FortiManager Zero-Day ‘FortiJump’ Is Now Publicly Addressed (CVE-2024-47575)
[Update] November 18, 2024: “PoC Released for FortiJump Vulnerability (CVE-2024-47575)”
[Update] October 25, 2024: “The Flaw Has Been Exploited Since June 2024, by Actors Now Tracked as UNC5820”, IOCs have also been updated.
The cybersecurity community is currently focused on a critical vulnerability within Fortinet’s FortiManager, a popular tool used in managing FortiGate firewalls in extensive networks. This vulnerability, tracked as CVE-2024-47575 and dubbed FortiJump, has been actively exploited in zero-day attacks.
Amid the unfolding situation, concerns about transparency arose, as some users learned of the flaw through unofficial channels before Fortinet publicly addressed it. This blog post will explore what is known so far about the vulnerability, how it has been exploited, and what steps organizations should take to protect themselves.
Patch Information ‘Leaked’ – How Does That Happen?
Before CVE-2024-47575 received its official designation, discussions about the vulnerability surfaced on various cybersecurity platforms, raising questions about how the information was handled.
Significantly, on October 13, cybersecurity researcher Kevin Beaumont shared a warning on social media, advising FortiManager users to immediately take steps to protect their systems. At the time, Fortinet had not publicly disclosed the vulnerability, though the company had privately notified some customers, offering mitigation steps via email.
Researcher’s post on Mastodon
However, some users expressed frustrations, mentioning that they did not receive advanced notice. Concerns were raised on Reddit about why certain updates seemed to lack information on resolved issues, leaving users confused about the purpose of the updates.
All in all, reports of incomplete notifications fueled concerns about transparency. Criticism emerged over patches being prepared without formal disclosure, leading many users to learn about the zero-day vulnerability only through ‘leaked’ posts and online discussions.
What is CVE-2024-47575 / FortiJump Vulnerability?
On October 23, 2024, Fortinet officially released an advisory detailing the CVE-2024-47575 vulnerability. This critical flaw affects the FortiManager API and holds a severity rating of 9.8 (Critical) on the CVSS scale.
