Dark Web Profile: UserSec
UserSec, a pro-Russian hacktivist group, first gained attention in early 2023. The group actively targets Western governments, organizations, and critical infrastructure, particularly those affiliated with NATO and supporters of Ukraine. The group operates primarily through Telegram, where it coordinates attacks and recruits hackers to join its efforts.
Who is UserSec?
UserSec is a pro-Russian cyber group known for politically motivated attacks against NATO countries and organizations that support Ukraine. The group has positioned itself as a major player in the cyber war, using Telegram as a recruitment and communication platform. Despite no confirmed ties to the Russian government, UserSec’s objectives align with Russia’s geopolitical interests, particularly in destabilizing Western nations and supporting pro-Russian narratives.

UserSec’s Telegram logo
Their public persona has been amplified through their “High Society,” a recruitment campaign launched in 2024, which seeks to attract cybercriminals and other groups sympathetic to their cause. This initiative aims to consolidate various hacktivist efforts under a unified banner and bolster UserSec’s operational capacity.
A recent recruitment campaign
UserSec’s motivations are deeply rooted in pro-Russian ideology, particularly in opposing Western involvement in the Ukraine conflict. Their campaigns align with Russian state narratives, often aiming to weaken NATO members and support Russia’s geopolitical agenda. The group has also sought to gain notoriety within underground hacker communities, using publicized data leaks and defacement campaigns as methods to boost its profile.
UserSec is less focused on financial gain than on ideological objectives. However, their recruitment efforts and campaigns suggest a willingness to collaborate with other hacktivist groups and even organized cybercriminals. Their involvement in data leaks could lead to the sale of sensitive information or DDoS-for-hire services, although this has not been the primary focus .
What are Their Tactics?
UserSec’s tactics reflect a combination of disruptive and destructive methodologies, often employed to achieve effiective visibility and disruption like many other pro-Russian groups. The group uses:
Distributed Denial-of-Service (DDoS) Attacks: UserSec has been involved in a series of DDoS attacks aimed at government and military infrastructure in NATO countries. These attacks, often well-coordinated, seek to disrupt the services of the targeted entities.
Data Breaches and Leaks: Another primary tactic involves breaching government databases to extract sensitive information. This data is often used for public exposure to embarrass governments or intimidate individuals and organizations.
Access and Exploitation: The group may possibly use spear-phishing campaigns to gain access to email accounts and systems, enabling the exfiltration of sensitive information. However more than phishing they tend to use Brute-Forcing or Default Credentials for access.
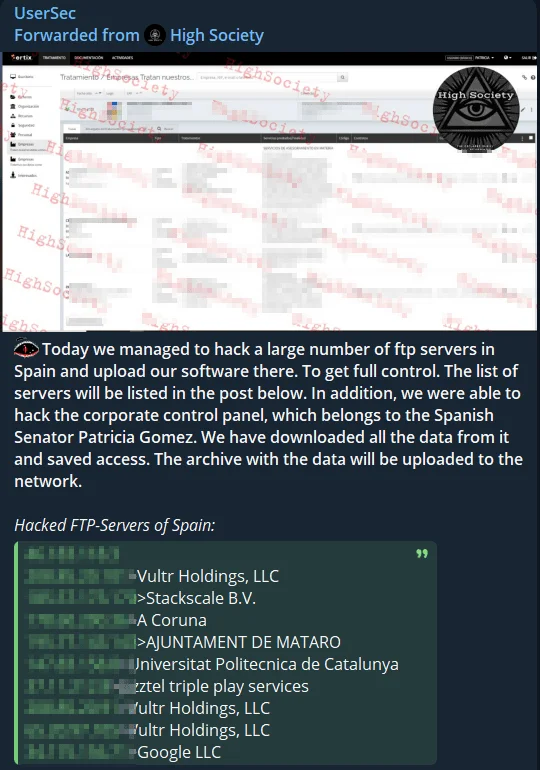
Alleged hack of FTP servers in Spain
Website Defacement: A less frequent but symbolic tactic where UserSec defaces websites of key targets to display pro-Russian or anti-Western messages.
What are Their Targets?
UserSec’s primary targets are government agencies, military and defense contractors, and critical infrastructure, especially in NATO-member countries. The group has consistently targeted sectors that hold strategic importance to Western nations, including:
Government Institutions: Frequent targets include ministries, military branches, and agencies associated with national security.
Military and Defense: UserSec has repeatedly aimed at military infrastructure in the United States and other NATO countries, attempting to disrupt defense-related operations.
Energy and Telecommunications: The energy sector has also been a prominent target, with attacks focused on disrupting utilities in Eastern Europe. Telecommunications infrastructure in the UK and Germany has faced frequent DDoS attacks .
