
EU & US Credit Cards, 750M Indian Mobile Data at Risk; Subway Hit by LockBit
The SOCRadar Dark Web Team identified critical incidents in the cyber threat landscape over the last week. These include the sale of 1,400 European credit cards, the leak of American citizens’ debt data, and the sale of unauthorized RDP access to an Australian freight company. Also, Subway emerges among the latest victims of LockBit 3.0 ransomware, while an alleged sale of 750 million Indian mobile consumer records poses a major data breach concern.
1,400 Credit Cards Belonging to Europe are on Sale
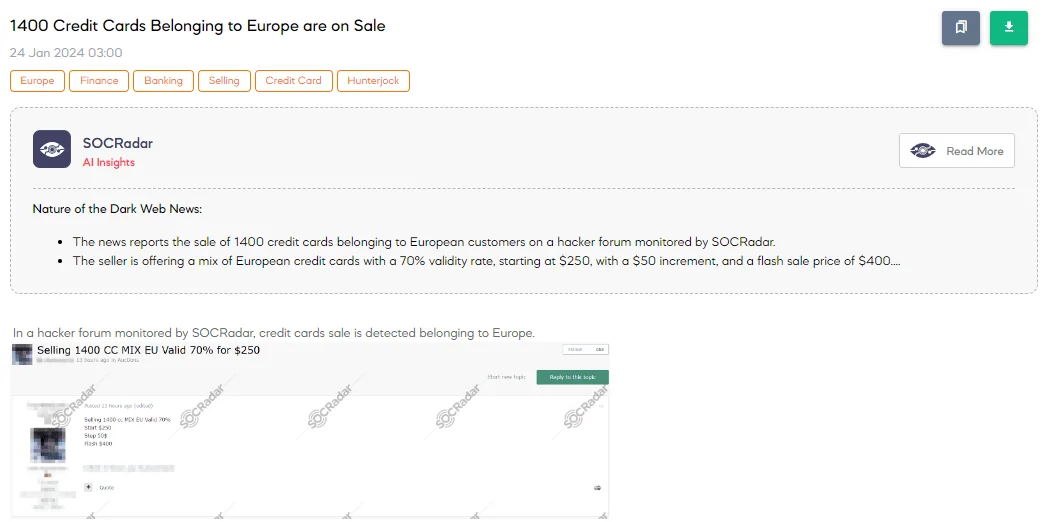
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor is selling 1,400 credit cards allegedly from Europe. The threat actor claims a 70% validity rate for these cards, with a starting price of $250 and incremental increases of $50. They also offer a ‘flash’ sale at $400, indicating a potentially quick, discounted offer.
Debt Data of American Citizens are Leaked
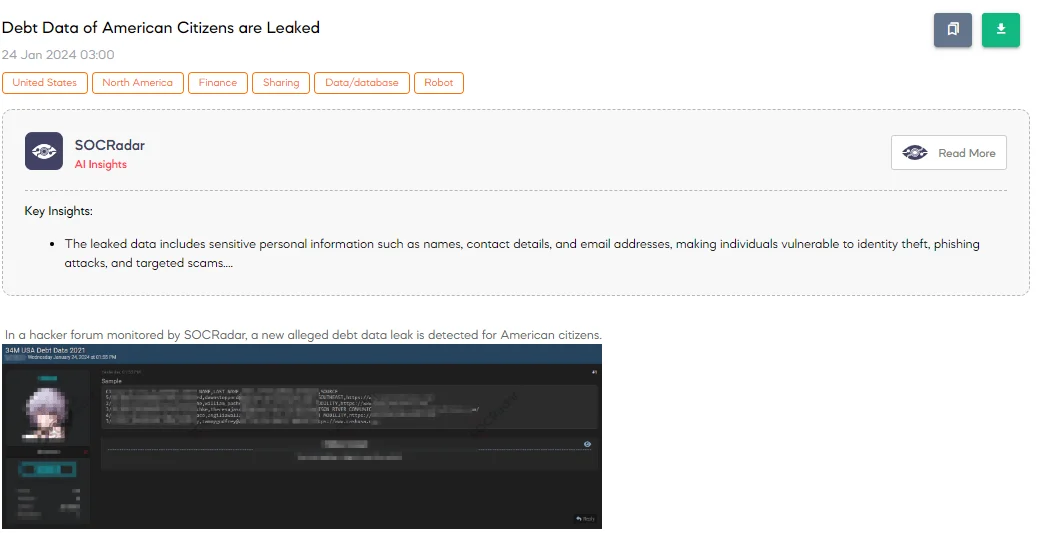
A SOCRadar Dark Web Analyst detected a post on a hacker forum indicating a sale of credit card information allegedly belonging to United States citizens. The threat actor has released sample data to support their claim. This data encompasses various personal details, including the date of interaction (formatted as Year-Month-Day), contact information, first and last names, email addresses, opt-in status, phone numbers, and operating sources. The exposure of this information makes individuals susceptible to identity theft, phishing attacks, and targeted scams.
