
Hacker Forums Reveal ICAO Leak, SonicWall Vulnerability, and Other New Exploit Sales
Recent findings from SOCRadar’s Dark Web Team spotlight a series of alarming cyber threats surfacing on hacker forums. These include an alleged leak of documents from the International Civil Aviation Organization (ICAO) and the sale of a pre-authentication RCE vulnerability targeting SonicWall SSLVPN devices. Additionally, the team uncovered a new hacking service offering fully undetectable malware setups, an alleged 0-day exploit for Cisco WebUI, and a massive database breach affecting Niva Bupa Insurance, exposing millions of records.
Receive a Free Dark Web Report for Your Organization:
Alleged Documents of International Civil Aviation Organization are Leaked
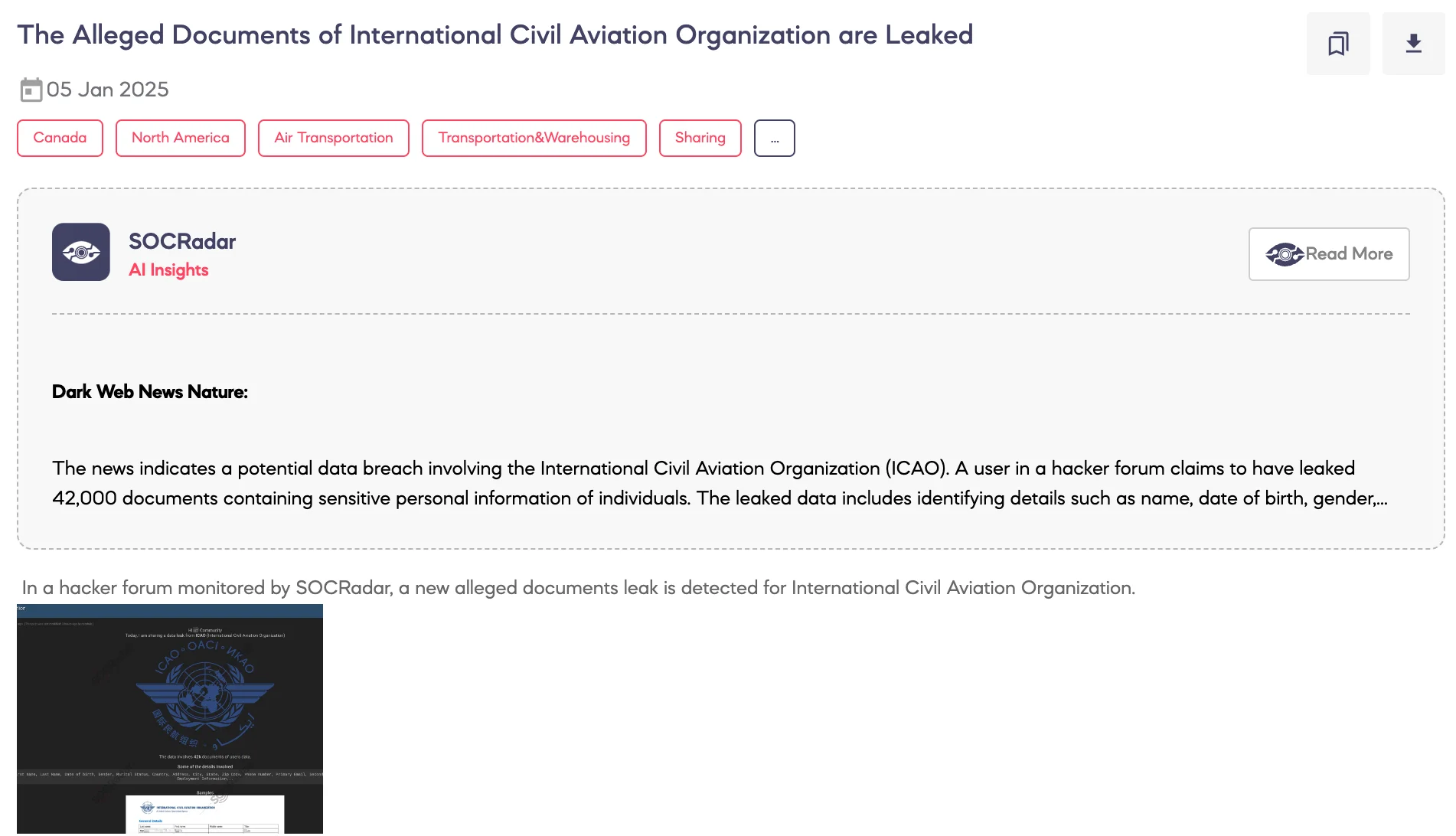
SOCRadar Dark Web Team detected a post on a hacker forum regarding an alleged data leak involving the International Civil Aviation Organization (ICAO).