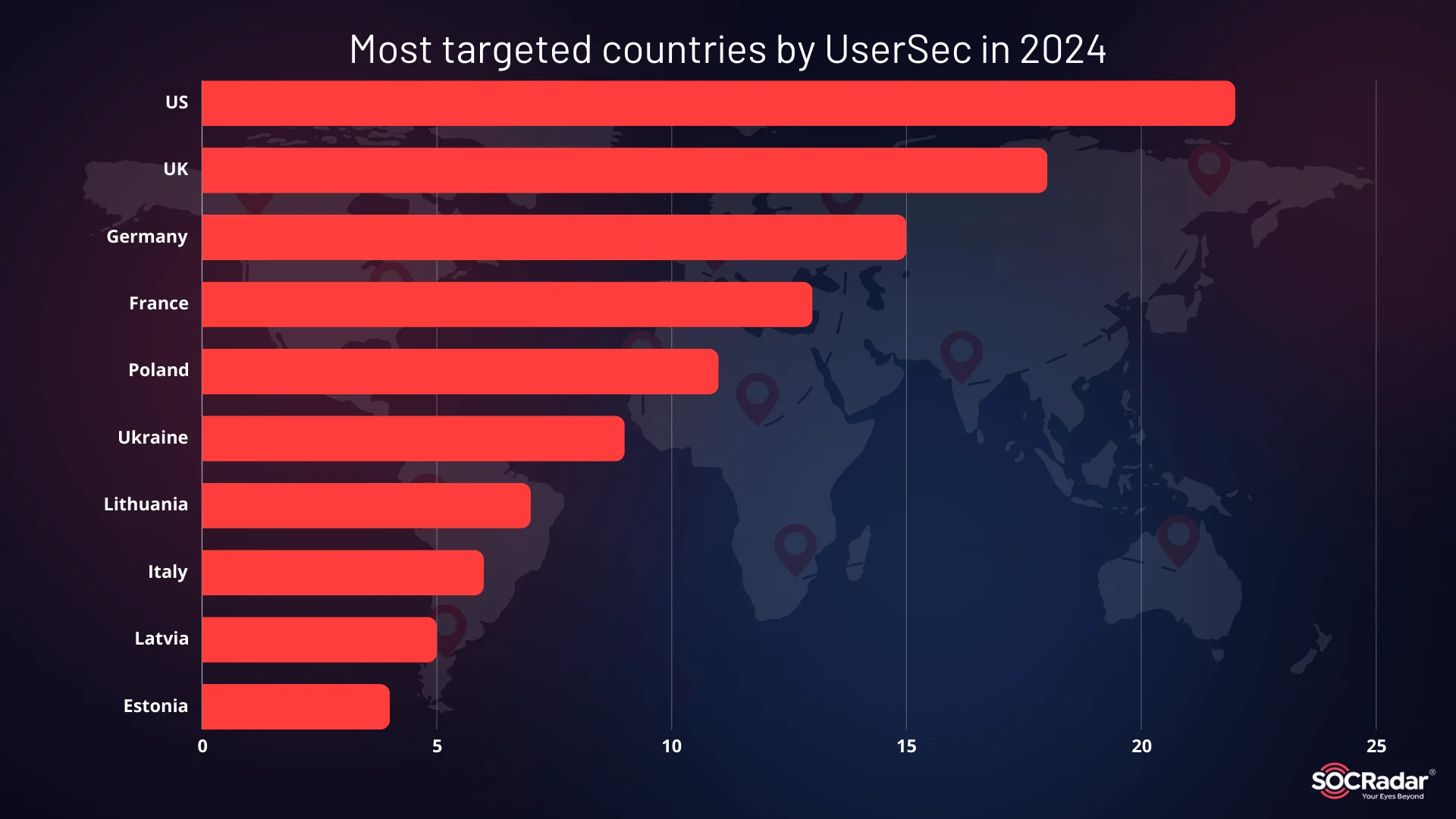
Estimated number of organizations in the most targeted countries by UserSec and associated groups of High Society in 2024
As stated above, UserSec predominantly attacks NATO-member states, particularly the United States, United Kingdom, Germany, France, and Poland. Their attacks target government and military sectors, and they have claimed responsibility for several disruptive campaigns in 2023 and 2024. Notable incidents include a cyber campaign that targeted NATO military networks, causing significant disruptions.
In recent months, the group has focused on high-profile targets in the energy sector, with a specific emphasis on disrupting European energy supplies amid the ongoing geopolitical tensions. Their attacks often aim to destabilize critical systems or embarrass governments by exposing sensitive information.
What is High Society?
