
Latest Dark Web Findings: Discord Credentials, Orange Customer Records, and Australian Bank Data
Once again, hacker forums are filled with new cyber threats, with SOCRadar’s Dark Web Team identifying several alarming activities this week. Notable findings include the sale of alleged bank account credentials from major Australian banks and a phishing database targeting Discord users. Additionally, a hacker claims to have leaked a database from Orange Romania, exposing customer records and internal documents. Other concerning discoveries include a breach of HighWire Press, compromising millions of academic and institutional records, and the launch of a new illicit marketplace specializing in stolen personal and financial data.
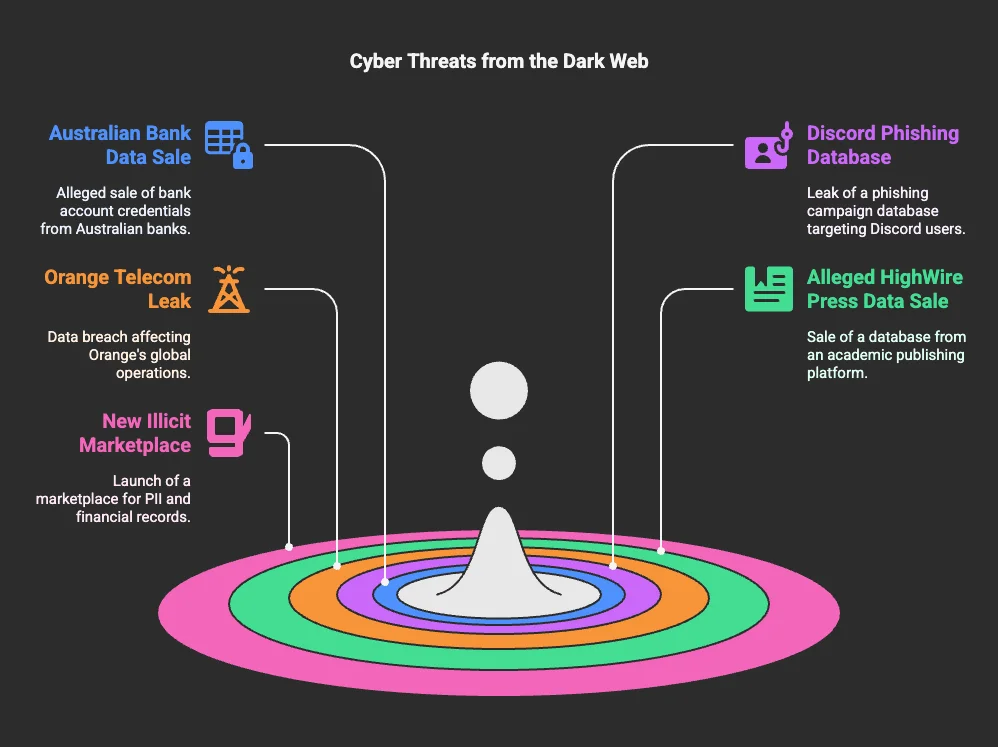
SOCRadar Dark Web News: Key highlights of this week’s detected threat actor activities
Receive a Free Dark Web Report for Your Organization:
Alleged Accounts of Australian Banks are on Sale
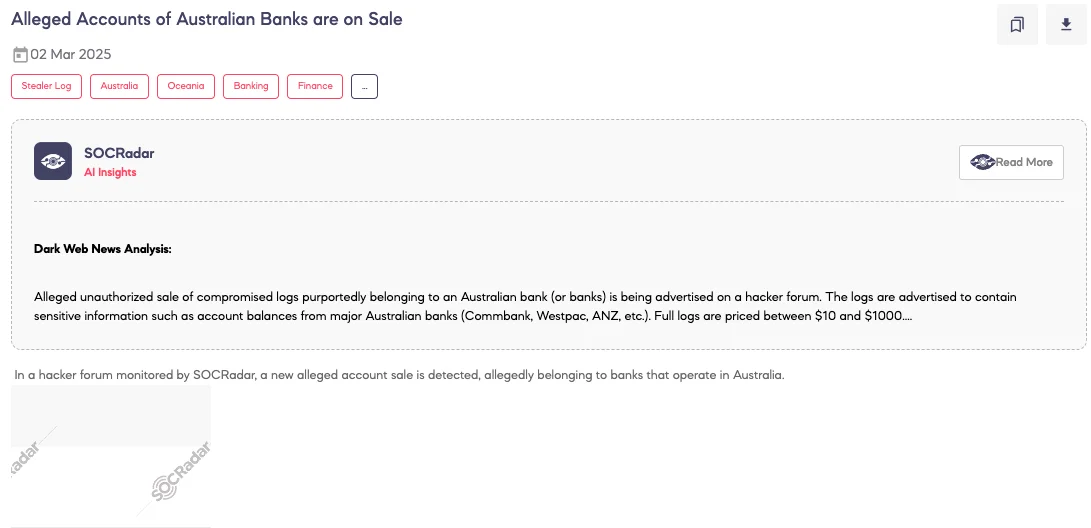
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling bank account credentials allegedly belonging to Australian financial institutions. According to the threat actor’s statements, the dataset includes accounts from Commonwealth Bank (CommBank), Westpac, ANZ, and other banks, with account balances included. The price varies between $10 and $1,000, depending on the account details, and the seller provides private messaging for inquiries.
