
Laravel Framework Affected by a New Critical Vulnerability (CVE-2024-40075): Patch Now
A very critical vulnerability, designated as CVE-2024-40075, has emerged in the Laravel PHP framework. This flaw could allow attackers to execute arbitrary commands, read sensitive data, and perform further malicious actions.
Laravel is an open-source PHP framework, widely used for building web applications and APIs. Known for its robust security features, scalability, and ease of use, Laravel is a preferred choice among developers worldwide.
What Is CVE-2024-40075?
CVE-2024-40075 (CVSS: 9.8) is an XML External Entity (XXE) vulnerability affecting the popular PHP framework Laravel.
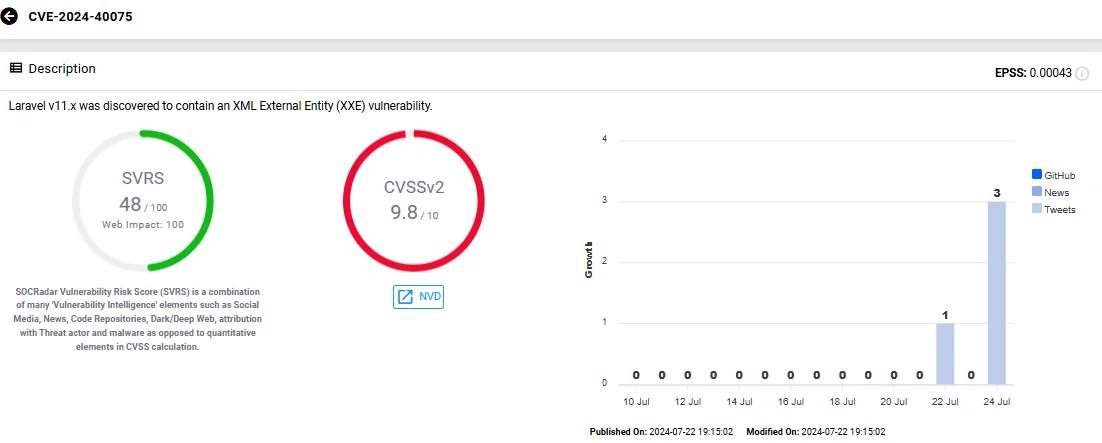
Vulnerability card of CVE-2024-40075 (SOCRadar Vulnerability Intelligence)
Attackers can exploit this vulnerability by manipulating XML input, potentially allowing them to read sensitive files on the application server, perform Server-Side Request Forgery (SSRF), cause Denial-of-Service, or execute arbitrary code.
Due to Laravel’s widespread use in web development, this vulnerability could have extensive impacts, resulting in data exposure, system compromise, and service disruptions on web applications.
Analysis of the CVE-2024-40075 Vulnerability
A detailed technical analysis of CVE-2024-40075 is already available, by Q16G on Gitee.
The vulnerability originates in the ‘__destruct’ function of an abstract class, which calls the ‘close’ method if not overridden. An attacker can exploit this by finding a subclass that overrides close but not __destruct, such as ‘GroupHandler’.
In this subclass, the close method iterates through handlers and calls their close methods. One handler calls ‘getStreamName’, which invokes md5. This chain requires a __toString method in an implementation class. The __toString function calls toString, which then calls $this->stypes->format, ultimately leading to command execution.
For a comprehensive understanding, see the full analysis here; it includes a POP chain, which is also detailed at the end of this blog post.
Which Laravel Versions Are Affected by CVE-2024-40075?
The vulnerability impacts Laravel v11.x.
Has the Vulnerability Been Exploited?
There is no evidence of exploitation regarding CVE-2024-40075 at the time.
However, a search on ZoomEye shows over 786,000 results, indicating the instances that are using the Laravel framework. These instances are mainly distributed in the United States, followed by Indonesia and other countries.
