Dark Web Profile: Phobos Ransomware
Phobos ransomware, first discovered in December 2018, is another notorious cyber threat that targets businesses. Unlike other cybercrime gangs that go after big hunts, the Phobos bad guys usually go after smaller firms that don’t have the financial wherewithal to pay massive ransoms.

Image illustrated by Bing AI Image Creator, Phobos Ransomware
More recently, it continues to attract attention as a ransomware strain not as a group. Lastly, the Cybersecurity and Infrastructure Security Agency (CISA) released the joint advisory on Phobos ransomware on February 29, 2024 and many variants of the Phobos are still prevalent.
Phobos, An Ordinary Ransomware
Phobos was popular among threat actors of various technical abilities because of its simple design. In addition, the Greek god Phobos was thought to be the incarnation of fear and panic; hence the name Phobos was likely inspired by him.
The CrySIS and Dharma malware families are closely connected to the Phobos ransomware. CrySIS was first identified in 2016; however, when the original author released the source code that same year, it earned a new level of popularity among threat actors.
The malware was renamed Dharma when its decryption keys were disclosed. Dharma is a Ransomware-as-a-Service (RaaS) paradigm that is sold by a number of different parties. After decryption tools and keys for the Dharma family were accessible late in 2018, Phobos debuted in the threat environment as a successor to Dharma. Dharma and Phobos have nearly identical ransom messages and share code commonalities. During an attack, the critical difference between the two is how they encrypt files.
More recently, affiliations and tactics have slightly changed and Phobos now appears to be associated with many other ransomware strains. Of course, this occurs within the scope of leaked ransomware codes and the subsequent mutation effect.