The Alleged Phishing Database of Discord is Leaked
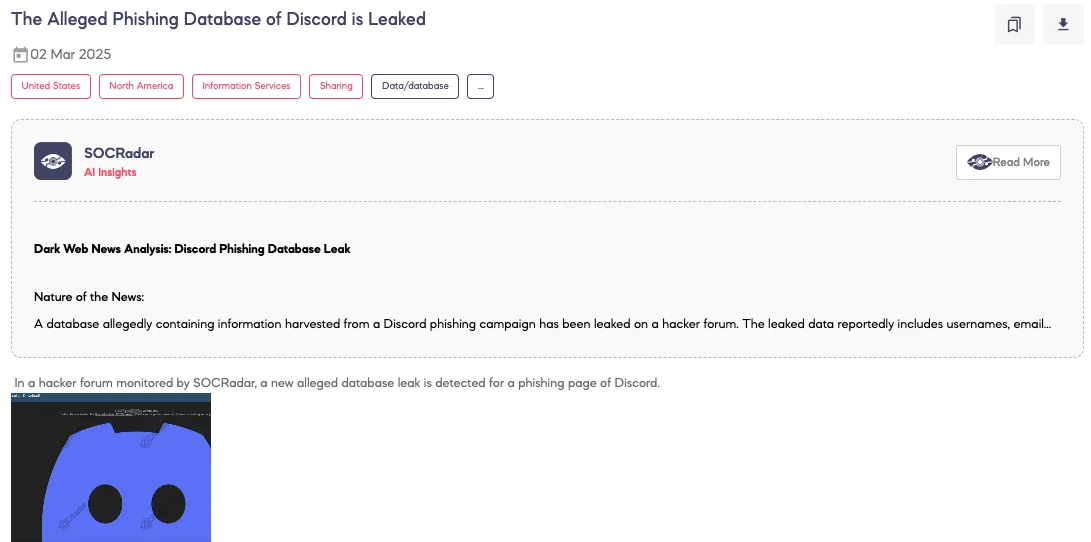
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked a phishing database allegedly targeting Discord users. The dataset, reportedly from a February 2025 phishing campaign, contains 16,393 records with usernames, email addresses, passwords, tokens, and phone numbers.
Additionally, phishing remains a significant cybersecurity threat, leveraging AI-driven deception techniques and deepfake technologies to compromise individuals and organizations. According to the SOCRadar 2024 End of the Year Threat Report, phishing campaigns in 2024 targeted over 576,100 unique websites, leading to the detection of 2.9 million malicious domains and 31,746 fake login pages, highlighting the growing scale and sophistication of these attacks.
SOCRadar’s Takedown Activity Management dashboard offers real-time takedown metrics, domain tracking, and content removal in one interface.
SOCRadar’s AI-enabled Digital Risk Protection platform provides proactive defense by identifying lookalike domains, phishing websites, and SSL-enabled fraudulent sites in real time. With advanced monitoring capabilities and an integrated takedown service, SOCRadar enables organizations to swiftly mitigate phishing threats and protect their digital assets.
Alleged Database of Orange is on Leaked
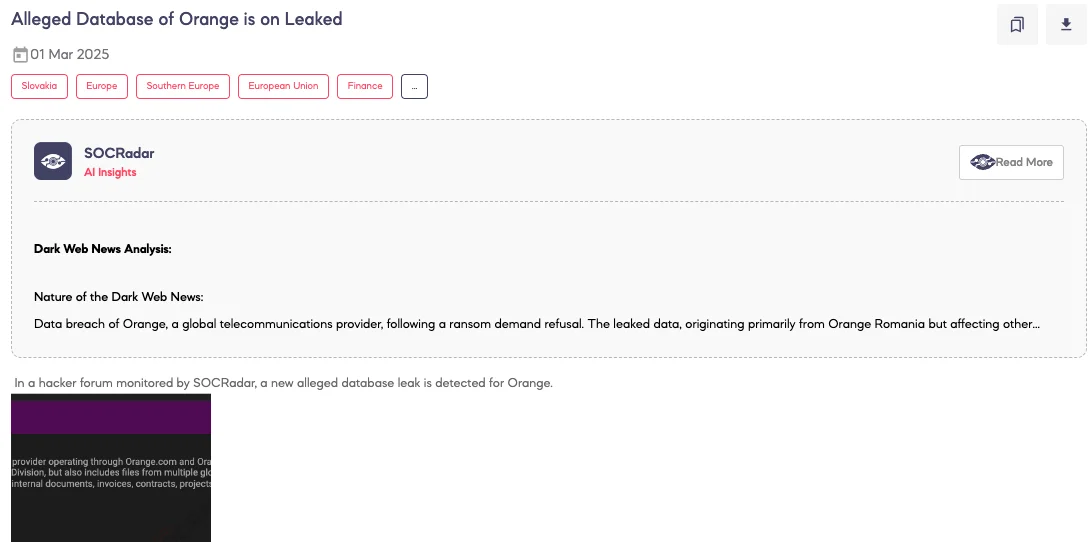
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked a database allegedly belonging to Orange, a leading global telecommunications provider. According to the threat actor’s statements, the breach occurred in February 2025, primarily affecting Orange Romania, with additional data allegedly sourced from multiple global divisions. The leaked dataset reportedly contains over 600,000 customer records, including 380,000 unique email addresses, as well as source codes, internal documents, invoices, contracts, employee data, and project details.
