
How is Threat Intelligence Used to Monitor Criminal Activity on the Dark Web?
The dark web is a part of the Internet that differs from the regular Internet as it is a network that offers anonymity and privacy. Because of its structure, it has evolved into a network where cyber attackers engage in various illegal activities and have access to marketplaces, forums, and communication channels. As a result, cybersecurity experts employ threat intelligence to monitor and prevent criminal activity on the dark web. This article will explore how threat intelligence can detect and monitor criminal activity on the dark web.
Dark Web Criminal Activities and the Role of Threat Intelligence
The Internet has three parts; surface, deep, and dark. The dark web has a completely different structure and is the most secret and difficult-to-access part. It hosts hidden sites and content on a network that can be accessed anonymously. This allows criminals to carry out illegal activities and unauthorized transactions.
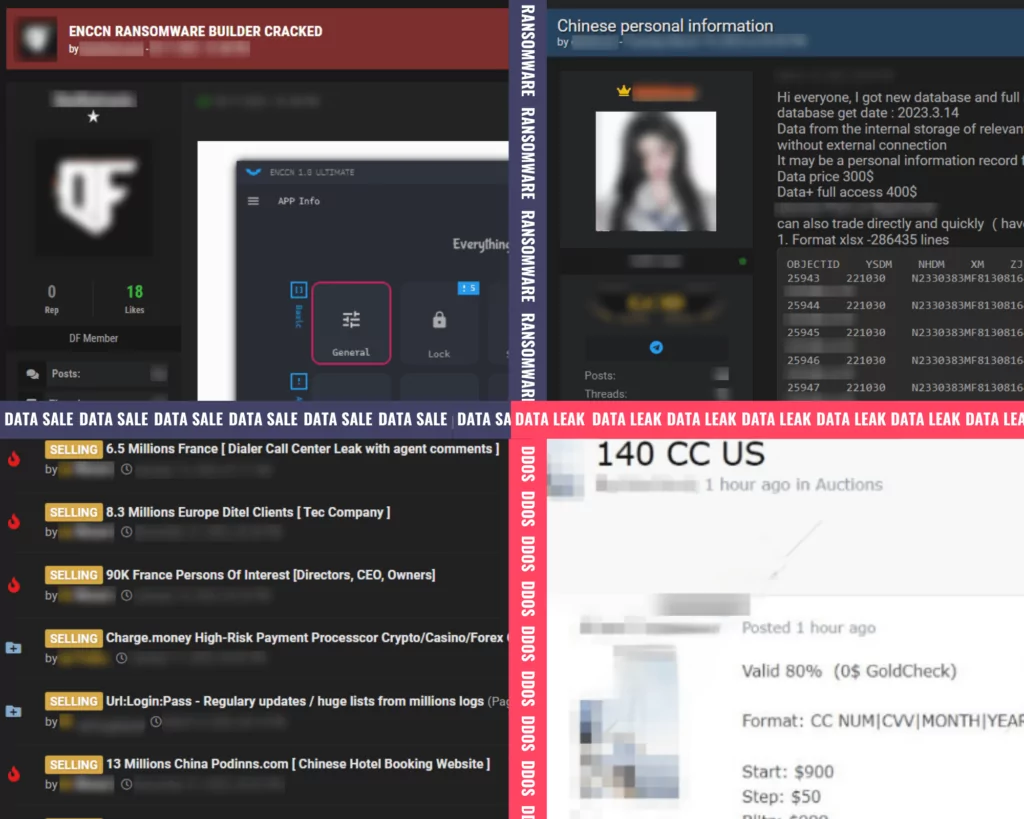
Various illegal activities on the dark web include online marketplaces, ransomware, cyber espionage, botnets, internet fraud, and human trafficking. Attackers who want to profit from these activities carry out transactions using cryptocurrencies. According to Forbes’ research, one of the five reasons for the rise of the dark web and cybercrime activities is that the anonymity of funds flows through cryptocurrencies.
Privacyaffairs.com‘s annual report of credit card data, forged documents, and hacked information sold on the dark web list the average price of each. The highest price category is malware, while the lowest is social media. Price ranges suit every user in the categories sold on the dark web. This situation shows that the activities appeal to a wide audience.