Victims of Phobos Ransomware
Phobos is a ransomware family that primarily targets small to medium-sized businesses including healthcare and victims were located in the U.S., Portugal, Brazil, Seychelles, Romania, Indonesia, Germany, and Japan.
When first discovered, attackers typically demanded far lower ransom sums than other ransomware families, making it more appealing to victims and increasing the possibility of payment. In July 2021, the average Phobos ransom payment was roughly $54,700.
Over time, Phobos has targeted a range of victims, encompassing state, county, and municipal governments, along with entities in healthcare, education, and critical infrastructure sectors.
In a recent case, a group linked to Phobos infiltrated approximately 100 hospitals in Romania using a variant known as Backmydata. They initiated the attack by focusing on a central health information system.
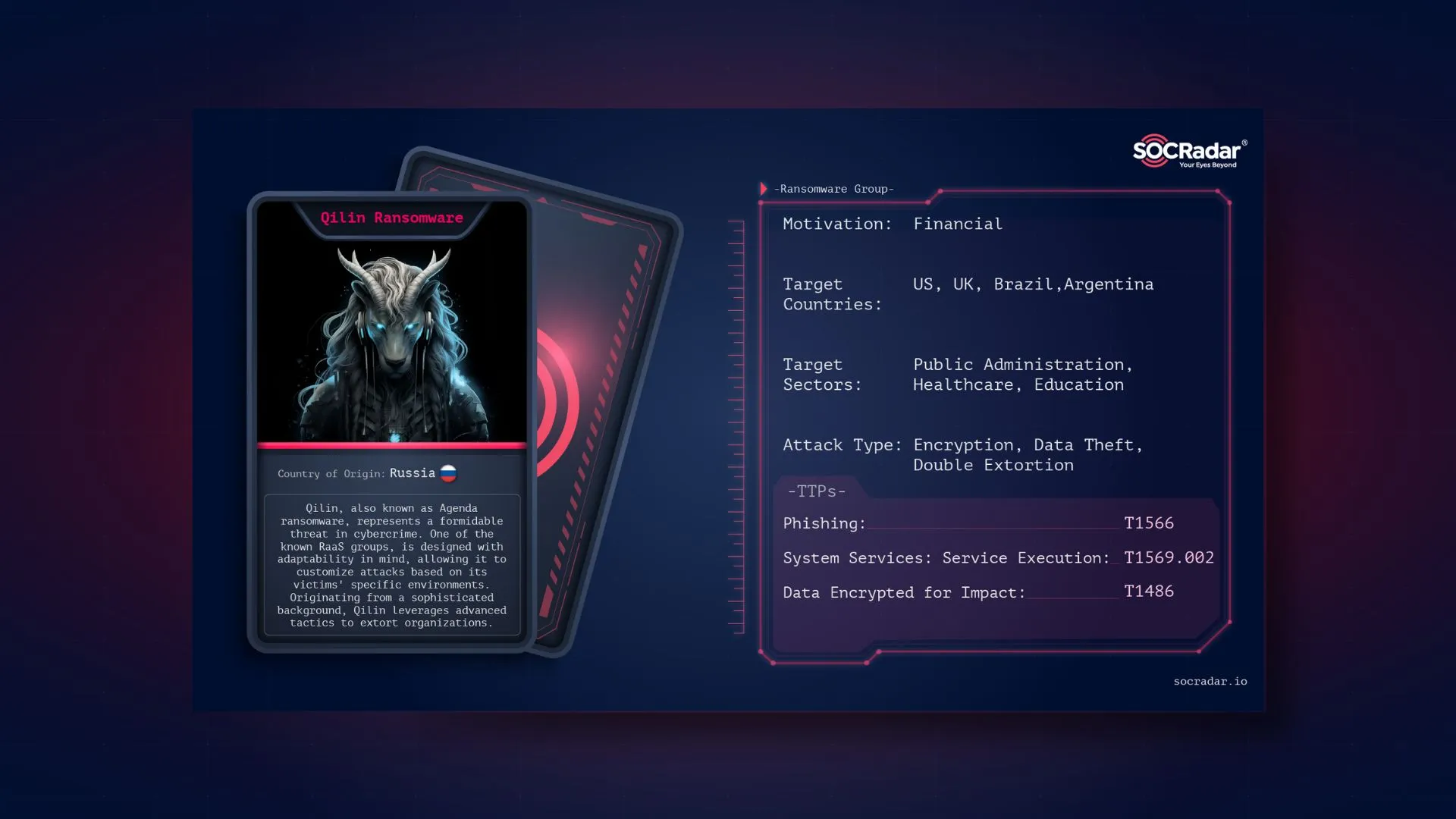
8Base, one of the most active groups of 2023, was also one of the groups using the Phobos variant. 8Base employed multiple ransomware strains, one of which is a version of Phobos.
8Base was one of the groups using a variant of Phobos
The group has tailored Phobos by adding ‘.8base’ to the encrypted files. However, the structure of the appended segment remains consistent with Phobos, featuring an ID section, an email address, and the file extension.
As a result, although it is difficult to draw a very specific target table today, we can get a few ideas if we look at 8Base’s example.
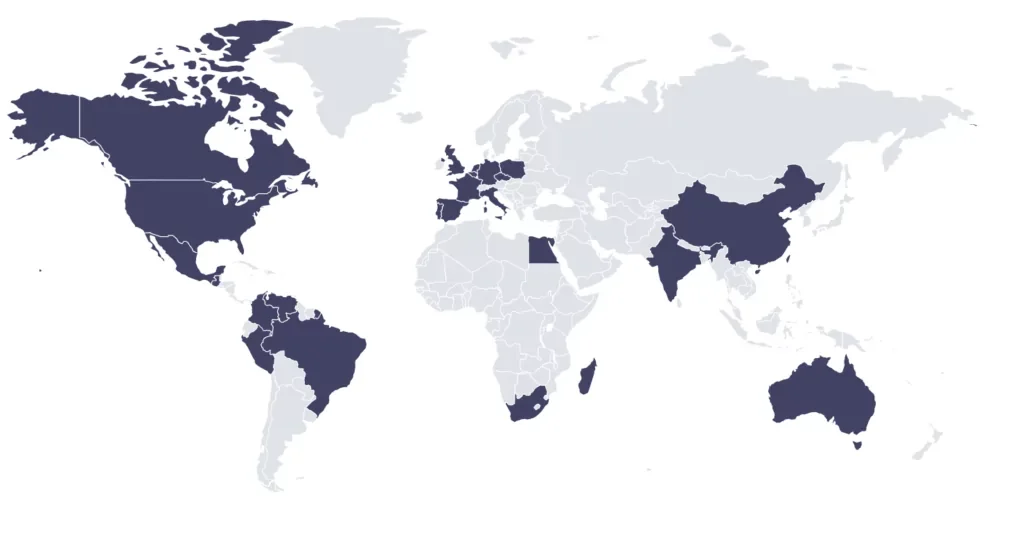
8Base’s target countries
Although we see that the Western hemisphere is more affected in this map, where Russia and former USSR countries are excluded, there is no very specific targeting other than the US.