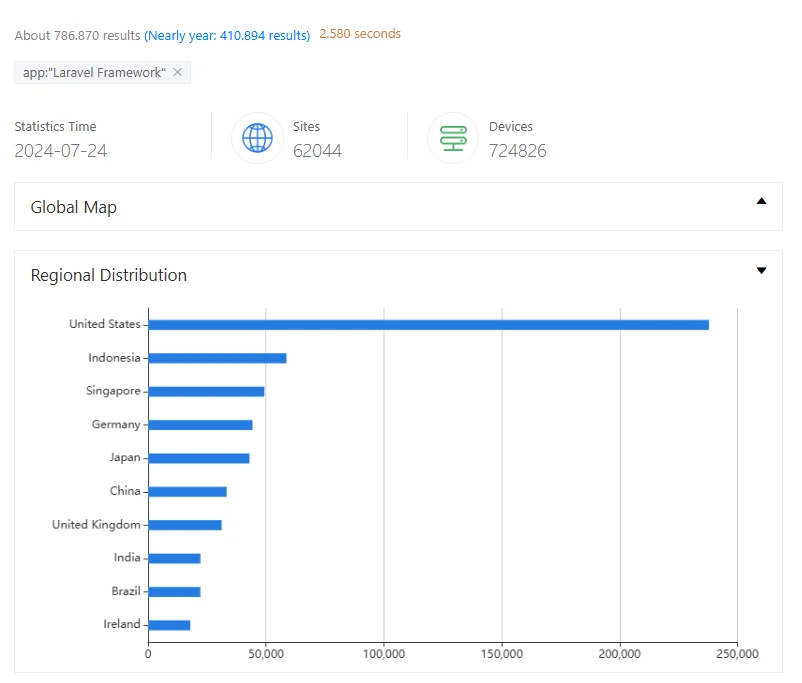
ZoomEye search results for the Laravel Framework
Improve your cybersecurity posture with SOCRadar’s Vulnerability Intelligence module. Access comprehensive insights and updates on vulnerabilities, as well as information on available exploits.
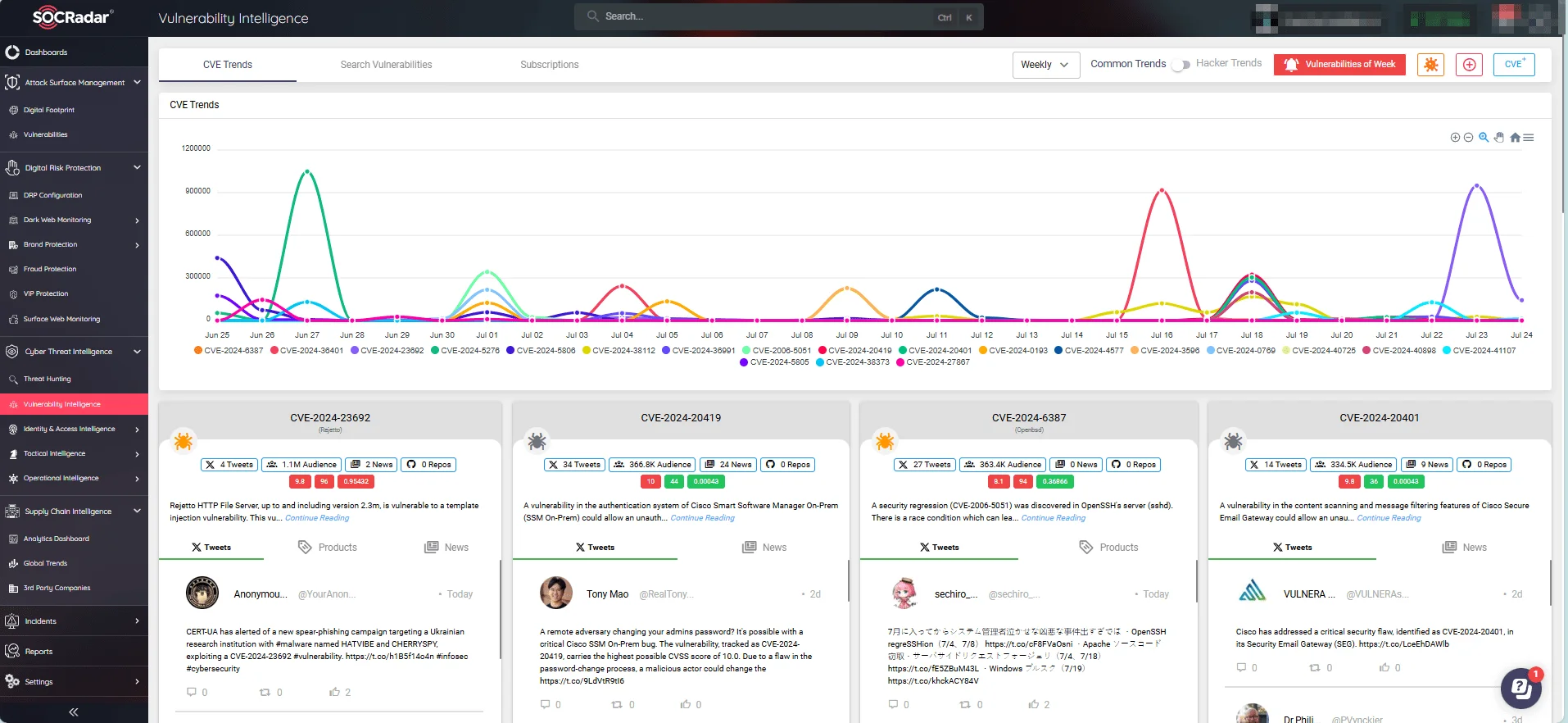
SOCRadar’s Vulnerability Management
Patch the CVE-2024-40075 Vulnerability in Laravel
To safeguard against CVE-2024-40075, ensure that Laravel and all dependencies are updated with the latest security patches. Applying the latest updates will address the vulnerability. You can find all Laravel releases here.
