
Dark Web Threat Profile: CLOP Ransomware
[Update] August 7, 2023: Clop ransomware has now adopted Torrents as a distribution method for the stolen data. See more under: “Clop Adopts New Extortion Approach: Leaking Data via Torrents.”
[Update] July 28, 2023: See the subheading: “Clop Breached US Contractor Maximus in MOVEit Attacks: 8-11 Million Personal Data Stolen.”
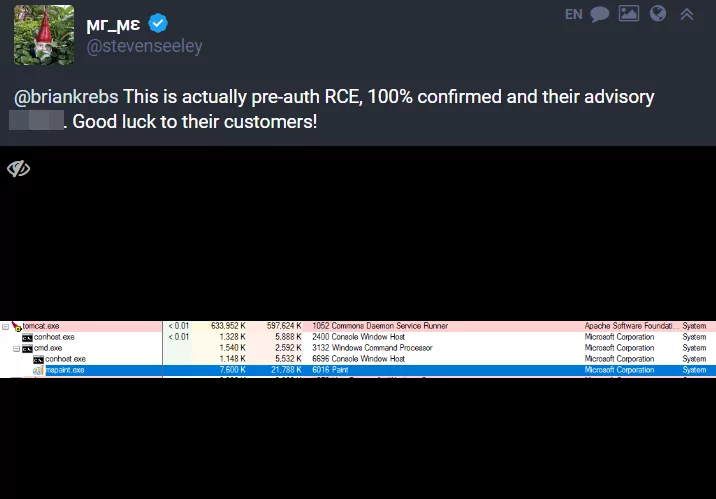
On February 2, 2023, Brian Krebs, author of KrebsOnSecurity, shared a post on the Mastodon platform about a newly discovered zero-day. In his post, he mentioned a remote code injection vulnerability in GoAnywhere MFT, Fortra’s secure managed file transfer solution. According to SOCRadar’s observations, there are more than 1000 systems worldwide whose administrative ports that may be vulnerable to this zero-day are open to the public internet. Truebot was observed actively exploiting this vulnerability. Clop ransomware, which is thought to be an affiliate of Truebot, has also started to appear in the headlines frequently with its high number of claims.
In this article, we’ll closely look into the activities of Clop ransomware and analyze its malware.
Don’t Worry C|0P
CLOP, aka CL0P, Ransomware, a member of the well-known Cryptomix ransomware family, is a dangerous file-encrypting malware that intentionally exploits vulnerable systems and encrypts saved files with the “.Clop” extension. The word clop comes from the Russian word “klop,” which means “bed bug,” a Cimex-like insect that feeds on human blood at night (mosquito). A distinguishing feature of CLOP is the string “Don’t Worry C|0P” found in the ransom notes.

CLOP attacks have been on the rise since February 2019, according to cybersecurity experts. CLOP, for example, attacked the well-known cybersecurity compliance company Qualys in March 2021 to steal client data. CLOP ransomware is linked to the financially motivated threat group TA505 (Hive0065), according to Palo Alto’s Unit42.
On June 16, 2021, As part of an international operation, including law enforcement agencies from Ukraine, South Korea, and the US, police arrested many people suspected of being involved in the CLOP ransomware gang. A few days after the operation, the ransomware group grabbed headlines by publishing data obtained from new victims.
Among their most notorious operations was the attack against Software AG in October 2020, which became the first recorded ransomware demand exceeding $20 million. This incident solidified their presence as a significant player in the ransomware landscape.
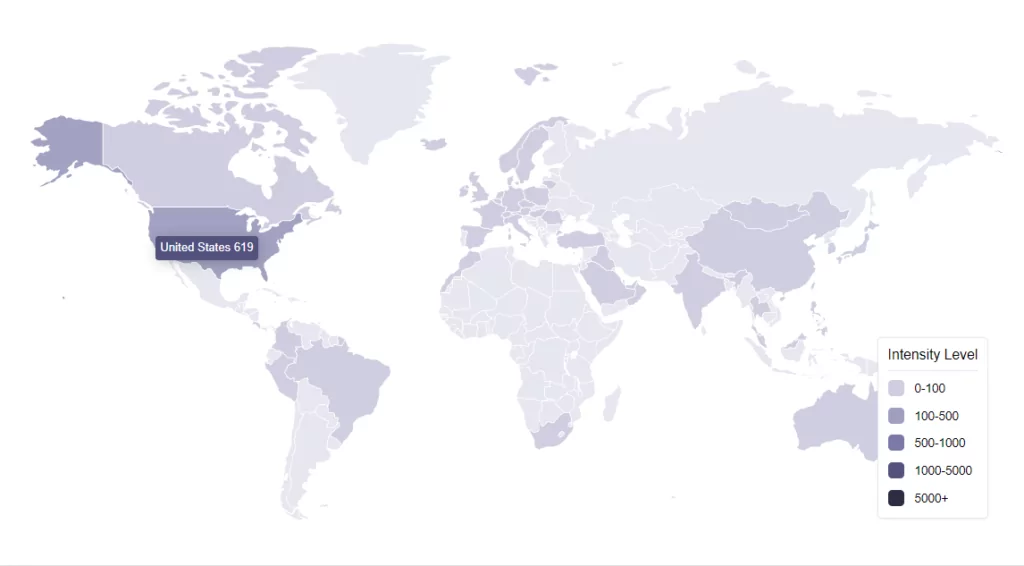
Targeting High-Profile Industry Giants Worldwide
The report released by CISA on March 23 argues CLOP has already been used to target a number of The International Network of Health Promoting Hospitals and Health Services (HPH) groups in the United States and organizations in Canada and Sweden.