According to the threat actor, the leaked data consists of 42,000 documents containing user information. The data reportedly includes personal details such as names, dates of birth, gender, marital status, addresses, phone numbers, primary and secondary email addresses, as well as education and employment records. A sample of the leaked documents has allegedly been shared to substantiate the claim.
Alleged RCE Vulnerability of SonicWall is on Sale
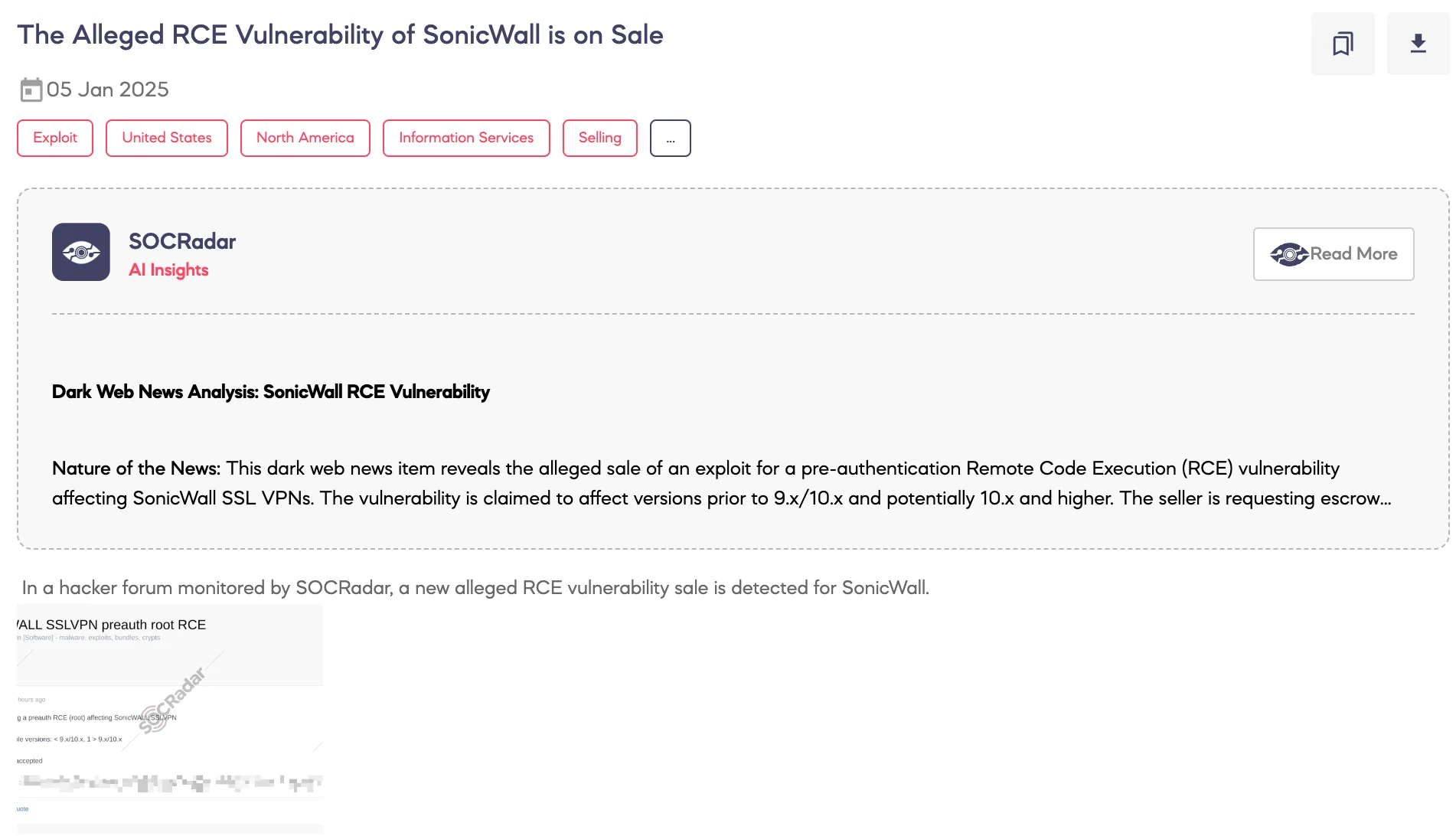
SOCRadar Dark Web Team identified a post on a hacker forum advertising the sale of an alleged Remote Code Execution (RCE) vulnerability impacting SonicWall SSLVPN devices.
