
Don’t be Blinded by What You See: Demystifying Homograph Attacks
From Nigerian Princes to Crafty Codes: The Evolution of Phishing
Remember the days when our inboxes were graced by those endearing messages from a distant “Nigerian Prince”? Ah, good times, right? If you’re thinking, “What in the world is this person talking about?”—well, those were some of the internet’s early attempts at what we now term as ‘phishing’. Yep, the classic bait-and-hook of the digital sea. Nowadays, these scams look as blatant as a neon sign!
Fast forward to today, and while our Nigerian royalty might have receded into the shadows, the art of the digital deception dance has evolved. The floor now welcomes some sophisticated moves like punycode and homograph attacks.
Intrigued? Good, because while the tactics have changed, our mission remains the same: staying one step ahead of the scammers. Let’s dive in, shall we?
Punycode, Decoded
Ever thought about how cool it would be to have domain names in Arabic, Cyrillic or Chinese? Well, the internet had the same thought. But there was a catch: our Domain Name System (DNS) was all about ASCII and did not really support non-ASCII characters.
Enter Punycode – our knight in ASCII armor. According to Wikipedia, ‘Punycode is a representation of Unicode with the limited ASCII character subset used for Internet hostnames.’ This encoding method allows for the representation of domain names in various scripts while still being compatible with the ASCII-based DNS. And if you see ‘xn--‘ in a domain, that is Punycode doing its thing.
Homograph Attacks, Demystified
Now, this is where things get a bit sneaky. Ever mistaken a ‘g’ for a ‘q’? (Guess, you see qooqle.com in the address bar). Probably not, but on the internet, there are characters from different scripts that look freakishly similar.
A homograph attack is a type of cybersecurity exploit wherein a hacker leverages the fact that many different characters look alike (homographs) across different writing systems. In terms of domains, it involves registering a domain name that visually resembles a legitimate domain by using characters from different scripts or writing systems.
Given the internationalization of domain names (thanks to Punycode), attackers can use similar-looking characters from other scripts. Some cyber tricksters exploit this to make deceptive domain names. Basically, they’re the doppelgangers of the domain world!
Therefore, Punycode is an encoding method that allows non-ASCII characters, like those from Cyrillic or Arabic scripts, to be represented in domain names that are compatible with the ASCII-based DNS system. However, this capability also opens the door for homograph attacks, where attackers use similar-looking characters from different alphabets to create deceptive domain names that appear legitimate but lead to malicious sites.
Example:
Unicode: apple.com (Note: The first letter ‘a’ is from the Cyrillic alphabet and looks very similar to the ASCII ‘a.’)
Punycode: xn–80ak6aa92e.com

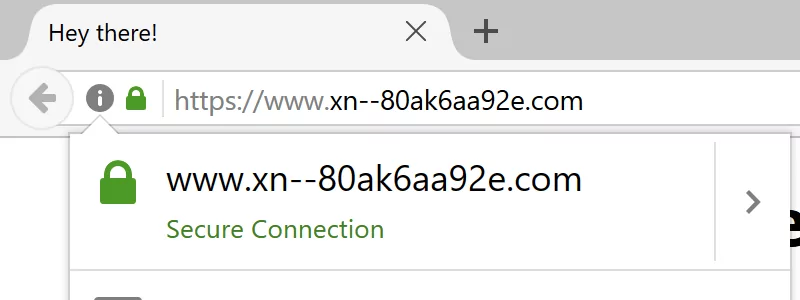
Its evil twin: аpple.com (Notice that first ‘a’? Yup, it is dressed in Cyrillic. Can’t spot the difference? Exactly. That is the whole game.)
So, Punycode is a neutral technology designed to represent non-ASCII characters in domain names, while a homograph attack is a malicious activity that exploits the visual similarities between characters of different scripts, often taking advantage of Punycode’s ability to render internationalized domain names.
Tools to Spot Homograph Attacks
Ready to dive into the realm of detecting those sneaky homograph attacks? Let’s gear up and explore the fantastic tools that will equip us in our epic quest against cyber trickery:
Web Browsers Got Your Back:
Modern browser pals like Chrome, Firefox, and Safari are not just there for your late-night YouTube marathons. They’ve got built-in alerts for when a domain seems like it is playing dress-up with confusing scripts. In certain circumstances, browsers will display the Punycode version of the domain instead of the Unicode version to alert the user. Sneaky, right?