Unauthorized RDP Access Sale is Detected for an Australian Freight & Logistics Services Company
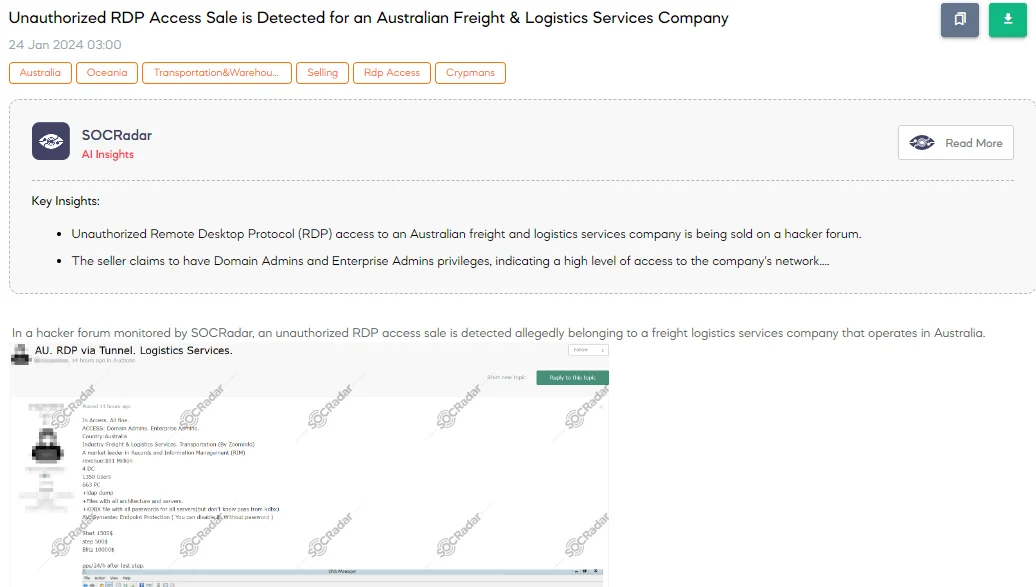
The SOCRadar Dark Web Team has discovered a post on a hacker forum where a threat actor allegedly claims to be selling unauthorized Remote Desktop Protocol (RDP) access to an Australian freight and logistics services company. According to the claim, the access includes high-level privileges like Domain and Enterprise Admins within the company, which is a market leader in Records and Information Management (RIM) and boasts a revenue of $91 million. The package purportedly offers extensive network control, affecting 4 data centers, 1,350 users, and 663 PCs.
Additionally, the sale allegedly includes a Lightweight Directory Access Protocol (LDAP) dump, architectural files of the company, and a KDBX file, an encrypted file format used by KeePass, a cross-platform password manager, containing server passwords, although the KDBX file password is unknown. The actor also claims to be able to disable the company’s Symantec Endpoint Protection without needing a password. The starting price for this unauthorized access is reportedly $1,500, with increments of $500 and a blitz (instant buy) price of $10,000, representing a significant and alarming security threat to the company.
The New Ransomware Victim of LockBit 3.0: Subway
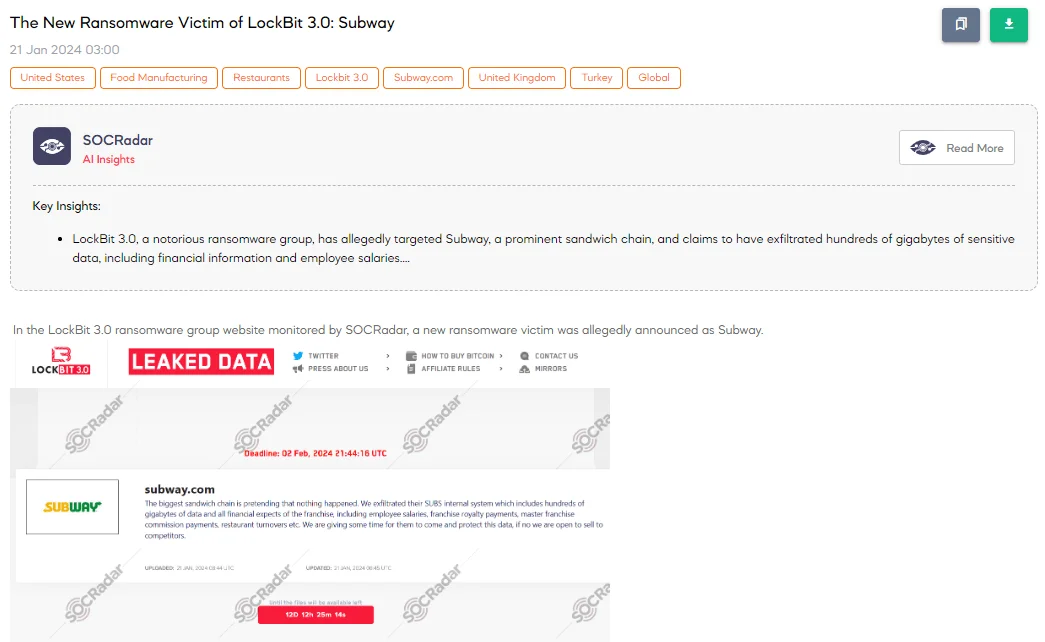
The SOCRadar Dark Web Team has uncovered a post on LockBit 3.0‘s dark web portal, revealing Subway as the latest victim of this ransomware group. The threat actor alleges that Subway ignored the breach despite extracting substantial data from their SUBS internal system. According to the threat actor, This data includes “hundreds of gigabytes” covering all financial aspects of the franchise, such as employee salaries, franchise royalty and commission payments, and restaurant turnovers.
