
IntelBroker Targets HPE, Carrefour France Leak, Nillious Android RAT
SOCRadar’s Dark Web Team has reported significant findings on hacker forums over the past week, including a range of high-profile data breaches and emerging cyber threats.
Notable incidents involve IntelBroker’s claim of breaching Hewlett Packard Enterprise (HPE). Additionally, a database allegedly containing details of millions of Carrefour France customers has surfaced. Other findings highlight the sale of the Nillious Android RAT, designed to target banking apps, and an auctioning of Japanese credit card records.
Receive a Free Dark Web Report for Your Organization:
Alleged Data of Hewlett Packard Enterprise are on Sale
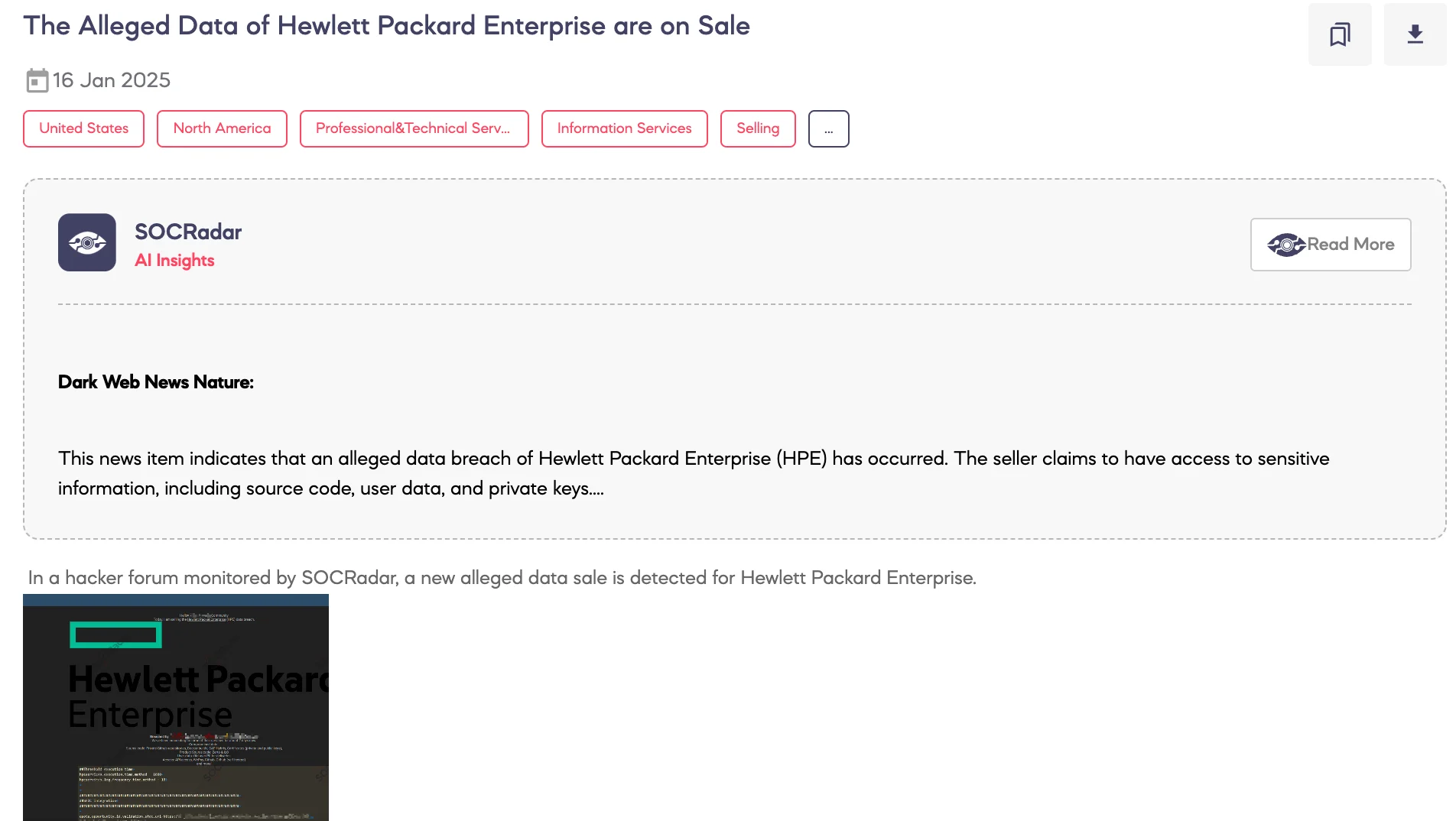
SOCRadar Dark Web Team detected a post on a hacker forum where the IntelBroker threat actor claimed a breach targeting Hewlett Packard Enterprise (HPE). The post detailed access to source code from private GitHub repositories, Docker builds, SAP Hybris, private and public certificates, Zerto and iLO product code, old user PII, and API credentials. IntelBroker, notorious for past breaches involving Europol, Apple, and Cisco, highlighted ongoing access to HPE systems.
