
Hacker Breached Nearly Entire Uber IT System
Transportation provider giant Uber is currently investigating a cyberattack. Following a network intrusion, multiple instances used by the company have been compromised. Uber announced on Twitter that they are working with law enforcement to address the issue.
The company’s compromised internal systems were taken offline to contain and further investigate the incident once it was noticed. According to two employees of Uber, Slack, the company’s internal messaging platform, was also forbidden from use.
What Did the Hacker Access?
The hacker provided screenshots of emails, the cloud, and repositories as evidence. According to the Uber representative, a hacker accessed a worker’s Slack account and used it to send the message.
Uber employees got a message saying, “I announce I am a hacker and Uber had suffered a data breach.”, just before the Slack system was shut down. The message continued by listing several internal databases the hacker claimed were exposed.
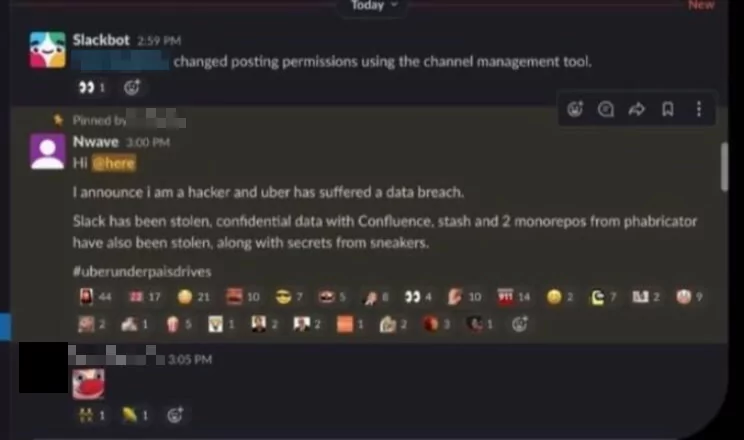
The threat actor in question claimed to be 18 years old and to have spent several years on his cybersecurity skills, and admitted to the New York Times that he used social engineering techniques and presented as an IT expert to obtain an employee’s password. This resulted in the attacker’s device being registered to the employee’s MFA.
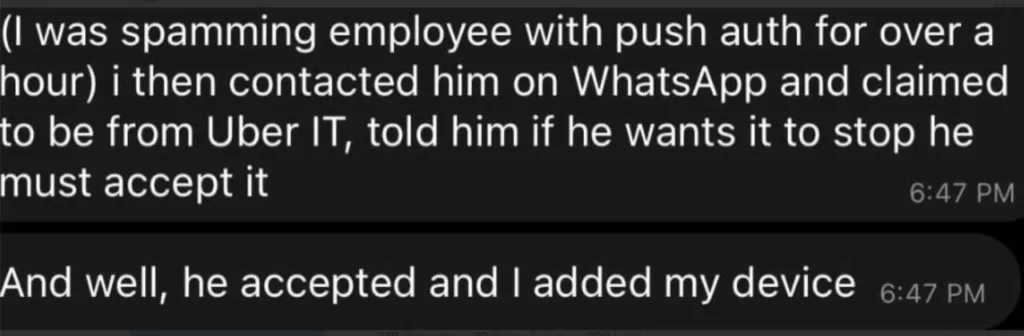
According to him, the company’s poor security allowed the hacking. He added that Uber drivers ought to be paid more.
The stolen password and MFA provide attackers with VPN access, thus also allowing them to utilize Uber’s intranet for scanning the internal network (*[.]corp[.]uber[.]com) and accomplish a man-in-the-middle attack.