Following FIN11, a threat actor, Mandiant experts have concluded that the gang is based somewhere within the Commonwealth of Independent States (CIS). This rating is based on FIN11’s avoidance of systems that use CIS-country keyboard layouts and file metadata in Russian.
Retail, transportation, education, manufacturing, engineering, automotive, energy, financial, aerospace, telecommunications, professional and legal services are among the industries that have been affected by CLOP ransomware. For example, in December 2020, CLOP operators and their affiliates started exploiting some zero-day vulnerabilities in the Accellion File Transfer Appliance (FTA) software and began targeting its consumers.
| Top 3 Industries Targeted by Cl0p | |
|---|---|
| Finance | 21.38% |
| Information Technologies | 18.62% |
| Manufacturing | 13.45% |
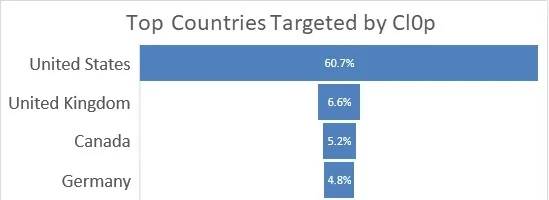
We analyzed the targeted locations of Cl0p’s attacks. Upon examining the statistics of the most frequently attacked countries, we found that they are predominantly Western countries, including the United States, United Kingdom, Germany, and Canada. Not surprisingly, a significant majority of Cl0p’s attacks, totaling 77.3%, were concentrated on these countries.
How Can CLOP Ransomware Infect Devices?
CLOP ransomware can infect a computer by various means, including spam email attachments, trojans, URLs, cracks, unprotected Remote Desktop Protocol (RDP) connections, malicious websites, and so on.
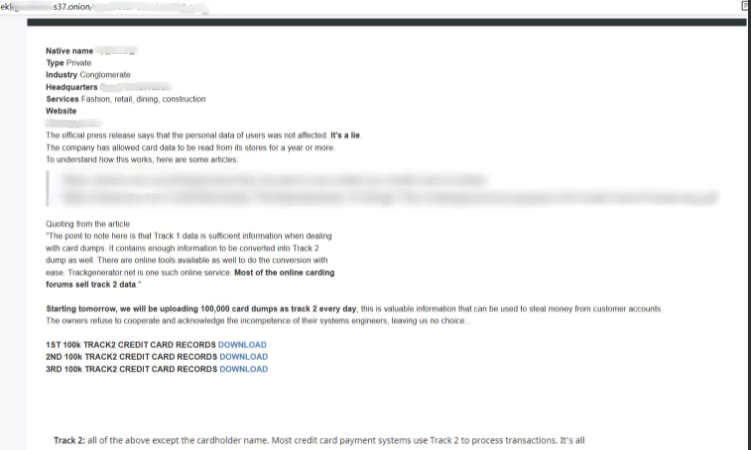
In February 2019, CryptoMix ransomware strain CLOP behaved similarly to previous versions of CryptoMix. Security researchers discovered in March 2019 that the release changed its behavior and now disables services for enterprise applications such as Microsoft Exchange, Microsoft SQL Server, MySQL, and BackupExec. CLOP’s December 2019 update enhanced this feature by identifying and eliminating 663 programs on the device before starting the encryption procedure.
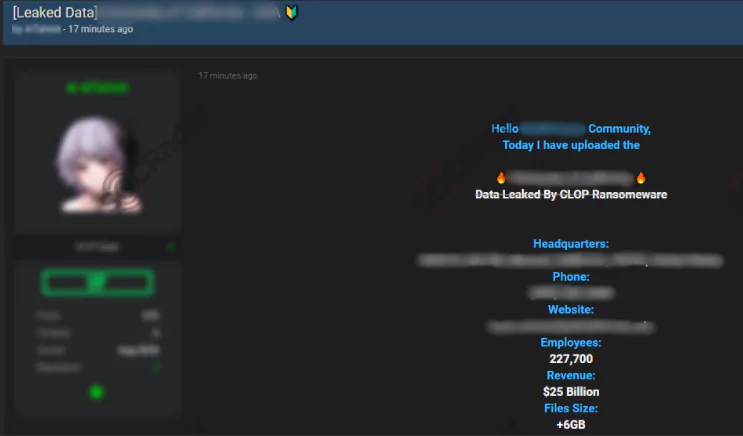
The actors then demand payment to decode the data and ensure that the organization’s data is not leaked. If a victim does not pay the ransom, their information will be published on CLOP’s ransomware website, CL0P – LEAKS.
CLOP operators have also been observed to combine a “spray and pray” approach with a more targeted approach to compromise targets by running large-scale phishing campaigns and then choosing which networks to compromise for monetization, according to Mandiant FireEye researchers.
As a result of the research conducted on Alienvault, a sample malware with a hash value of 82d4025b84cf569ec82d21918d641540 associated with TA505 and Clop is gathered by SOCRadar’s threat researchers and examined. The analysis observed that the malware made process injection and transmitted the running processes to the hxxp[:]//qweastradoc[.]com/gate.php domain address in a base64 encoded format.
