
Exploring Telegram DDoS Groups: Threats, Tools, and Evolving Strategies
Telegram-based hacktivist groups have established themselves as a critical component of the modern cyber threat landscape. These groups, often focusing on Distributed Denial of Service (DDoS) attacks, use the platform to distribute specialized tools, coordinate operations, and recruit participants. From pro-Russian collectives like NoName057(16), utilizing tools such as the DDoSia Project, to pro-Palestinian entities like RipperSec and their MegaMedusa tool, these actors rely heavily on Telegram to execute their campaigns effectively.

Illustration of Telegram DDoS groups (Generated By DALL-E)
DDoS attacks continue to dominate the cyber threat landscape, with their sophistication and scale increasing year by year. According to Cloudflare’s Q2 2024 DDoS Threat Report, there has been a 20% year-over-year increase in the number of DDoS attacks. With over 4 million attacks mitigated in just three months and 10.2 trillion HTTP requests blocked, the report highlights the growing complexity of such attacks, often attributed to advanced tools and tactics. Notably, 1 out of every 25 surveyed organizations reported being targeted by state-level or state-sponsored actors, underlining the seriousness of the threat.
Why Monitoring Telegram DDoS Groups Is Critical
The prevalence of DDoS attacks is fueled by the accessibility of powerful tools and platforms used by hacktivist groups. Many of these actors operate on Telegram, where they coordinate campaigns, recruit participants, and distribute specialized DDoS tools. Groups like NoName057(16), RipperSec, and others not only execute attacks but also provide services and tools that enable even inexperienced individuals to launch disruptive operations.
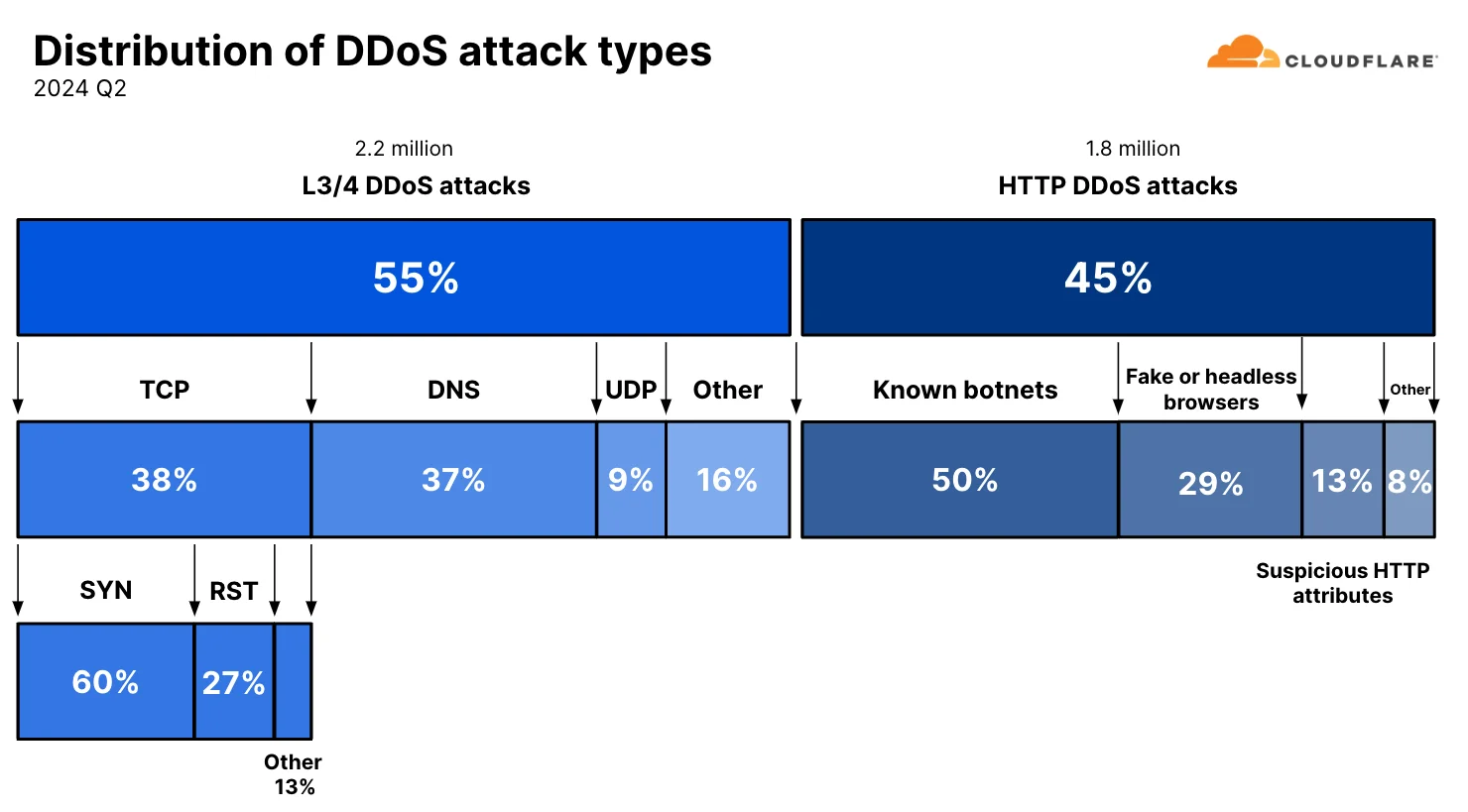
Breakdown of DDoS attacks by types and methods (Source: Cloudflare)
Tracking these groups is vital to understanding the methods and tools driving the modern DDoS threat landscape. The increasing sophistication of attacks, often mirroring the capabilities of state-level actors, poses a significant risk to businesses, governments, and critical infrastructure worldwide. By monitoring these hacktivist ecosystems, organizations can better anticipate threats and bolster their defenses against the evolving tactics of cyber adversaries.
