
How Stealer Logs Target E-Commerce Giants During Black Friday
As the holiday season approaches, Black Friday stands out as one of the busiest shopping days of the year. For consumers, it’s an opportunity to snag deals from the comfort of their homes. For retailers, it’s a chance to reach record-breaking sales. However, amidst the online frenzy, Black Friday also attracts a darker element: cybercriminals eager to exploit the surge in online activity.
With millions of consumers visiting e-commerce sites, making purchases, and sharing sensitive information, Black Friday offers an ideal environment for cyber threats to thrive. The sheer volume of transactions opens a larger window of opportunity for attackers, and the urgency to secure limited-time deals often makes shoppers more susceptible to phishing scams, fake websites, and other forms of online fraud. For threat actors, the potential rewards are enormous—both in terms of financial gain and valuable data.
One of the most alarming cyber threats during this period is the rise in stealer logs. These are malicious logs created by information-stealing malware that silently captures sensitive data from compromised devices. Stealer malware works in the background, gathering data such as login credentials, payment information, and browsing history, all without the user’s knowledge.
Why E-Commerce Giants Are Prime Targets
Stealer malware fundamentally differs from other attacks or tools, as it does not focus on specific companies or high-value individuals. Instead, it spreads broadly through malicious websites and links, indiscriminately infecting various devices. Once installed, stealer malware silently collects sensitive data from compromised devices, including passwords, browser cookies, session tokens, and autofill information. The lack of targeted deployment means that any internet user, whether an employee or a private individual, may unknowingly contribute to data exfiltration schemes that put corporate security at risk.
This approach represents a significant and unique threat to e-commerce companies. Given the widespread use of online shopping, employees in e-commerce businesses often interact with personal and corporate email accounts linked to various digital services. These email accounts—and their associated credentials—can be found in stealer logs and can serve as a convenient entry point for threat actors.
Threat actors can exploit these credentials directly instead of navigating complex security systems. For e-commerce giants, the stakes are particularly high. A breach’s consequences extend beyond monetary losses; customer trust and brand reputation are also at risk.
Case Studies: Real-World Incidents
SOCRadar’s analysts have thoroughly examined data collected from the top 10 e-commerce domains to gain a precise understanding of the types of information targeted by threat actors and the geographical distribution of affected victims.
| Searched Domains |
| aliexpress.com |
| amazon.com |
| ebay.com |
| etsy.com |
| flipkart.com |
| ozon.ru |
| rakuten.co.jp |
| temu.com |
| walmart.com |
| wildberries.ru |
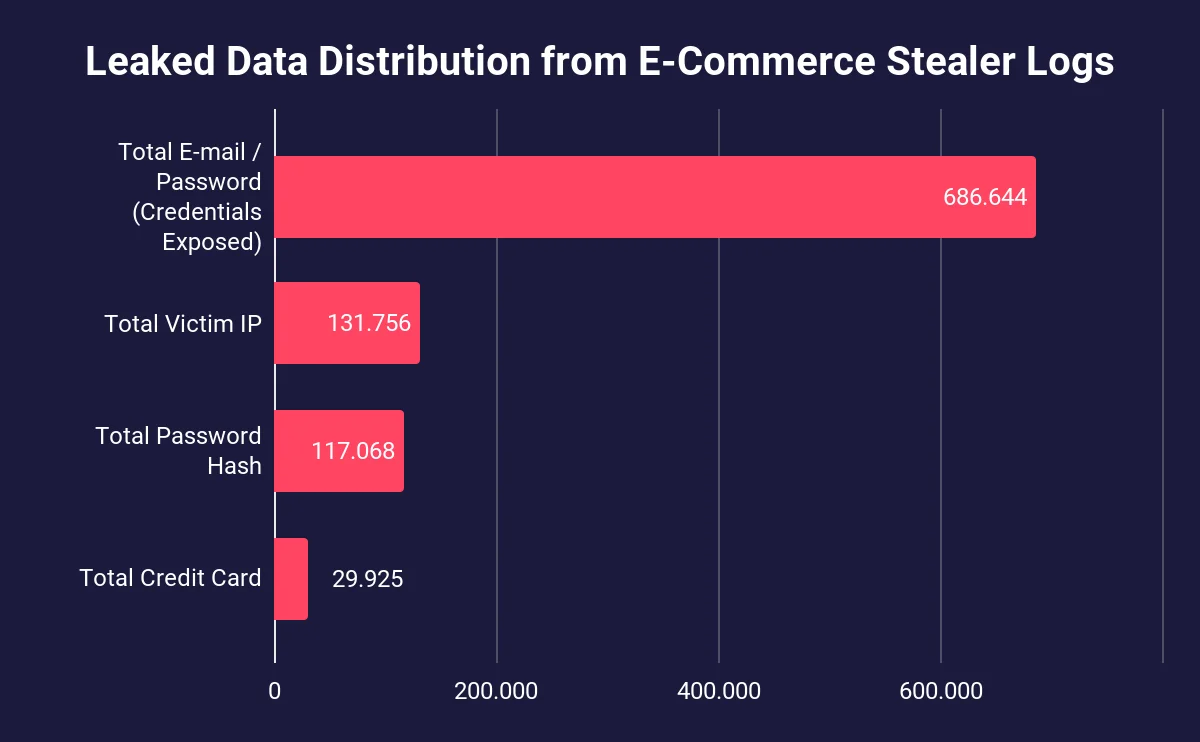
Data distribution of stealer logs
This analysis contains 686,644 email-password combinations, highlighting the scale of credentials potentially available for threat actors and the need for Identity & Access measures in e-commerce. Additionally, the most concerning is the collection of 29,925 credit card details, representing a direct financial threat to affected users and increasing the likelihood of subsequent fraud incidents.
