
Dark Web Profile: Ymir Ransomware
The emergence of Ymir ransomware adds a new layer to the cybersecurity landscape, featuring advanced tactics that challenge traditional security defenses. Originating from stealer malware as its initial access vector, Ymir operates stealthily in memory, marking it as a notable topic for IT security teams.

AI illustration of Ymir Ransomware
While the name ‘Ymir’ might bring to mind a frosty giant from Norse mythology, the only thing this ransomware freezes is your computer system—not the kind of ‘chill’ anyone would welcome! This blog post explores the mechanics of Ymir ransomware, highlights key Indicators of Compromise (IoC), and provides a comprehensive guide to its operational tactics, its business impacts, and the essential measures to mitigate its threats.
Who is Ymir Ransomware?
Ymir is a new ransomware strain that exemplifies the evolving sophistication of cyber threats. Identified by Kaspersky researchers during an incident response, Ymir stands out for its advanced in-memory execution technique, which allows it to encrypt systems stealthily without significant traces on the hard drive. This ransomware was first noticed in the wild in July 2024 when it began targeting companies globally, signaling its rapid spread and the significant threat it poses.
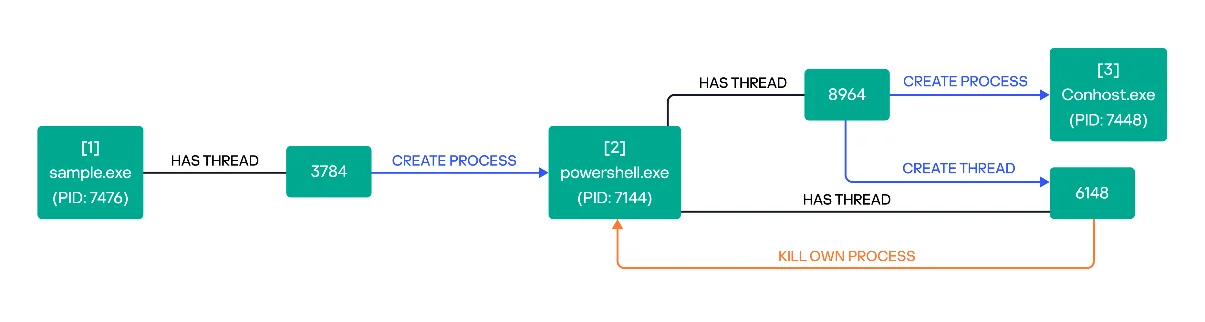
Malicious processes (Source: Kaspersky)
Originating from systems compromised by the RustyStealer infostealer malware, Ymir utilizes this foothold to launch ransomware attacks. This partnership between different types of malware underscores a growing trend in cybercrime operations collaborating to maximize their impact. Interestingly, Ymir includes unique elements such as the use of the African Lingala language in its code comments and employs PDF files as ransom notes, adding layers of complexity to its operations.
While Ymir has the capability to connect to external servers — potentially indicating preparations for data exfiltration — it currently lacks the functionality to perform exfiltration itself. This aspect could suggest either an unfinished capability or reliance on other tools for this purpose.
How Does Ymir Operate? – The Modus Operandi
Initial Access Vectors: Ymir ransomware typically gains entry into systems through a previous infection with stealer malware like RustyStealer. This malware family is designed to harvest credentials and sensitive information, paving the way for subsequent attacks. By exploiting these stolen credentials, attackers can bypass security measures and deploy Ymir directly within the compromised systems.
Execution and Evasion Techniques: Once inside, Ymir operates predominantly in the system’s memory, using sophisticated techniques to avoid detection. It leverages system functions such as malloc, memmove, and memcmp to manipulate memory and execute its payload stealthily. This in-memory approach minimizes its footprint on the hard disk, reducing the chances of being detected by traditional antivirus and endpoint detection solutions that monitor file activities.
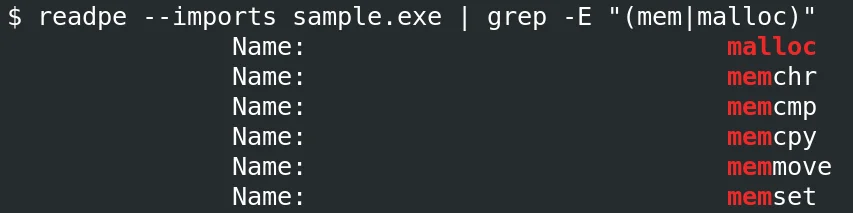
Calls to functions that operate on memory (Source: Kaspersky)
Persistence and Spread: Despite its primary reliance on in-memory execution, Ymir can establish persistence by creating scheduled tasks or registering as a system service, ensuring it remains active even after a system reboot. Additionally, it may use lateral movement techniques to spread across the network. These methods typically involve further exploitation of the harvested credentials to access other systems or using common administrative tools in a way that mimics legitimate user activity.