Modern browsers have implemented checks against homograph attacks. They often display the Punycode version of a domain instead of the internationalized version if they detect a potential mix of scripts, making it clear to a user that something might be amiss.
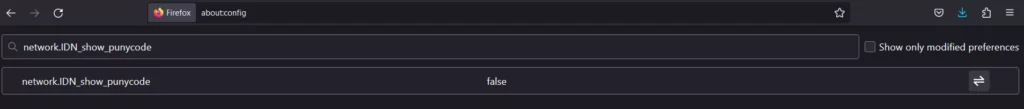
Ever wondered why browsers have not completely solved this problem? Well, the answer is quite straightforward: not all languages use the Latin alphabet. If browsers displayed every domain name in Unicode, it could create a lot of confusion for many users. However, if you are interested in always being able to spot punycode in domain names, there is a neat trick for Firefox users. Just type about:config in the address bar, find the optionnetwork.IDN_show_punycode, and switch it to true. No more decoding puzzles!
Peeking into Certificate Transparency (CT) Logs:
CT logs are public records of SSL/TLS certificates that have been issued. By monitoring these logs, organizations can spot potentially malicious domains that are visually like their own legitimate domains. Tools like Facebook’s CT monitor and Certificate Transparency project act like your magnifying glass here.
SSL/TLS Certificates:
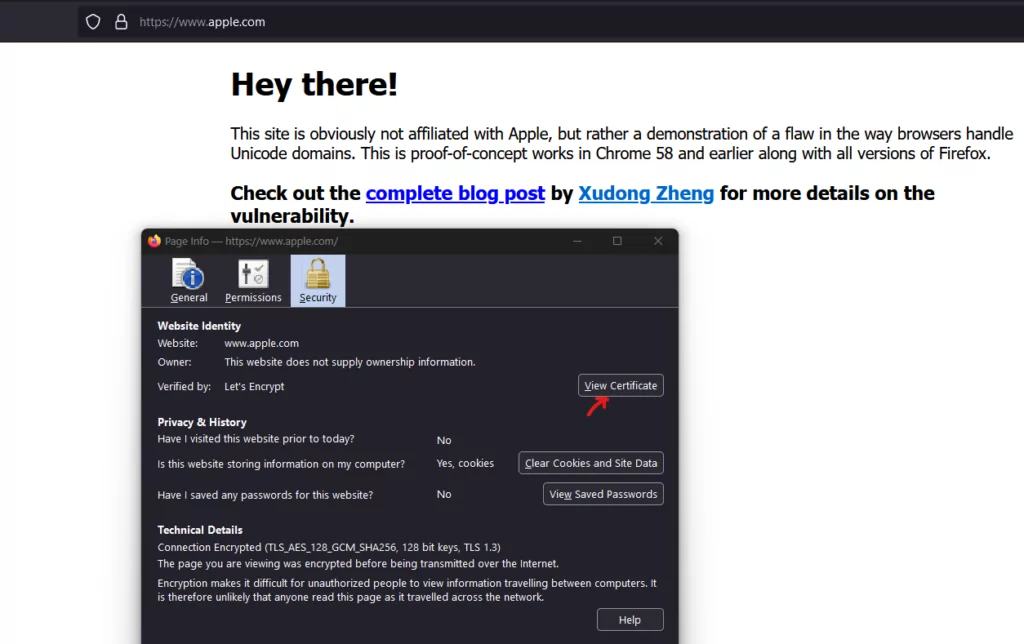
If a user is trained to look for secure indicators, like the padlock icon in the address bar indicating a valid SSL/TLS certificate, they can be more certain they are on the legitimate site. While not foolproof (since attackers can also obtain SSL/TLS for their malicious domains), it adds an additional layer of trust.
