
Fortinet Data Breach: What We Know So Far
On September 12, Fortinet, a prominent cybersecurity company, acknowledged a security incident involving unauthorized access to a third-party cloud-based file drive. According to the company, a small number of files stored on Fortinet’s instance of the third-party service were accessed, impacting a limited number of customers. Fortinet assured that its operations, products, and services were unaffected by the breach.
Which regions were impacted by the Fortinet data breach?
The Fortinet data breach allegedly impacted customers primarily in the Asia-Pacific (APAC) region. While no specific customer data or details have been fully disclosed, Fortinet has reassured the public that it promptly communicated with the affected individuals and offered assistance to mitigate any potential risks.
SOCRadar’s Supply Chain Intelligence module offers a critical advantage for organizations seeking to safeguard their extended network of vendors, partners, and suppliers. By providing real-time insights into the security postures of third-party entities, SOCRadar helps identify potential vulnerabilities and exposures that could impact your organization.
SOCRadar XTI Supply Chain Intelligence
With continuous monitoring of third-party digital assets, this module ensures that any weaknesses in your supply chain are detected early, enabling you to address risks before they lead to significant security breaches.
What claims were made by threat actors concerning the Fortinet data breach?
Shortly after Fortinet’s initial announcement, the SOCRadar Dark Web Team detected a post from a threat actor on a hacker forum, claiming responsibility for breaching Fortinet. The actor alleged they had accessed 440 GB of data from Fortinet’s Azure SharePoint, which they made available through an S3 bucket.
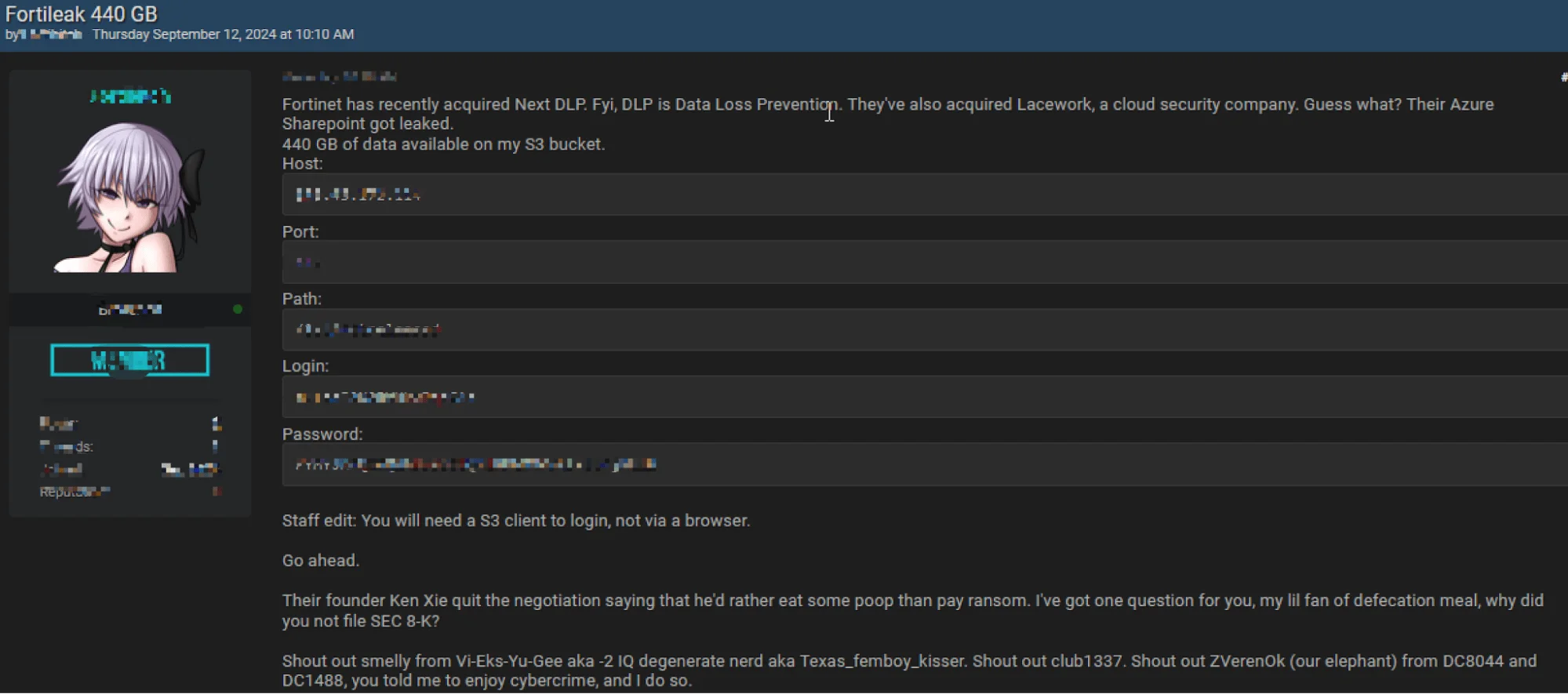
Threat actor claims to have breached Fortinet
The claim also included unverified statements about Fortinet’s founder, Ken Xie, reportedly rejecting ransom negotiations. Additionally, the threat actor accused Fortinet of failing to file an SEC 8-K form, which is a mandatory disclosure following significant events.