The vulnerability, caused by missing authentication for critical functions, allows remote attackers to execute arbitrary code or commands on vulnerable FortiManager devices by sending specially crafted requests.
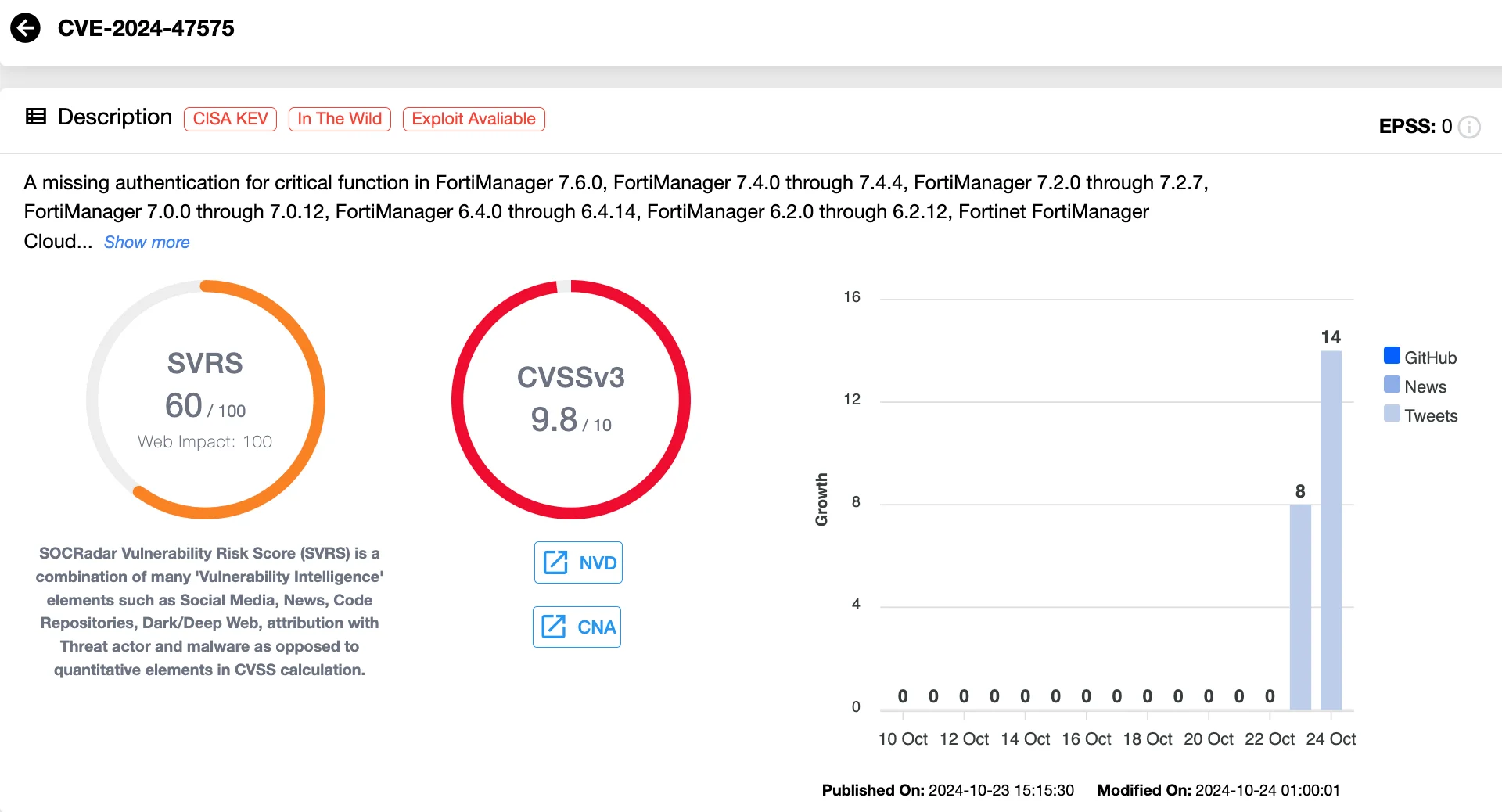
Missing auth flaw in FortiManager, CVE-2024-47575 (SOCRadar Vulnerability Intelligence)
Exploitation of this vulnerability puts organizations at significant risk. Threat actors could potentially gain unauthorized access to FortiManager servers and exfiltrate sensitive data, including configuration files, IP addresses, and credentials for managed devices. In the context of Managed Service Providers (MSPs), this vulnerability could allow attackers to traverse networks, elevating the risk for downstream clients.
In fact, Fortinet has acknowledged that CVE-2024-47575 was being actively exploited in the wild before the official patch was released. The vulnerability allows attackers to remotely take control of FortiManager devices, which could lead to wider compromises across connected FortiGate firewalls and networks. However, the company stated that there have been no reports of malware, backdoors, modified databases, or changes to managed devices on compromised systems.
CISA has also taken action following confirmations, adding CVE-2024-47575 to its Known Exploited Vulnerabilities (KEV) Catalog. Federal agencies are required to patch this vulnerability by the compliance deadline of November 13, 2024.
Analysis and FGFM Exposure
Beaumont brought attention to the vulnerability in a blog released just yesterday, in which he dubbed it as ‘FortiJump’. He explained that the FortiGate to FortiManager (FGFM) protocol, responsible for communication between FortiManager and FortiGate devices, is at the core of the vulnerability.
It was noted that the protocol allows attackers to exploit flaws in how devices are authenticated. Specifically, an attacker can register a rogue FortiGate device with the FortiManager, gaining control over managed firewalls and accessing sensitive configuration data. Even with basic security measures in place, attackers can bypass protections by reusing certificates from existing FortiGate devices to register their malicious versions.
The blog also highlighted that, based on a Shodan search, approximately 60,000 FGFM devices are directly exposed to the internet. Most of these devices are in the U.S.