![Decoded Base64 request using CyberChef that the malware sent tp gate[.]php, Clop ransomware](https://socradar.io/wp-content/uploads/2023/03/decoded-1024x424.png.webp)
When the IP address is queried in SOCRadar’s Threat Hunting panel, it can be seen that it is blacklisted by SOCRadar.
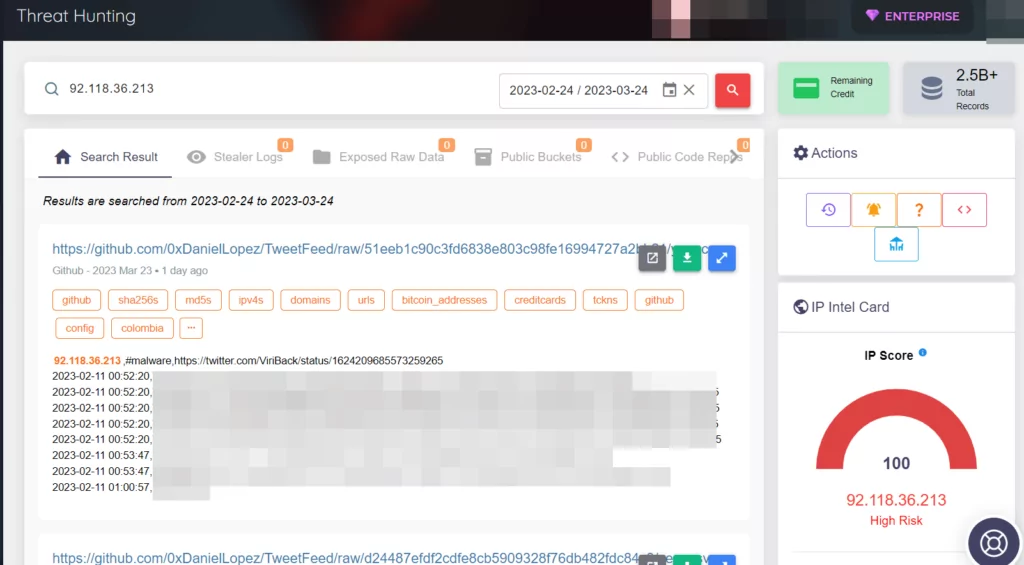

When we examined the exposed data from the outputs, we observed that Truebot used this IP address on February 11, 2023.
Clop Adopts New Extortion Approach: Leaking Data via Torrents
Clop had recently resorted to creating clear web sites as a means to leak stolen data from certain victims of the MOVEit data theft campaign. Nevertheless, such domains are more susceptible to takedown by law enforcement and companies. Seeking an alternative, Clop has now adopted Torrents as a distribution method for the data.
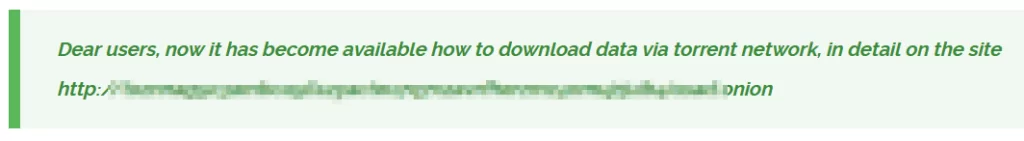
In this new extortion tactic, Clop has established a TOR site with instructions on using Torrent clients to download the leaked data, and listed magnet links.
Torrents enable faster transfer speeds through peer-to-peer transfer and offer decentralized distribution, making it difficult for law enforcement to shut down. A new device can be used to continue seeding the stolen data even if the initial seeder goes offline.
Clop has created Torrents for 20 victims so far: Putnam, Iron Bow, City National Bank, Andesa, Stiwa Group, Enzo Biochem, Delaware Life, NavAXX, Heidelberg, Landal, Zurich Brazil, Aon, UnitedHealthcare Student Resources, K&L Gates, Paycor, CareSource, 1stSource, PwC, Ernst & Young (EY), Paycom.