NoName057(16): Pro-Russian Hacktivists and the DDoSia Project
NoName057(16) is a pro-Russian hacktivist group that surfaced in March 2022 during the Russia-Ukraine conflict. The group conducts Distributed Denial of Service (DDoS) attacks, primarily targeting Ukraine, NATO member states, and countries supporting Ukraine. Their operations are managed through Telegram, where they run multiple channels, including the DDoSia Project—a platform inviting volunteers to join DDoS campaigns. Participants are rewarded with cryptocurrency based on their contribution to successful attacks, fueling the group’s growing network.
Telegram channel of NoName057(16)
The group’s key tool, DDoSia, has been upgraded with advanced encryption (AES-GCM) to conceal target lists, complicating efforts to intercept or block their attacks. NoName057(16) focuses on sectors like finance, public administration, transportation, and critical infrastructure. Recent operations include high-profile attacks on Polish and Swedish financial institutions and government websites in Germany and Denmark.
DDoSia Project by NoName057(16)
Initially operating in isolation, NoName057(16) shifted its strategy in late 2023, aligning with prominent hacktivist groups. In addition to collaborating with pro-Russian entities, the group has forged alliances with pro-Palestinian and Islamic hacktivist groups, further broadening its influence and operational scope. This diverse coalition has allowed NoName057(16) to undertake more coordinated and ideologically varied campaigns, posing a heightened threat to global cybersecurity.
To counteract threats like NoName057(16), SOCRadar Advanced Dark Web Monitoring offers organizations the ability to gain real-time insights into underground activities, including those on Telegram. This solution allows cybersecurity teams to identify early warning signs of coordinated attacks, such as discussions of specific targets or tool developments.
SOCRadar Dark Web Monitoring
By analyzing threat actors’ communications, SOCRadar provides actionable intelligence to preemptively fortify defenses. Moreover, the platform helps track ransomware negotiations, data breaches, and even recruitment efforts by groups like NoName057(16), ensuring organizations stay ahead of emerging threats.
