
Hot Topic Data Breach: A Massive Leak Exposes Millions of Customer Records
Data breaches have become increasingly common, affecting millions of users across various sectors. One of the latest high-profile incidents has impacted Hot Topic, a well-known retail brand popular for its alternative fashion and pop culture merchandise.
This breach has put the personal information of millions of customers at risk, including data from Hot Topic’s associated brands, Box Lunch and Torrid. With sensitive details like email addresses, phone numbers, and weakly encrypted credit card information exposed, this breach underscores the importance of strong data security practices and highlights the significant risks posed to both companies and consumers.
Overview of the Hot Topic Data Breach
The data breach involving Hot Topic and its affiliated brands, Box Lunch and Torrid, has exposed sensitive information from over 54 million customer accounts. This breach was first disclosed on a Dark Web forum by a threat actor who initially claimed to have obtained 350 million records and demanded a ransom of $20,000. Later, the hacker attempted to sell the data outright, reducing the price to $4,000.
Cybersecurity firm Atlas Privacy, which has been analyzing the stolen data, confirmed that the compromised database is approximately 730GB in size and contains email addresses, phone numbers, physical addresses, birth dates, purchase histories, and partially encrypted credit card information. The weak encryption on the credit card data, described as “lightly encrypted,” poses an added security risk as it can potentially be decrypted.
The data, spanning from 2011 to October 19, 2024, suggests that information has been accumulated over a long period, highlighting potential issues in secure data storage and encryption protocols.
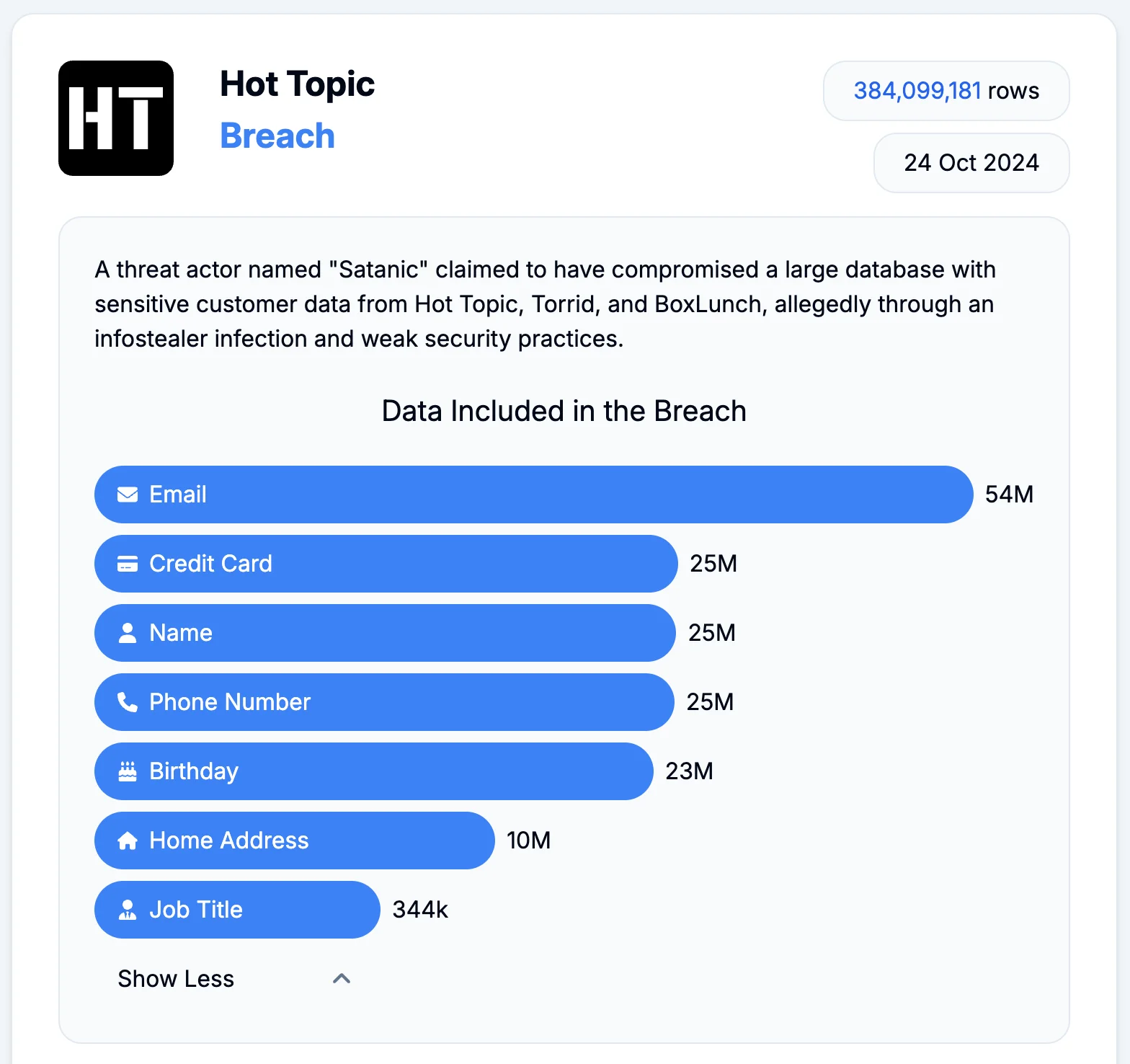
Data included in the breach (Source: databreach)
The security firm also validated the breach, noting that roughly half of the email addresses in the stolen data set had not appeared in past breaches, making this incident particularly concerning for both the company and affected customers.
