
How Can SOC Analysts Benefit from Cyber Threat Intelligence?
A modern-day SOC is made from three components: people, processes, and technologies. In the people factor, a SOC team accounts for the provision of IT security services via detecting potential cyber threats and attacks actively, proactively, and predictively with responding to cyber incidents as quickly and promptly as well.
Daily Tasks of SOC Analysts
The SOC analysts are an integral part of a SOC team for whom they are tasked with continuously monitoring and trying to detect potential cyber threats, triaging the alerts, and properly escalating them. SOC analysts are kept on their toes twenty-four hours a day to perform effective and efficient monitoring, detection, analysis, triaging, and escalation processes. While performing these critical tasks, SOC Analysts should utilize CTI (Cyber Threat Intelligence) to serve many valuable purposes of cyber security missions.
How CTI Makes SOC Analysts’ Tasks Easier?
CTI can add value across security functions for all sizes of organizations. While SOC analysts face an increasing workload entailing a large volume of security events and alerts needed to be investigated that are causing their burnout, CTI can help automatically prioritize and filter alerts for them. It also provides the most critical vulnerabilities with external insights and contextual data for the vulnerability management process. Moreover, CTI can serve other critical security processes with data enrichment; for instance, it can be a superior starting point for threat hunting accordingly.

CTI can collect and aggregate information from external sources gained from dark web resources that verify and enrich this information to identify what kind of threat and its severity level. Furthermore, CTI informs security gaps related to a specific threat actor’s infrastructure knowledge that may produce technological breakthrough data, including key insights on them like their behaviors associated with TTPs (Tactics, Techniques, and Procedures). CTI enables SOC analysts to understand the current threat landscape and take the necessary steps.
Which Components Exist in Custom CTI Feeds?
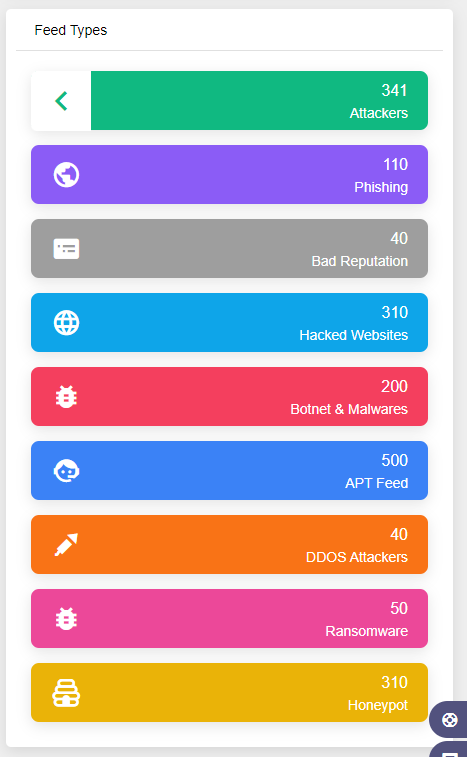
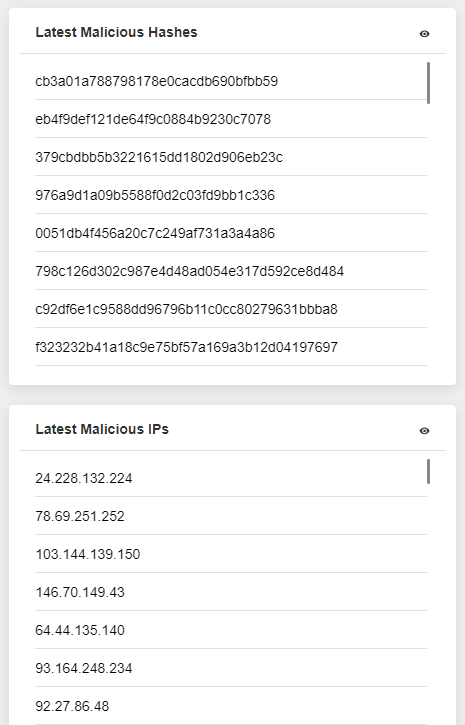
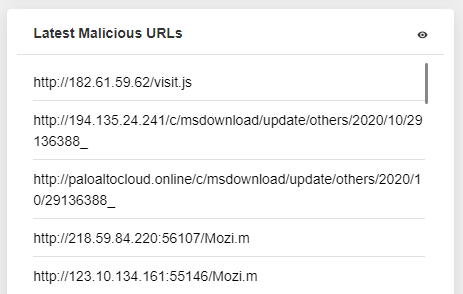
With the aim of effective security visibility and threat management processes, although it can be challenging to filter useful and actual data, the most valuable and actionable data has proven to be event data from threat intelligence feeds. The custom CTI Feeds cover all major attack vectors like malicious URLs, phishing scams, malware, spam sources, botnets and trojans, adware/spyware, ransomware, and more. SOC analysts can use actionable intelligence data to improve security operations’ accuracy and consistency. They have enough to discover how to pivot on your extracted indicators to provide a more holistic view of the threat via CTI.
What Questions Can CTI Platforms Answer?
CTI platforms can assist in lifting the veil on cyber threat actors by getting better answers to the questions below to SOC analysts.
- What are the latest cyber threat trends?