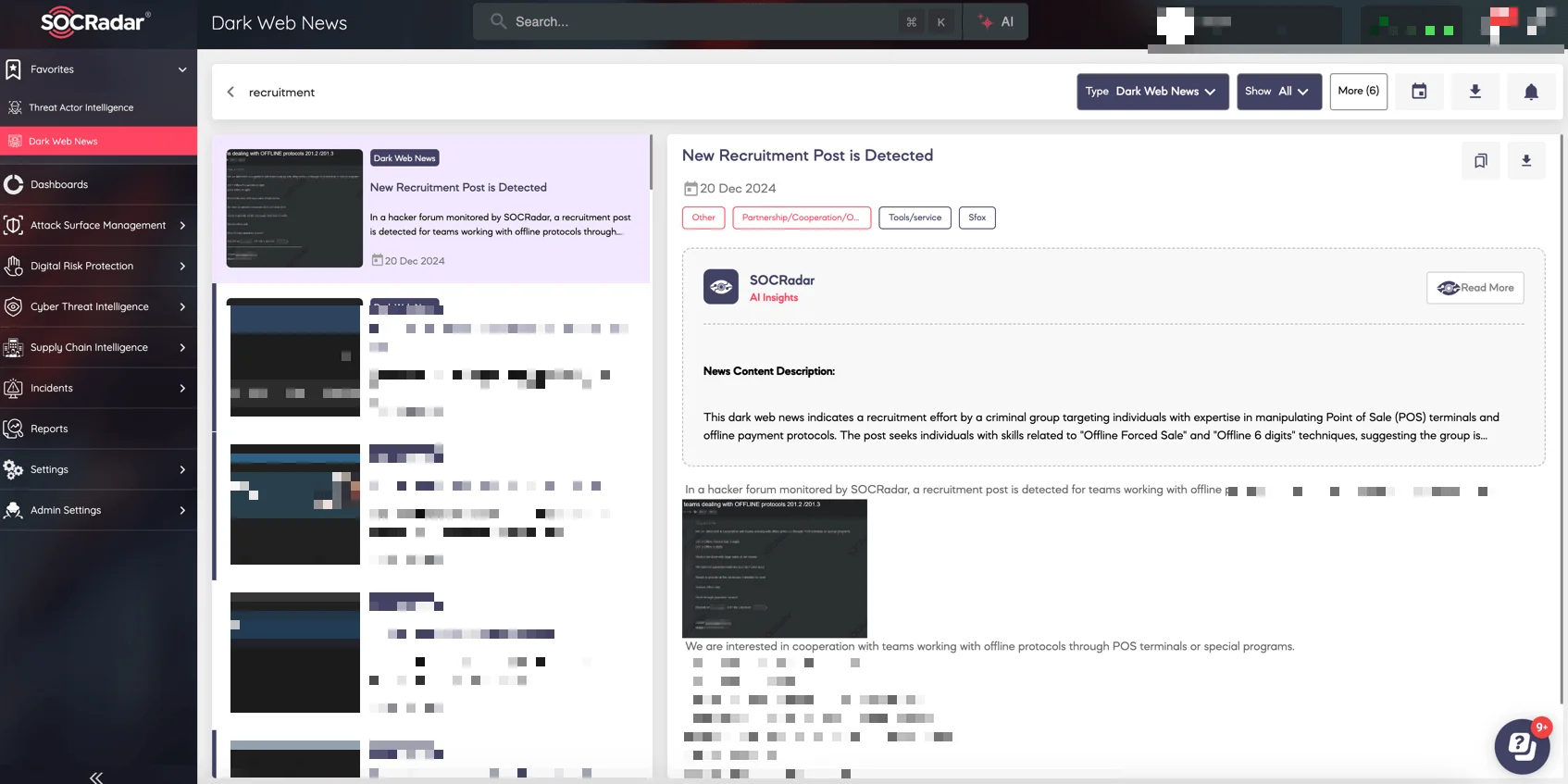
SOCRadar Dark Web News
RipperSec: Pro-Palestinian Hacktivists and the MegaMedusa Tool
RipperSec, a pro-Palestinian hacktivist group originating from Malaysia, has been active on Telegram since June 2023. Known for targeting Israel and its allies, the group has also formed alliances with pro-Russian threat actors, expanding its reach and influence. RipperSec’s primary targets include Israel and countries that openly support Israel.
RipperSec’s Telegram channel
While RipperSec is best known for its DDoS capabilities, the group is also involved in website defacement campaigns and intrusions into SCADA-like systems, demonstrating its diverse range of cyberattack methods. These activities reflect the group’s broader objectives of causing disruption and gaining visibility for its cause.
One of RipperSec’s standout contributions is the MegaMedusa tool, a Web DDoS attack platform developed by a group member. MegaMedusa is a NodeJS-based Layer-7 DDoS tool developed by the RipperSec team. This tool is central to the group’s operations, allowing users to execute scalable Web DDoS attacks with minimal technical expertise. Designed for efficiency, MegaMedusa supports various operating systems, including Debian, Ubuntu, Kali Linux, Termux, and Windows, making it widely accessible.
Alleged MegaMedusa’s Features:
- Bypasses multiple security layers, including UAM Challenges, Cloudflare NoSec, DDoS Guard, vShield, and ShieldSquare Captcha.
- Can hold a DDoS attack for up to 100,000K seconds.
- Proxy support enables traffic to originate from different IPs and countries, increasing the attack’s impact.
Command:
node MegaMedusa.js https://example.com 500 30 10 proxy.txt
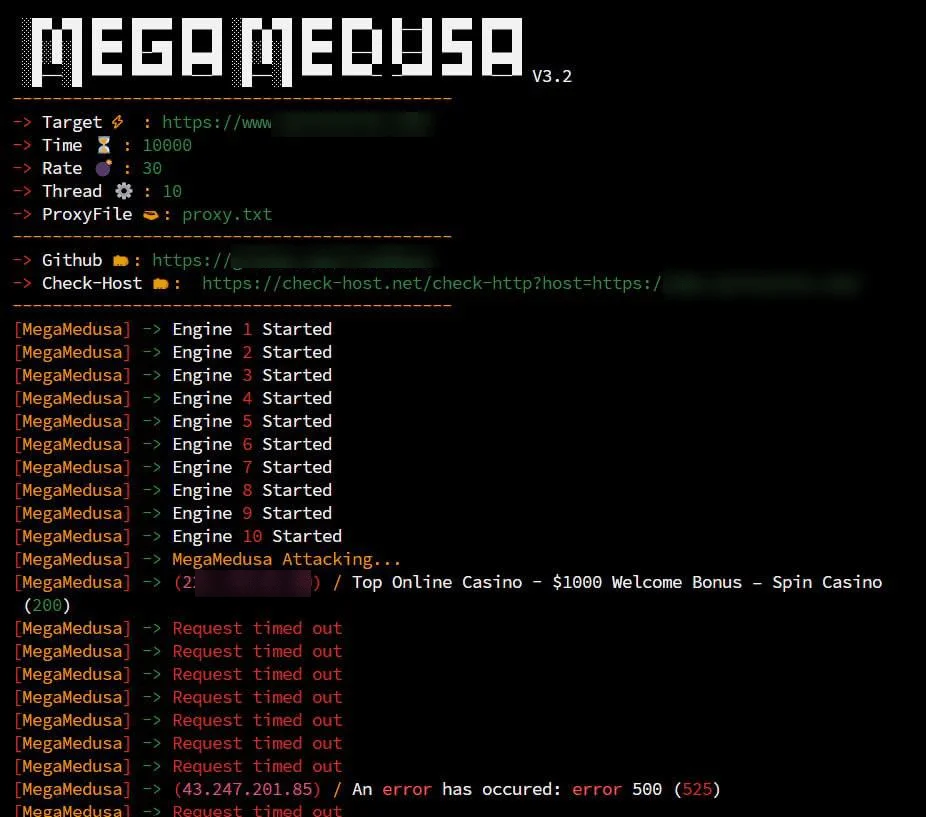
MegaMedusa’s control panel (Source: GitHub)
What sets RipperSec apart is its ability to empower members to launch independent attacks using MegaMedusa. These actions are then showcased within the group, fostering recognition and a sense of accomplishment for participants. This approach not only provides a simple tool for less technically skilled individuals but also creates a reputation-building platform within the hacktivist community.
