Fake Extortion: How to Tackle and How to Verify?
Today, one of the most critical aspects of maintaining a respectable business is to have resistance against cyber attacks. To that aim, organizations try to implement extraordinary measures to keep a solid security posture. Yet as it turns out, according to a study in 2022, 64% of the participant decision-makers admit that their own cybersecurity incidents are the result of their own outdated IT security plans.
One of the most common ways cybercrime is conducted is through Ransomware and DDoS attacks. It is in correlation with the findings in the same study that 85% of companies experience at least one ransomware attack per year. It is expected that by 2027, cybercrime will cost the world nearly $25 trillion. Because of these reasons, organizations should be on their toes.
Even though there are real threats targeting organizations through the techniques above, there are also fake threats disguised as legitimate ones. The threat actors conducting these activities can be called fake extortion groups.
Fake extortion groups send threatening messages to organizations, claiming control over their systems or sensitive data. They manufacture scams and prey on unsuspecting individuals and organizations, using fear and urgency to coerce victims into paying a ransom to protect their data. Their threats are often fraudulent, relying on deception rather than actual possession of the claimed data.
How do Fake Extortion Groups Operate?
In the operations of fake extortion, social engineering plays a huge role. It is the primary tool for fraudsters to use to achieve their goal of receiving a ransom. Most of the time, they contact the target via email. They create a sense of urgency and fear through various threats. They may manipulate the target into giving up a ransom through false data breach claims. They can scare the target with data leak threats and may set a deadline for a ransom to be paid.
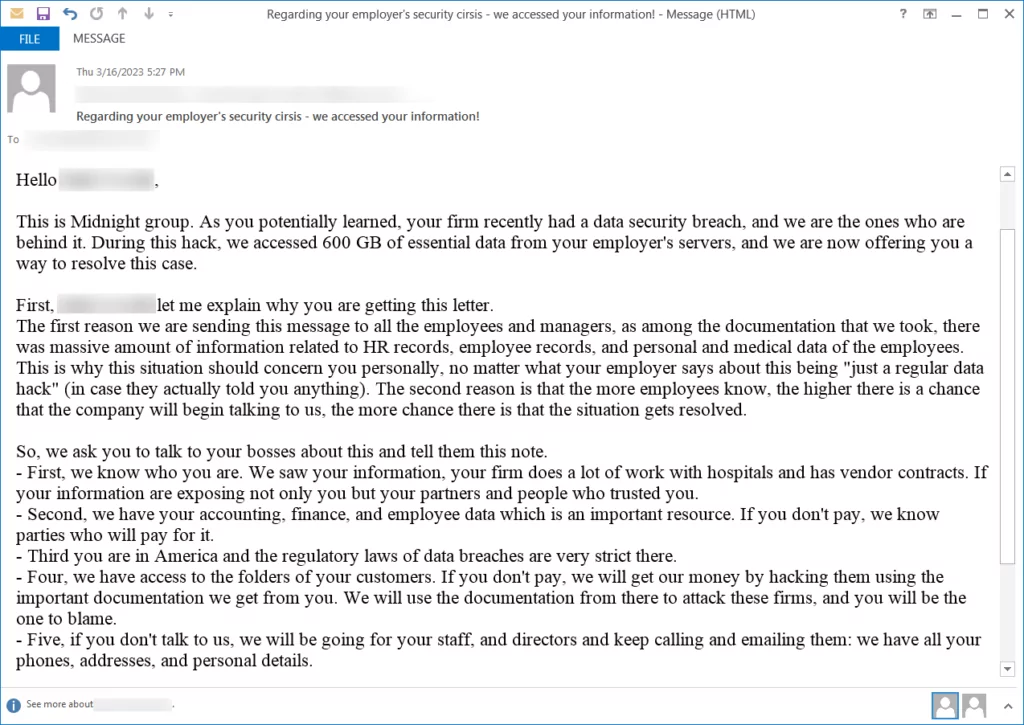
In some instances, these threat actors can also impersonate well-known ransomware groups or notorious cybercriminals to increase the perceived credibility of their threats. They may use similar tactics and language or even reference previous high-profile attacks to further deceive their victims. As recent news shows, fake extortionists threaten U.S. companies with publishing allegedly stolen data unless they get paid. They are piggybacking on the recent data breaches and ransomware incidents.
