January 2024 – Microsoft Patch Tuesday & SAP Security Patch Day Highlights
Microsoft has released its January 2024 Patch Tuesday, addressing a total of 48 security vulnerabilities, with two classified as critical in Microsoft advisories. CISA has underscored these updates with an alert, urging users and administrators to thoroughly review Microsoft’s advisories.
The January 2024 Patch Tuesday focuses on various vulnerability types, including:
- 11 Remote Code Execution (RCE) Vulnerabilities
- 11 Information Disclosure Vulnerabilities
- 10 Elevation of Privilege (EoP) Vulnerabilities
- 7 Security Feature Bypass Vulnerabilities
- 6 Denial of Service (DoS) Vulnerabilities
- 3 Spoofing Vulnerabilities
Critical Vulnerabilities Patched in January 2024 Patch Tuesday
Two out of the 48 vulnerabilities have been assigned the maximum severity level of critical in Microsoft advisories, irrespective of their CVSS scores.
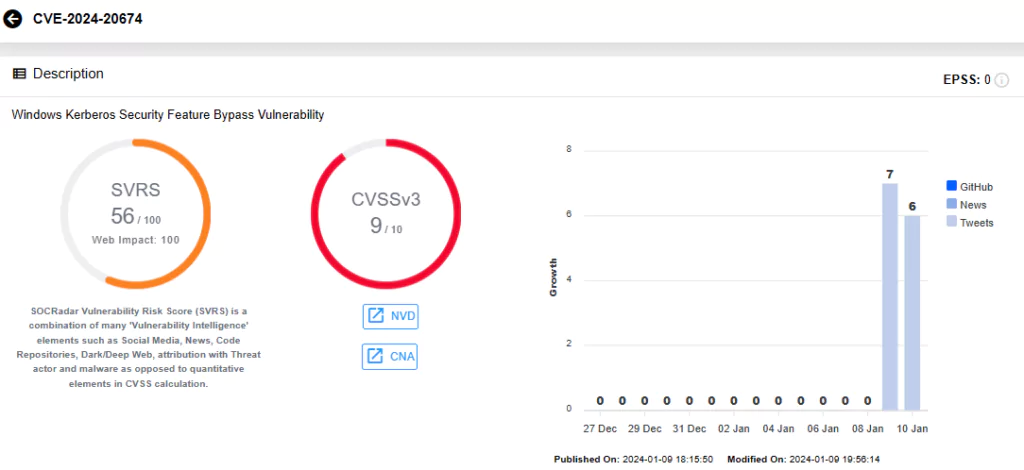
The first critical vulnerability is CVE-2024-20674 (CVSS Score: 9.0), identified as a Security Feature Bypass vulnerability affecting Windows Kerberos. An authenticated attacker could exploit it by initiating a Machine-in-the-Middle (MITM) attack or utilizing other local network spoofing techniques. The attacker then sends a malicious Kerberos message to the victim machine, spoofing itself as the Kerberos authentication server.
Successful exploitation necessitates prior access to the restricted network. Microsoft notes the absence of workaround methods for this vulnerability, yet its exploitation is ‘more likely’; users will have to receive the updates to fix the issue.
There are multiple other vulnerabilities that are likely to be exploited in Microsoft’s January 2024 Patch Tuesday, which also have no workarounds available. They will be detailed in a subsequent section.
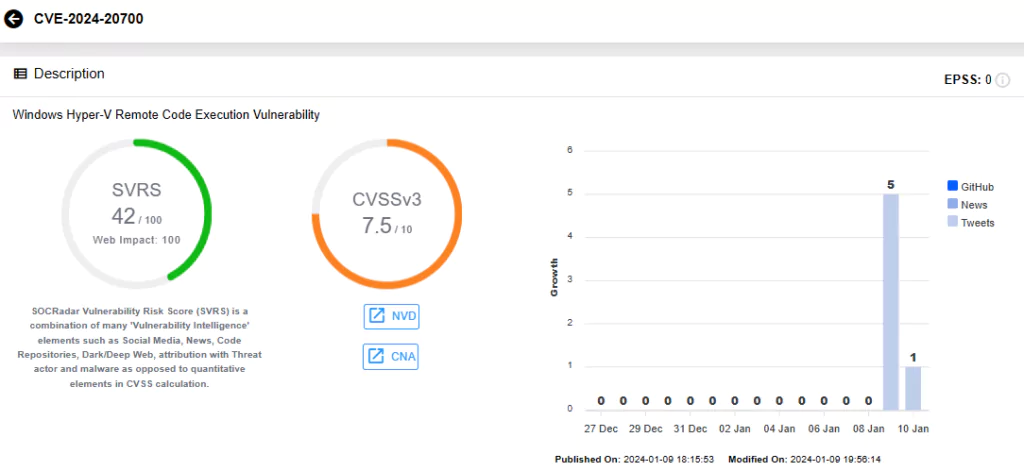
The second critical vulnerability is CVE-2024-20700 (CVSS Score: 7.5), identified as an RCE vulnerability affecting Windows Hyper-V. Exploitation of this vulnerability requires the attacker to win a race condition.