While the public version of MegaMedusa is available to volunteers and Telegram subscribers, evidence suggests that RipperSec members use more advanced, customized versions of the tool. These enhanced versions allow for more sophisticated and impactful attacks, further solidifying RipperSec’s position as a growing force in the hacktivist landscape.
UserSec: Pro-Russian Hacktivists and DDoS-for-Hire Operations
UserSec, a pro-Russian hacktivist group, gained attention in early 2023 for its politically driven cyberattacks targeting NATO countries, Ukraine supporters, and Western critical infrastructure. Operating primarily through Telegram, the group uses the platform to coordinate attacks, recruit participants, and amplify its propaganda. While there are no confirmed ties to the Russian government, UserSec’s actions align with Russia’s geopolitical objectives, including destabilizing Western nations and advancing pro-Russian narratives.
UserSec’s Telegram channel
The group has expanded its capabilities by collaborating not only with pro-Russian hacktivist groups but also with Islamic-oriented groups. These alliances have broadened UserSec’s operational reach and increased its ability to carry out coordinated and impactful attacks. Their activities include DDoS campaigns, data breaches, website defacement, and credential exploitation. Additionally, UserSec is believed to engage in DDoS-for-hire operations, offering tools and access to malicious actors while monetizing their capabilities alongside their ideological objectives.
By leveraging alliances and diversifying its strategies, UserSec has positioned itself as a growing threat in the cyber domain. Its focus on both ideological and financial goals, along with its ability to collaborate across different ideological lines, underscores the evolving nature of politically driven cyber threats.
Holy League: An Alliance Strengthening Hacktivist Collaborations
The Holy League, formed in July 2024, is not a distinct threat group but an alliance designed to enhance cooperation among pro-Russian and pro-Palestinian hacktivist groups. Created through the merger of two major alliances, this collective aims to coordinate cyberattacks against shared adversaries, including Western nations, India, and countries supporting Ukraine and Israel. Its establishment marked a significant effort to unify disparate hacktivist efforts under a common agenda.
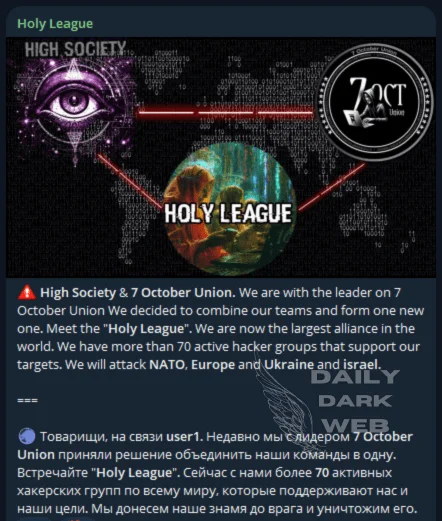
Holy League’s announcement (Source: Daily Dark Web)
Operating with a mix of political and ideological motivations, the Holy League leverages its network to launch large-scale campaigns, including Distributed Denial of Service (DDoS) attacks, website defacements, and data breaches. These actions are orchestrated not only to disrupt critical infrastructure but also to bolster the reputation of participating groups and attract new allies.
The group’s messaging, often infused with religious and geopolitical rhetoric, emphasizes solidarity and resistance against perceived adversaries. The alliance’s reliance on propaganda, strategic coordination, and its ability to unite over 80 member groups underscores its role as a significant enabler in the hacktivist ecosystem. By fostering collaboration and amplifying the capabilities of its members, the Holy League represents an evolving model of hacktivist operations in today’s geopolitical conflicts.
MR. Hamza: An Islamist-Oriented Hacktivist Group
MR. Hamza is a relatively new Islamist-oriented threat group that began its operations on Telegram on October 3, 2024. The group is primarily known for its anti-Israel campaigns and its collaboration with other pro-Russian and pro-Palestinian hacktivist groups. Its operations focus on targeting Israel and nations that openly support Israel through coordinated cyberattacks.