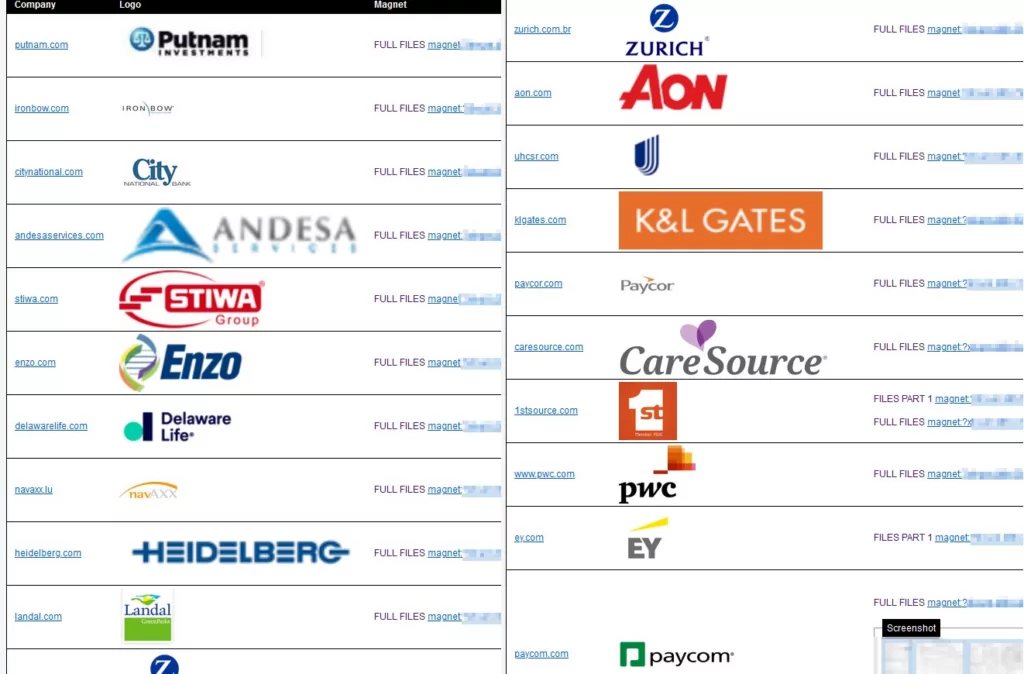
This development raises concerns, as obtaining files through the TOR network was previously characterized by considerable challenges and time-consuming processes. With the integration of Torrent, the dissemination of data will now occur at a significantly accelerated pace. However, it is essential to acknowledge the potential drawbacks of this approach, as it enables the possibility of identifying individuals who engage in downloading activities, thereby compromising their anonymity.
SOCRadar Platform Statistics and Cl0p
In 2022, the monthly average of ransomware announcements, which included sharing the names of new victims or exposing data from previous incidents, was around 215. However, in the first half of 2023, this number increased significantly to 328, marking an increase of approximately 52% compared to the previous year.
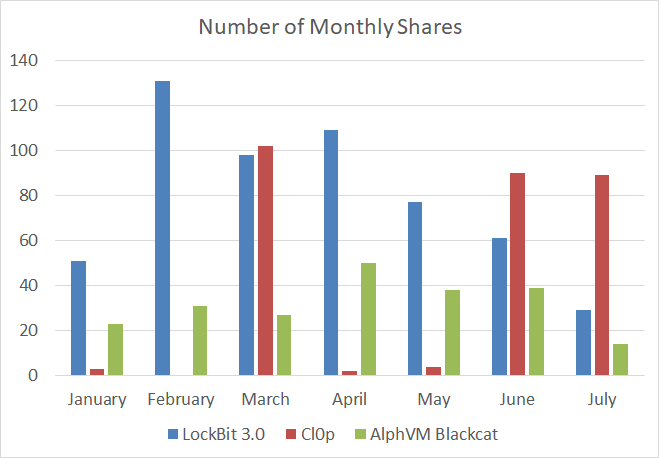
For the period from January 1, 2023, to July 17, 2023, SOCradar researchers recorded a total of 2211 shares. Of these, the three most active groups were LockBit 3.0, Cl0p, and AlphVM BlackCat, with LockBit 3.0 leading the pack with 556 shares.
Recent Attacks of CLOP Ransomware
Clop, which victimized hundreds of companies with the GoAnyWhere MFT vulnerability, has started to announce new victims by exploiting the zero-day vulnerability of another managed transfer tool (MFT) solution, MOVEit Transfer.
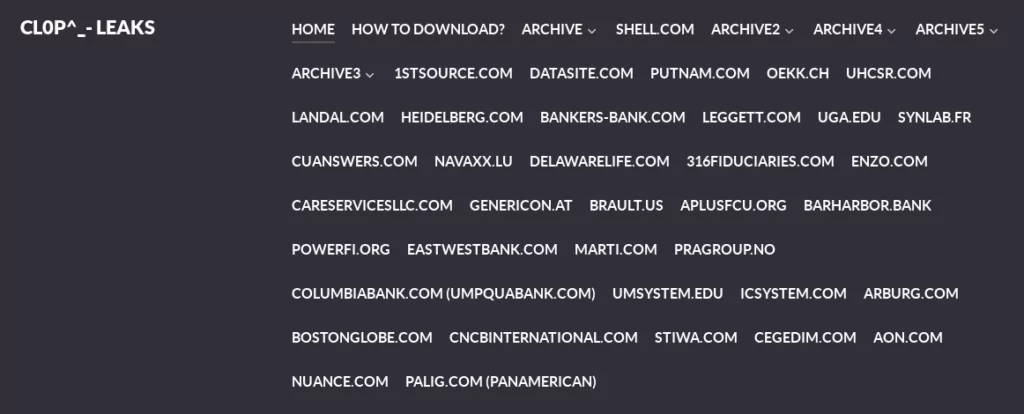
The list of victims is extensive and includes several US banks and universities. Financial services organizations like 1st Source and First National Bankers Bank, investment management firm Putnam Investments, and energy giant Shell were among the compromised. Other victims included a wide range of organizations such as financial software provider Datasite, educational non-profit National Student Clearinghouse, student health insurance provider United Healthcare Student Resources, American manufacturer Leggett & Platt, and Swiss insurance company ÖKK.