How Phobos Infiltrates Data
As CISA suggests, Phobos is likely associated with multiple variants like Elking, Eight, Devos, Backmydata, and Faust ransomware due to similar Tactics, Techniques, and Procedures (TTPs) observed in Phobos attacks. It operates alongside accessible open source tools such as Smokeloader, Cobalt Strike, and Bloodhound, making it a preferred choice for many threat actors due to its adaptability across different environments.
Initial Access
Phobos attackers commonly gain entry into vulnerable networks through phishing campaigns to deliver hidden payloads or by employing IP scanning tools like Angry IP Scanner to identify susceptible Remote Desktop Protocol (RDP) ports. They also leverage RDP in Microsoft Windows environments. Upon discovering an exposed RDP service, they utilize open source brute force tools to gain access. Successful authentication leads to reconnaissance activities, creating victim profiles, and establishing remote access within compromised networks. Alternatively, they deploy spoofed email attachments containing hidden payloads like SmokeLoader to initiate infection.
Execution and Privilege Escalation
Phobos actors execute commands such as 1saas.exe or cmd.exe to install additional Phobos payloads with elevated privileges. They leverage Windows command shell capabilities for system control and utilize Smokeloader in a three-phase process for payload decryption and deployment, ensuring evasive actions against network defenses.
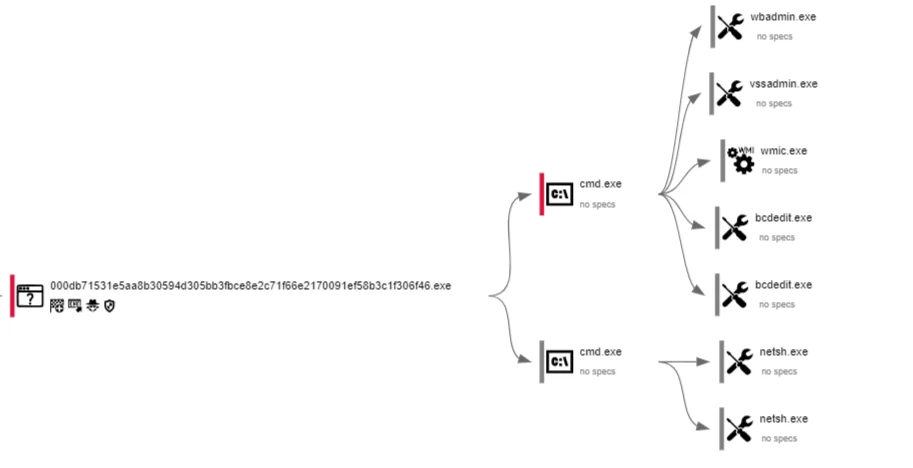
Additional payloads are dropped or installed(Sample analysis in Any.run)
Defense Evasion and Persistence
To evade detection, Phobos ransomware modifies firewall configurations, utilizes evasion tools like Universal Virus Sniffer and Process Hacker, and employs techniques such as token theft and privilege escalation through Windows API functions.
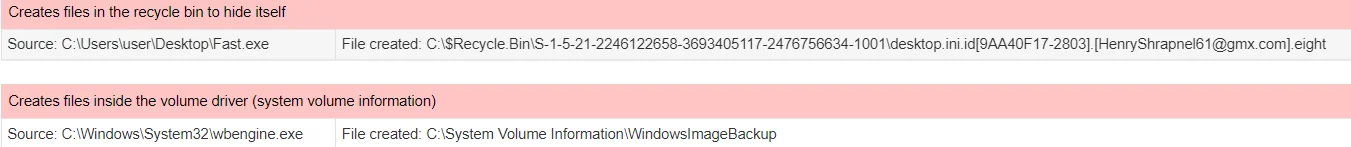
It also maintains persistence through methods like Windows Startup folders and Run Registry Keys. (Sample analysis in JoeSandbox)
Discovery, Credential Access, and Exfiltration
Phobos actors use tools like Bloodhound and Sharphound for active directory enumeration, Mimikatz for credential extraction, and WinSCP/Mega.io for file exfiltration. They target various data types for exfiltration, including legal, financial, technical, and database files, which are archived and later exported.