Encryption Process: Ymir uses the ChaCha20 encryption algorithm to lock files, appending a unique extension to encrypted files. This process is swift and designed to target specific file types that are crucial for business operations, thereby maximizing disruption and increasing the pressure on the victim organization to comply with ransom demands.
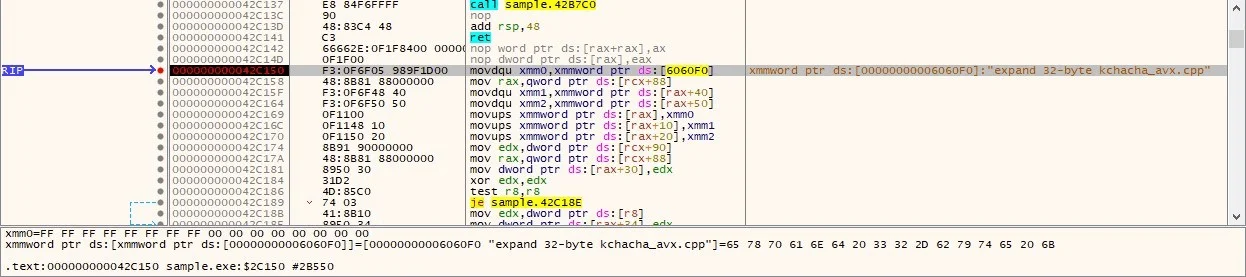
ChaCha20 encryption(Source: Kaspersky)
Covering Tracks: To further evade detection and hinder response efforts, Ymir meticulously deletes any traces of its initial entry vectors and activity logs. This includes overwriting files and cleaning up system logs that could be used to investigate the attack, making forensic analysis more challenging.
Countries targeted by the Ymir ransomware campaign
According to researchers, the Ymir ransomware campaign has demonstrated its global reach, affecting multiple countries. Notable regions include Colombia, where the ransomware was deployed; Pakistan, identified as the origin of a test sample; and countries such as Australia and Ukraine, linked through command-and-control (C2) server activity.
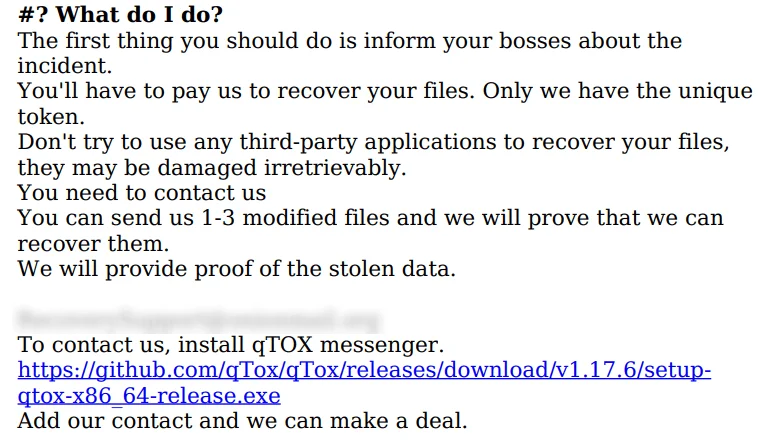
Ymir’s ransom note (Source: Kaspersky)
Additionally, the presence of Lingala language comments suggests potential ties to Central African countries, including the Democratic Republic of the Congo, Republic of the Congo, Angola, and the Central African Republic. Despite its activity, researchers note that the group behind Ymir has not yet established a dedicated data leak site.
How Can You Defend Against Ymir and Similar Ransomware Attacks?
To effectively defend against ransomware attacks like those executed by Ymir, organizations must adopt a robust, multi-layered security strategy. Below are key measures to minimize the risk of such infections:
Preventing Initial Access
- Patch Management: Regularly update and patch systems, especially public-facing applications, to close vulnerabilities that attackers exploit. Automated tools can streamline this process.
- Network Segmentation: Restrict lateral movement by isolating sensitive systems and critical data from broader networks.
- Access Controls: Implement firewalls, Intrusion Prevention Systems (IPS), and secure Virtual Private Networks (VPNs) to monitor and control access to remote services.
Strengthening Identity Security
- Multi-Factor Authentication (MFA): Apply MFA across all critical systems to mitigate brute-force attacks and unauthorized access.