MR. Hamza’s Telegram channel
MR. Hamza primarily conducts DDoS attacks, but it has also made claims regarding data leaks targeting its adversaries. The group is believed to be managed by Moroccan threat actors, further adding a regional dimension to its operations. MR. Hamza has rapidly gained attention within the hacktivist landscape due to its collaborative efforts and its ability to carry out high-profile campaigns.
In addition to its cyberattacks, MR. Hamza is engaged in the sale of malicious tools through its Telegram channel. These tools, designed for conducting cyberattacks, include:
- Elite Botnet
- Rebirth Botnet
- Nova Botnet
- Sapphire C2
- Cindy Network
- Ryzer Stresser
Hamza’s activities highlight its dual focus on advancing ideological objectives and generating revenue through the distribution of sophisticated attack tools. This combination of targeted cyberattacks and tool sales positions it as a growing threat within the broader cyber threat ecosystem.
In combating groups like MR. Hamza, SOCRadar Threat Hunting provides a critical edge. Threat Hunting allows organizations to automatically monitor Telegram channels and quickly locate specific information or threats they are investigating.
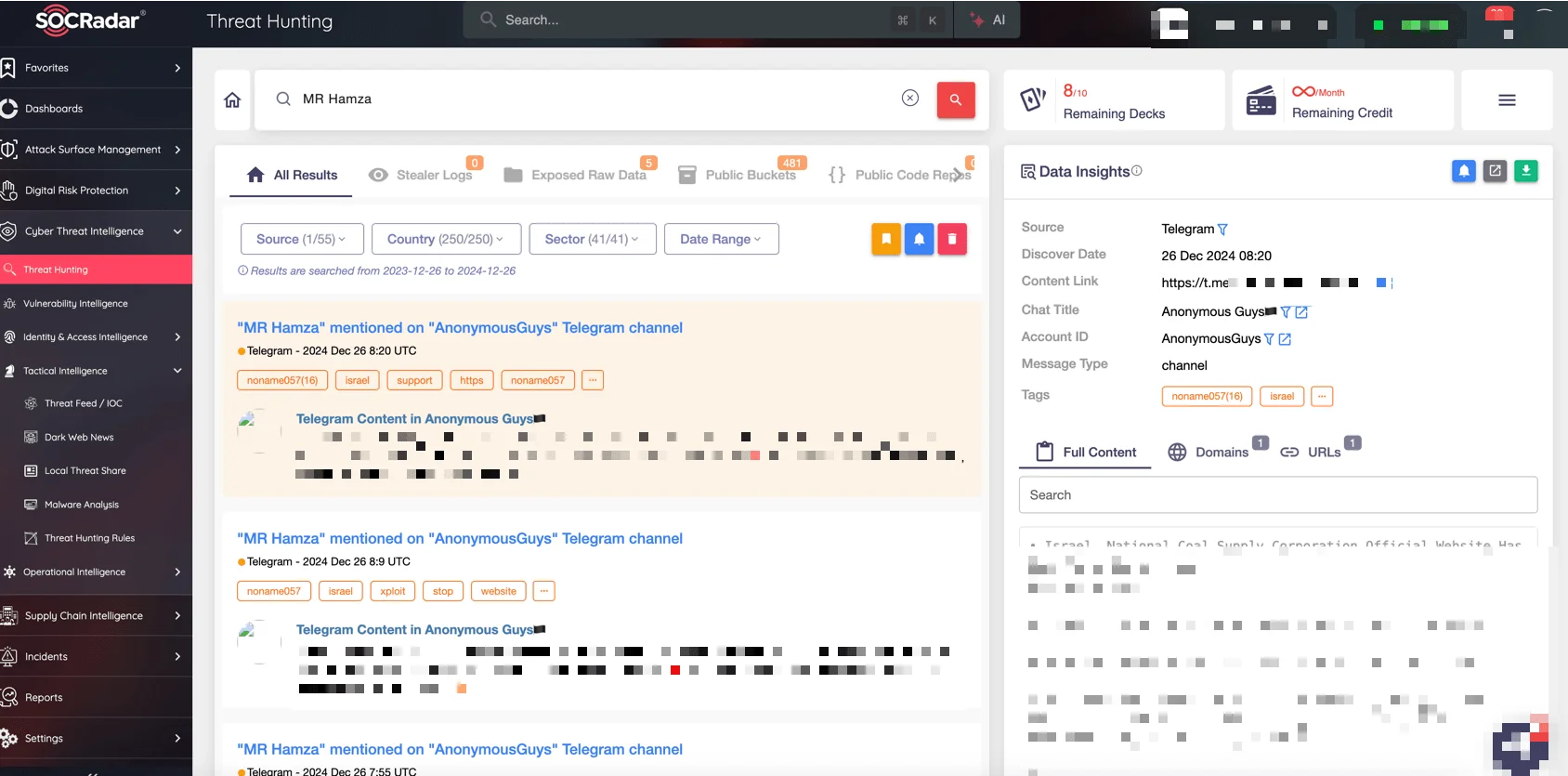
SOCRadar Threat Hunting
This capability ensures that security teams can efficiently track suspicious activity, identify emerging campaigns, and gather actionable intelligence in real-time. By enabling swift and precise threat identification, SOCRadar Threat Hunting ensures that organizations remain proactive and prepared in the face of evolving cyber threats.