Similar to CVE-2024-20674, gaining access to the restricted network is also a prerequisite for launching an attack. However, in contrast, the exploitation of this vulnerability is deemed ‘less likely’.
Vulnerabilities That Are More Likely to be Exploited
The following high-severity vulnerabilities are more likely to be exploited, and concerningly, there are no workarounds available, emphasizing the importance of promptly applying official patches for remediation.
CVE-2024-21318 (CVSS Score: 8.8) is an RCE vulnerability in Microsoft SharePoint. Due to the vulnerability, an authenticated attacker with Site Owner permission can inject arbitrary code, executing it within the context of SharePoint Server.
CVE-2024-20652 (CVSS Score: 7.5) is a Security Feature Bypass Vulnerability in Windows HTML Platforms. An attacker can bypass the MapURLToZone method due to the vulnerability, requiring the preparation of the target environment for improved exploit reliability.
CVE-2024-21307 (CVSS Score: 7.5) leads to RCE in Remote Desktop Client. However, successful exploitation requires the attacker to win a race condition.
Four privilege escalation vulnerabilities, each with a CVSS score of 7.8, grant an attacker SYSTEM privileges upon successful exploitation. The following are their CVE identifiers and the associated affected Microsoft products:
- CVE-2024-20653 – Microsoft Common Log File System
- CVE-2024-20683 – Win32k
- CVE-2024-20686 – Win32k
- CVE-2024-20698 – Windows Kernel
- CVE-2024-21310 – Windows Cloud Files Mini Filter Driver
It is strongly advised to apply the patches to secure your environment and enhance your overall security posture. For more details on the vulnerabilities addressed in the January 2024 Patch Tuesday update, refer to Microsoft’s Release Note.
SAP January 2024 Security Patch Day Highlights: Critical Vulnerabilities Addressed in BTP
In parallel with the January 2024 Patch Tuesday, SAP has introduced ten new security notes as part of its Security Patch Day. Additionally, the company has updated two previously disclosed security notes.
The January 2024 Security Patch Day from SAP focuses on three critical issues, categorized with a priority rating of ‘Hot News.’
The vulnerabilities listed under the three security notes, under specific conditions, allow escalation of privileges. Upon successful exploitation of any of these vulnerabilities, an unauthenticated attacker can obtain arbitrary permissions within the application.
Here are the details of the affected products and versions associated with the distinct vulnerabilities outlined in the critical security notes:
- Security Note #3412456
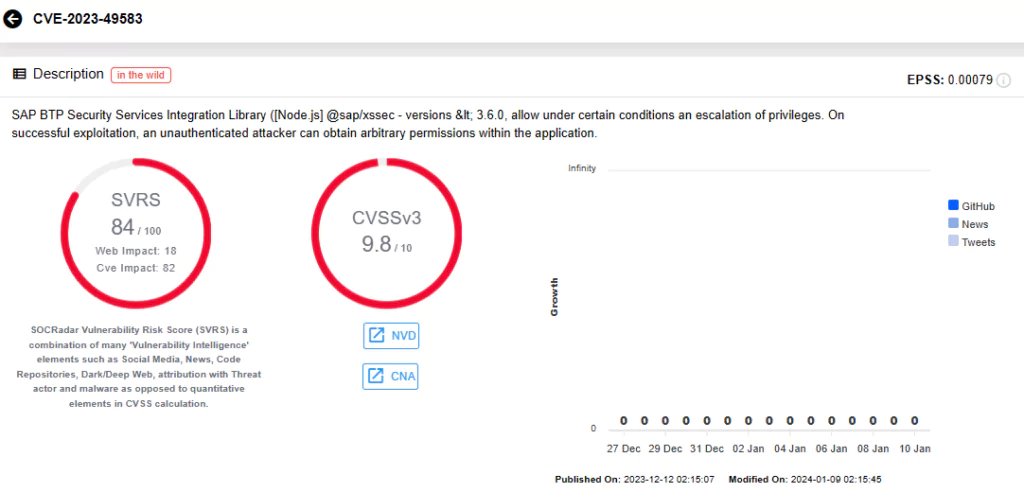
CVE-2023-49583 (CVSS Score: 9.8): SAP BTP Security Services Integration Library ([Node.js] @sap/xssec) – versions < 3.6.0.
