Key to Achieving a Stronger Cybersecurity Posture: Zero Trust Policy
In recent years, we have seen countless high-profile data breaches that have left businesses and individuals vulnerable. To combat these threats, there is one most effective security policy: Zero Trust (ZT). This powerful security concept is gaining traction in the industry as a way to safeguard data and prevent unauthorized access.
In the past, organizations typically relied on perimeter-based security measures such as firewalls, intrusion detection systems, and antivirus software. However, these methods are no longer sufficient in today’s complex and evolving threat landscape, where vulnerabilities can arise from various sources, including emails, attachments, and links. This has led to the adoption of Zero Trust security models, which assume that all internal and external network traffic is potentially malicious.
What Is Zero Trust (ZT)?
Zero Trust is a security architecture that requires all users, whether within or outside the organization’s network, to be verified, approved, and continually checked for security configuration and posture before gaining or maintaining access to applications and data. It uniquely handles contemporary corporate concerns, such as safeguarding remote employees, hybrid cloud systems, and ransomware attacks.
One of the key features of a Zero Trust policy is identity management, which involves verifying the identity and authorization of users and devices before granting them access to resources and continuously monitoring user behavior to detect any suspicious activity, such as attempts to access restricted resources. This approach reduces the impact of a potential security breach by preventing unauthorized access and limiting lateral movement within the network.
What are the Principles of Zero Trust?
The utmost important rule of Zero Trust is: to assume that everything is hostile. It is a significant departure from the network security architecture that has been in use since the 1990s, which is based on a centralized data center and a secure network perimeter. These network designs rely on allowed IP addresses, ports, and protocols to create access restrictions and confirm what is trusted within the network, which frequently includes anyone connecting via remote access VPN.
A Zero Trust approach, in contrast, considers all traffic hostile, even if it is already inside the perimeter. Communication between workloads, for example, is prohibited unless a set of qualities, such as a fingerprint or identity, authenticates them. Identity-based validation standards result in improved security that follows the workload wherever it communicates, whether in the public cloud, a hybrid environment, a container, or an on-premises network architecture.
Zero Trust protects applications and services even when they interact across network contexts, with no architectural or policy changes required. Zero Trust enables secure digital transformation by connecting individuals, devices, and apps across any network using business rules.
Challenges of a Zero Trust Security Model
There are still several places where these fundamentals are too difficult to execute. Common problems include the continued use of obsolete technology, immature business processes, and the deprioritization of security as a critical business function.
Zero Trust often necessitates a mental shift for executives and security experts. Existing, obsolete security architectures pose a risk that leaders must assess. IT and operational technology (OT) experts must determine where they may use current investments to reduce the cost of Zero Trust implementation and where they should prioritize new expenditures.
According to the IBM Cost of a Data Breach Report, implementing a Zero Trust security approach can significantly reduce the cost of a data breach. Organizations that use Zero Trust may save up to $1 million in the event of a breach. The report also found that while 41% of organizations have adopted a Zero Trust security architecture, most organizations (59%) have not yet implemented this approach.
Nonetheless, it is a fact that certain protocols and devices will never achieve Zero Trust, necessitating judgments over whether to replace or preserve them.
In addition, if specific systems cannot completely adopt a Zero Trust strategy, OT experts must determine what mitigating controls are in place and whether alternative security measures can be implemented to decrease their risk.
The transition to “deny by default” or “always verify,” the core assumption of Zero Trust, demands the commitment of teams to both install and maintain over time while ensuring that no section of the business creates “shadow IT” products to circumvent the Zero Trust security architecture.
Why Do Companies Consider a Zero Trust Policy?
Numerous organizations have adopted the zero-trust security architecture design concept for various reasons.
- Protection of client data eliminates the wasted time and irritation caused by the loss of customer data and the expense of losing consumers who have lost faith in the company.
- When a Zero Trust system handles all security functions, redundant firewalls, web gateways, and other virtual and hardware security devices may be removed.
- Reduced need to recruit and train security experts: A centralized zero-trust solution reduces the personnel required to administer, monitor, protect, enhance, and update security policies.