- Searches system informations with scripts as:
| Code function: GetTickCount,GetLocaleInfoW,Sleep,Sleep,Sleep,CreateThread,WaitForSingleObject,EnterCriticalSection,LeaveCriticalSection,WaitForMultipleObjects,CloseHandle,EnterCriticalSection,CloseHandle,CloseHandle,DeleteCriticalSection,ReleaseMutex,CloseHandle, |
Impact
After exfiltrating data, Phobos ransomware targets backups by deleting volume shadow copies and encrypts connected drives on the target system.
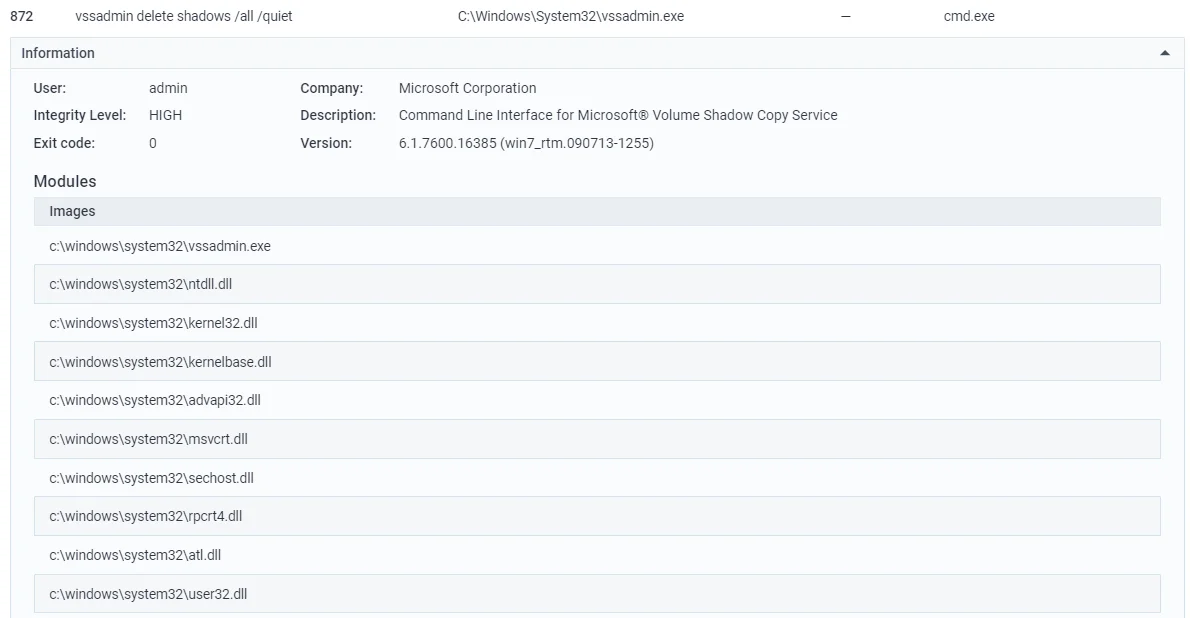
Deleting shadow copies, a classic example of inhibiting system recovery (Sample)
It delivers unique ransom notes and communicates with victims via email, voice calls, and instant messaging platforms, often utilizing onion sites for data hosting and communication.