The threat actor, identified as Rey, asserts that they maintained access to Orange’s systems for over a month by exploiting compromised credentials and vulnerabilities in Jira software. The actor claims to have exfiltrated approximately 6.5GB of data within a three-hour window before detection. Furthermore, the post states that a ransom demand was issued but not met, leading to the subsequent data leak.
Orange confirmed the cyber incident to BleepingComputer, clarifying that the breach impacted a non-critical back-office application and did not affect customer operations. The company has initiated an internal investigation and is collaborating with relevant authorities to assess the scope of the breach and mitigate its impact.
The Alleged Database of Highwire Press is on Sale
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a database allegedly belonging to HighWire Press, a digital publishing platform specializing in academic and scholarly content. According to the threat actor’s statements, the breach occurred on February 25, 2025, compromising nearly 26 million records, including 6.5 million unique email addresses from universities, schools, medical centers, and other organizations that use HighWire Press services
The leaked dataset allegedly contains subscriber details, institutional data, internal documentation, and user information, structured in various database files. The threat actor claims that they attempted to contact HighWire Press to request payment before making the data public.
A New Marketplace is Detected
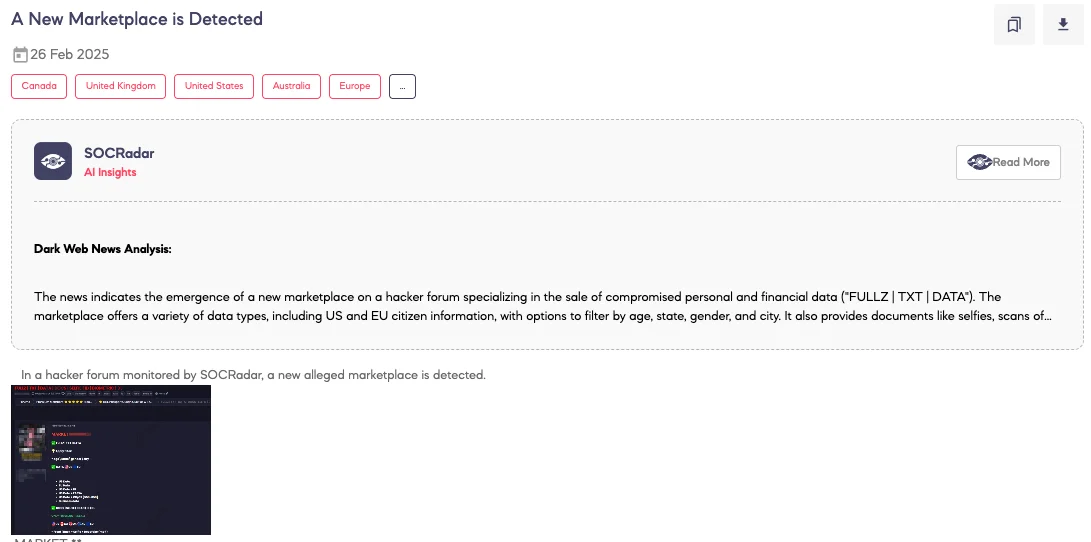
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have launched a new illicit marketplace specializing in Personally Identifiable Information (PII), identity documents, and financial records. According to the threat actor’s statements, the marketplace offers:
- Full identity profiles (Fullz) with filtering options by age, state, gender, and city
- U.S. and EU datasets, including driver’s licenses (DL), FAFSA records, and credit scores.
- Business-related data
- Identity documents, such as ID scans, selfies, deepfake-generated videos, social security numbers, and medical records
The marketplace claims to provide fresh data that has not been resold, with support available in Russian and English. Transactions are facilitated through Telegram and Session, and the platform operates according to New York time (3:00 AM – 5:00 PM).
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