GlorySec: A Hacktivist Group with Anti-Authoritarian Aims
GlorySec has gained attention for targeting governments and institutions it views as corrupt, focusing on countries like Russia and other perceived authoritarian regimes. The group operates primarily through Telegram, where its main channels, established on August 10, 2023, are used to publicize cyber activities such as DDoS attacks, data breaches, website defacements, and doxxing, while promoting anti-authoritarian ideals.
GlorySec’s Telegram channel
Identifying with Anarcho-Capitalist principles, GlorySec advocates for minimal government and individual freedoms, opposing authoritarian regimes such as those in Russia and China.
While collaborating with other hacktivist groups, GlorySec also adopts unique practices, such as selecting leaders through “democratic” votes. Despite operational inconsistencies and abrupt campaign shifts, their activities highlight the disruptive potential of hacktivist groups in the current cyber landscape.
Dark Storm Team: A Pro-Palestinian Hacktivist Group
Dark Storm Team is a pro-Palestinian hacktivist group primarily known for targeting Israel and its allies. The group also collaborates with pro-Russian hacktivist entities, leveraging these partnerships to expand its operations. Dark Storm Team is particularly active in launching DDoS attacks against its adversaries and is involved in the sale of hacking tools and services through its channels.
Dark Storm Team’s Telegram channel
In addition to its ideological focus, the group offers various cyberattack services for financial gain, including DDoS attacks on both protected and unprotected websites, as well as database breaches. These offerings further underline the group’s dual role as a hacktivist entity and a provider of illicit cyber services.
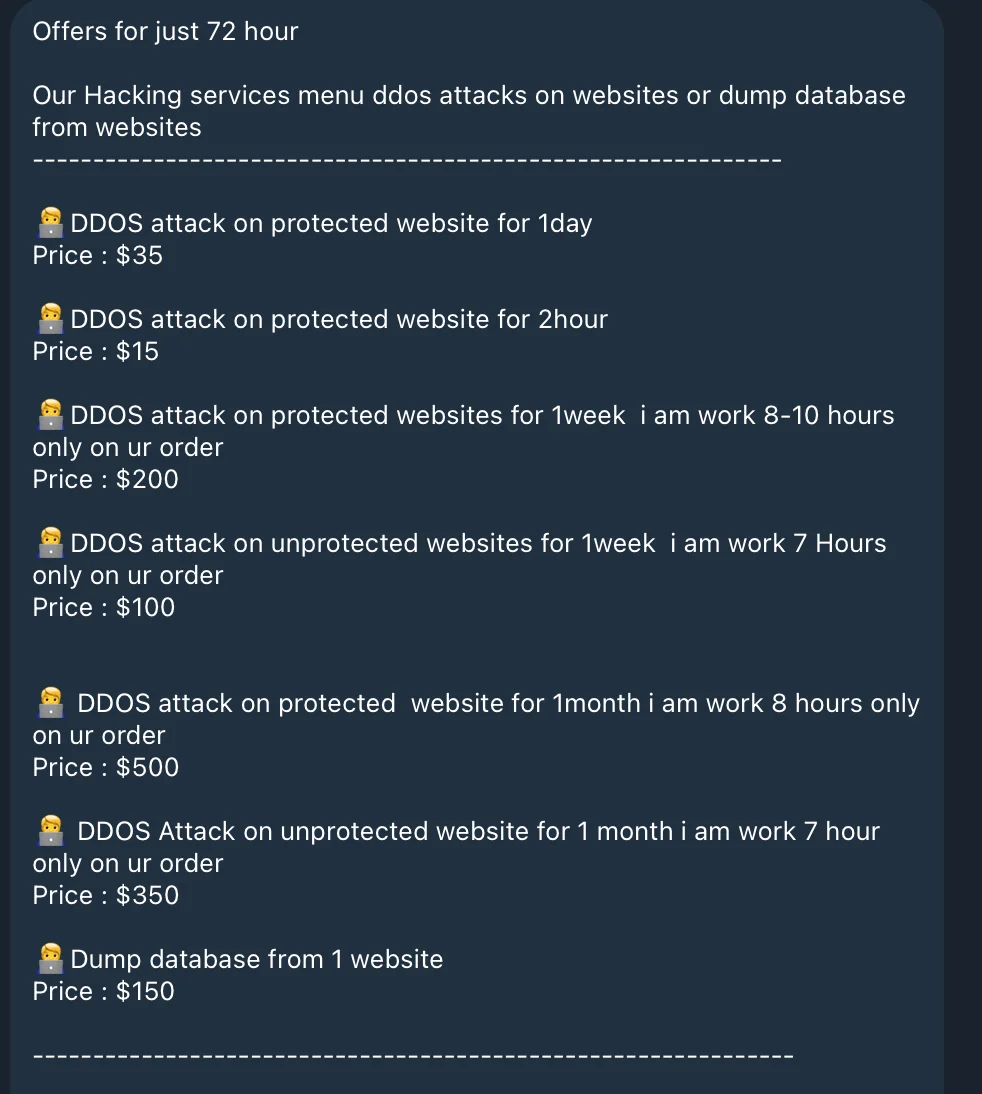
Dark Storm Team’s advertised prices for DDoS attacks and database breaches
Wolf Cyber Team: An Indonesian Hacktivist Group Known for DDoS Attacks
Wolf Cyber Team is an Indonesian hacktivist group widely recognized for its DDoS attacks and pro-Palestinian campaigns. Like many other pro-Palestinian groups, Wolf Cyber Team frequently targets Israel and nations supporting it. However, their scope is not limited to these targets, as the group has been known to attack random entities, including those within their own country.