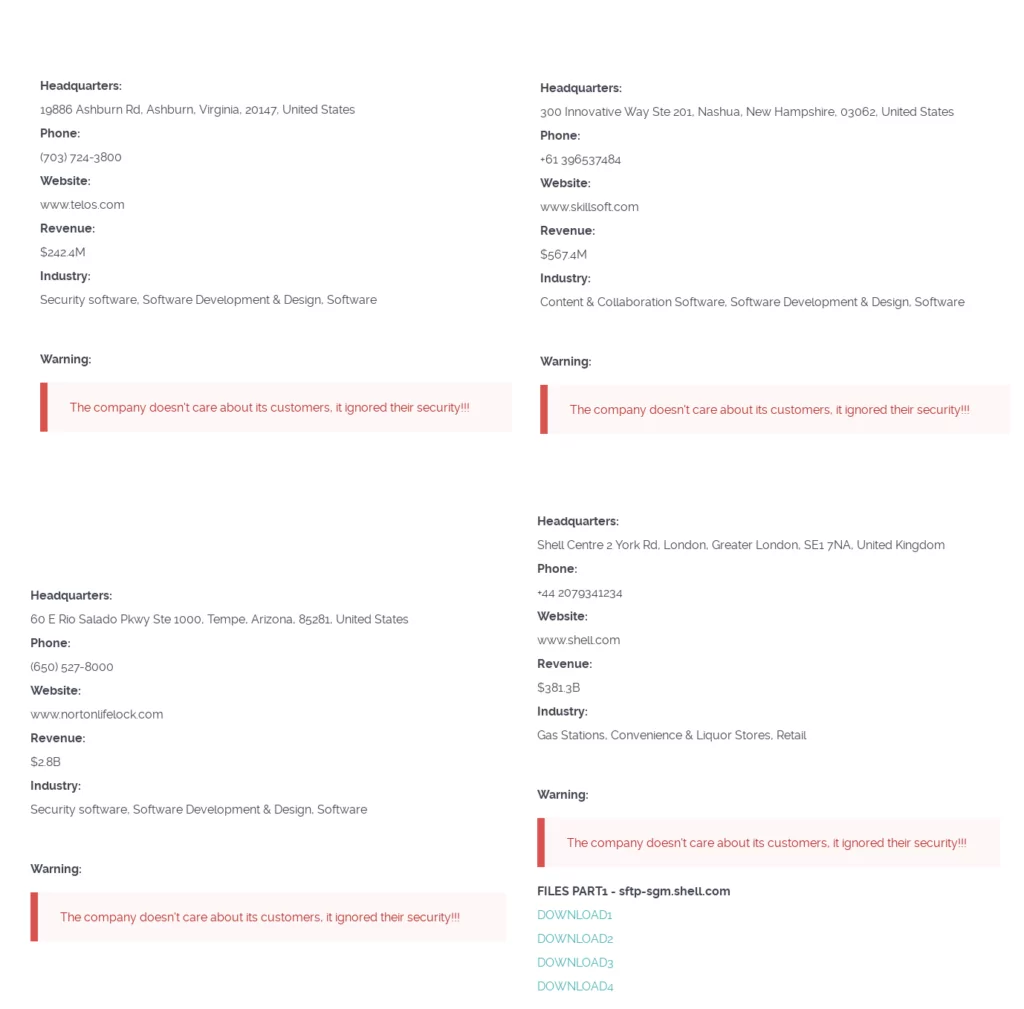
Lately,
- Global energy and petrochemical company Shell’s leaked data has been shared on Clop’s Tor page.
- Australian accounting firm PwC has been targeted.
- Innovative cloud-based corporate learning provider Skillsoft has been announced as a victim.
- American IT and cybersecurity firm Telos Corporation has been announced as a victim. Researcher Dominic Alvieri posted on Twitter that known customers of Telos include FedEx, Raytheon Technologies, Verizon, Citi, the US Department of State, and the US Department of Defense, which raises concern.
- Leading consumer cybersecurity software provider NortonLifeLock has been announced as a victim.
It seems they are just a few of the notable victims of this “automated exploitation attack chain.”
Interestingly, Clop took an unusual step in its ransomware attack strategy. Instead of contacting the organizations it had hacked to demand a ransom, it instructed the victims how to contact them:
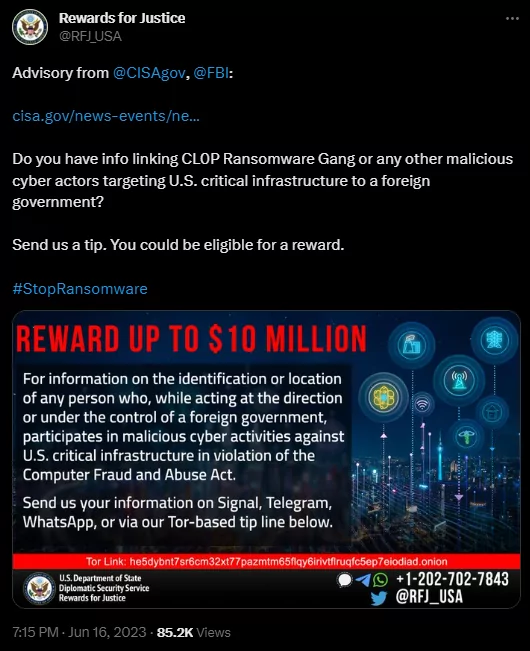
CISA published an advisory on Clop’s MOVEit activity, and shortly after these announcements, U.S Rewards for Justice announced on its official Twitter page that it would offer a reward of up to $10 million for information sharing that links to Clop ransomware and other malicious cyber actors, It would not be wrong to foresee this announcement as a good move to conquer the castle from the inside.