The group is called Midnight. They were detected to target U.S. companies since at least March 16. They reportedly use various techniques, including impersonating two different Ransomware groups in multiple instances. In one of the emails to the petroleum additives holding company employee, the threat actor claimed to be the Silent Ransom Group (SRG), also known as Luna Moth. However, the same message was used while impersonating another threat actor, the Surtr ransomware group.
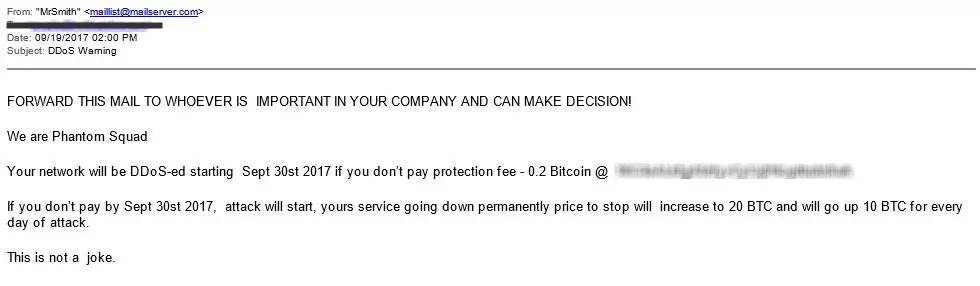
Another tool that the fake extortion groups may occasionally use to instigate fear in their targets is DDoS attacks. These attacks overload the target’s systems, rendering their online services inaccessible. The threat of a DDoS attack is used to add pressure and urgency to the victim’s decision-making process. These activities have been seen in the wild regularly in the last decade.
In 2017, a notorious DDoS extortion group called Phantom Squad launched a widespread spam campaign, targeting thousands of companies worldwide. The group threatened to carry out DDoS attacks on September 30 unless the victims paid a ransom.
Unlike their usual approach of targeting a small number of companies individually, this time, they have adopted a shotgun approach, sending the threats to multiple recipients simultaneously. Security experts who have examined the emails and ransom demands believe that the group lacks the capability to launch DDoS attacks on such a large scale and is likely resorting to scare tactics in the hopes of tricking victims into paying.
How to Act When Faced With These Threats?
On the daily run of the business, any organization can face these kinds of threats. What can be done if a fake extortionist group threatens your organization with a data breach? One of the most critical steps to take would be to confirm the legitimacy of the threat.
The first signaler of a fake extortion threat would be the ransom price demanded. Considering the fact that the average demand for a ransom is up in the hundreds of thousands, mere thousands of dollars may indicate an actor who did not put much effort into the attack. Therefore, it may not be a legitimate attack.
In order to confirm the legitimacy of the attack, the claims of the extortionists should be investigated thoroughly. Conduct an internal review of data security practices to identify potential vulnerabilities the attackers may have exploited. The ropes should not be released if no evidence is found in the internal investigation regarding the breach. External help may be the deciding factor in deducing a conclusion. Engaging cybersecurity professionals outside the organization may help decide whether the threat is real or not.
With the help of cyber intelligence, it can be determined whether the threat actor, maybe impersonated by the fake extortion groups, is active or not. If it is an active actor, behavioral analysis can be made on the ransom demands or targeting scheme. If everything correlates with the alleged threat actor’s behaviors, sample data can be requested from the attacker, and through cyber intelligence, it can be determined whether this sample is from an earlier breach or not.
In the case of Midnight Group’s extortion attempts, it was reported that they have been conducting these kinds of extortion attacks since 2019. After their recent attempts, it was quickly correlated with their old attacks and deemed as an empty threat.
On top of all the reactive approaches mentioned above, the most important step to take is to act proactively. Robust security measures should be implemented beforehand. A strong password policy that is on par with the current trends must be implemented with an MFA solution. The backup of critical systems must be kept in case of a destructive ransomware attack.