Dark Web Allegations and Database Listings
On October 21, 2024, a threat actor initially posted on BreachForums under the alias “Satanic,” claiming a breach of two major U.S. companies—Hot Topic and Box Lunch—and detailed a vast amount of customer information.
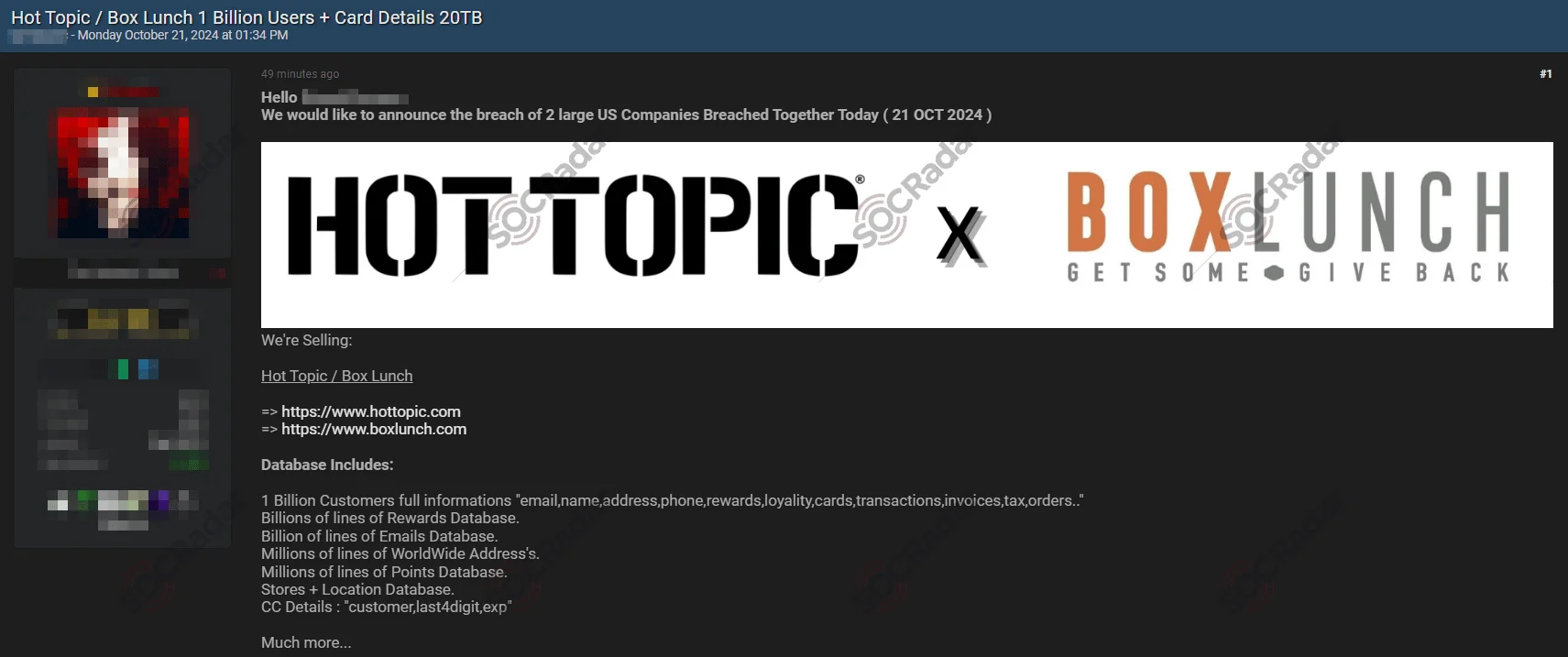
BreachForums Initial Post (SOCRadar Dark Web News)
Soon after, the post was edited to include a third company, Torrid, with the actor claiming they possessed data on 350 million customers. The revised post specified that the data included emails, names, addresses, phone numbers, dates of birth, and partial credit card details, among other sensitive information. The actor set the price at $20,000 for the entire database and shared a Telegram contact for interested buyers.