The information on Clop’s Tor page shows that the group insists that they are a threat actor with “financial” motives and that they do not hold any government data:
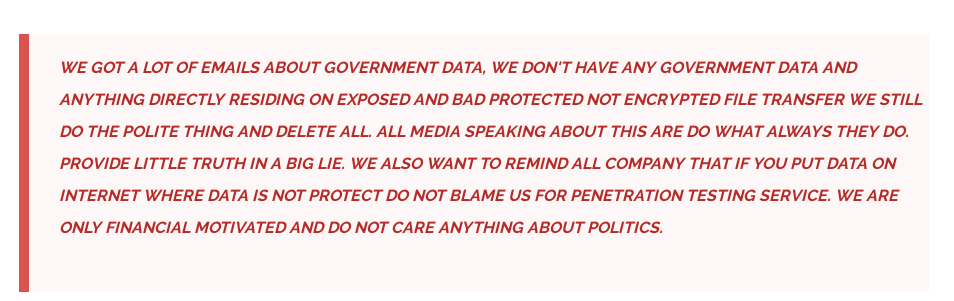
As previously mentioned, the Clop Ransomware gang makes claims from an onion extension page with the “CL0P^_-LEAKS” logo. It has made a lot of claims by exploiting the recently revealed CVE-2023-0669 vulnerability.
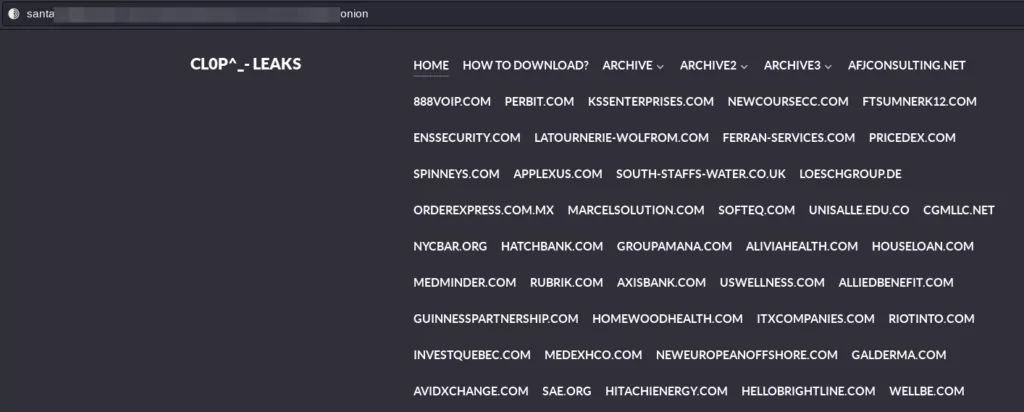
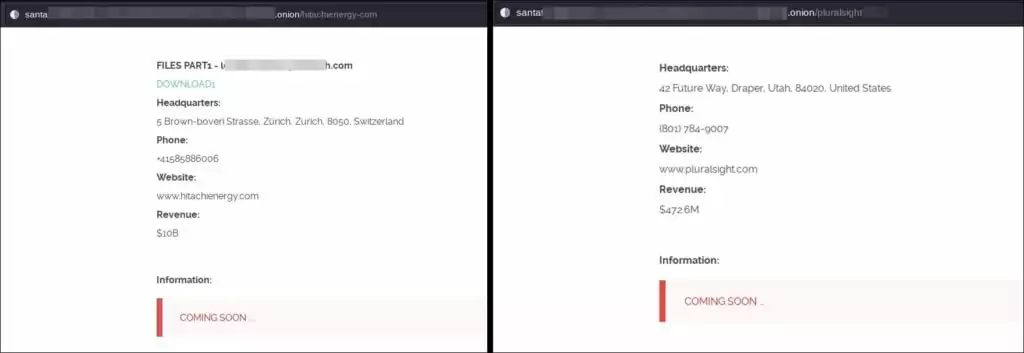
The fact that there were more claims than expected and no data was exposed led to the impression that the claims were fake at first. But, the recent confirmations by Rubrik and Hitachi Energy, respectively, make it more and more likely that they are real.