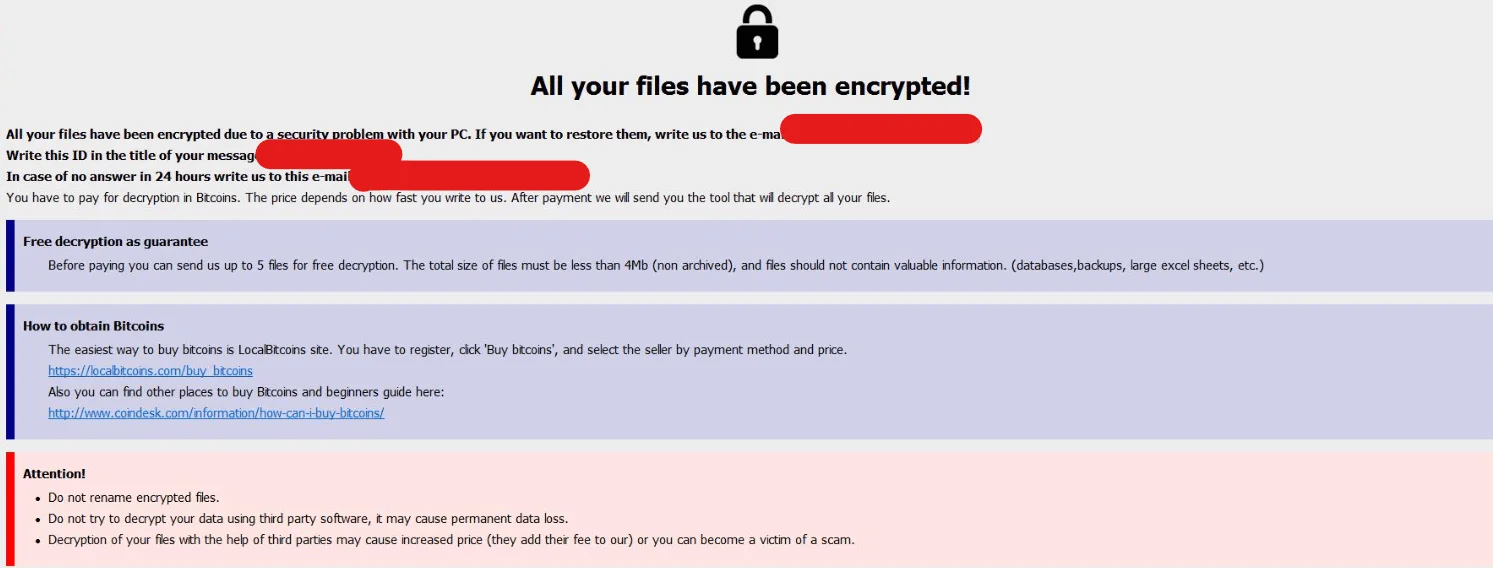
Probos ransom note in a recent sample
Mitigation Advices for Phobos Ransomware
The FBI, CISA, and MS-ISAC urge all critical infrastructure organizations and cybersecurity teams to adopt secure design and default practices. This includes encouraging software developers to integrate secure design principles into their development processes, which can help minimize the impact of ransomware attacks and enhance overall security for their users.
- Secure remote access tools by following recommendations outlined in the Guide to Securing Remote Access Software.
- Employ application controls to manage software execution, including allowing only approved remote access programs.
- Utilize log collection best practices and intrusion detection systems to detect and defend against unauthorized changes to firewall configurations.
- Deploy Endpoint Detection and Response (EDR) solutions to counter threat actors’ memory allocation techniques.
- Minimize the use of Remote Desktop Protocol (RDP) and enforce strict security measures if its usage is unavoidable.
- Enable phishing-resistant multifactor authentication (MFA) for enhanced security.
- Implement robust access controls, audit user accounts regularly, and adhere to the Principle of Least Privilege (PoLP).
- Enhance credential security by placing domain admin accounts in protected users’ groups and avoiding storing plaintext credentials in scripts.
- Develop and maintain a comprehensive recovery plan, including offline backups and multiple copies of critical data in secure locations.
- Ensure compliance with NIST standards for password policies, including using longer passwords, storing passwords securely, and avoiding password reuse.
- Segment networks to contain the spread of ransomware and monitor network activity for abnormal behavior using network monitoring tools.
- Regularly update and enable real-time detection for antivirus software on all devices.
- Disable unused ports and protocols, and consider implementing email banners and disabling hyperlinks in external emails.
- Encrypt all backup data, ensure its immutability, and cover the entire data infrastructure.
How Can SOCRadar Help?