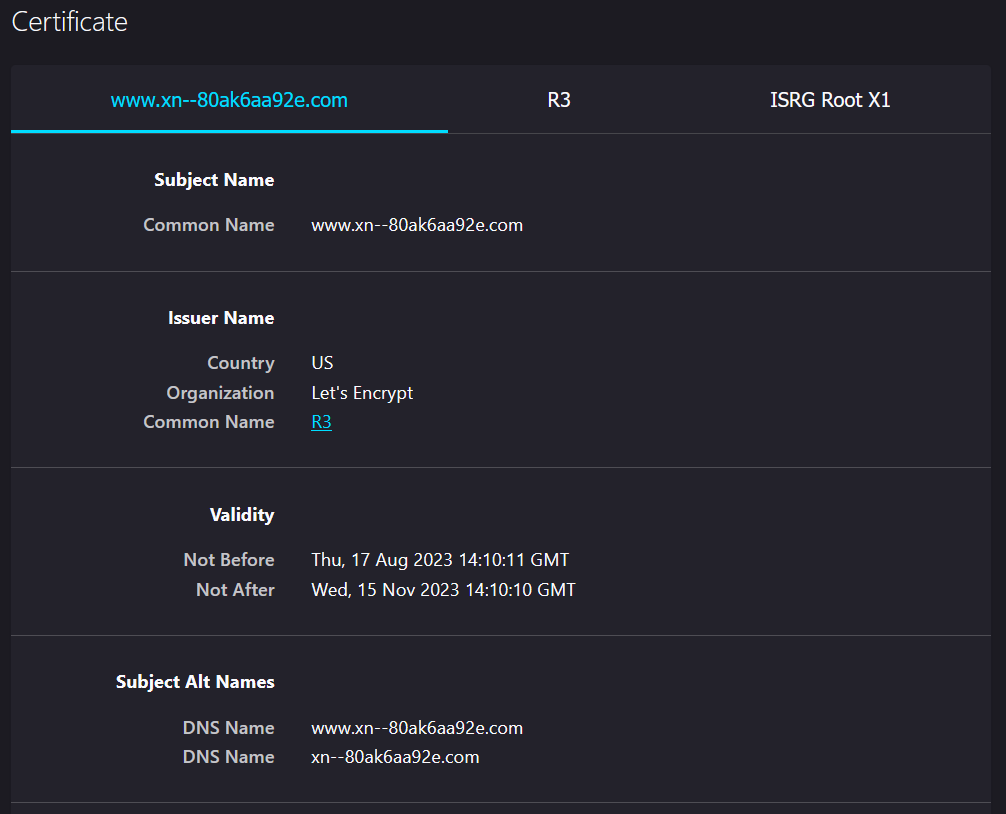
URL Scanners to the Rescue:
Tools like VirusTotal allow users to input a URL and scan it across multiple databases to check for malicious intent or associations.
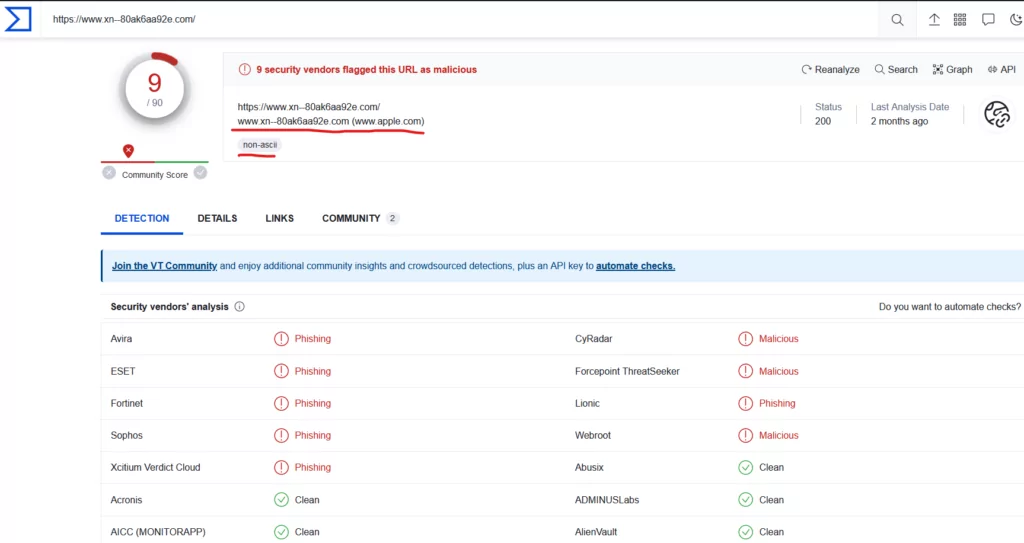
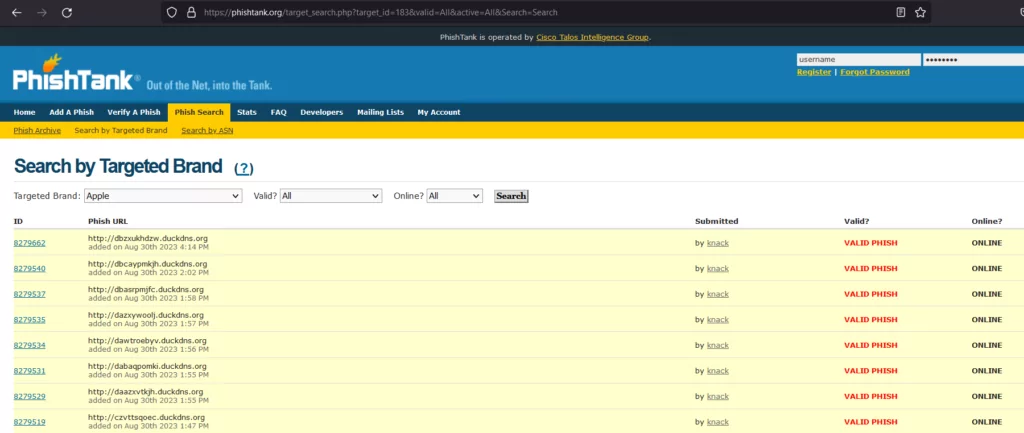
PhishTank’s Sea of Reports:
This is an open community that reports and verifies known phishing sites. It can be used to check