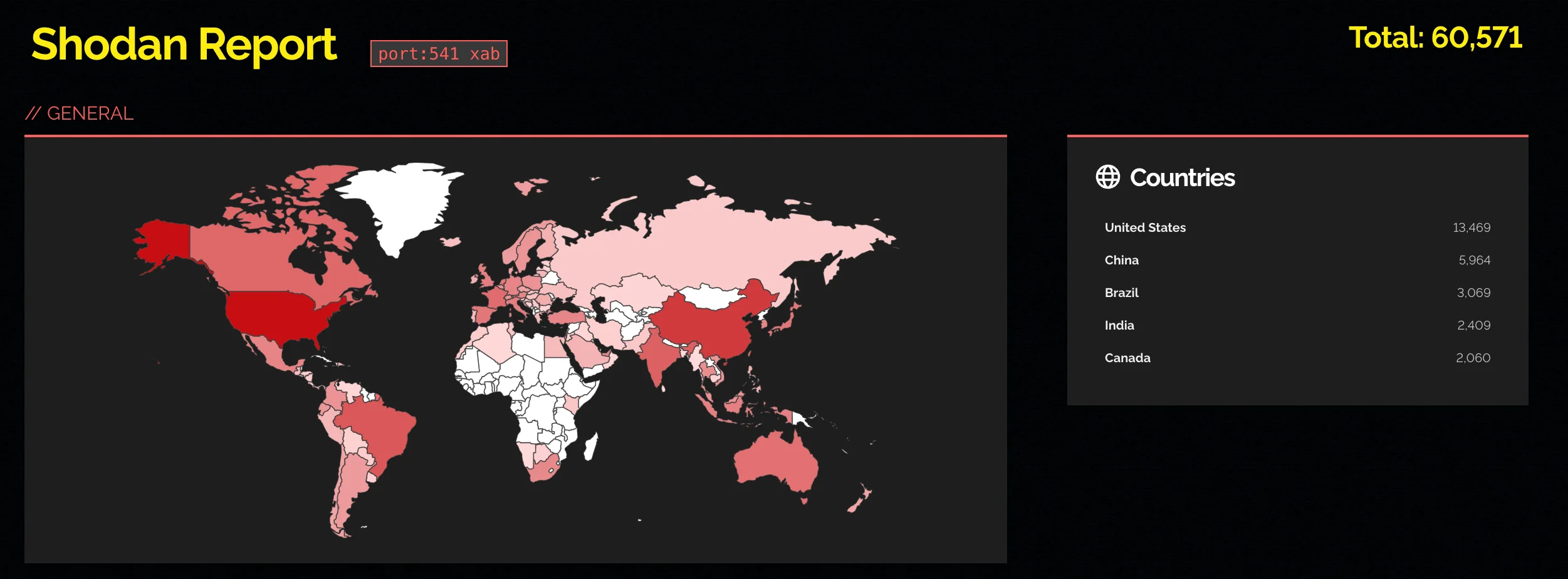
A search on exposed devices (Shodan)
Do you know the full extent of your attack surface? SOCRadar’s Attack Surface Management (ASM) gives you the visibility you need to stay secure. By continuously monitoring your digital footprint – uncovering shadow IT, exposed assets, and vulnerabilities – you can quickly identify and fix weaknesses before attackers strike.
Company vulnerabilities are easier to identify and assess with SOCRadar’s ASM module
SOCRadar’s ASM puts you in control, helping you close gaps and strengthen your defenses, all while staying ahead of potential threats. Moreover, it includes a CISA KEV Check feature that automatically tracks the CISA Known Exploited Vulnerabilities (KEV) list, alerting you to actively exploited vulnerabilities impacting your systems, helping you prioritize patches and stay compliant with regulatory requirements.
The Flaw Has Been Exploited Since June 2024, by Actors Now Tracked as UNC5820
Recent updates from Google’s blog reveal further details on CVE-2024-47575. In collaboration with Fortinet, researchers at Google’s Mandiant are tracking the threat cluster as UNC5820. It is noted that UNC5820 has been actively exploiting the FortiManager vulnerability since June 27, 2024.
According to analysis, while UNC5820 has been leveraging the FortiManager flaw, there is no recorded evidence of lateral movement or additional compromise within the impacted environments. Due to limited data on specific exploitation methods, the threat actor’s motivations and origin remain unclear at this time.
For more information, refer to the full research article here.
PoC Released for FortiJump Vulnerability (CVE-2024-47575)
The technical details and a Proof-of-Concept (PoC) exploit for the critical FortiJump vulnerability (CVE-2024-47575) have been released by security researcher Sina Kheirkhah. This zero-day vulnerability, affecting Fortinet’s FortiManager, has been actively exploited since June, raising significant concerns across the cybersecurity community.
During their investigation, researchers uncovered additional vulnerabilities while replicating the FortiJump exploit. Among these were:
- FortiJump Higher: A privilege escalation vulnerability that enables an authenticated FortiGate device to gain control over FortiManager instances.
- Two Denial of Service (DoS) Vulnerabilities: Capable of crashing the system under certain conditions.
These findings suggest that Fortinet’s initial patch for FortiJump may be incomplete, prompting researchers to urge organizations to remain cautious.