One of the shares that support the reality of the claims is the exposed data belonging to the 888voip domain:
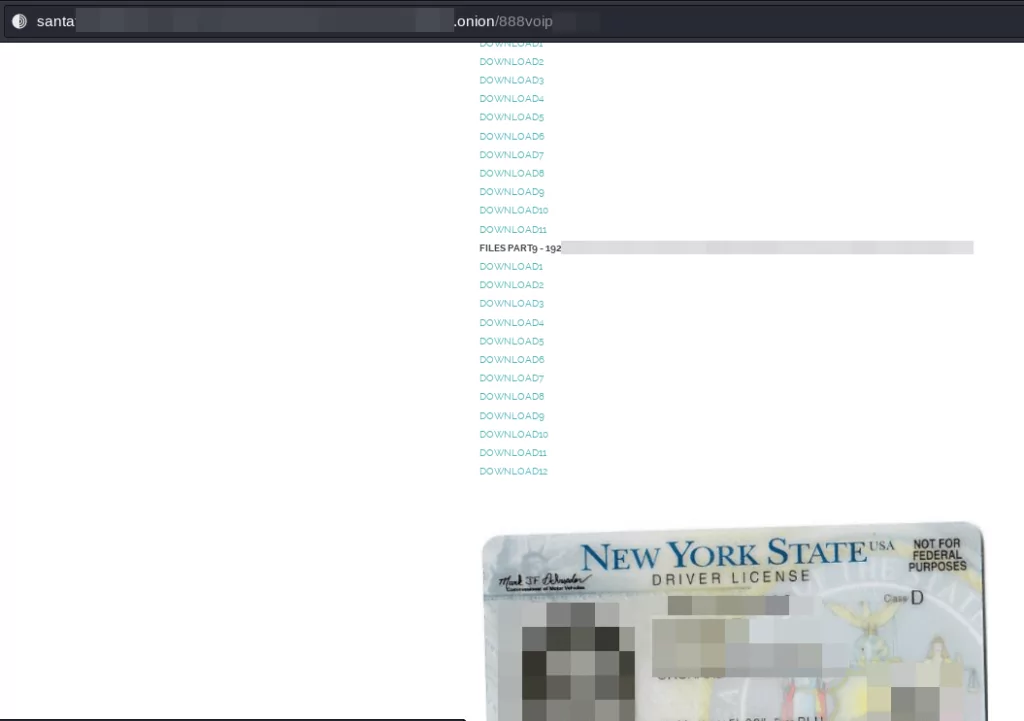
Based on various posts confirming that this vulnerability is pre-auth remote code injection, it can be assumed that customers using GoAnywhere MFTs are still at risk.
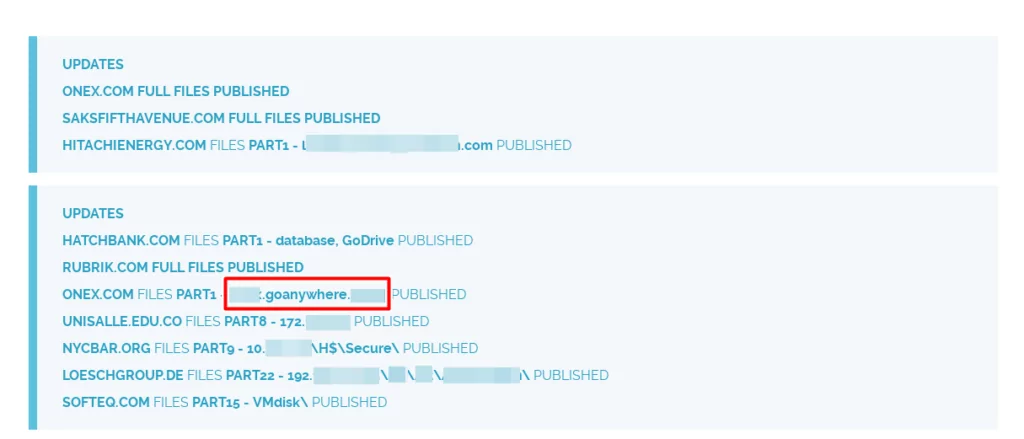
Another situation that may support the fact that GoAnywhere MFT is actively exploited by the group is that its domains are mentioned in the leaked data extensions, as seen in the screenshot taken from the Clop leaks site below:
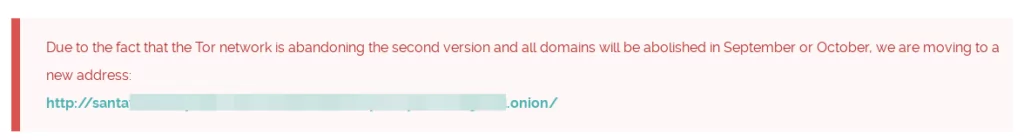
Another question that comes to mind is whether the fact that the group recently updated the onion URL to a different onion URL with the “Santa” word contained at the beginning could be a message that they share more of these claims and data.
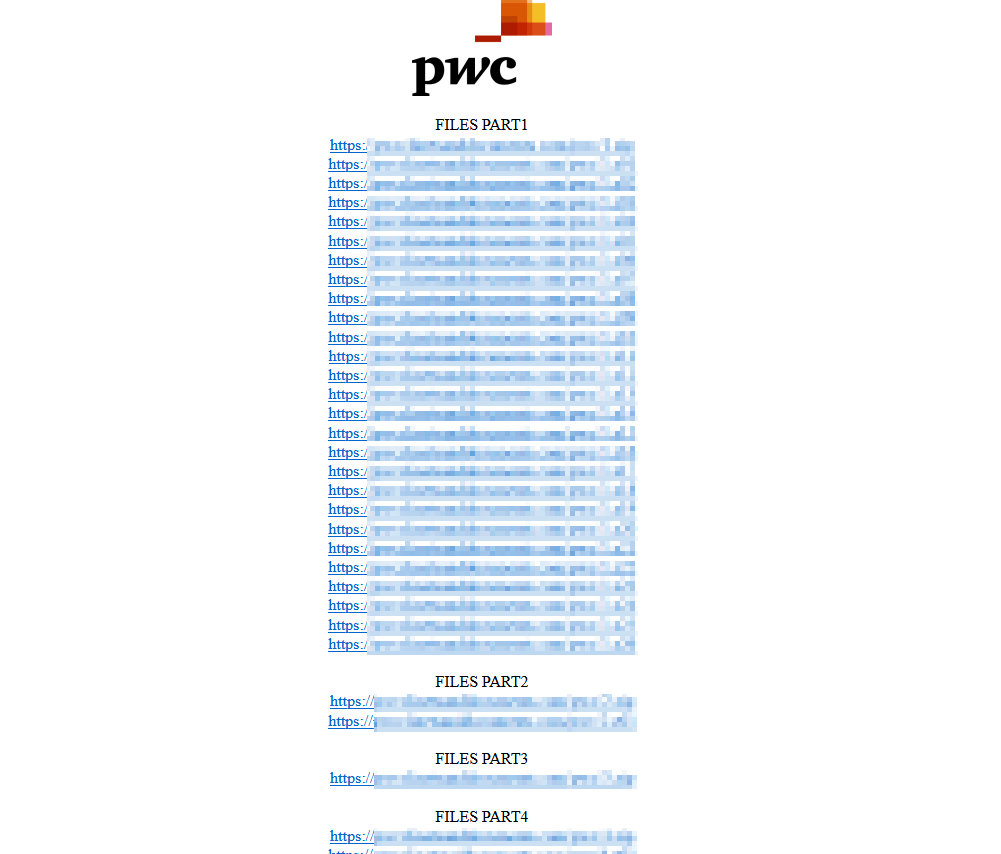
Clop Makes a New Site for PwC Leak
Having exploited the vulnerability in MOVEit, the Clop Ransomware group continues to leak documents and data related to victims. The group most recently shared the 11th part of files related to PwC before creating a new URL to house the entirety of stolen information.