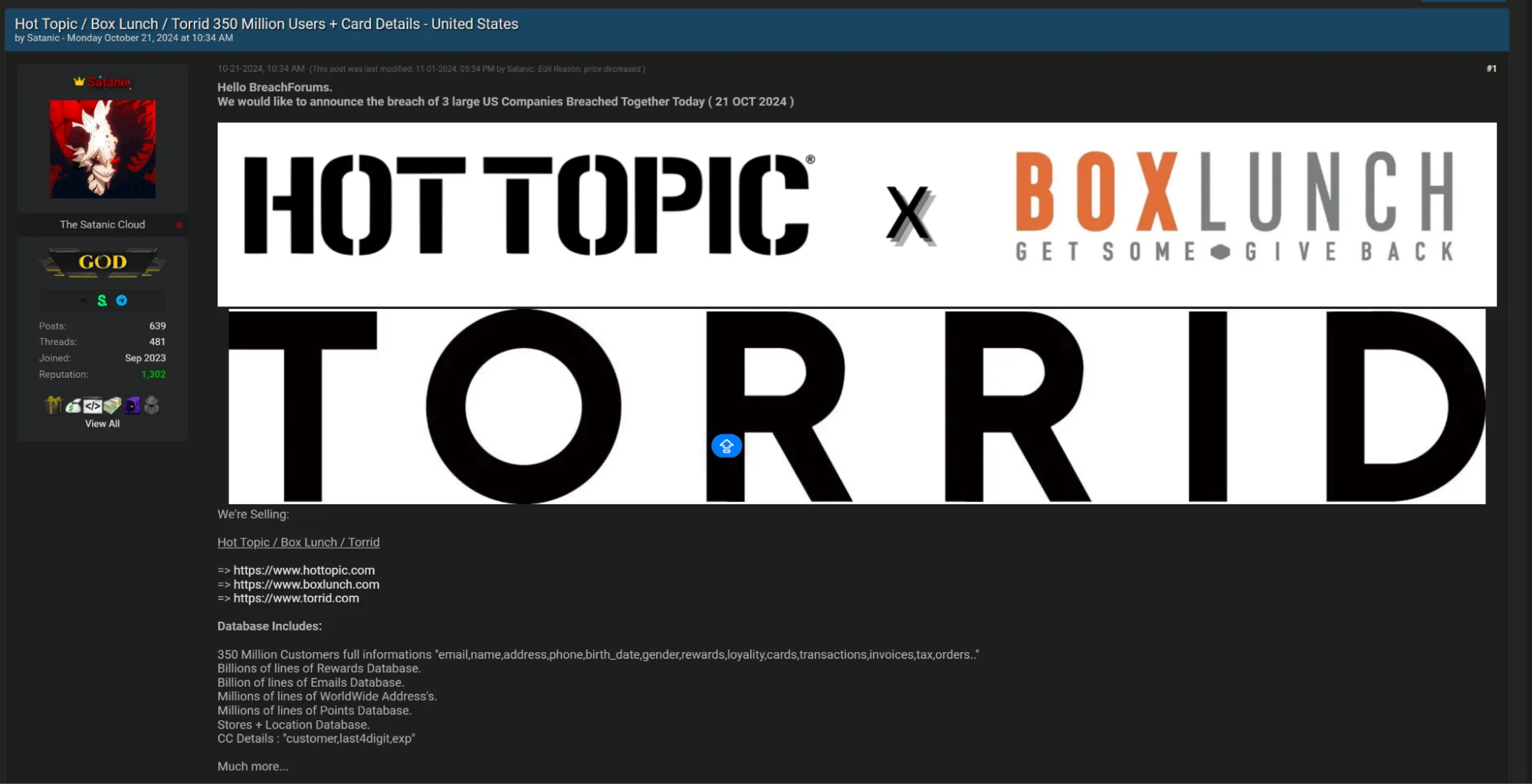
Edited BreachForums Post (SOCRadar Dark Web News)
The following day, on October 22, the same threat actor, this time using the alias “Mrxdark,” posted on a popular Russian-speaking hacker forum to further promote the sale. This additional post mirrored the edited details from BreachForums, aiming to reach a broader audience and accelerate the sale. The consistent information shared across both forums indicated a coordinated effort by the threat actor to market the data to as many potential buyers as possible.