SOCRadar provides robust protection against Phobos ransomware variants. Our proactive threat monitoring and intelligence solutions are designed to bolster your organization’s security posture. With our platform, you can actively monitor and analyze specific threat actors, gaining valuable insights into their strategies, targeted vulnerabilities, affiliations, and signs of compromise. This proactive approach empowers you to anticipate and respond to potential threats effectively, safeguarding your critical assets.
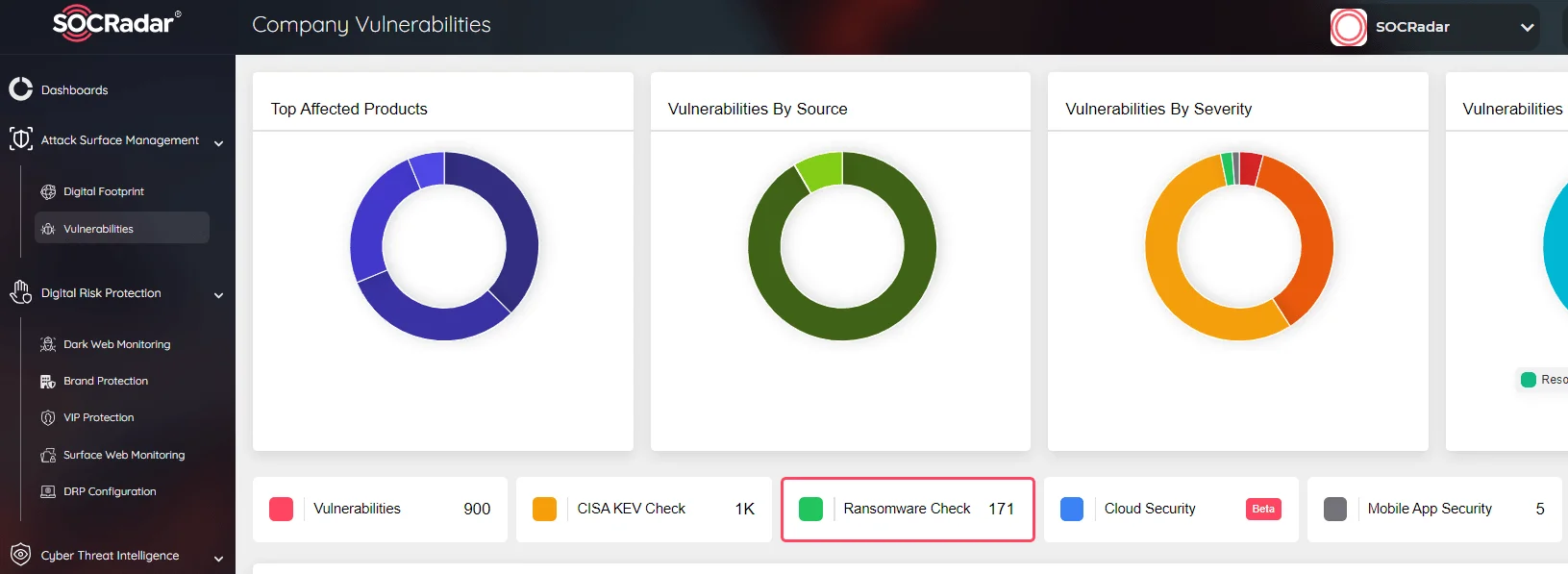
SOCRadar’s Attack Surface Management Ransomware Check
In addition, our Attack Surface Management module includes a Ransomware Check function, enabling continuous monitoring of all potential attack vectors. This ensures that you receive immediate alerts about any suspicious activities related to ransomware. By staying vigilant against threats, you can quickly respond and strengthen your cybersecurity defenses, reducing the risk posed by Phobos ransomware and other emerging threats.