Cyber threat intelligence specializes in detecting, collecting data, analyzing, and interpreting cyber threats to an organization in advance. The dark web is a source of cyber threat intelligence for monitoring cybercrime activities. Cyber threat intelligence tracks illegal activities, marketplaces, and shared sensitive data on the dark web. Analyzing data collected from multiple sources through threat intelligence makes the dark web ecosystem more intelligible, and potential threats are prevented before they become a major problem.
Threat Intelligence Collection Techniques and Tools
Cyber security analysts use various techniques when gathering intelligence on the dark web. Some of these techniques are as follows:
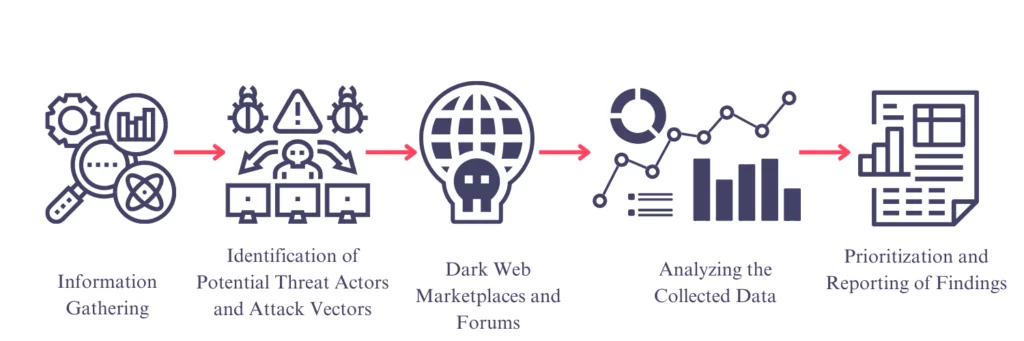
- Information Gathering: The information gathering phase is about gathering as much information about the organization as possible. In the information-gathering phase, research should be done on the keywords to be searched on the dark web, and a keyword list should be prepared. A massive list of keywords about the organization is created by using publicly available sources such as the name of the organization, its affiliated sub-companies, and social media accounts. Google Dork, Ubersuggest, and Keyword Tool can be used in keyword research.
- OSINT: One of the best ways to gather information. The most important part of collecting information with OSINT is to identify sources. These sources include dark web forums, social media platforms, marketplaces, or search engines designed for dark web searches.
- Identification of Potential Threat Actors and Attack Vectors: Hacktivists, cybercriminals, or state-sponsored actors should be identified. The vulnerabilities in the network or software that attackers can target should be identified. Identifying potential attack vectors such as phishing and social engineering is also important.
- Dark Web Marketplaces and Forums: Marketplaces usually sell services such as stolen data, malware, hacking tools, and phishing activities. Marketplaces should be identified first to gather intelligence. Each marketplace has its search features and interfaces. The data to be searched is determined to be related to malware, hacker group, or cyber attack method, and the data is collected. (Grey Market, Russian Market, Brian’s Crabs Club, Kingdom Market, etc.) Forums are communities where cyber criminals can discuss and share various topics. They provide valuable information about threat intelligence and clues about how cyber attacks are carried out. When choosing a forum, one can choose between public forums and private forums. In order to access private forums, an invitation is required. DarkSearch or OnionSearch, which are Dark Web search engines, can be used to increase the number of forums. Selected forums should be monitored during certain periods. Gathering intelligence by interacting with communities and staying in contact with cyber criminals is useful.
- Analyzing the Collected Data: Data analysis should be performed to ensure the accuracy of the attackers’ goals, objectives, methods, and information collected on the Dark Web. In data analysis, the collected data is classified and analyzed. Analysis processes vary depending on the type and source of the data. Data mining and machine learning techniques can be used at this stage.
- Prioritization and Reporting of Findings: Prioritization is classifying the intelligence collected. In this way, it will be easier for the organization to decide which threat to act on first. Reporting is used to inform the organization about cybersecurity issues and to enable the management to make the right decisions.