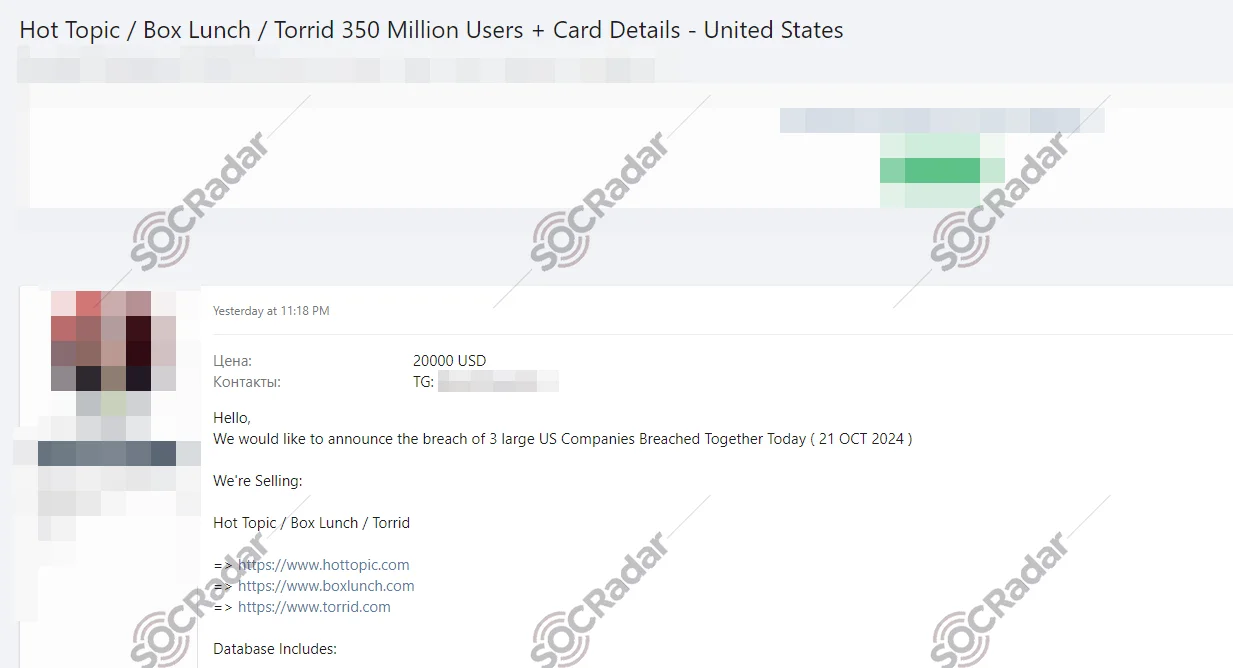
Russian-Speaking Forum Post (SOCRadar Dark Web News)
SOCRadar Dark Web Monitoring provides a comprehensive solution for identifying and tracking data breaches, threats, and other malicious activities across dark web forums, and illegal marketplaces. By scanning in real-time, this service detects emerging risks, giving organizations critical information on potential threats that could impact their security. SOCRadar’s monitoring capabilities extend to alerting businesses about exposed data and identifying early signs of attacks, empowering users to respond swiftly and minimize potential damage from data leaks and cyberattacks.
SOCRadar Dark Web News
Origins of the Breach
On October 23, researchers suggested that the Hot Topic data breach likely originated from an information stealer malware infection. This malware reportedly compromised login credentials for a third-party data unification service used by Hot Topic, potentially giving the attacker unauthorized access to sensitive data.
Investigation revealed over 240 compromised credentials on the infected device, including corporate access credentials for Hot Topic and its subsidiary, Torrid. Among these, researchers identified login credentials for Hot Topic and Torrid’s cloud environments on platforms like Snowflake, Azure, and Looker, highlighting potential exposure points within these cloud services.
Organizations looking to safeguard their own systems from similar risks can benefit from SOCRadar’s Identity & Access Intelligence module, which offers comprehensive monitoring of compromised credentials in real time. By tracking stealer logs and other sources of credential leaks, SOCRadar’s Identity & Access Intelligence helps organizations detect and address compromised credentials before they’re exploited by attackers. This tool not only identifies when credentials are leaked but also provides contextual information about the stealer and any associated malware, enabling companies to remove threats entirely and secure affected systems.