In 2024, UserSec escalated its efforts by launching a widespread recruitment drive called the “High Society”, seeking to bolster its membership and operational reach. This initiative has enabled the group to conduct more sophisticated and coordinated attacks across a broader range of sectors. Furthermore, their focus on NATO-member states has intensified, with growing attacks aimed at critical infrastructure and defense systems .

High Society’s Telegram logo
Their first message translated to English is as follows: “I announce that we have formed a new international hacker organization. In 8 hours, more than 20 hacker groups from all over the world have joined us. They all support us. From this day on, we begin to work with our brothers. Day and night, work will be in full swing to crack the enemy’s servers. Now there are hundreds of us and we are going after the heads of NATO and Europeans. Anyone who even blows in the direction of our country and the countries of our friends will be affected. The consequences will not take long to come.”
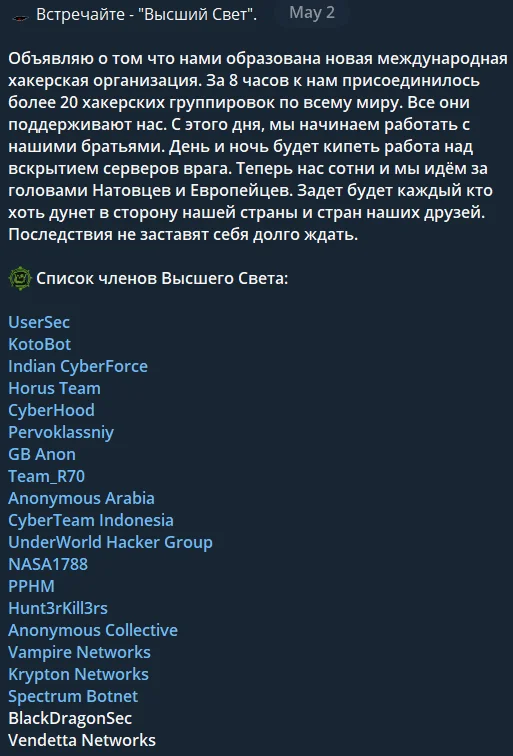
The message and the initial associated groups
When this hacker association was first founded, the largest pro-Russian groups were not initially involved, but the collective is still active and has continued to grow. The most prominent associated groups are NoName(057)16 and Cyber Army of Russia, which have also started working with the collective.

Joint operation against Canadian organizations with major pro-Russian groups
What Are Their TTPs?
| Tactic | Technique | Description |
| Initial Access | T1078.001 – Valid Accounts, Default Accounts | UserSec often uses brute-forcing or default credentials to gain unauthorized access to systems. |
| Execution | T1203 – Exploitation for Client Execution | The group exploits known vulnerabilities in public-facing applications to execute malicious code. |
| Persistence | T1078 – Valid Accounts | UserSec maintains access by using compromised credentials for continued system access. |
| Privilege Escalation | T1055 – Process Injection | They elevate privileges within systems through process injection techniques. |
| Credential Access | T1110.001 – Brute Force: Password Guessing | They with no prior knowledge of legitimate credentials within the system or environment may guess passwords to attempt access to accounts. |
| Discovery | T1083 – File and Directory Discovery | The group conducts searches to locate valuable files and directories for data exfiltration. |
| Collection | T1005 – Data from Local System | Sensitive data is gathered from local systems for exfiltration. |
| Impact | T1499 – Endpoint Denial of Service | UserSec carries out DDoS attacks to disrupt services and cause operational delays. |
What to Do to Mitigate the Threat?
To mitigate the threat posed by UserSec, organizations should consider the following actions:
- Patch Vulnerabilities Regularly: Apply patches and updates to public-facing applications and systems to prevent exploitation.
- Enable Multi-Factor Authentication (MFA): Protect all critical accounts with MFA to prevent the misuse of stolen credentials.
- Monitor Network Activity: Continuously monitor for abnormal behavior that could indicate lateral movement or credential dumping.
- Deploy DDoS Protection: Implement DDoS mitigation services to handle high-traffic attacks aimed at disrupting online services.
- Data Encryption: Encrypt sensitive data both in transit and at rest to limit the damage caused by potential data exfiltration.
- Incident Response Plan: Ensure that your organization has a robust incident response plan in place to quickly respond to and recover from cyberattacks.
How Can SOCRadar Help?
SOCRadar can assist organizations in defending against UserSec and similar threat actors through its Advanced Dark Web Monitoring and Threat Actor Intelligence services. SOCRadar’s Advanced Dark Web Monitoring continuously tracks dark web activity, including mentions of your organization or sensitive data, helping detect early signs of a potential attack. In addition, SOCRadar’s Threat Actor Intelligence provides detailed insights into the Tactics, Techniques, and Procedures (TTPs) used by groups like UserSec, enabling proactive defense strategies. These tools empower security teams to identify and mitigate threats before they cause significant damage.