Without Zero Trust architecture, businesses expose themselves needlessly to expensive data breaches. In May 2014, hackers acquired access to the addresses, names, birth dates, and passwords of 145 million eBay members. They just exploited the login credentials of three eBay workers to get access.
Threat actors’ use of information stealer malware and hacked credentials belonging to employees poses a tremendous security risk, which is why everything inside the boundary is also considered hostile in the context of Zero Trust. These types of incidents frequently occur, and through hacker forums and the dark web, the compromised information ends up in the hands of numerous other malicious actors.
If eBay had implemented a zero-trust strategy with at least two layers of authentication, such as 2FA (two-factor authentication) or MFA (multi-factor authentication), the hackers would have needed more than just a login and password to gain access. Requiring a USB device connected to a specific computer could have saved eBay from public distrust.
How to Establish Zero Trust Security?
Establishing a Zero Trust security model does not necessarily require a complete network overhaul or significant investments in new technology. Instead, the framework should complement and reinforce existing security practices and technologies. Many organizations may already have some of the necessary components for a zero-trust architecture in place, which include the following:
- Identity and access administration
- Authorization
- Implementing micro-segmentation to limit activity in case of unauthorized access
- Programmable policy choices
- Ensuring that assets are updated
- Continuous monitoring with documented and evaluated transactions
- Automating repeated tasks that are prone to human errors as feasible
- Ensuring the security of software used for communications within the organization
Additionally, organizations can use behavioral analytics and threat intelligence to enhance their security posture. Threat intelligence allows organizations to gather information about threats, understand threat actor motivations and tactics, and identify patterns and trends.
In addition to all the above, organizations need to determine the number of assets in their network. By knowing the number of assets, organizations can effectively take action to secure them.
SOCRadar allows you to keep track of your assets and continuously monitor them and take quick and easy actions via alarms.
The Zero Trust approach has gained significant momentum across the global cyber industry, and the European Union has started prioritizing its adoption. The EU has recognized Zero Trust architecture’s regulatory benefits and embraced this security approach to combat the increasing threat landscape. The US government, led by President Biden, has made implementing a Zero Trust policy mandatory. However, organizations in the private sector may find it challenging to adopt a Zero Trust policy immediately.
It is worth noting that the principles of Zero Trust are already being implemented in various organizations of all sizes. The basic tenets of Zero Trust rely on utilizing current security measures and organizational and process controls.
Federal agencies, such as the US Department of Defense, Homeland Security, and the Intelligence Community, already implement Zero Trust as a cultural pillar of their security paradigm.
Implement Zero Trust with SOCRadar
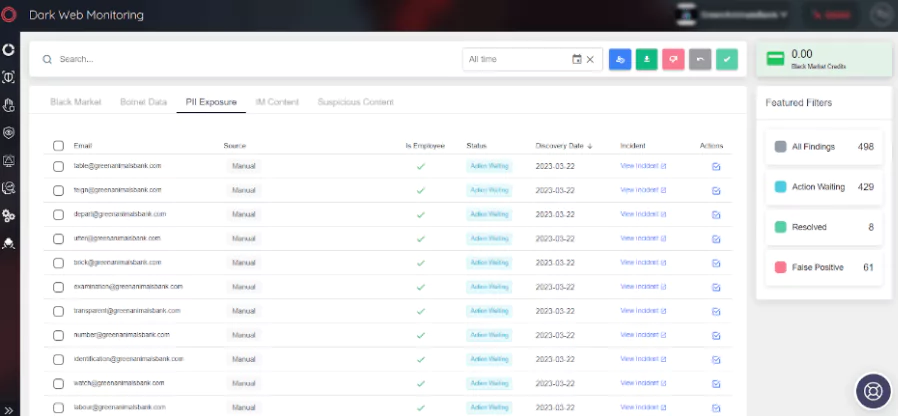
Dark web monitoring for PII can enforce the Zero Trust policy by detecting compromised employee information and taking necessary action to prevent unauthorized access, reducing the risk of data breaches and cyber-attacks.
SOCRadar’s platform uses advanced technology and intelligence to scan the dark web for compromised PII. It provides customizable alerts, reporting, and seamless integration with security tools to help organizations maintain a strong security posture and avoid emerging threats.