According to the post, the vulnerability is pre-authentication, potentially granting root access to affected systems. It is reported to affect specific versions of SonicWall SSLVPN devices, including versions below 9.x/10.x and above 9.x/10.x. The threat actor has indicated acceptance of escrow services for the transaction and provided contact details for further inquiries.
A New Hacking Service is Detected
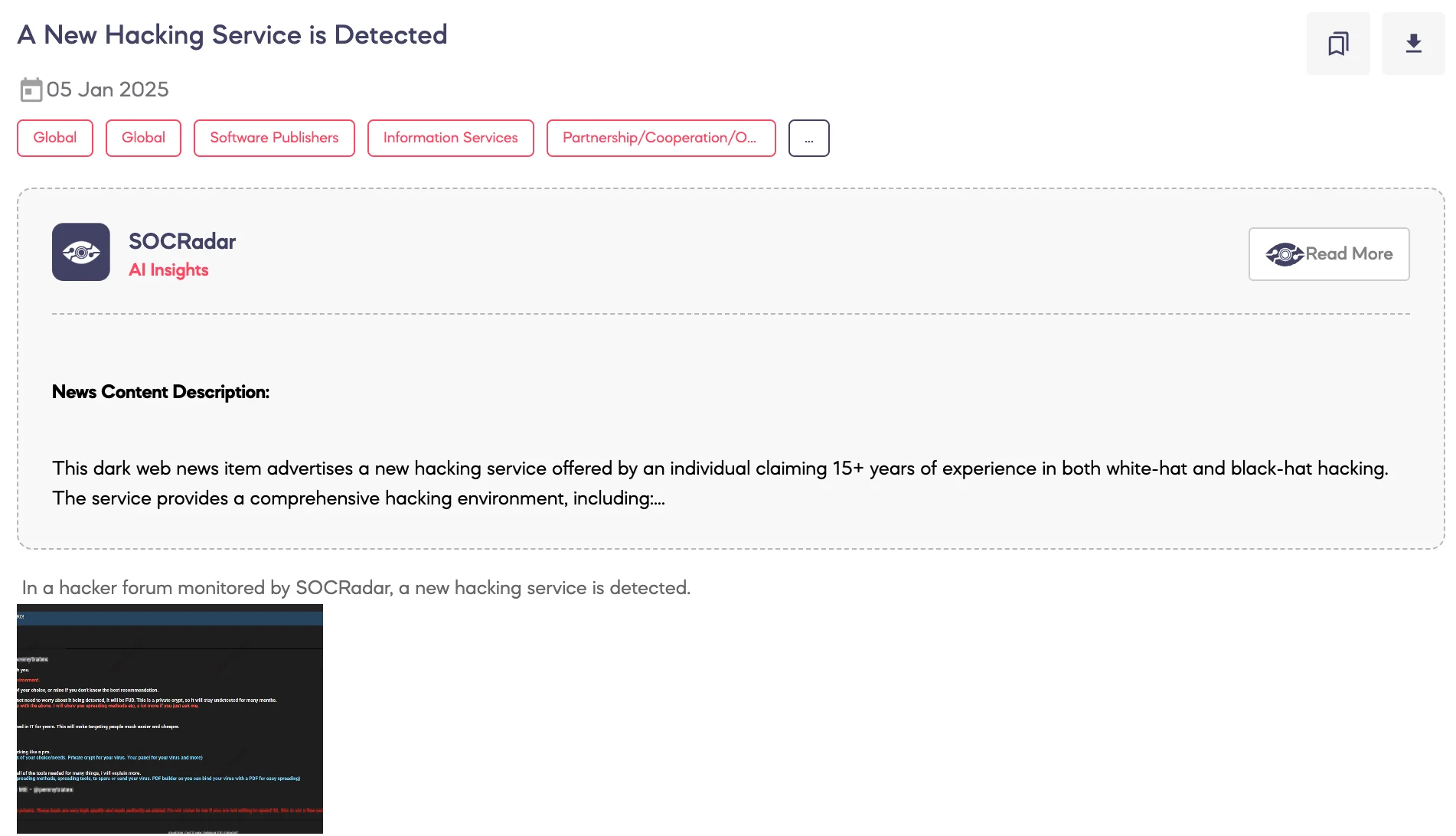
SOCRadar Dark Web Team identified a post on a hacker forum advertising a new hacking service.
The threat actor claims to offer a comprehensive service for setting up hacking environments, including the configuration of keyloggers, Remote Access Tools (RATs), and loaders. Additionally, the actor states that they can crypt malicious software to remain Fully UnDetectable (FUD) for extended periods. The service includes the creation of Remote Desktop Protocol (RDP) setups, spreading methods, and additional customization upon request.