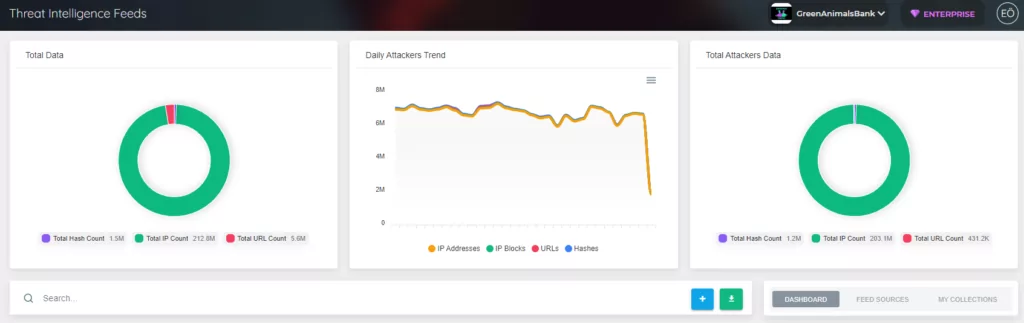
- When and where have threat actors been seen on attack surfaces recently?
- Where are the threat actors and the malicious variants most active by countries or industries?
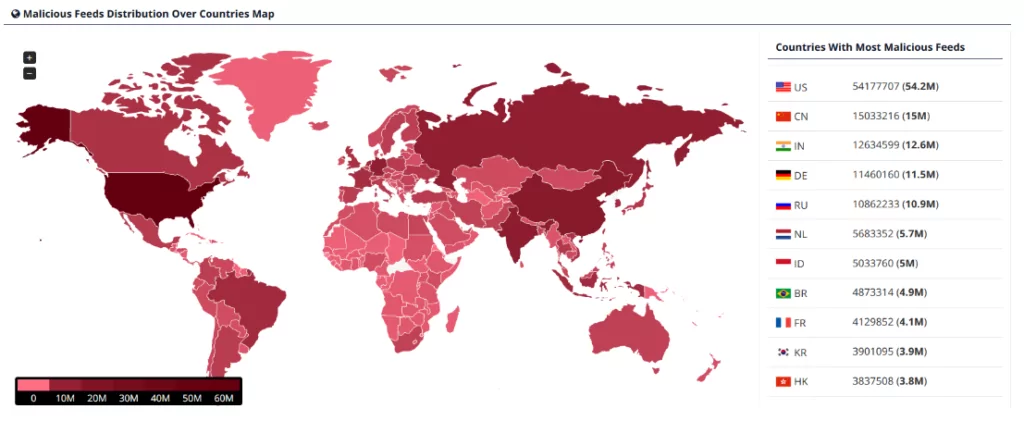
- Is there any active and coordinated campaign against a specific target?
- Which type of malware or tools are currently available and utilized for cyber-attacks?
- Which malicious activities have been observed on the enterprise’s face?
- What are the newly discovered vulnerabilities (CVEs) that have been exploited actively, and how to take action to mitigate this cyber risk?
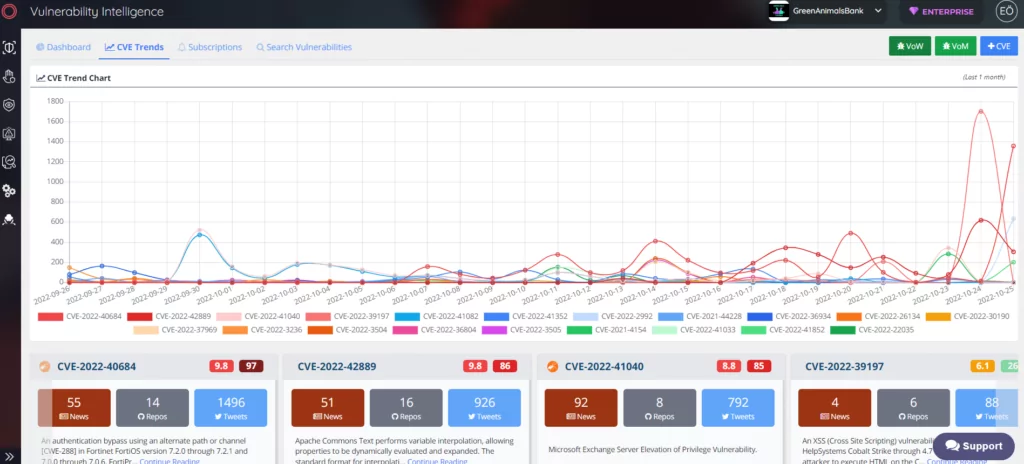
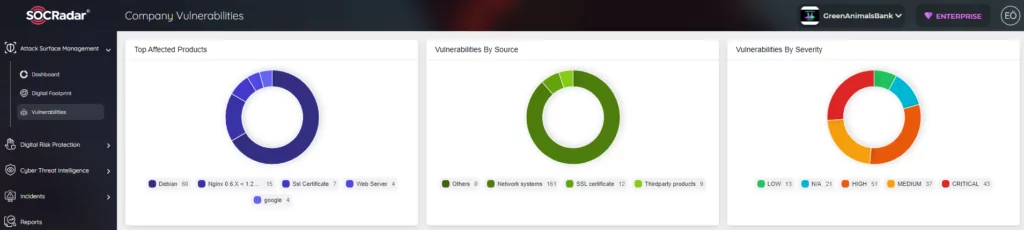
- What are the TTPs related to exploits and payloads used in current malicious activity, and how can this mapping be used for contextualizing and categorizing attacks?
- What are the indicators of compromise or attack (IoCs / IoAs) for intended cyber activities, and how to reactively and proactively respond or mitigate them?
Conclusion
The SOC can blend data generating various products that connect CTI, from daily updated data feeds via APIs to annual threat intelligence reports in CTI platforms. SOC analysts should get exact and better information through outreach and engagement of CTI, including external and internal sharing knowledge, which may be the best way to take a step forward and lead SOCs. For providing and enabling SOC effectiveness, it has been recommended to examine and explore CTI solutions on how to ingest and process threat intelligence information properly and integrate it into your IT security Operations.


