Researcher Dominic Alvieri took to Twitter to share the incident as breaking news and highlighted that Clop is using the tactic of the BlackCat group by making a new site for the leak.
Clop has also recently added 10 more victims to its dark web leak site. The US victims include American Airlines, Jonas Fitness, logistics company SMC3, multi-sector manufacturer ITT, Allegiant Air, cosmetics company Estée Lauder, Bluefin Payment Systems, and Ventiv Technology, while telecommunications sector companies Ofcom (UK) and ComReg (Ireland) are also listed.
Clop Breached US Contractor Maximus in MOVEit Attacks: 8-11 Million Personal Data Stolen
The Clop ransomware gang has added 70 new victims to its dark web data leak site, all breached using the MOVEit zero-day vulnerability (CVE-2023-34362). Among these victims is the US government services contractor Maximus, which reported the theft of personal data from 8 to 11 million individuals due to the incident.
Operating across the US, Canada, Australia, and the United Kingdom, Maximus manages various government-sponsored programs, including healthcare and student loan servicing.
According to the claims made by the Clop group, they successfully stole 169GB of personal data from Maximus’ MOVEit Transfer server. However, as of yet, the ransomware gang has not disclosed any of the stolen data.
With the list of victims affected by the MOVEit Transfer attacks continuously expanding, the Clop ransomware group intensifies their extortion tactics. In their recent efforts, they have launched clear web leak sites specifically to leak stolen data from certain companies. This approach puts increased pressure on the victims by making the data more accessible to a wider audience.
Maximus investigated the breach and found no evidence of hackers advancing beyond the MOVEit environment, which was quickly isolated from the corporate network. The company is working on notifying the affected individuals.
The Motivation Behind Clop’s Target Selection
The significant deviation in Cl0p’s target selection from global averages led us to reassess their attacking strategies. This suggests their choice of targets is either deliberate or an unintended consequence of their attack techniques and tactics.
Considering Cl0p is a financially-motivated ransomware group, it would be highly uncommon for them to specifically and purposefully choose targets. Hence, the more plausible explanation is that the observed discrepancy is an artifact resulting from their attack techniques and tactics rather than a deliberate targeting strategy.
Cl0p is recognized for pioneering innovative tactics and exploiting recent vulnerabilities like GoAnywhere, PaperCut, and MOVEit. Their focus on data-rich servers, especially targeting the MOVEit File Transfer utility, which is commonly used by financial institutions. While direct proof may be challenging, this theory explains the observed patterns.
This observation supports the notion that Cl0p strategically selects their targets based on the potential value and sensitivity of the data they can gain access to. By focusing on sectors with a higher likelihood of housing valuable financial information, they maximize their chances of achieving their financial motivations.
Mitigations for Preventing CLOP Infection

When defending against ransomware/extortion cybercrime groups, CLOP should be handled the same as any other.
- Think twice before opening email attachments or clicking on links. You should not open a file if it does not affect you or if the email address appears to be shady.
- It would help if you avoided third-party downloaders since they regularly produce dangerous programs.
- Remember that using unlicensed software is a kind of piracy, and there’s a high risk you’ll get infected because software cracking tools are regularly used to propagate malware.
MITRE ATT&CK TTPs of CLOP
The TTPs of the cl0p ransomware’s latest Linux variant can be found below:
(Used hash value is: 09d6dab9b70a74f61c41eaa485b37de9a40c86b6d2eae7413db11b4e6a8256ef)
| Technique Name | ID |
| Unix Shell Configuration Modification | T1546.004 |
| Linux and Mac File and Directory Permissions Modification | T1222.002 |
| File Deletion | T1070.004 |
| Virtualization/Sandbox Evasion | T1497 |
| System Information Discovery | T1082 |
| Email Collection | T1114 |
| Ingress Tool Transfer | T1105 |





