- Security Note #3413475
CVE-2023-50422 (CVSS Score: 9.8): SAP BTP Security Services Integration Library ([Java] cloud-security-services-integration-library) – versions below 2.17.0 and versions from 3.0.0 to before 3.3.0.
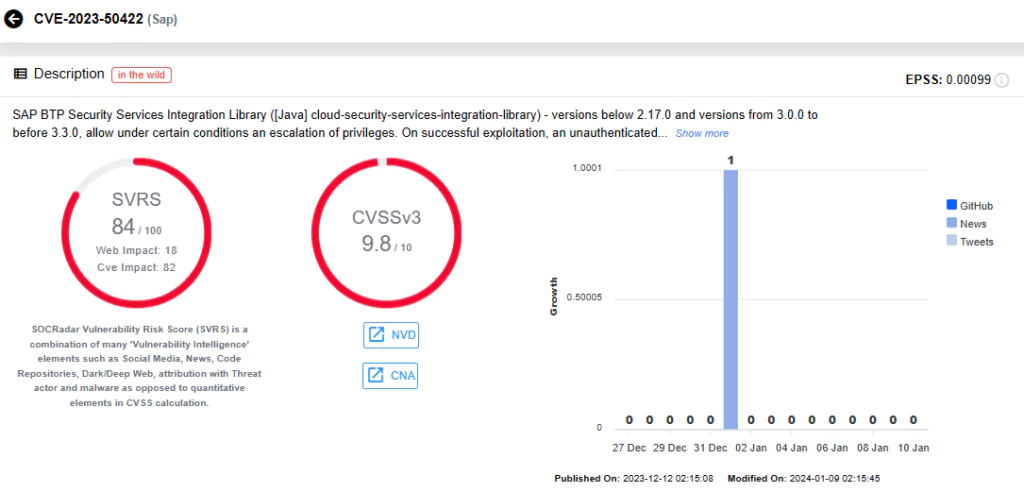
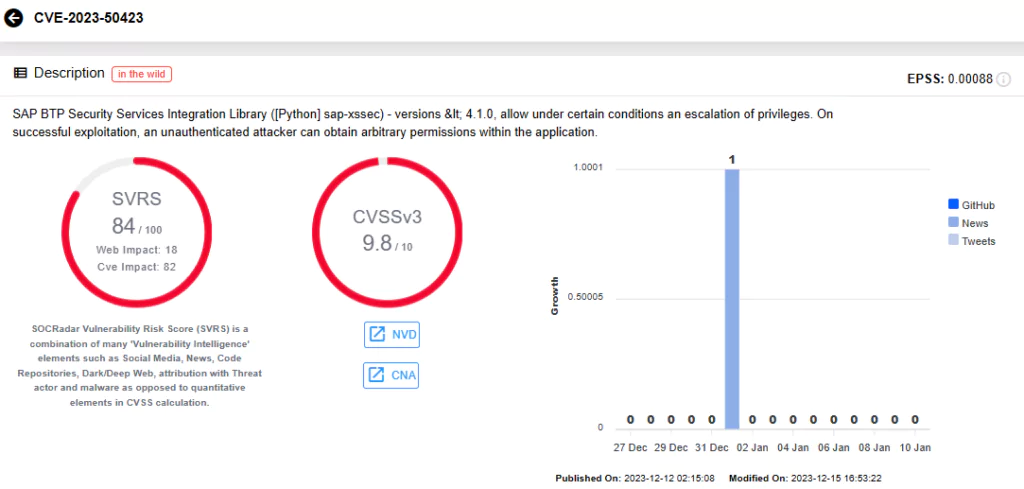
- Security Note #3411067 (Update to a Security Note released on December 2023 Patch Day)
CVE-2023-50423 (CVSS Score: 9.8): SAP BTP Security Services Integration Library ([Python] sap-xssec) – versions < 4.1.0.