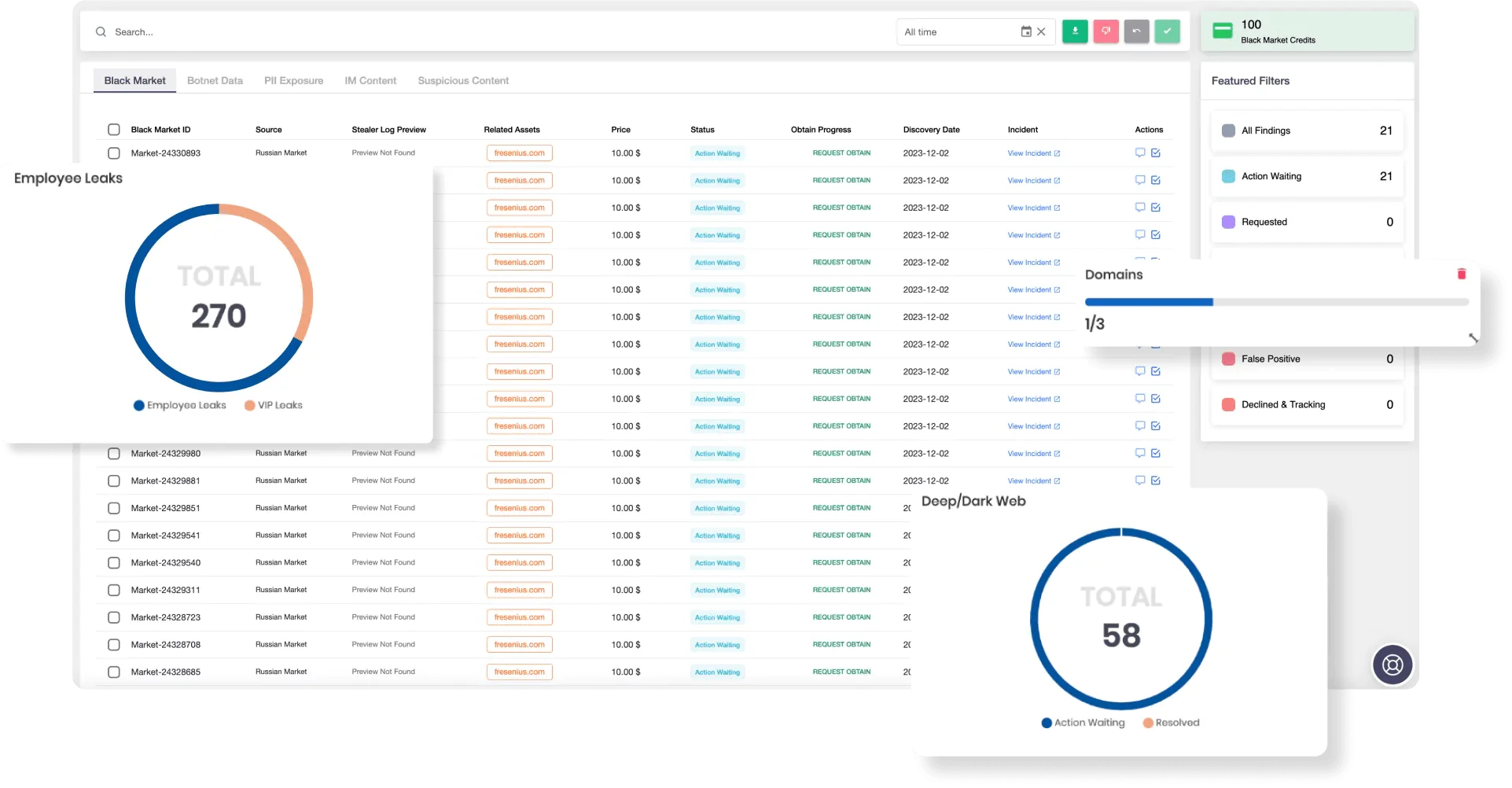
SOCRadar’s Advanced Dark Web Monitoring
Conclusion
UserSec has rapidly evolved into a formidable pro-Russian hacktivist group, known for its cyberattacks against NATO member states and organizations sympathetic to Ukraine. Leveraging platforms like Telegram, UserSec coordinates large-scale attacks, including DDoS, data breaches, and phishing campaigns. Their operations have targeted government institutions, defense contractors, and critical infrastructure, aiming to disrupt operations and expose sensitive information.
Their growing recruitment efforts and attacks on critical infrastructure suggest that UserSec’s threat to Western nations and NATO members will likely increase. Their alignment with pro-Russian narratives, although unofficial, implies a strategic motivation to further geopolitical objectives.




