Alleged Database of Carrefour France is on Sale
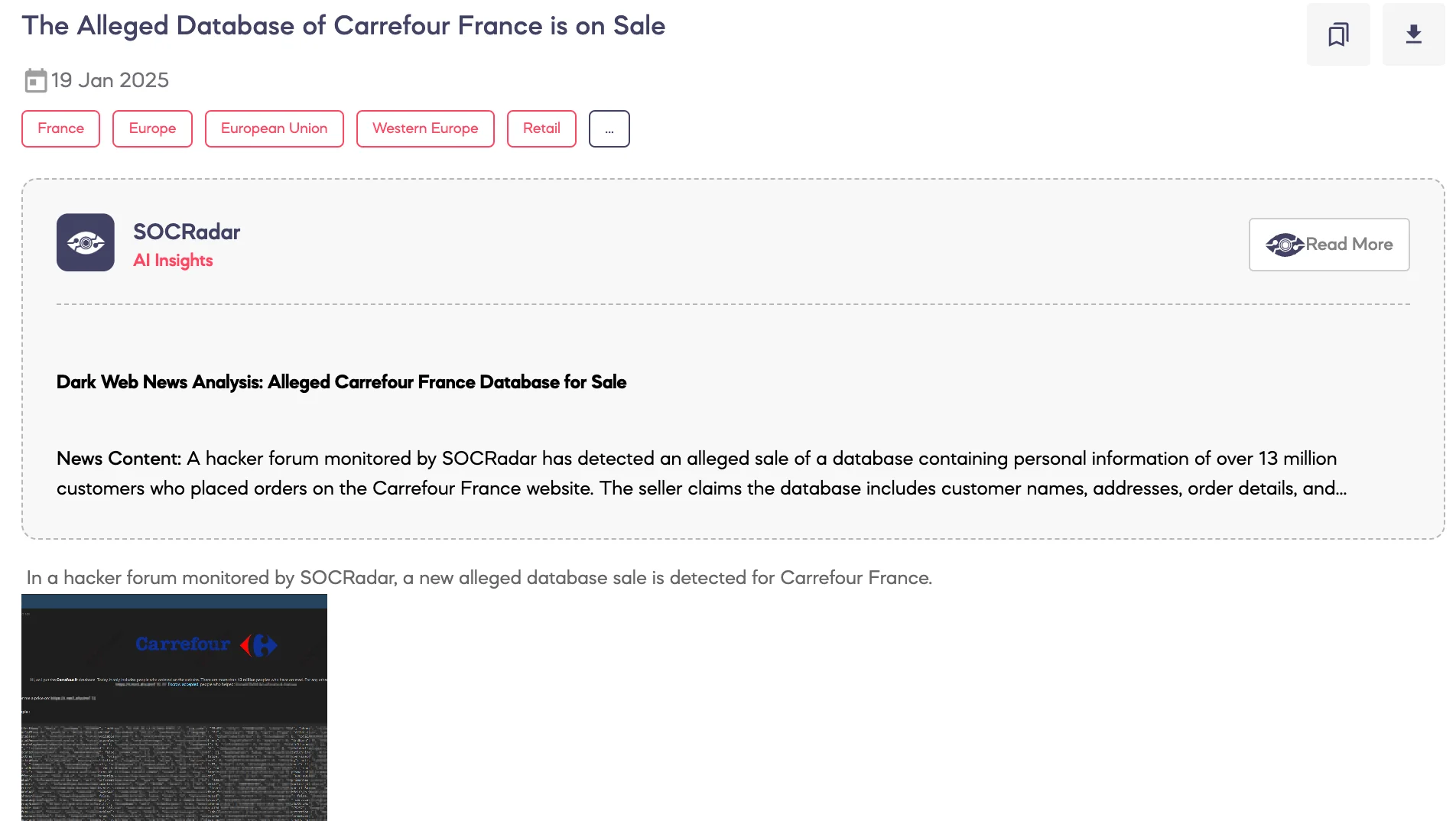
SOCRadar Dark Web Team detected a post on a hacker forum advertising a database allegedly belonging to Carrefour France. The threat actor claims the database contains information on over 13 million customers who placed orders on Carrefour’s website. A sample includes partial details such as names, states, purchase data, product descriptions, and payment details.