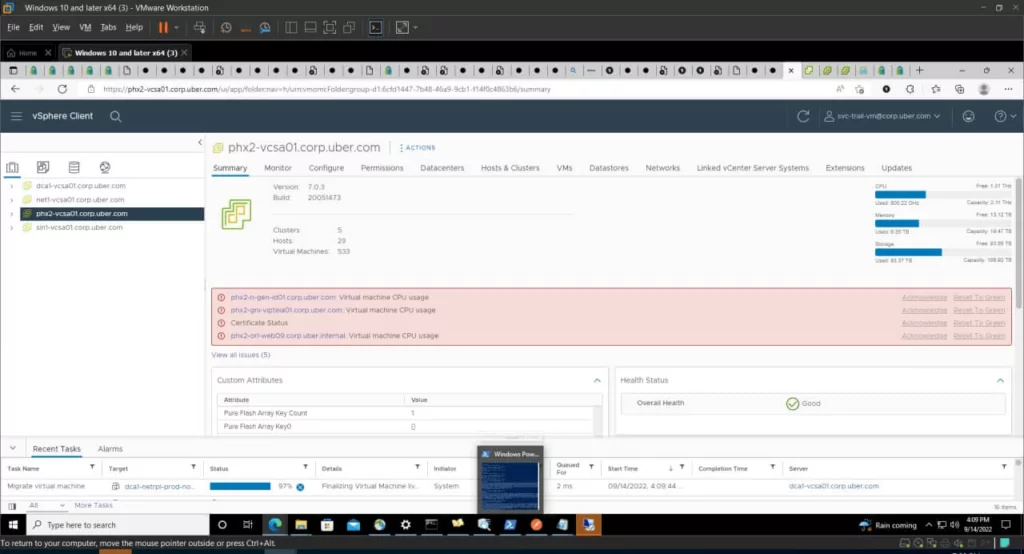
The hacker apparently succeeded in getting entry to further internal systems (GCP, AWS, financial information) by using privileged credentials that were also exposed after gaining access to the network. These credentials (Thycotic Private Access Management admin username and password) were included in PowerShell scripts.

Uber HackerOne Admin Panel Also Has Been Compromised
Sam Curry, a security specialist at Yuga Labs, claims that the hacker also had access to the organization’s HackerOne bug bounty program, where they left comments on all the bug bounty tickets.
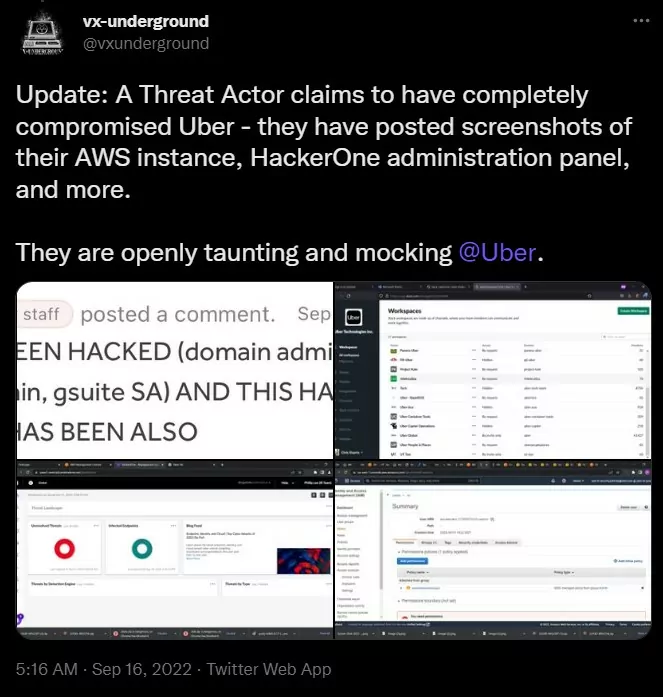
The threat actor likely acquired data and source code from Uber, but if the company’s vulnerability reports and possible information about unpatched flaws are stolen, it may pose a greater risk. Because the compromised HackerOne threat reports may have been downloaded by the hacker, there is a risk that they will be sold along with other stolen data and exploited by other threat actors.
In an update, Uber stated that there is no evidence that users’ sensitive information was compromised. Though this attack on Uber and recent incidents involving Twilio and LastPass demonstrate how social engineering remains a threat to organizations.
Researchers explain after an analysis that the threat actor might be related to a recent stealer malware activity. The logs in Uber’s hack were found to be posted for sale between September 12 and 14 in hacker marketplaces. Further details can be found in this thread.



































