
From Hacktivists to Cyberterrorists: Understanding Modern Motivations
As digital infrastructure grows, the landscape of cyber threats has evolved in complexity and scope. What started as isolated incidents of hackers challenging systems for notoriety has now escalated into a full spectrum of threats—from hacktivists fighting for political or social change to cyberterrorists aiming to dismantle critical infrastructure. These actors, while differing in motives and methods, share a common goal of disrupting the digital environment. Understanding their motivations and tactics is crucial for building robust defense mechanisms in today’s interconnected world.

Representative image generated by artificial intelligence
Defining Hacktivists and Cyberterrorists
Hacktivists and cyberterrorists, although often conflated, have distinct motivations and methods. Hacktivists aim to promote political or social change through disruptive means, while cyberterrorists seek to create widespread fear and destabilization, particularly targeting critical infrastructure.
Motivations Behind Modern Cyber Threats
The motivations driving modern cyber threats vary significantly between hacktivists .
- Hacktivists: In 2021, the hacking group Anonymous launched a campaign against Belarus’ government following the controversial re-election of President Alexander Lukashenko. Anonymous hacked into government systems, leaked sensitive documents, and disrupted operations to protest the suppression of dissent and the violation of human rights in Belarus. This campaign was part of their larger goal to promote freedom and transparency.
- Cyberterrorists: In 2022, the pro-Russian hacker group Killnet conducted a series of cyberattacks targeting countries supporting Ukraine during the Russian invasion. One of their major attacks was against Lithuania in June 2022, which resulted in a large-scale Distributed Denial of Service (DDoS) attack that crippled state systems and business services. This attack aimed to create economic disruption and send a political message to nations opposing Russia.
Evolution of Modern Cyber Threats
The rise of the digital age has not only expanded the opportunities for innovation but also broadened the scope of potential threats. While hacktivist movements emerged as early as the 1990s, modern cyberterrorism only began to take shape as global networks became integral to national and economic security. These threats do not discriminate—they target individuals, corporations, and governments alike.
Hacktivists often employ techniques like DDoS attacks and data leaks to make a political statement, such as Anonymous’ aforementioned actions. On the other hand, cyberterrorists deploy advanced tactics like ransomware or attacks on critical infrastructure to inflict widespread damage. This shift from isolated attacks to global campaigns highlights the growing sophistication and danger of modern cyber threats.
Common Types of Cyber Threats
- Malware: Malicious software designed to damage, disrupt, or gain unauthorized access to systems. Variants include viruses, worms, trojans, and ransomware.
- Phishing: Attackers trick victims into sharing sensitive information, often by impersonating trusted entities like banks or well-known companies.
- Distributed Denial-of-Service (DDoS) Attacks: Overwhelm a system with traffic, rendering it unusable. DDoS is commonly used by hacktivists for protests, as seen in “Operation Payback.”
- Ransomware: A type of malware that encrypts a victim’s files, demanding a ransom for their release. This has been a popular tool in cyberterrorism due to its destructive nature.
- Social Engineering: Manipulating individuals into divulging confidential information. Often combined with phishing for maximum effect.
Historical Context of Hacktivism and Cyberterrorism
The origins of hacktivism and cyberterrorism can be traced back to the early days of the internet, when the digital realm became a new frontier for protest and warfare. As the internet matured, both activists and malicious actors recognized its potential to influence political, social, and economic landscapes. Over time, the motivations behind cyberattacks diverged, with hacktivists using their skills to promote freedom and justice, while cyberterrorists aimed to spread fear and cause long-term damage.
Key Events in Hacktivism
Hacktivism has evolved dramatically over the past few decades. Some of the most significant moments include:
- 1990s: The Cult of the Dead Cow (cDc), an influential hacking group, developed Back Orifice, a tool designed to expose vulnerabilities in Microsoft Windows. This marked one of the first major acts of hacktivism, highlighting the power of software exploitation for raising awareness about security flaws.
- 2000s: Anonymous, a decentralized hacktivist collective, emerged as a champion of freedom of information. The group launched high-profile attacks against governments, corporations, and organizations, including the Church of Scientology and Visa, to protest censorship and corruption.
- 2010s: Hacktivists played a pivotal role in the Arab Spring, using social media and hacking tools to organize protests, defy government surveillance, and disseminate critical information. These efforts helped mobilize people and amplify the voices of oppressed communities in the Middle East.
Recent Example: 2023 Attack on Russian State TV by Anonymous
A more recent example of hacktivism occurred in 2023, when Anonymous targeted Russian state television in protest of the invasion of Ukraine. The group hacked into broadcast systems, interrupting regular programming to display anti-war messages and images, a direct attempt to counter Russian propaganda.
During the attack, Anonymous employed a variety of techniques, including DDoS (Distributed Denial of Service) attacks and website defacement. They also used tools like LOIC (Low Orbit Ion Cannon), a popular DDoS tool within hacktivist circles, to flood Russian government websites with traffic, causing temporary outages.
This attack demonstrated the persistent power of hacktivism to challenge state narratives and disrupt the flow of information, even in tightly controlled environments.