Security Recommendations Against XML Vulnerabilities
If updating is not immediately possible, consider these steps to mitigate such XXE vulnerabilities:
- Disable XML external entity processing in your XML parsers if possible.
- Use alternative data formats like JSON instead of XML when feasible.
- Implement input validation and sanitization for XML data.
- Apply the principle of least privilege on your Laravel application and its underlying systems.
- Monitor your systems for unusual activity.
SOCRadar’s Attack Surface Management (ASM) module continuously monitors your digital assets, enabling you to quickly detect and respond to security issues and emerging vulnerabilities.
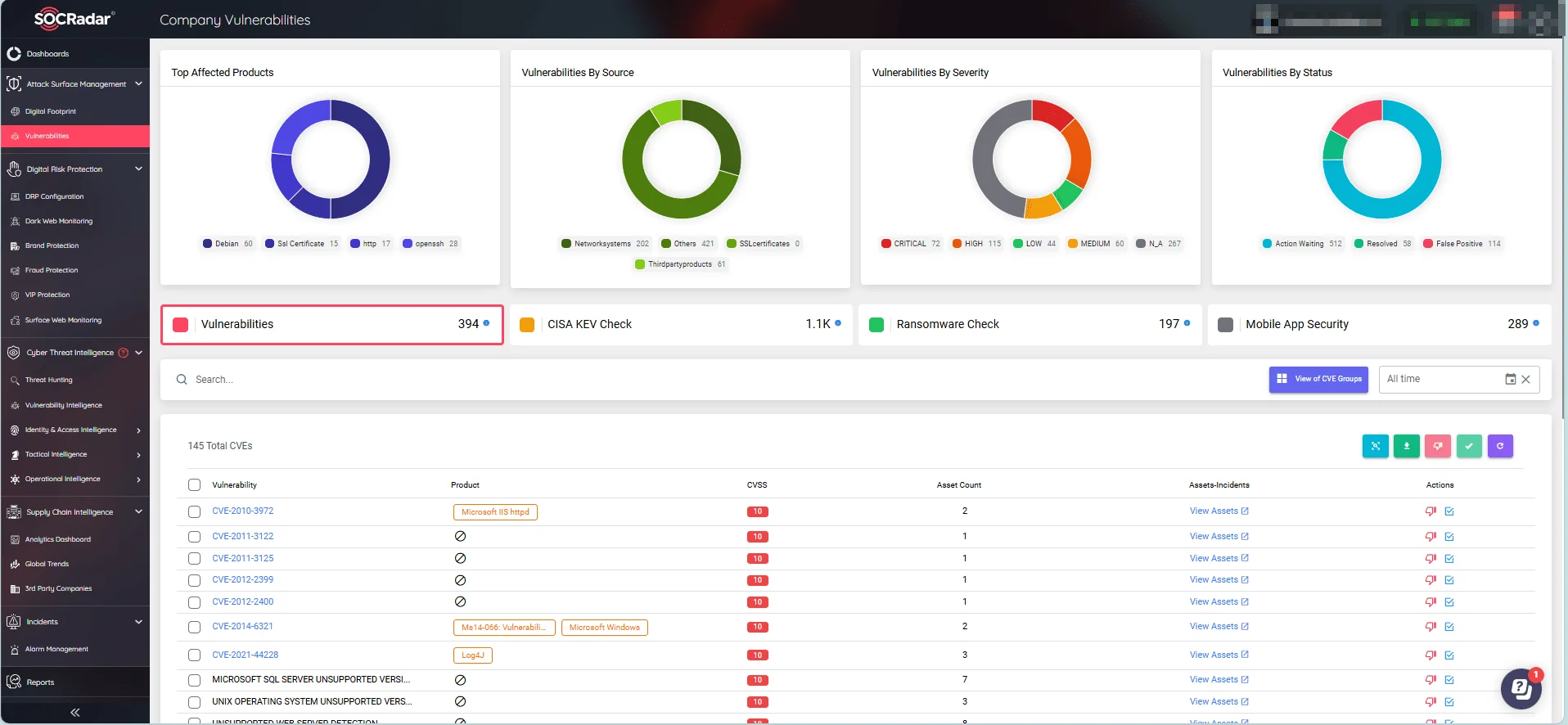
SOCRadar’s Attack Surface Management
The ASM module provides prompt threat alerts with actionable insights, allowing you to take proactive actions to improve your cybersecurity strategy.




