Alleged Sale of 750 Million Indian Mobile Consumer Records Detected
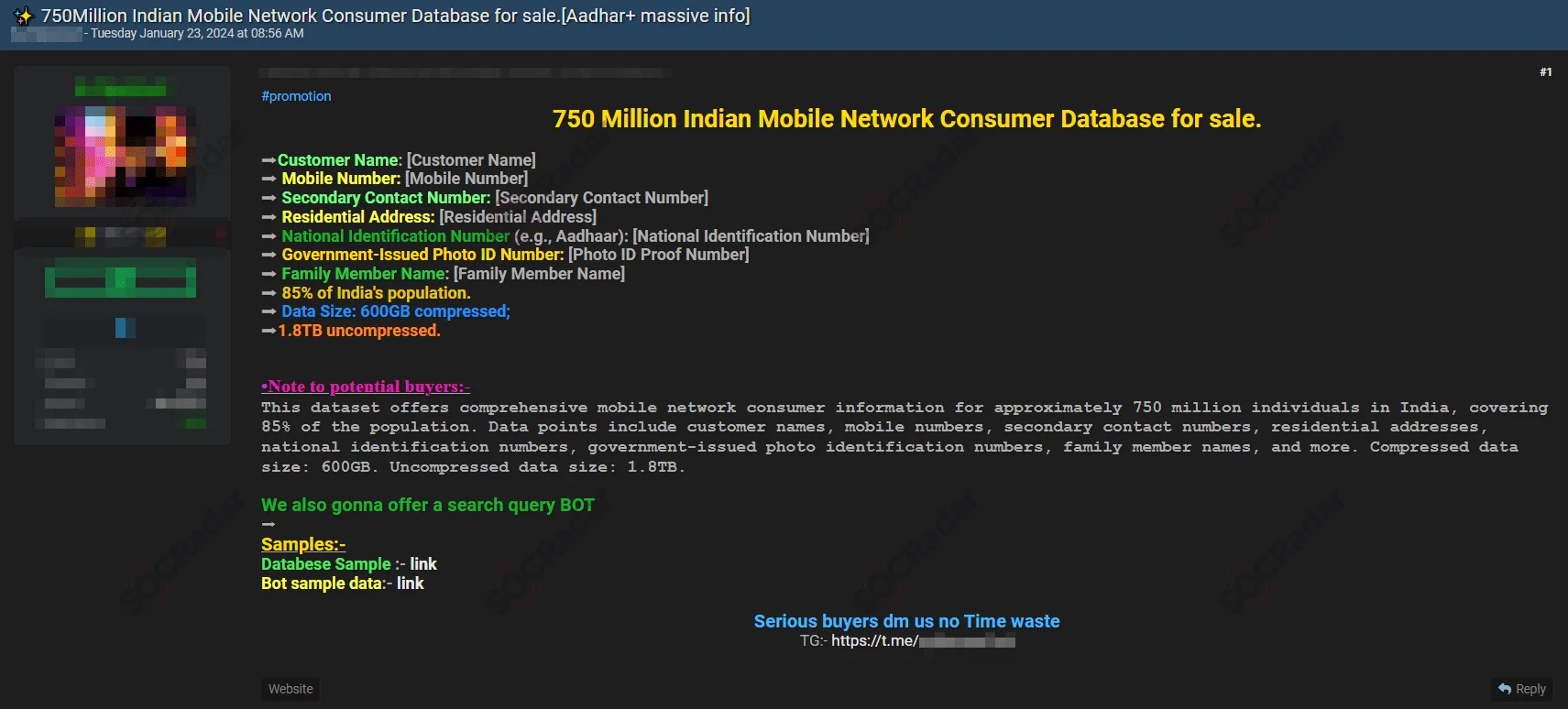
On January 23, a SOCRadar Dark Web Analyst detected a post on a hacker forum alleging the sale of mobile network consumer data in India. The threat actor claims to have a database of 750 million Indian mobile network consumers. The data includes detailed personal information such as customer names, mobile and secondary contact numbers, residential addresses, national identification numbers, government-issued photo ID numbers, and family member names. The dataset is extensive, with a compressed size of 600GB and an uncompressed size of 1.8TB. Additionally, the seller offers a search query bot, emphasizing the comprehensive nature of this data breach.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































