
DNSBomb: A New DoS Threat Targeting Critical Internet Infrastructure

Illustrative Image – Generated by DALL-E
Introduction
As the digital landscape continues to change, so does the doom on the infrastructure. This revolution of the digital landscape has been epitomized by the identification of a new threat to the internet infrastructure in the form of Distributed Denial of Service (DDoS) attacks; to be precise, one that was discovered by Tsinghua University researchers that manipulates DNS traffic—dubbed DNSBomb. The attack vector identified by the manipulators was threatening important internet systems.
How DNSBomb Works
DNSBomb leverages the recursive nature of DNS resolvers to amplify traffic up to the exponential level. Such an attack is one where the attacker forges malevolent DNS queries that, in effect, become giant traffic flows straight to the systems under attack.
The following is an explanation of how DNSBomb operates:
- Recursive DNS Reflection Attack: This means an attack where attackers can reflect their malicious DNS queries off DNS resolvers across the entire network.
- Traffic Amplification: It is the recursive nature of the query; it amplifies traffic distribution to 8.7 Gbps, flooding the targeted infrastructure.
- Target Systems: The most vulnerable components are the DNS servers and Content Delivery Networks, which aggregate and distribute traffic across the internet.
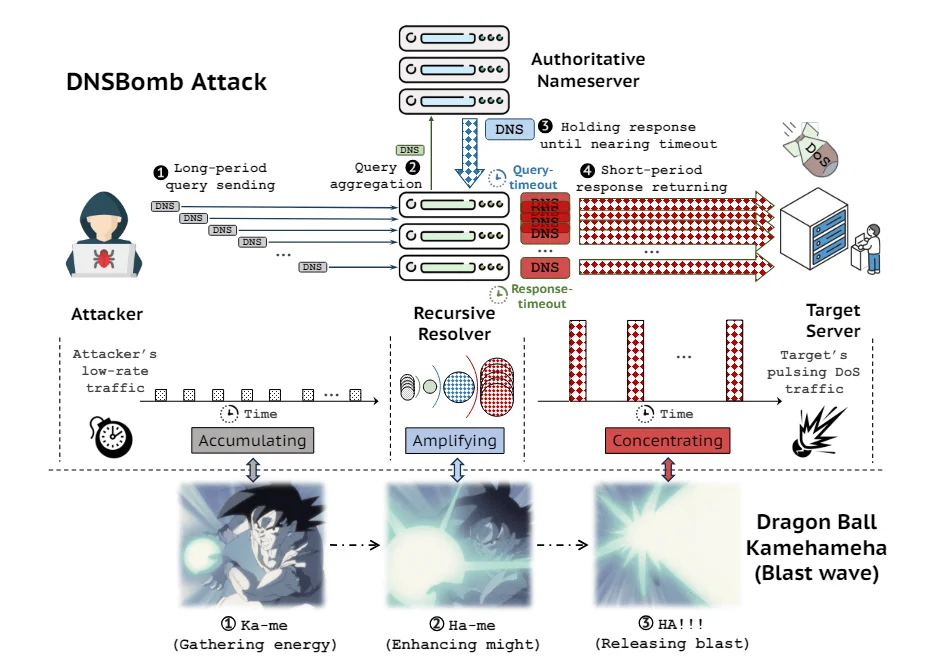
How DNSBomb Attack Works – Source: xakep.ru
Technical Analysis
Query Crafting
This means that very well-crafted DNS queries are used to exploit the recursive nature of DNS resolvers. Through the manipulation of the authority and response sections of DNS queries, the attackers create an amplification effect process, raising the volumes in a big way.
Amplification Factor
It’s experimentally verified by Tsinghua University researchers that all DNS resolvers on the Internet are vulnerable to abuse that could be exploited to launch much more effective and efficient DNSBomb attacks than previous pulsing DoS attacks. Small-scale experiments show a peak pulse magnitude that can approach 8.7 Gbps in volume and a bandwidth amplification factor that could exceed 20,000x.
Impact Metrics
- Traffic volume: Up to 8.7 Gbps — more than enough to cripple even the most robust infrastructures.
- Service degradation: The attack will lead to significant losses of packets and latency, eventually resulting in reduced service quality delivered to end-users.
- Operational Disruption: The DNS servers and CDNs getting defaced have seen instances of operational failures, and in turn, a great number of services depending on these infrastructures have also come to a standstill.
- Connection Types: The kill is only applicable to both types of stateful and stateless connections, including those of the TCP, UPD, and QUIC types.