Alleged New 0-Day Exploit for Cisco WebUI is on Sale
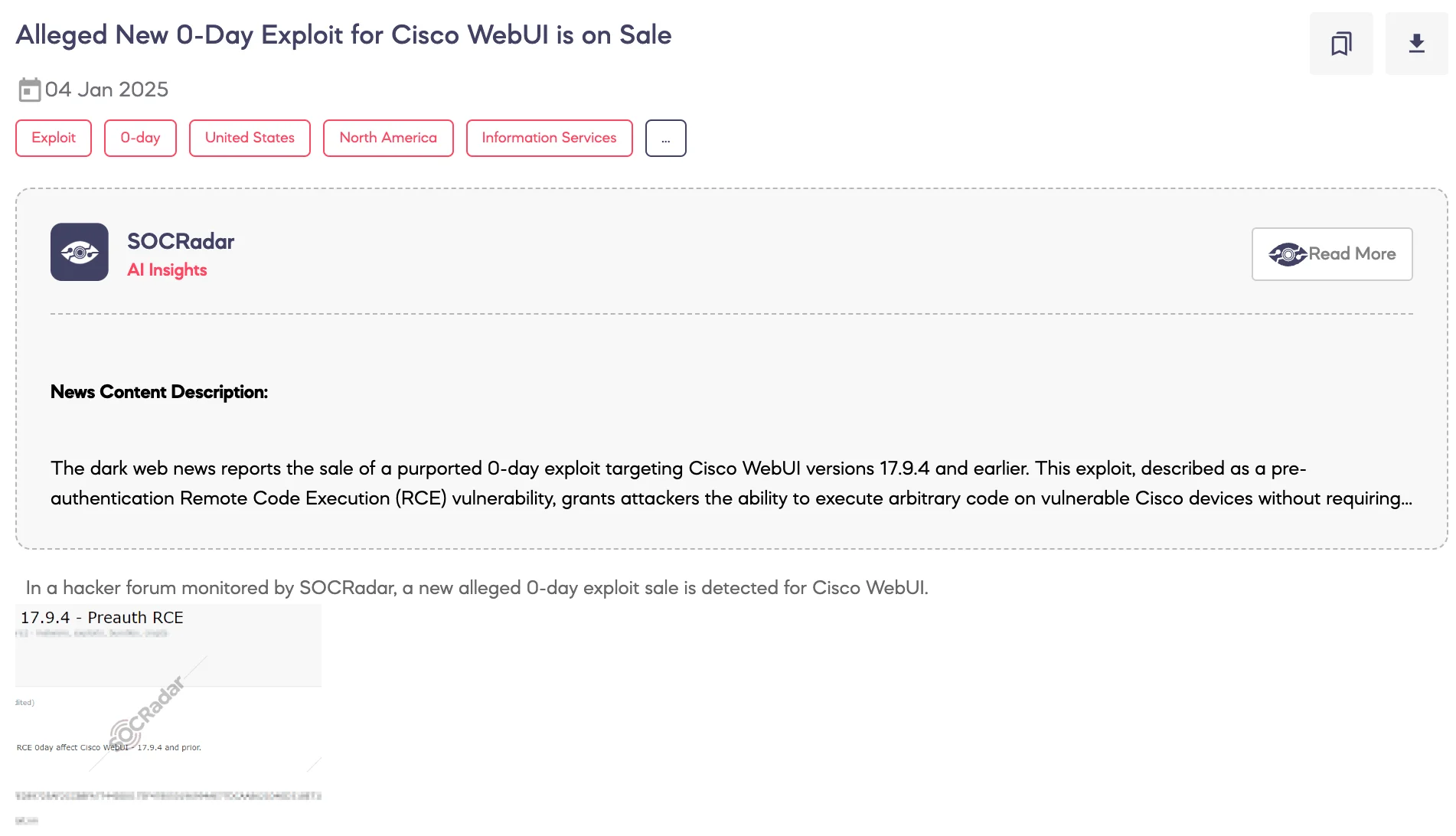
SOCRadar Dark Web Team identified a post on a hacker forum advertising the sale of an alleged 0-day exploit targeting Cisco WebUI.
According to the threat actor, the exploit allows pre-authentication Remote Code Execution (RCE) and impacts Cisco WebUI versions 17.9.4 and earlier. The threat actor is offering the exploit for sale under escrow terms and has provided contact details through TOX, a secure peer-to-peer communication platform often used for anonymous interactions, and Jabber.