Nillious Android RAT Tool Sale is Detected
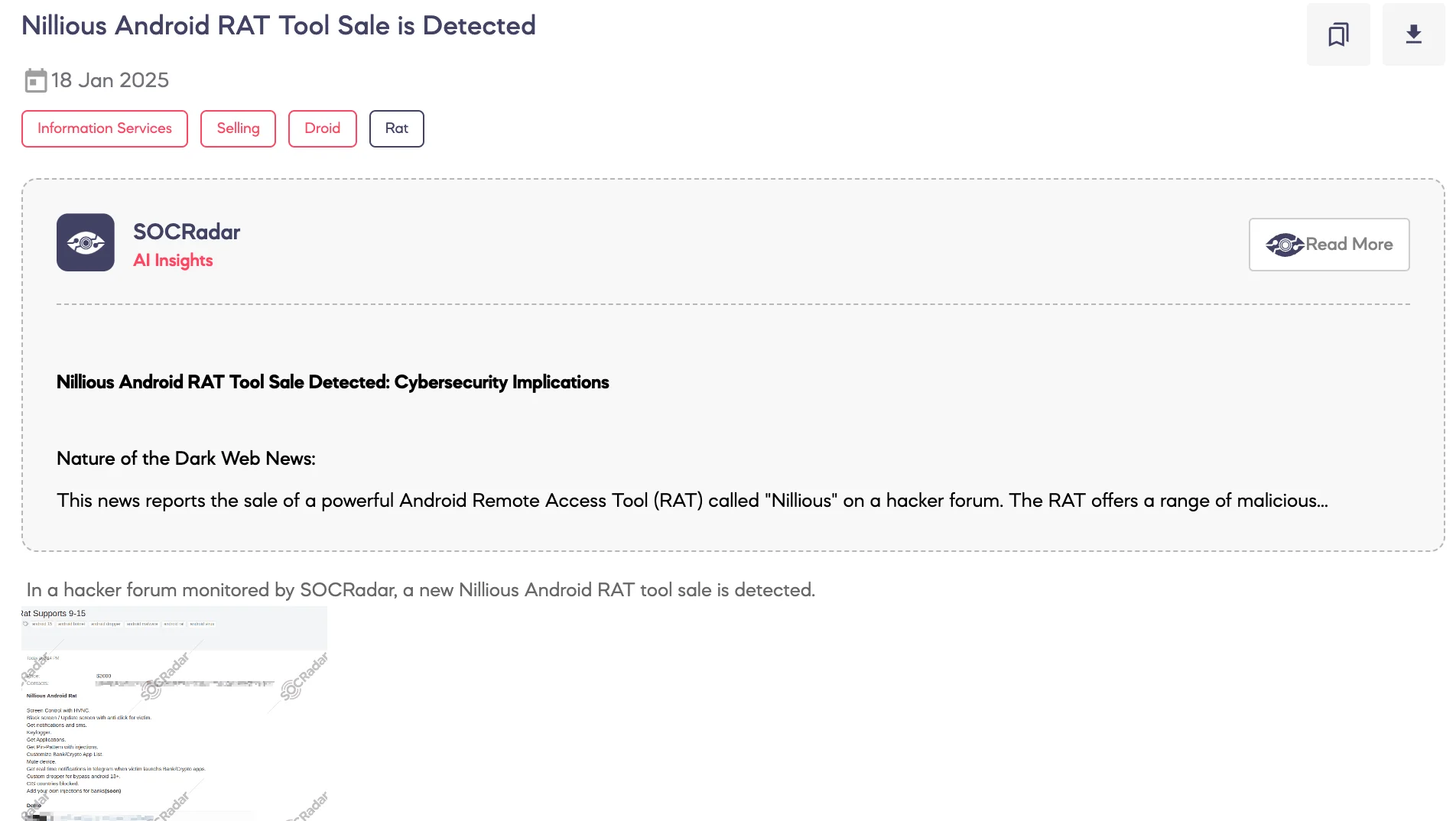
SOCRadar Dark Web Team detected the sale of a new Android Remote Access Tool (RAT) named Nillious on a hacker forum. The tool is being offered for $2,000 and includes features such as HVNC screen control, SMS and notification access, keylogging, custom injection capabilities for banking and cryptocurrency applications, and compatibility with Android 13+.
Additionally, the tool provides real-time notifications via Telegram and allows further customization based on buyer requirements. The seller specifies that the tool is designed to target banking credentials and excludes Commonwealth of Independent States (CIS) countries from its operations.
The exclusion of CIS countries suggests the threat actor might be a Russian-speaking threat actor. This tactic is often used to avoid attracting attention from local law enforcement in their operating region.
Alleged 3,000 Credit Cards Belonging to Japan are on Sale
SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of 3,000 alleged credit card records associated with individuals in Japan. According to the threat actor, the dataset includes complete credit card details, cardholder information, and contact data, with an estimated validity rate of 60%. The auction is set to begin at $5,000, with a blitz (instant purchase) price of $9,000, and will conclude within 24 hours.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