- Strong Password Policies: Enforce complex, unique passwords, rotated regularly, and managed securely with password managers.
- Employee Training: Educate users on phishing risks and proper password hygiene to prevent credential-based attacks.
Monitoring and Protecting Credentials
- Dark Web Monitoring: Regularly track credential dumps and leaks to identify exposed data early.
- Account Lockouts: Set thresholds for failed login attempts to prevent brute-force attacks and unauthorized access.
Preventing Malware Execution
- Endpoint Detection and Response (EDR): Deploy tools to detect unauthorized script executions, suspicious behaviors, and new account creations.
- Application Whitelisting: Only allow approved applications to run within the network to limit malware execution.
- Behavioral Analytics: Identify anomalous activities that may indicate ransomware behavior.
Limiting Persistence and Lateral Movement
- Principle of Least Privilege (PoLP): Regularly review and minimize user privileges to reduce attack surfaces.
- Harden Remote Services: Disable Remote Desktop Protocol (RDP) and restrict Server Message Block (SMB) access when unnecessary.
- Network Traffic Monitoring: Detect unusual activity indicative of lateral movement or command-and-control communications.
Mitigating Ransomware Impact
- Data Backup: Maintain regular offline backups and test their restoration to ensure business continuity in case of an attack.
- Isolated Backup Systems: Separate backups from the main network to prevent encryption by ransomware.
- Incident Response Plan: Develop a comprehensive IR plan for ransomware, including containment, stakeholder communication, and recovery steps.
Post-Incident Recovery
- Ransomware Decryption Tools: Check for publicly available decryption tools from trusted sources like No More Ransom.
- Forensics and Logging: Analyze detailed logs to identify attack vectors and strengthen defenses.
- Law Enforcement Collaboration: Report incidents to authorities to support broader threat intelligence efforts.
How SOCRadar Can Assist in Defending Against Ymir Ransomware
SOCRadar provides advanced tools to help organizations detect, mitigate, and prevent ransomware attacks like Ymir. Key capabilities include:
- Threat Intelligence: Gain insights into emerging ransomware tactics, techniques, and procedures (TTPs), staying ahead of attackers.
- Dark Web Monitoring: Detect and respond to leaked credentials, exploits, and ransomware payloads related to Ymir on the Dark Web.
- Vulnerability Intelligence: Receive real-time updates on vulnerabilities exploited by ransomware groups, enabling preemptive patching.
- Ransomware Tracking: Identify ransomware variants and associated tools to prepare defenses against new strains.
- Timely Alerts: Leverage real-time alerts and detailed reports on ransomware IoCs, attack vectors, and recommended actions to protect your infrastructure effectively.
By combining proactive measures with SOCRadar’s advanced cybersecurity capabilities, organizations can significantly reduce the risk of ransomware infections and improve their overall resilience against sophisticated threats like Ymir.
What Are Their MITRE ATT&CK Techniques?
MITRE ATT&CK techniques by Kaspersky:
Ymir TTPs Identified from Malware Analysis
| Tactic | Technique | ID |
| Discovery | File and Directory Discovery | T1083 |
| Discovery | System Information Discovery | T1082 |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| Impact | Data Encrypted for Impact | T1486 |
| Defense Evasion | Virtualization/Sandbox Evasion: Time Based Evasion | T1497.003 |
| Defense Evasion | Indicator Removal: File Deletion | T1070.004 |
RustyStealer TTPs
| Tactic | Technique | ID |
| Discovery | File and Directory Discovery | T1083 |
| Discovery | Process Discovery | T1057 |
| Execution | Shared Modules | T1129 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
IOC’s Related to Ymir Ransomware
File Hashes
3648359ebae8ce7cacae1e631103659f5a8c630e
fe6de75d6042de714c28c0a3c0816b37e0fa4bb3
f954d1b1d13a5e4f62f108c9965707a2aa2a3c89 (INCIDENT_REPORT.pdf)
5ee1befc69d120976a60a97d3254e9eb
5384d704fadf229d08eab696404cbba6
39df773139f505657d11749804953be5
8287d54c83db03b8adcdf1409f5d1c9abb1693ac8d000b5ae75b3a296cb3061c
51ffc0b7358b7611492ef458fdf9b97f121e49e70f86a6b53b93ed923b707a03
b087e1309f3eab6302d7503079af1ad6af06d70a932f7a6ae1421b942048e28a
IPs
74.50.84[.]181:443
94.158.244[.]69:443
5.255.117[.]134:80
85.239.61[.]60



