The breadth of this data reminds us of the critical importance of data security measures in digital marketplaces.
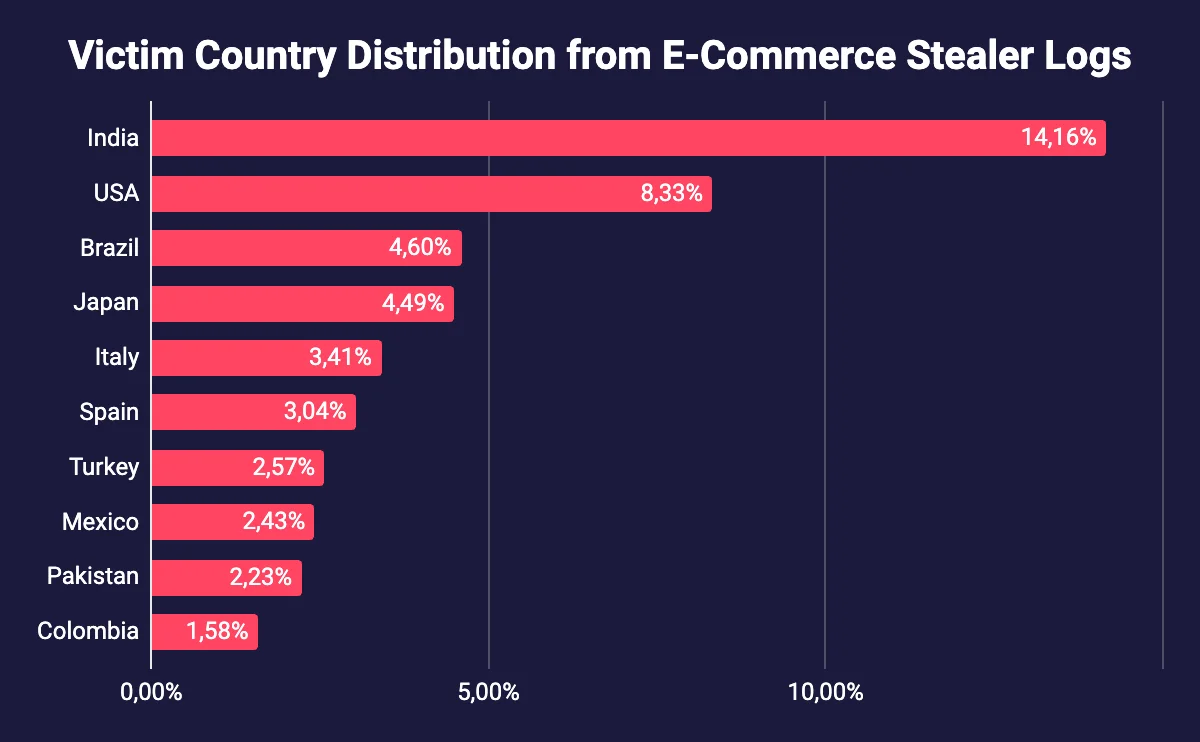
Country distribution of Stealer Logs
When we look at the location of victims, our analysis reveals that India is the most affected country, with 14.16% of compromised credentials belonging to users based there. This high percentage points to India’s large and increasing digital user base.
The United States follows, with 8.33% of credentials exposed, underscoring a persistent threat to one of the world’s largest e-commerce markets.
Brazil, at 4.6%, ranks third, highlighting vulnerabilities within its expanding online economy.
These insights reflect the broader global reach of stealer malware and suggest that regions with growing digital adoption may be particularly attractive to cyber actors seeking to exploit their data.
A common misconception regarding stealer logs lies in how they function. Many organizations respond to the discovery of employee credentials in stealer logs by updating passwords. However, this approach often provides temporary relief, as the issue frequently reoccurs quickly. This recurrence is typically due to stealer malware still embedded within company devices, continuously harvesting sensitive data. SOCRadar’s Identity & Access Intelligence module addresses this challenge by detecting these hidden threats and enabling organizations to thoroughly cleanse their systems, ensuring comprehensive protection against ongoing data leaks.