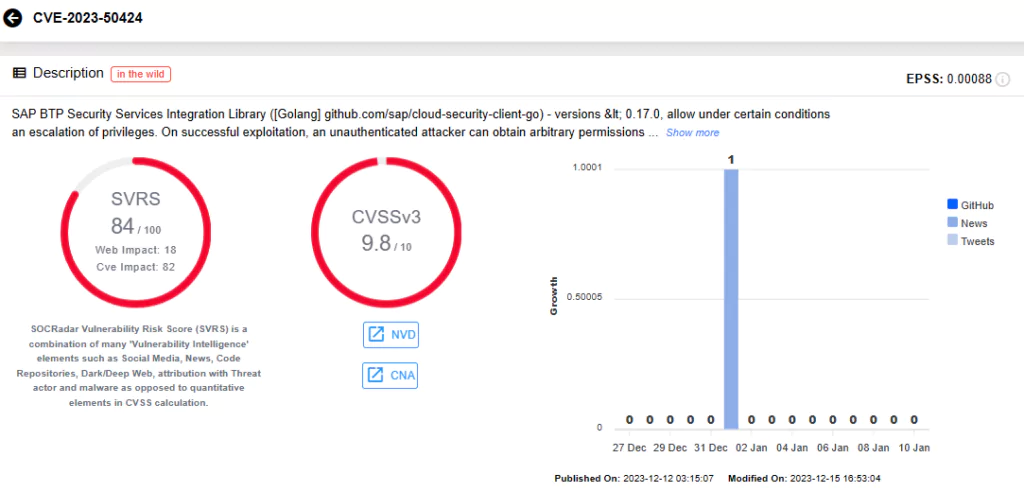
CVE-2023-50424 (CVSS Score: 9.8): SAP BTP Security Services Integration Library ([Golang] github.com/sap/cloud-security-client-go) – versions < 0.17.0.
Find more information and access the advisories through SAP’s January 2024 Patch Day release note.
Strengthen Your Security Defenses with SOCRadar
With SOCRadar XTI, you can enhance your defense mechanisms and proactively counter emerging threats. The platform’s Attack Surface Management module empowers organizations with tools to swiftly identify, assess, and mitigate vulnerabilities, while offering insights into vulnerabilities affecting your assets.
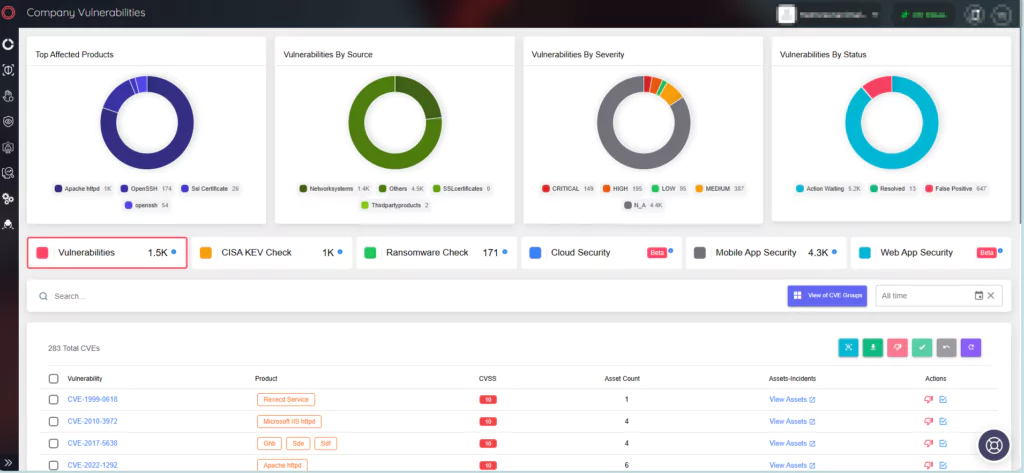
Moreover, the Vulnerability Intelligence feature elevates security measures by consistently monitoring and tracking security vulnerabilities, enabling you to search for their details and monitor associated activities, including hacker trends.