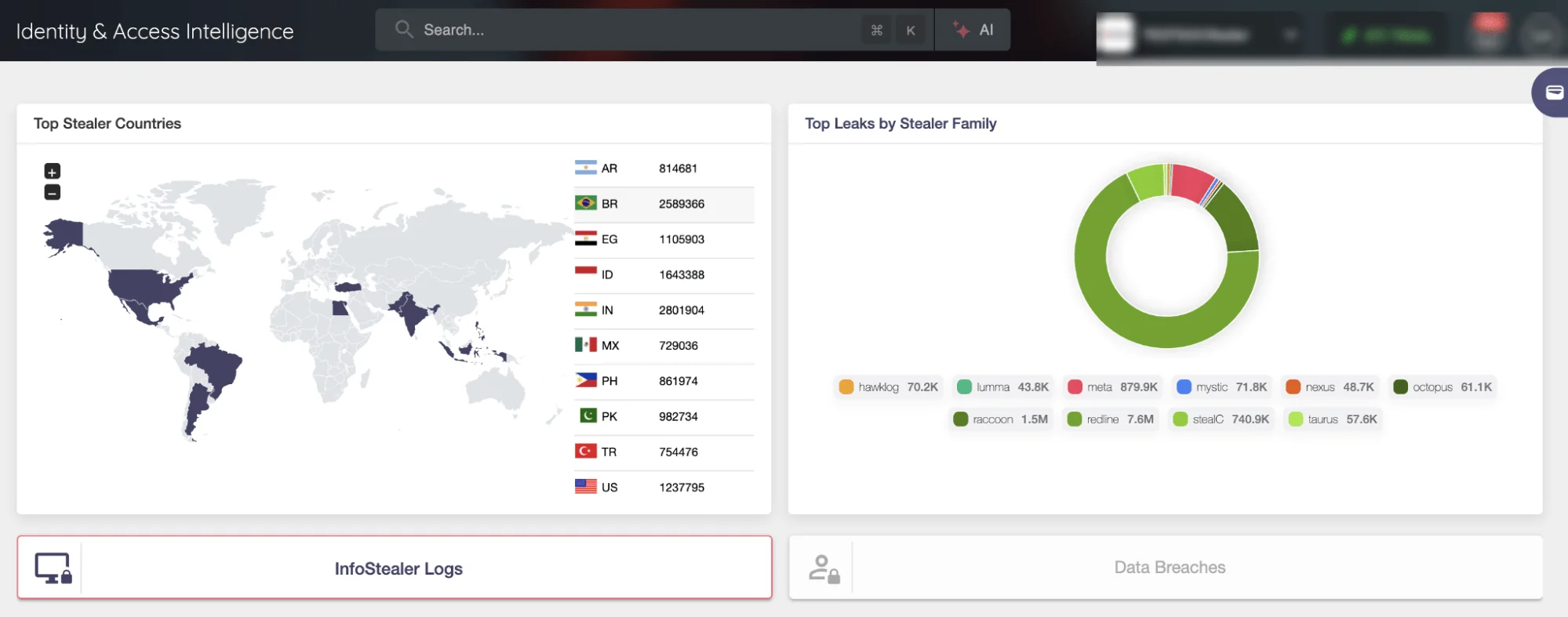
SOCRadar Identity & Access Intelligence
SOCRadar’s proactive approach helps ensure that leaked credentials are isolated and removed from threat actor access, allowing businesses to reinforce security measures and minimize the likelihood of further exploitation.
Conclusion
The Hot Topic data breach has exposed millions of customers to various security risks, particularly identity theft, financial fraud, and potential account takeovers. The compromised data includes detailed personal information, such as names, email addresses, physical addresses, and partial credit card data. Additionally, loyalty and reward program details could be exploited by attackers to gain unauthorized access to customer accounts, as many points in the dataset reportedly do not expire.
For affected users, experts recommend taking immediate precautions to minimize potential harm. Customers should monitor their financial accounts for any suspicious activity, especially if they’ve used the same credentials on multiple platforms. Changing passwords and enabling multi-factor authentication (MFA) across all accounts are highly advised. Additionally, users are encouraged to remain vigilant against phishing attempts, as cybercriminals may use the leaked information to craft convincing phishing emails.




