MITRE ATT&CK Table for Phobos Ransomware
| Technique Title | ID | Use |
| Reconnaissance | ||
| Search Open Websites/Domains | T1593 | Phobos actors perform open source research to create a victim profile. |
| Scanning IP Blocks | T1595.001 | Phobos actors use IP scanning tools to search for vulnerable RDP ports. |
| Phishing for Information | T1598 | Phobos actors use phishing campaigns to gain access to vulnerable RDP ports. |
| Resource Development | ||
| Establish Accounts | T1585 | Phobos actors establish accounts for communication. |
| Obtain Capabilities: Tool | T1588.002 | Phobos actors use open source tools in their attacks. |
| Initial Access | ||
| Valid Accounts | T1078 | Phobos actors create victim profiles post-RDP authentication. |
| External Remote Services | T1133 | Phobos actors leverage external-facing remote services. |
| Phishing: Spearphishing Attachment | T1566.001 | Phobos actors use spoofed email attachments for attacks. |
| Execution | ||
| Windows Management Instrumentation | T1047 | Phobos actors use WMIC to prevent file recovery. |
| Windows Command Shell | T1059.003 | Phobos actors perform commands with Windows shell functions. |
| Native API | T1106 | Phobos actors use open source tools to enumerate Active Directory. |
| Malicious File | T1204.002 | Phobos actors use malicious email attachments. |
| Persistence | ||
| Registry Run Keys / Startup Folder | T1547.001 | Phobos ransomware uses Exec.exe and Windows Startup folders/Registry Run Keys. |
| Privilege Escalation | ||
| Privilege Escalation | TA0004 | Phobos actors deploy additional payloads with escalated privileges. |
| Portable Executable Injection | T1055.002 | Phobos actors use Smokeloader for code injection. |
| Asynchronous Procedure Call | T1055.004 | Phobos ransomware makes calls from identified entry points. |
| Access Token Manipulation: Token Impersonation/Theft | T1134.001 | Phobos actors steal tokens using Windows API functions. |
| Create Process with Token | T1134.002 | Phobos actors create new processes using stolen tokens. |
| Defense Evasion | ||
| Software Packing | T1027.002 | Phobos actors deploy portable executables to conceal code. |
| Embedded Payloads | T1027.009 | Phobos actors embed ransomware as hidden payloads. |
| Deobfuscate/Decode Files or Information | T1140 | Phobos ransomware decrypts information during execution. |
| System Binary Proxy Execution: Mshta | T1218.005 | Phobos actors use Mshta for malicious file execution. |
| Impair Defenses | T1562 | Phobos actors use various tools to evade detection. |
| Disable or Modify System Firewall | T1562.004 | Phobos ransomware modifies system firewall configurations. |
| Credential Access | ||
| OS Credential Dumping: LSASS Memory | T1003.001 | Phobos actors use Mimikatz for credential dumping. |
| OS Credential Dumping: Cached Domain Credentials | T1003.005 | Phobos actors use cached domain credentials for authentication. |
| Brute Force | T1110 | Phobos actors may use brute force techniques for access. |
| Credentials from Password Stores | T1555 | Phobos actors search for credentials in password storage. |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 | Phobos actors export browser client credentials. |
| Credentials from Password Stores: Password Managers | T1555.005 | Phobos actors target password management software. |
| Discovery | ||
| Process Discovery | T1057 | Phobos ransomware runs processes. |
| System Information Discovery | T1082 | Phobos ransomware enumerates connected storage devices. |
| File and Directory Discovery | T1083 | Phobos ransomware discovers files and directories. |
| Domain Account | T1087.002 | Phobos threat actors enumerate Active Directory. |
| Collection | ||
| Archive Collected Data | T1560 | Phobos actors archive data for exfiltration. |
| Command and Control | ||
| Data Obfuscation: Protocol Impersonation | T1001.003 | Phobos actors obfuscate C2 activity. |
| File Transfer Protocols | T1071.002 | Phobos actors use WinSCP for file transfer. |
| Ingress Tool Transfer | T1105 | Phobos ransomware extracts final payloads. |
| Remote Access Software | T1219 | Phobos threat actors establish remote connections. |
| Exfiltration | ||
| Exfiltration | TA0010 | Phobos threat actors exfiltrate data. |
| Exfiltration Over Alternative Protocol | T1048 | Phobos threat actors use alternative protocols for exfiltration. |
| Exfiltration to Cloud Storage | T1567.002 | Phobos threat actors use Mega.io for cloud exfiltration. |
| Impact | ||
| Data Encrypted for Impact | T1486 | Phobos threat actors encrypt data on logical drives. |
| Inhibit System Recovery | T1490 | Phobos threat actors inhibit system recovery efforts. |
| Financial Theft | T1657 | Phobos threat actors engage in financial extortion. |