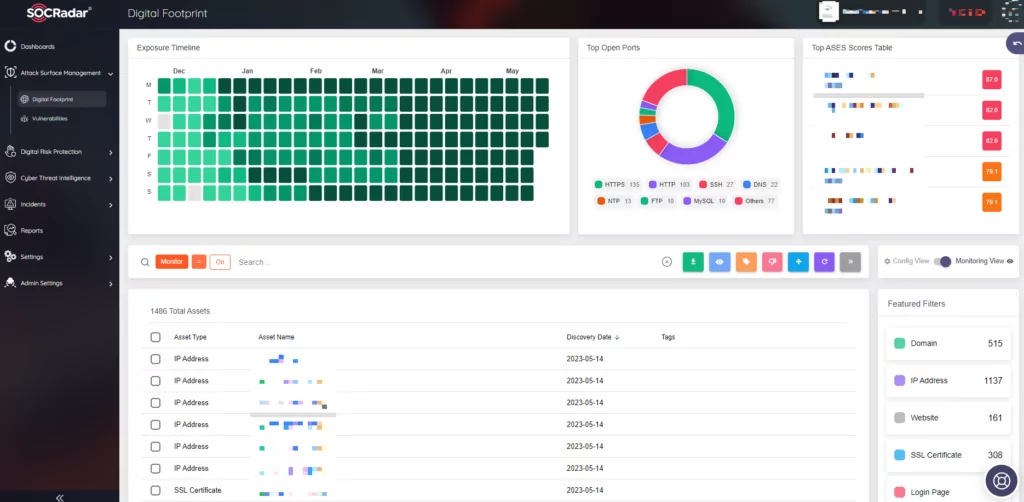
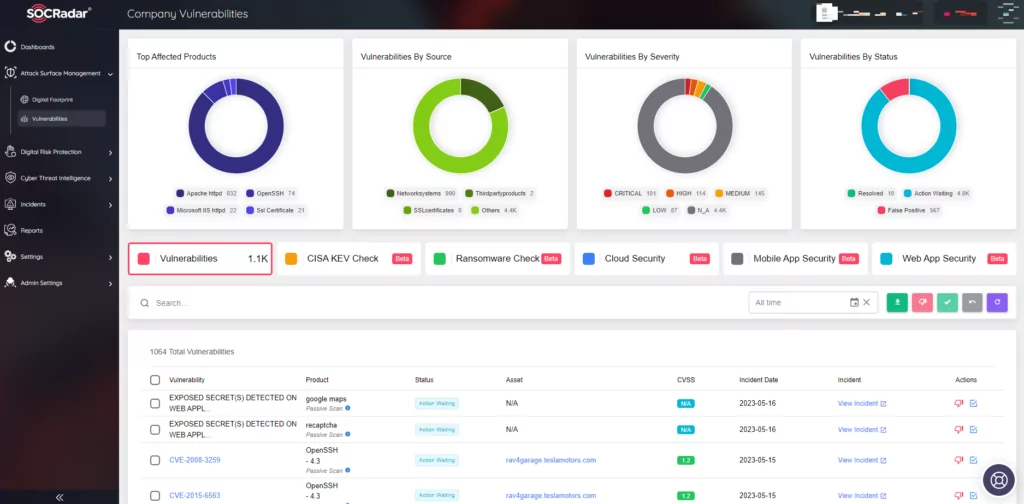
On the external-facing digital assets, SOCRadar can help with its Attack Surface Management. It constantly monitors external-facing digital assets and maps vulnerabilities with the assets. With SOCRadar’s ASM, security teams can track which vulnerabilities are present in the environment. Knowing which vulnerabilities are present in the organization can give the organization an advantage in defending against threats.
How SOCRadar Can Help to Tackle with Fake Extortion Groups?
Fake extortion groups are not the most significant threats out there; however, they can be painful to deal with. While some of them may be questionable threats, as in the case of Phantom Squad’s DDoS threats, others can be well-crafted extortion attempts to the point of providing some real undisclosed information obtained from other sources.
These kinds of threats will incept the question of “What if?” in the minds of the organizations. Investigating the legitimacy of the extortion attempt will require both time and effort.
It’s important to note that while fake extortion groups can be intimidating, their threats are often baseless. They rely on psychological manipulation and deception rather than actual possession of the claimed information or enough skillset to carry out the alleged attack. Organizations should remain vigilant, verify the credibility of threats, and report any incidents to the appropriate authorities to combat these fraudulent schemes effectively.
With its predictive, preventive, and proactive approach toward security SOCRadar can help you stay ahead of the curve and maintain a good security posture. SOCRadar’s Digital Footprint module enables enterprise security teams to automatically detect and view all assets and public-facing infrastructure, including IP addresses, DNS configurations, network software, domains, and cloud applications, in order to mitigate exposures and threats and to proactively prevent attacks before they lead to brand reputation and financial losses.