Wolf Cyber Team’s Telegram channel
The group, whose Telegram channels were established on November 7, is also known for its interactions with pro-Russian threat actors, further expanding its influence in the hacktivist ecosystem. In addition to their DDoS operations, Wolf Cyber Team is associated with alleged data breach activities, often publicized on popular hacker forums. Their unpredictable targeting and varied collaborations highlight their prominence as an evolving hacktivist threat.
Wolf Cyber Team’s statement on BreachForums
Anonymous Guys: An Iranian Hacktivist Group
Anonymous Guys is an Iranian hacktivist group that identifies itself as a defender against groups opposing Islam. Their Telegram channel, established on October 10, is claimed to be their third iteration following previous suspensions. The group also engages with pro-Russian hacktivist entities, reflecting their broader alliances within the hacktivist ecosystem.
Anonymous Guys’ Telegram channel
Anonymous Guys positions itself as a key player in ideological cyber campaigns, leveraging these alliances and their operations to further their stated objectives. Their activities demonstrate a commitment to their ideological stance while maintaining connections with other prominent hacktivist groups.
Golden Falcon: A Pro-Palestinian Hacktivist Group
Golden Falcon is a hacktivist group that launched its Telegram channels on June 13. The group is known for its pro-Palestinian campaigns and interactions with pro-Russian hacktivist entities, highlighting its strategic alliances in the hacktivist ecosystem.
Golden Falcon’s Telegram channel
Golden Falcon primarily conducts DDoS attacks and is also associated with claims of unauthorized system intrusions.
Given their collaborative efforts and expanding operational scope, SOCRadar Threat Actor Intelligence becomes an indispensable tool for organizations aiming to stay ahead of such threats. This solution provides continuous, real-time tracking of threat actors across platforms like Telegram, offering detailed insights into their activities, alliances, and evolving strategies.
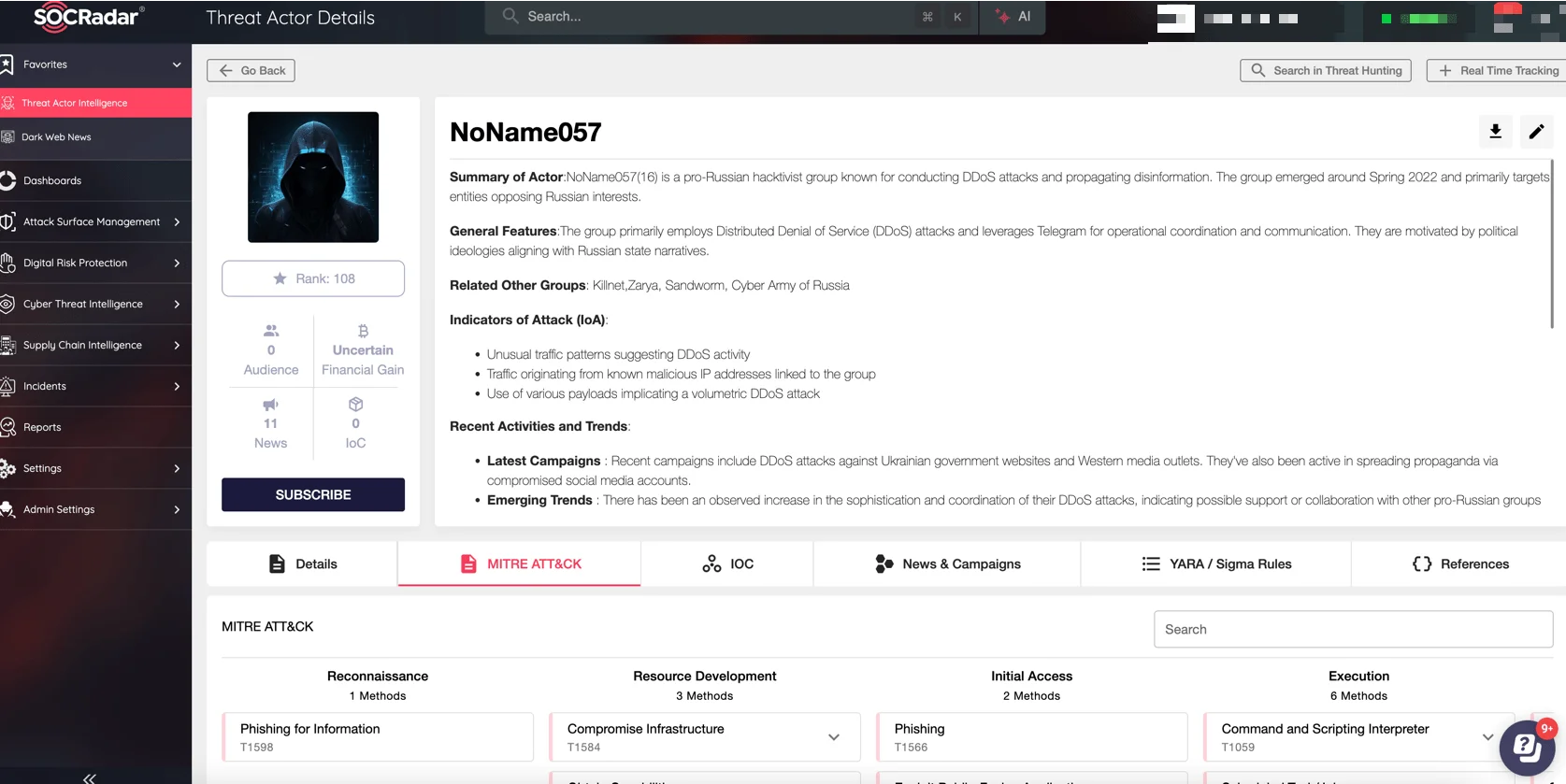
SOCRadar Threat Actor Intelligence
By monitoring groups like NoName057(16), organizations can identify potential risks early, understand the tactics being employed, and implement preemptive measures to safeguard their critical assets. SOCRadar Threat Actor Monitoring ensures that security teams remain informed and ready to respond to the dynamic nature of the cyber threat landscape.
DDoS Prevention Measures
As Distributed Denial of Service (DDoS) attacks become increasingly sophisticated and impactful, implementing robust defense mechanisms is essential for organizations to maintain operational continuity and safeguard critical assets. Below are key strategies for mitigating and preventing DDoS attacks:
- Traffic Filtering and Rate Limiting
Use advanced filtering systems to differentiate legitimate user traffic from malicious requests. Rate-limiting mechanisms can restrict the number of requests from specific IPs or geographic locations, minimizing the impact of volumetric attacks. - Adopt a Multi-Layered Defense