Navigating the complex Dark Web environment can be difficult. Tools are used at this point. Some practical tools and search engines are
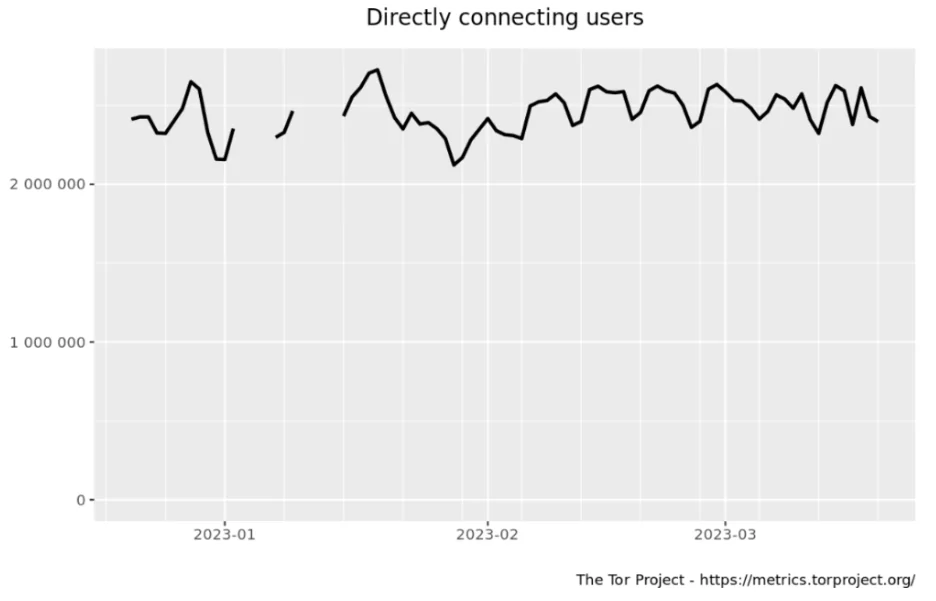
- Tor Browser: It is the most widely used web browser for Dark Web access. The Tor network uses layer encryption. Dark Web forums, marketplaces, and other sites can be browsed with Tor Browser.
Tor Browser estimates the number of users by analyzing the requests it routes to relays and bridges and provides publicly available graphs.
- Candle: A search engine contains more than 100,000 websites for marketplaces and forums on the Dark Web and provides the most relevant results for searches.
- Maltego: An open-source data mining tool that collects intelligence from the Dark Web and various sources. It can be used to analyze data such as social media profiles, email addresses, phone numbers, etc., collected on the Dark Web.
- DarkSearch: A search engine indexes content on the Dark Web. It can be used to search websites, forums, and other online resources that are not indexed by typical search engines.
- TorBot: “.onion” is a tool that describes the sites with the extension, takes data, and checks whether the links are up or not. In this way, many tasks are performed at once during the research.
By using these tools and search engines, organizations can obtain valuable information about the tactics and techniques used by cybercriminals on the Dark Web.
Dark Web Threat Intelligence Challenges and SOCRadar Solutions
The dark web is a challenging network that requires specialized skills, expertise, and extensive knowledge of sources to gather threat intelligence. On the dark web, organizations can only collect individual intelligence in a limited way, as invitations are required to access certain areas or communities. SOCRadar communicates with specific communities to access critical intelligence on the dark web (This communication is done through SOCRadar ethical guidelines and standards). SOCRadar has a massive list of sources and identifies new sources daily in the rapidly developing dark web environment.
Due to the large volume of dark web intelligence, the information obtained may contain fraudulent or deceptive content, making it difficult to determine the accuracy/precision of the information. Overcoming this challenge may require the use of advanced data analysis tools, machine learning, and artificial intelligence algorithms. SOCRadar is a platform that helps organizations with large volumes of dark web intelligence with monitoring. In addition, it uses artificial intelligence and machine learning algorithms to score the risks identified with risk scoring. In this way, organizations can prioritize risks.
The dark web constantly expands, and new tactics, techniques, and tools emerge. Organizations need to monitor trends regarding these threats. SOCRadar is an effective platform for collecting threat intelligence data on the dark web by providing real-time monitoring, risk scoring, and automation. Sectoral and regional dark web news, another feature of SOCRadar, enables organizations to stay informed by following news not only about themselves but also about their sector and the region they are located in. It also uses agile and flexible intelligence collection processes to adapt to changing threat environments. With the right approach, SOCRadar’s intelligence collection efforts help organizations avoid cyber threats and protect their critical assets and data.
Find out how popular you are on the dark web.
Find out if your data has been exposed.




