Alleged Database of Nivabupa Insurance is on Sale
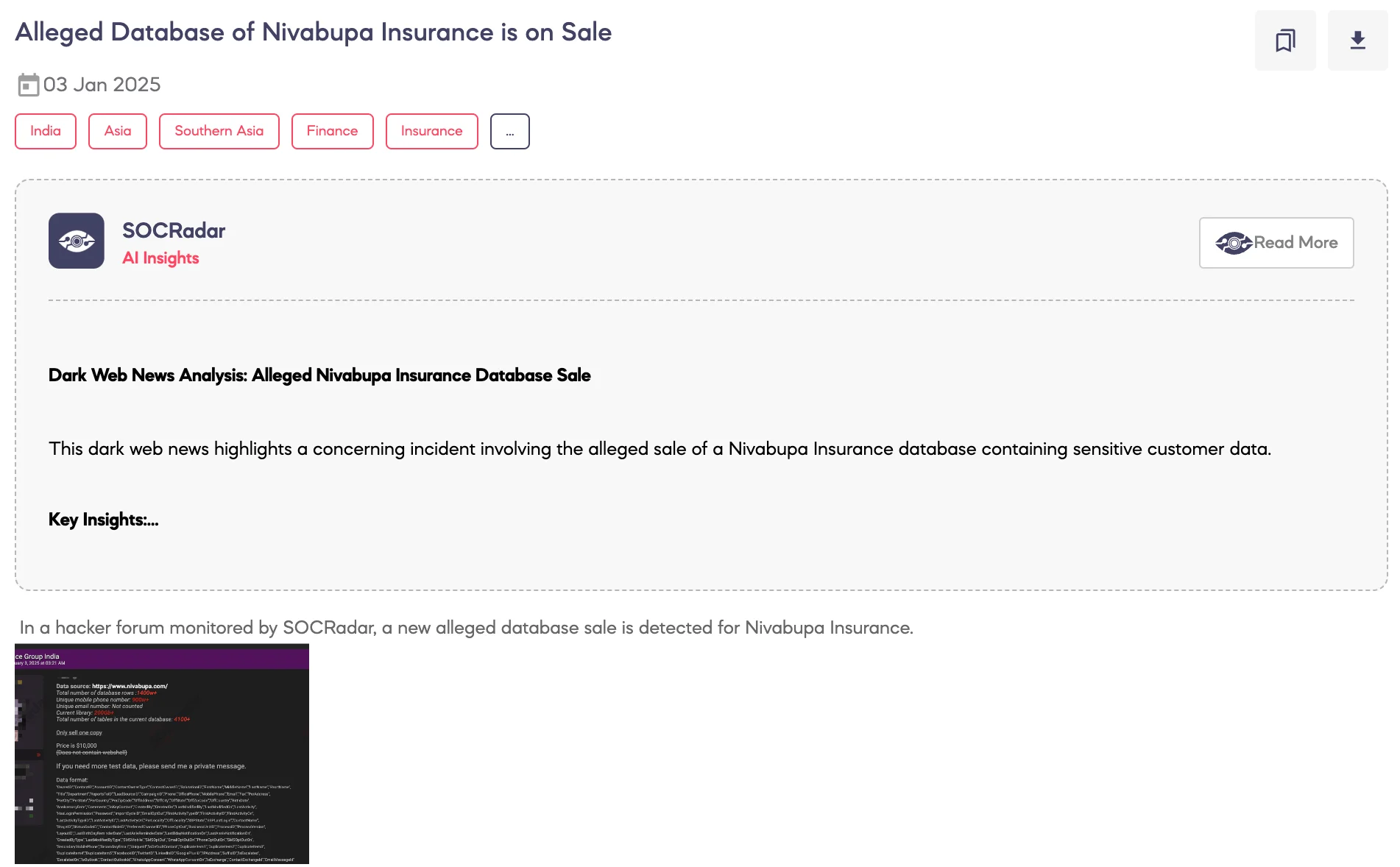
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of an alleged database belonging to Niva Bupa Insurance.
The threat actor claims that the data source is linked to Niva Bupa’s official website and that the database contains over 14 million rows of information, including 9 million unique mobile numbers. The total size of the database is reportedly over 200 GB and includes more than 4,100 tables. The data format allegedly consists of detailed customer and contact information such as names, phone numbers, email addresses, physical addresses, birthdates, business details, and activity logs. The dataset does not include any webshells, according to the actor.
The threat actor states the database is available for purchase for $10,000, with only one copy being sold. A sample of the data is offered upon request. If validated, this alleged leak could expose sensitive personal and operational data, posing risks to the affected individuals and the organization.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