Meanwhile, the PoC, available on GitHub, demonstrates how attackers can leverage the CVE-2024-47575 vulnerability to execute unauthorized remote code on unpatched FortiManager systems. By exploiting a flaw in the system’s handling of specific requests, the script provides a pathway for unauthenticated attackers to compromise FortiManager instances.
Organizations are strongly advised to adhere to Fortinet’s official guidance for patching this vulnerability and to secure their systems promptly. Given the availability of the PoC, unpatched systems face an elevated risk of exploitation.
For additional information and to access the PoC, visit the GitHub repository.
Which FortiManager Versions Are Affected?
The CVE-2024-47575 vulnerability impacts several versions of FortiManager and FortiManager Cloud. Here’s a breakdown of affected versions:
- 7.6.0
- 7.4.0 through 7.4.4
- 7.2.0 through 7.2.7
- 7.0.0 through 7.0.12
- 6.4.0 through 6.4.14
- 6.2.0 through 6.2.12
For FortiManager Cloud:
- 7.4.1 through 7.4.4
- 7.2.1 through 7.2.7
- 7.0.1 through 7.0.12
Additionally, all versions of FortiManager Cloud under release 6.4 must be migrated to a fixed release to address this vulnerability.
Fortinet has also identified that older FortiAnalyzer models – including 1000E, 1000F, 2000E, 3000E, 3000F, 3000G, 3500E, 3500F, 3500G, 3700F, 3700G, and 3900E – are impacted if the following configuration is applied and at least one interface has the fgfm service enabled:
config system global
set fmg-status enable
end
How Can You Address CVE-2024-47575?
To mitigate the risk posed by CVE-2024-47575, Fortinet has recommended upgrading to fixed versions of FortiManager. The vulnerability is addressed in updated firmware releases, and it is essential to ensure that systems are running these patched versions to prevent exploitation.
For detailed information on the recommended versions and patching instructions, refer to the official advisory issued by Fortinet.
Ensuring timely updates is critical, as cybercriminals continue to exploit unpatched vulnerabilities for data theft and network infiltration. Fortinet has also provided workarounds for those unable to immediately apply patches.
Are There Any Workarounds Available?
For those unable to immediately apply the patch, Fortinet has provided several workaround options based on the version in use. These include:
- For versions 7.0.12 and above (except 7.6.0), block unknown devices from registering.
- For versions 7.2.0 and above, set up local-in policies to allow connections only from trusted FortiGate devices.
- For versions 7.2.2 and above, 7.4.0 and above, and 7.6.0 and above, use custom certificates to restrict access, ensuring only devices with a matching certificate can connect.
For older versions like 6.2 and 6.4, an upgrade to a patched version is required as they do not support these workarounds.
For full details of these workaround methods and configuration settings, please refer to Fortinet’s official advisory here.
Indicators of Compromise (IOCs)
Here are the Indicators of Compromise (IOCs) associated with the exploitation of CVE-2024-47575, most outlined by Fortinet.
IP Addresses:
- 45.32.41.202
- 104.238.141.143
- 158.247.199.37
- 45.32.63.2
- 195.85.114.78 (not listed by Fortinet)
It was noticed that one of these IP addresses (104.238.141.143) was previously associated with SuperShell C2 infrastructure, used in attacks on F5 BIG-IP routers. This malicious activity was attributed to UNC5174 in March 2024.
Files:
- /tmp/.tm
- /var/tmp/.tm
Serial Number:
- FMG-VMTM23017412
Hashes:
- 9DCFAB171580B52DEAE8703157012674 (unreg_devices.txt, Hash type: MD5)
Log Entries:
- type=event,subtype=dvm,pri=information,desc=”Device,manager,generic,information,log”,user=”device,…”,msg=”Unregistered device localhost add succeeded” device=”localhost” adom=”FortiManager” session_id=0 operation=”Add device” performed_on=”localhost” changes=”Unregistered device localhost add succeeded”
- type=event,subtype=dvm,pri=notice,desc=”Device,Manager,dvm,log,at,notice,level”,user=”System”,userfrom=””,msg=”” adom=”root” session_id=0 operation=”Modify device” performed_on=”localhost” changes=”Edited device settings (SN FMG-VMTM23017412)”
Researchers also noted the use of a disposable email address (0qsc137p@justdefinition[.]com) in the attack. Additionally, the name “Purity Supreme” was observed in subs.dat and subs.dat.tmp, and might be linked to exploitation activities.