if a suspicious-looking domain has already been reported as a phishing site.
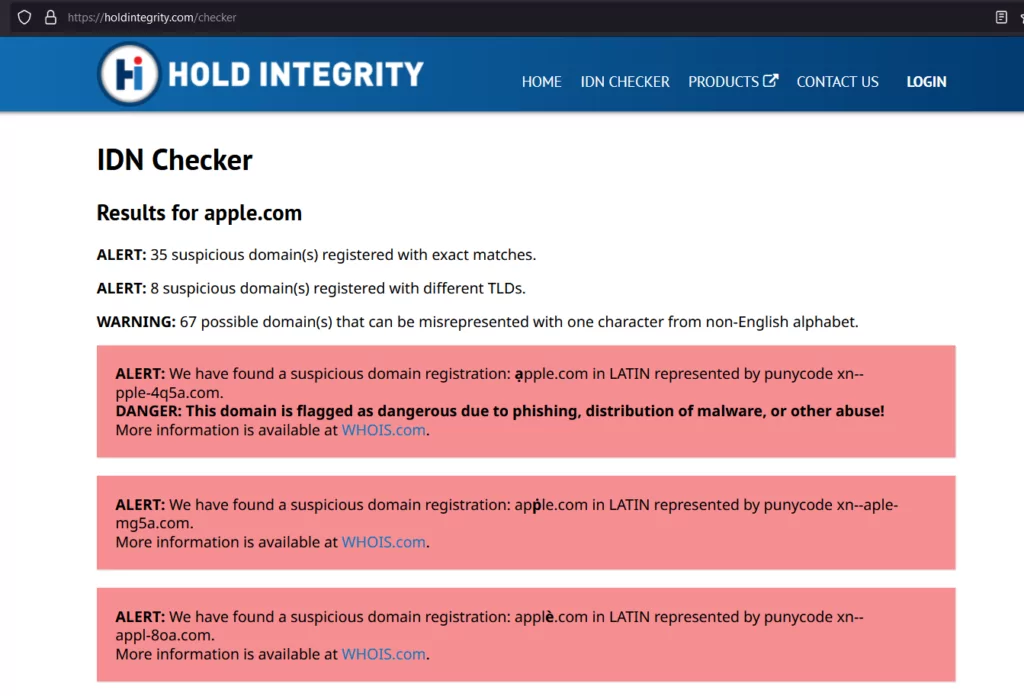
IDN (Internationalized Domain Name) Checker:
This tool allows users to identify potentially deceptive domains for a given domain name by bringing the results for existing or possible impersonations. If there is already an impersonation, additional information may be available from WHOIS data.
