Termite. With its advanced threat intelligence platform, SOCRadar provides critical insights and real-time monitoring capabilities to identify, assess, and respond to cyber threats, including those related to ransomware and data breaches. Here’s how SOCRadar can help protect your organization:

Extended Threat Intelligence (XTI) by SOCRadar
- Dark Web Monitoring: SOCRadar’s Dark Web Monitoring service continuously scans underground forums and marketplaces where ransomware groups like Termite operate. By identifying any leaks of sensitive data or mentions of your organization, SOCRadar helps you stay ahead of potential threats. This early warning system allows you to take swift action to secure your data and prevent it from being sold or used against your organization.
- Real-Time Threat Intelligence: With SOCRadar’s real-time threat intelligence, you gain immediate visibility into emerging threats and tactics used by ransomware groups. This includes identifying Initial Access Broker (IAB) activity and other threat actor movements within the cybercrime ecosystem. By understanding these dynamics, your security team can implement targeted defense strategies to counteract ransomware attempts.
- Comprehensive Attack Surface Management: SOCRadar’s Attack Surface Management module helps you identify and monitor all digital assets exposed to potential exploitation. By continuously tracking vulnerabilities, open ports, and weak points in your network, SOCRadar ensures that your attack surface is minimized and protected from unauthorized access.
- Ransomware and Data Leak Monitoring: SOCRadar tracks data-leak sites and other ransomware-related platforms where groups like Termite may post stolen data. If your organization’s data is involved in an extortion attack, SOCRadar’s monitoring tools will alert you immediately, allowing you to respond quickly to prevent further exposure and mitigate the risk of extortion.
- Threat Actor Profiling: SOCRadar’s profiling tools allow you to monitor and analyze the tactics, techniques, and procedures (TTPs) of ransomware groups like Termite. By understanding their attack patterns and targets, you can proactively strengthen your defenses and develop countermeasures that are specifically tailored to the threat landscape posed by these groups.
- Customizable Alerts and Notifications: SOCRadar allows you to set up customized alerts for any suspicious activity, including potential ransomware threats. Whether it’s detecting signs of data exfiltration or identifying attempts to purchase access via IABs, SOCRadar ensures that your team is always in the loop with actionable intelligence.
- Vulnerability Management: SOCRadar’s Vulnerability Management capabilities help you identify weaknesses in your systems and take corrective actions before they can be exploited by ransomware groups. By continuously monitoring for vulnerabilities and applying timely patches, you reduce the risk of unauthorized access and data exfiltration.
By leveraging SOCRadar’s advanced capabilities, your organization can gain a significant advantage in defending against ransomware groups like Termite. Through continuous monitoring, threat intelligence, and proactive defense strategies, SOCRadar ensures that your organization stays one step ahead of cybercriminals.
What are Termite’s TTPs?
Understanding Termite ransomware’s tactics, techniques, and procedures (TTPs) through the MITRE ATT&CK framework provides a detailed view of how this threat actor operates. The table below highlights key techniques Termite employs during its attacks, offering valuable insights for cybersecurity teams to strengthen defenses and detect malicious activity effectively.
| Tactic | Technique ID | Technique Name |
| Execution | T1204.002 | User Execution |
| Defense Evasion | T1070.004 | Indicator Removal on Host |
| Discovery | T1083 | File and Directory Discovery |
| Lateral Movement | T1021 | Remote Services |
| Privilege Escalation | T1078 | Valid Accounts |
| Discovery | T1135 | Network Share Discovery |
| Command and Control | T1105 | Ingress Tool Transfer |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1490 | Inhibit System Recovery |





