Mitigating Risks from Cyber Actors
To mitigate risks from both hacktivists and cyberterrorists, organizations must implement a comprehensive cybersecurity strategy. This includes:
- Proactive Defense Strategies
- Education and Public Awareness
- Collaboration
- Incident Response Plans
SOCRadar’s Threat Actor Intelligence: Your First Line of Defense
SOCRadar’s Threat Actor Intelligence Module provides unparalleled insights into the activity of global cyber actors. With comprehensive dashboards, users can track threat actors, monitor targeted countries and industries, and stay informed on emerging risks.
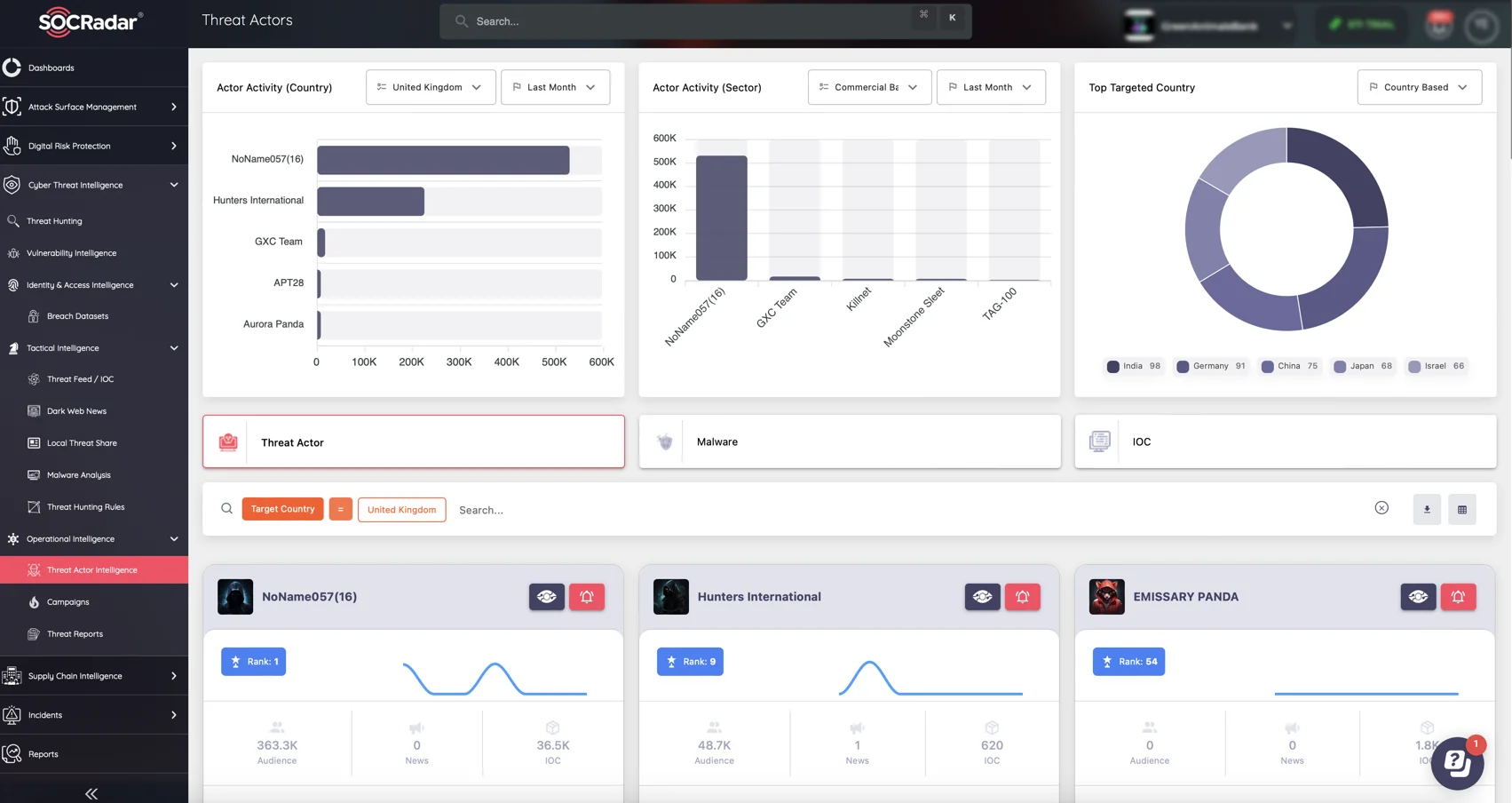
Track global threat actors and their activities with SOCRadar’s Threat Actor Intelligence Module.
Features include:
- Actor Profiles: Analyze the behavior and tactics of active cyber actors.
- IOC Tracking:Access the Indicators of Compromise linked to specific groups.
- Real-Time Insights: Detect and mitigate threats targeting your organization or industry.
Equip your team with actionable intelligence to defend against evolving cyber adversaries. With SOCRadar, you’re not just reacting to threats—you’re staying ahead of them.
The growing threat of hacktivism and cyberterrorism requires coordinated responses from governments, corporations, and individuals. By leveraging tools like SOCRadar’s XTI and fostering collaboration, we can reduce the risks posed by these actors and better protect our increasingly digital world.



