Alright, here is the deal: While these tools do pack a punch against our cyber adversaries, none of them don the cape of invincibility. Often, our best defense strategy weaves together these tools, some solid policies, and always keeping our learning game strong.
And if all of this seems a bit overwhelming, there is always a shortcut: SOCRadar and its DPRS suite! With a phishing detection algorithm that is more alert than my cat at 3 AM, it is ready to have your back. Dive into a safer cyber world with SOCRadar, and keep those phishing goons at bay.
Network Security Solutions:
Many enterprise network security solutions, like next-generation firewalls and secure web gateways, have features that can detect and block traffic to and from malicious domains. Some might specifically have IDN decoding features to identify potentially misleading Punycode domains.
DNS Filtering: These services, like Cisco Umbrella (formerly OpenDNS) or Quad9, can block access to known malicious domains. They may also have heuristics to identify and block domains that use suspicious character combinations. (like domains which contain Punny codes start with x)
Strengthen the Weakest Link of the Chain: Educate People for Risks
Education and Awareness: Knowing is half the battle. The best defense remains an educated user. Being aware of the possibility of such attacks, and always double-checking the domain in the address bar, especially when entering sensitive information, is crucial.
Use of Password Managers: These tools only auto-fill credentials on recognized URLs, making it less likely for a user to unintentionally enter their credentials on a malicious site.
Bookmarking: Encourage users to bookmark essential sites and access them via bookmarks instead of clicking on links from emails or other sources.
Whitelist, the VIP Club: Consider this as setting up an exclusive club where only known and trusted domain names make the list. Everyone else? They stay outside.
Summing it up, as domain owners in this dynamic digital terrain, you are not just stakeholders; you are gatekeepers. With the many threats lurking around, tools like SOCRadar become essential in your defense arsenal. Equip yourself, fortify your domain, and remember: every domain is not just a name—it is a legacy. Here is to unyielding digital resilience!
SOCRadar: Your Trusty Guardian
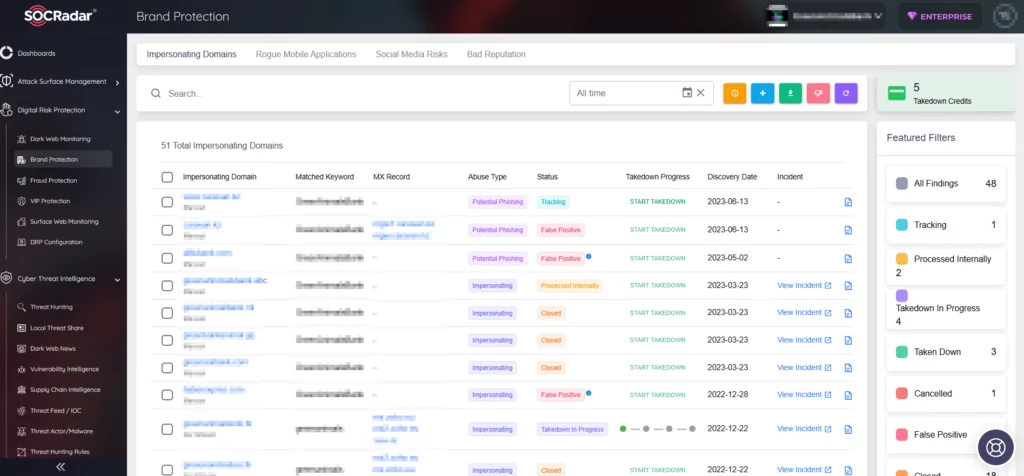
Picture this: You’ve got a domain, and like any proud owner, you want it safe from any digital mischief. Here is where our tech magic steps in. SOCRadar’s algorithm cleverly conjures keywords from your domain name, punycode included, and scours the vast expanses of the internet, hunting for those dubious phishing domains. But wait, it does not bombard you with every find. Oh no, it is smarter than that. Through a harmonious collaboration between AI and our research analysts, the results are meticulously sifted, ensuring what reaches you is of genuine concern. It is like casting a wide fishing net into the digital sea, but then expertly handpicking only the catch that matters.
With SOCRadar, you get the assurance of comprehensive protection with none of the noise. So, sit back and let us do the heavy lifting!



