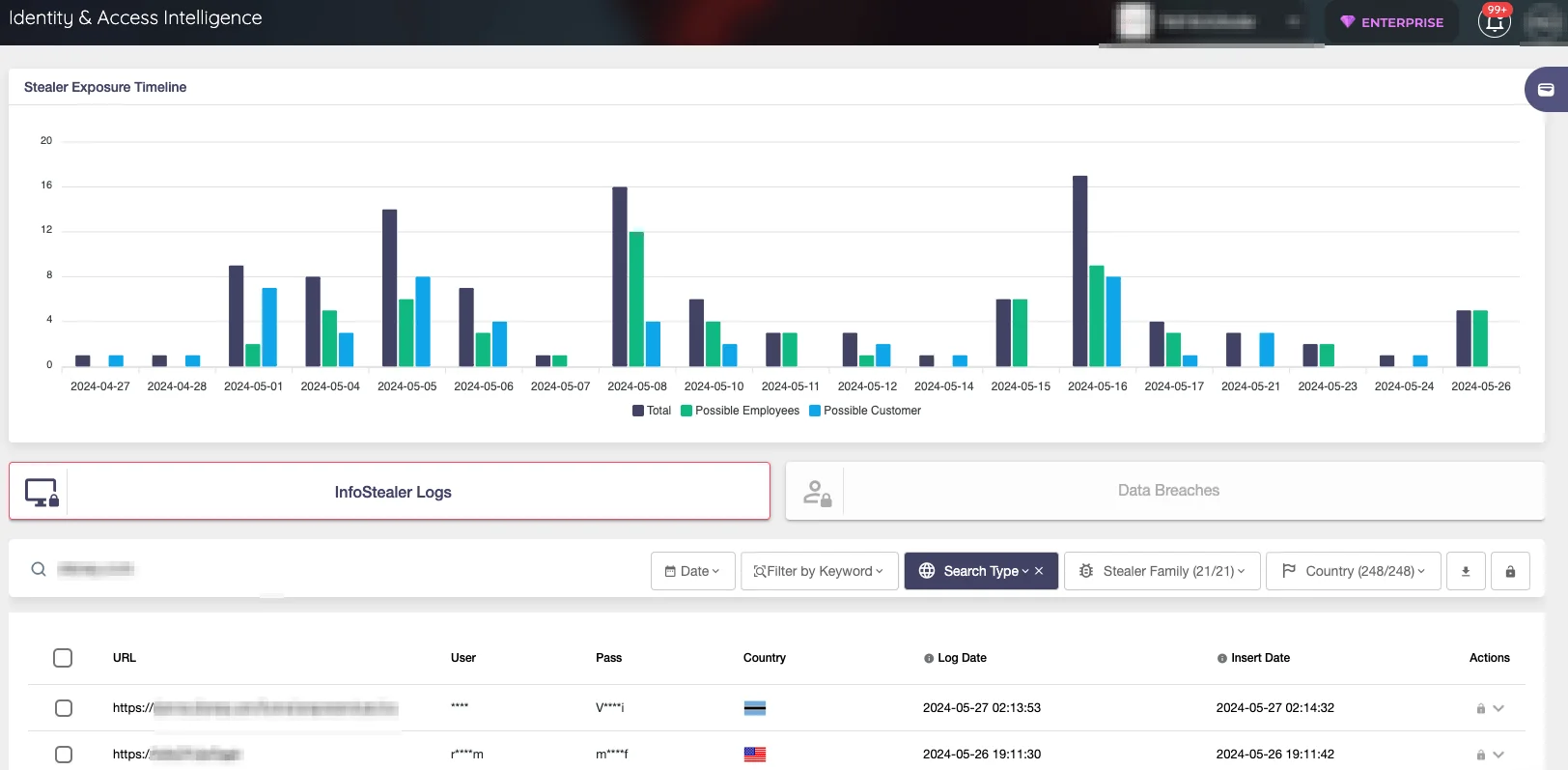
SOCRadar Identity & Access Intelligence Module
Conclusion: Staying Resilient Amid Evolving Threats
As Black Friday continues to draw both eager consumers and relentless cybercriminals, the risks for e-commerce companies become ever more pronounced. The rise of stealer log threats highlights a new level of sophistication in cyberattacks that demands heightened vigilance and proactive measures from all involved. For online retailers, these events are both a significant opportunity and a high-stakes challenge to their cybersecurity resilience.
The dynamic nature of cyber threats requires e-commerce platforms to remain agile and well-prepared. While stealer logs already pose a significant risk, future developments in malware and data-stealing tactics are likely to evolve, becoming even more complicated to detect and counter. The increased reliance on digital wallets, stored credentials, and one-click purchasing further intensifies the need for sophisticated security measures that can quickly adapt to emerging threats.
To stay resilient, e-commerce companies must adopt a proactive security posture that goes beyond basic defenses. This includes investing in Extended Threat Intelligence systems that can identify leaks and signals of potential attacks before they fully materialize. By leveraging real-time data and analytics, companies can detect and respond to suspicious activities more swiftly, minimizing potential damage.
The holiday shopping season will always bring heightened cyber risk, but e-commerce companies can defend against even the most sophisticated attacks with the right strategies. By staying informed, implementing robust defenses, and empowering customers to shop safely, e-commerce platforms can protect their users and continue to thrive despite the evolving landscape of cyber threats.


