What additional claims surfaced after the initial post?
Following the initial claim of the Fortinet data breach, several forum users began questioning the authenticity and functionality of the provided download links. Many reported difficulties accessing the alleged data, raising skepticism about the legitimacy of the threat actor’s assertions.

IntelBroker’s comments
At this point, IntelBroker, a threat actor within Dark Web forums, intervened. IntelBroker confirmed that the links had initially been problematic but assured the forum that these issues had been resolved. This statement added weight to the ongoing discussions about the validity of the Fortinet data breach.
IntelBroker is not only a well-known figure in the Dark Web for orchestrating high-profile cyberattacks, but also serves as a key administrator for both BreachForums and the CyberNiggers threat group. These roles further cement IntelBroker’s influence within the cybercriminal community, where they are involved in selling access to compromised systems and managing significant data leaks.

SOCRadar threat actor card of CyberNiggers
For more detailed information about IntelBroker’s activities, including their involvement with these groups, check out SOCRadar’s comprehensive blog: Dark Web Profile: IntelBroker.
How did the threat actor respond to criticisms?
In response to users’ criticisms about the broken links and doubts regarding the Fortinet data breach, the threat actor made several points in defense of their claim, including:
- The server had never been taken down and remained accessible.
- The credentials provided were valid, with the only issue being a self-signed TLS certificate.
- The data was hosted on an S3 bucket, and users needed an S3 client to access the data rather than a browser.
- The data was not being sold; it was available for free.
These statements were intended to address the technical concerns raised by forum members and reaffirm the validity of the alleged breach.
SOCRadar’s Advanced Dark Web Monitoring module provides organizations with real-time insights into the hidden corners of the internet, including hacker forums, Telegram channels, and dark web marketplaces.
SOCRadar XTI Advanced Dark Web Monitoring
By constantly monitoring these platforms, SOCRadar detects early-stage threats such as stolen credentials, data leaks, or mentions of an organization’s assets being sold or targeted. This proactive approach allows businesses to act quickly, reducing the potential for data breaches or other malicious activities.
Was the threat actor’s claim verified?
While these claims were discovered by the SOCRadar Dark Web Team, the connection between the threat actor and Fortinet’s actual breach remains unverified. The account of the threat actor who made the claim was newly created, raising the possibility that this could be an opportunistic attempt to exploit the situation. This kind of behavior is not uncommon on Dark Web forums, where scammers often attempt to cash in on legitimate incidents by making exaggerated or false claims.
There is a chance the claim is part of classic Dark Web scams, where threat actors seize on major incidents to extort or deceive. Therefore, although the claim might be valid, there’s also a high likelihood of it being a case of opportunistic deception.
What actions did Fortinet take to address the breach?
In its latest notice, Fortinet highlighted that it worked closely with the affected customers, providing direct communication and support to mitigate risks. The company also ensured that no further breaches occurred by implementing strong security measures and closely monitoring its systems.
Fortinet later provided more details, stating, “An individual gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive, which included limited data related to a small number (less than 0.3%) of Fortinet customers. To date, there is no indication that this incident has resulted in malicious activity affecting any customers.”



