Deploy solutions that address attacks across all layers of the OSI model. Network-layer defenses, such as firewalls and intrusion prevention systems, should complement application-layer protections like Web Application Firewalls (WAFs). - Utilize DDoS Mitigation Services
Partner with a reputable DDoS mitigation provider, such as Cloudflare, Akamai, or AWS Shield. These services offer scalable protection capable of handling high-throughput attacks. - Implement Redundancy and Load Balancing
Distribute traffic across multiple servers and data centers to avoid single points of failure. Load balancers can dynamically route traffic to ensure availability during peak loads or attacks. - Monitor Network Activity
Use tools to monitor traffic patterns and detect anomalies in real-time. - Keep Systems Updated
Ensure that all software and hardware are up to date to mitigate vulnerabilities that attackers may exploit. - Educate Employees
Conduct regular training sessions to increase awareness of phishing and social engineering tactics that may precede DDoS attacks.
Assess Your Domain’s Resilience
Utilize tools like the SOCRadar Labs DoS Resilience Service to evaluate your domain’s or subnet’s ability to withstand DoS attacks, such as slowloris attacks. This service helps organizations identify vulnerabilities and enhance their defensive posture by proactively addressing weaknesses.
SOCRadar Labs DoS Resilience Service
Conclusion
Telegram-based hacktivist groups have become pivotal players in the modern cyber threat landscape, but their operations are far from static. Many of these groups exhibit significant fluidity, frequently adapting to external pressures and platform policies. For example, Telegram’s evolving stance on combating cybercrime—particularly following the reported detention of its founder, Pavel Durov—has resulted in the closure of numerous threat group channels and forced many to rebrand or operate under different names.
In response to these changing dynamics, some groups have chosen to dissolve entirely, citing concerns over privacy and the inability to maintain secure communications. This makes the cyber threat ecosystem on platforms like Telegram and the dark web highly unpredictable, underscoring the importance of continuous monitoring.
To effectively address this ever-changing environment, organizations need advanced tools such as SOCRadar Dark Web Monitoring and Threat Actor Monitoring. These solutions enable proactive tracking of emerging threats, providing actionable intelligence to adapt to the fluid landscape. Regular monitoring ensures that security teams can respond promptly to new risks, track rebranded or relocated groups, and maintain a strong defensive posture. Staying informed in this dynamic environment is not just recommended—it is essential for mitigating the risks posed by these elusive adversaries.





































