
E-Commerce Report: Threat Actors Use HTTPS in 70% of Scams
E-commerce is a fragile industry, opening many doors to various attacks. Phishing is a widespread attack in this industry; in fact, e-commerce is the third most targeted industry for phishing attacks.
Customers of e-commerce sites are especially vulnerable to phishing during this time of the year, according to SOCRadar’s e-commerce report, because of Black Friday campaigns. Customers should be cautious of all kinds of threats during the holiday season.
The full report mentions four key points of attacks in e-commerce: phishing, credit card fraud, gift card/rewards fraud, and credential stuffing.
Click the button below to download SOCRadar E-Commerce Threat Landscape Report.
Phishing Attacks Become More Typical
In e-commerce, phishing is done by emails, messages, phone calls, fake landing websites, fake notifications, and marketing phone calls. It has become a common attack technique, with over 300,000 phishing attacks recorded in December 2021.
One of the helpful graphs in the report displays the total number of potential phishing websites that impersonate various e-commerce websites detected by Phishing Radar.Taobao[.]com, Alibaba[.]com, and Rakuten[.]com are the top three sites scammers have impersonated.
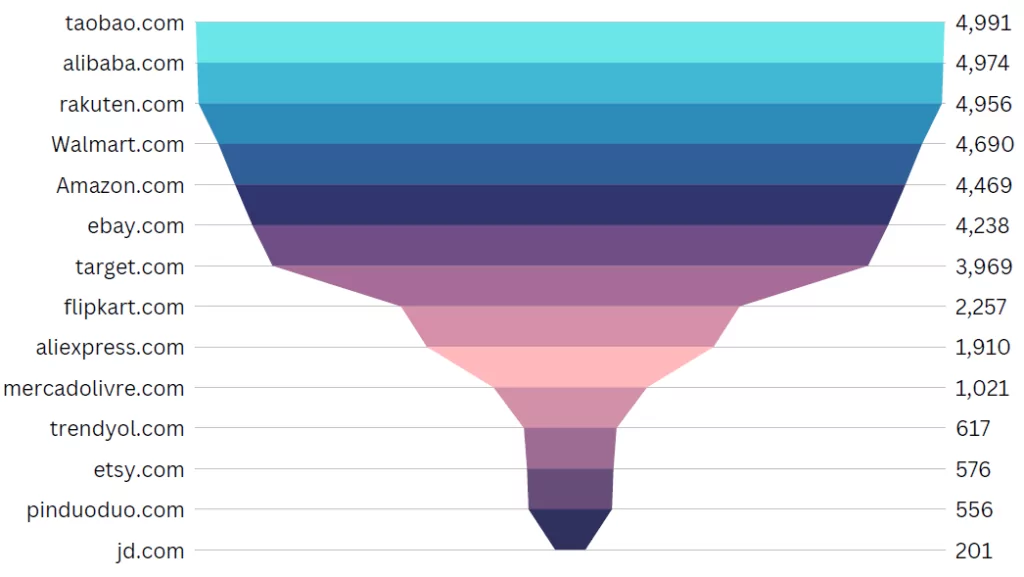
SOCRadar Labs Phishing Radar)
Phishing Radar is a free tool provided by SOCRadar Labs to help detect impersonator sites related to your domain and business.
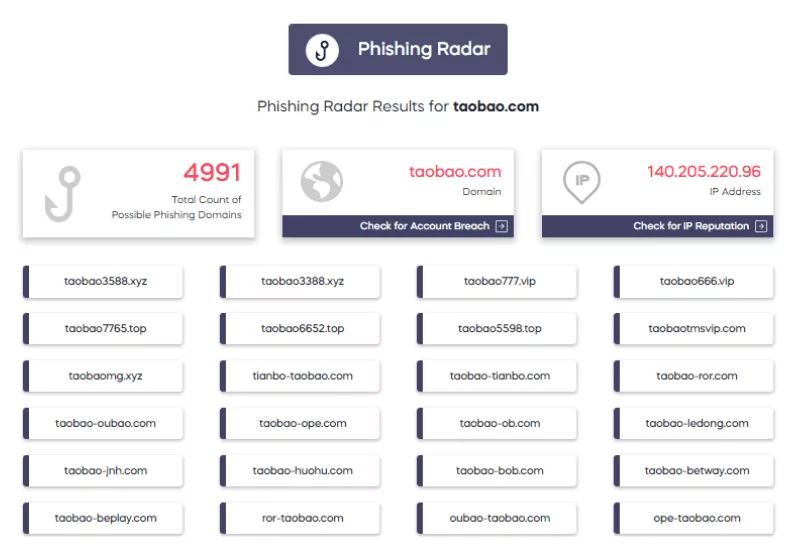
Impersonating phishing sites typically make use of the typosquatting technique to mislead users; threat actors also frequently utilize the top-level domain (TLD) “com” for these sites.
The “com” TLD was designed for commercial entities but is also used for other purposes. On the report, you can find other TLDs.
Threat Actors Favor Certificated URLs
In 2020, nearly 80% of threat actors preferred free registrars for phishing domain registration. However, by 2022, only 32% still did due to the SSL/TLS certificate’s role in convincing users of the website’s security.
Users get a false sense of security when they see HTTPS (the nice padlock sign) at the beginning of the URL. However, as the report shows, in 2022, the threat actors adopted HTTPS at a rate of almost 70%.

