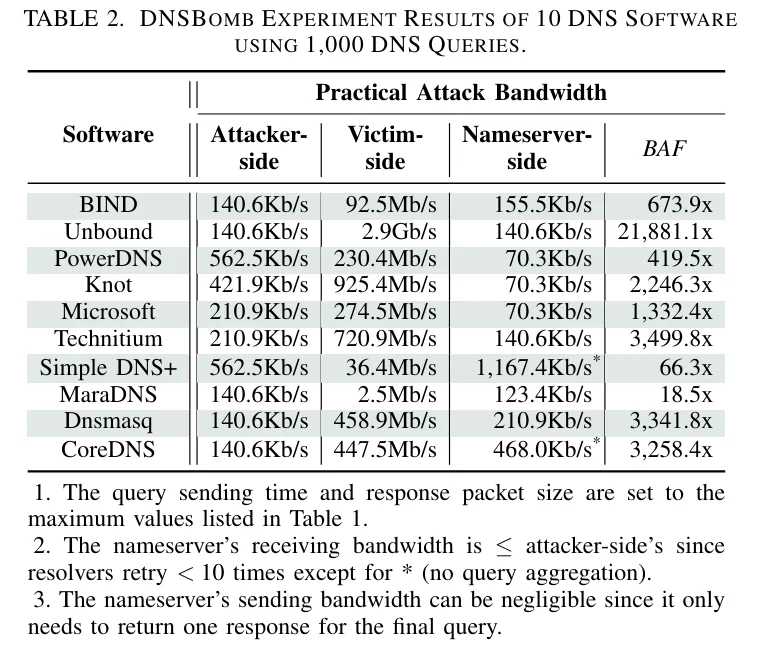
DNSBomb Experiment Result – Source IEEE
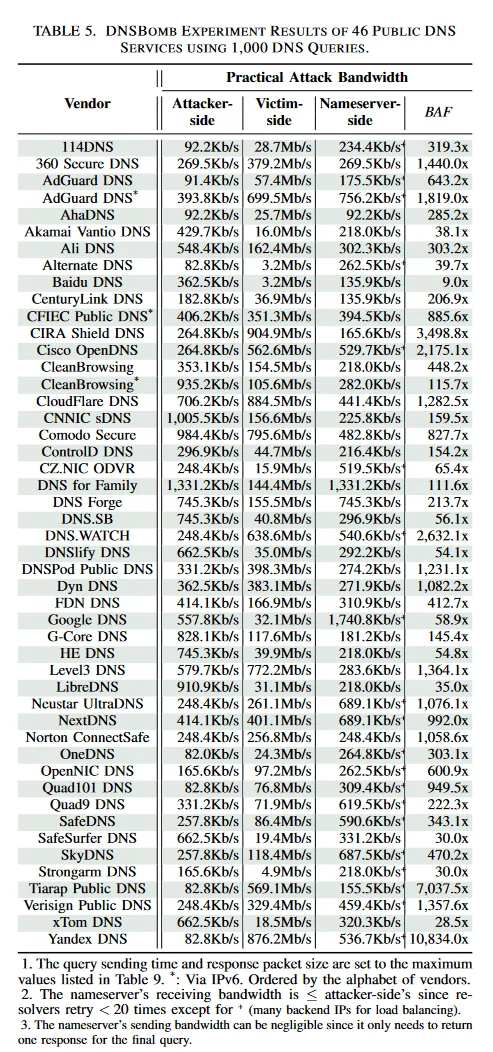
DNSBomb Experiment Result – Source IEEE
Defensive Mechanisms
DNSBomb is an advanced service, to the extent that it requires its defense to be multi-strategy.
- Rate Limiting and Filtering: Implement rate filtering on DNS queries as one of the measures to mitigate the volume of malicious traffic.
- DNS Resolver Security: Hardening should be done in the security parameters of the DNS resolver in a way that it won’t be exploited.
- Regular Updates: A regular updating mechanism by patching the DNS software plays an important role in defense against known vulnerabilities.
Vendor Response
As a result of this work, a series of effective fixes was designed and responsibly disclosed to affected vendors. To date, this work has resulted in acknowledgments by 24 vendors, including the maintainers of BIND, Unbound, PowerDNS, and Knot, all working on code fixes based on the proposed solutions. In total, 10 CVE-IDs were allocated for vulnerabilities discovered as part of this research.
To effectively safeguard against DDoS attacks, it is imperative to grasp their operational mechanisms and analyze the prevailing tactics. You can use the SOCRadar Labs-DOS Resilience tool for free to measure your strength in this situation. The DoS Resilience Service allows you to check your domain’s or subnet’s resilience against DoS attacks. After determining your strengths and weaknesses from DOS Resiliency, you can use the SOCRadar Attack Surface Management module, no matter what action you must take.
SOCRadar DoS Resilience Module
You can visit our blog post for more information on DDoS attacks and mitigation methods.
Conclusion
DNSBomb is a significant leap in the technique of carrying out process attacks and has not only the potential to threaten critical internet infrastructure but also to draw quite some focus around it. It will, therefore, be better to protect, through technical understanding and the adoption of solid defense approaches, the information systems of organizations. If anything, it behooves one to keep the foot heavy on staying up to date with industry changes, as the sum of all fears is the disruption to our digital systems’ integrity and reliability.




































