Latest Alerts for WordPress: POP Chain Leading to Site Takeover, Backdoor-Distributing Phishing Campaign
On December 6, 2023, WordPress rolled out version 6.4.2, addressing a vulnerability introduced in version 6.4 – specifically, a POP chain issue within the core. This vulnerability depended on the existence of an additional PHP Object Injection vulnerability. Simply put, coupled with any other Object Injection vulnerability that may exist in a plugin, it presented a critical threat, potentially enabling arbitrary PHP code execution on websites. Wordfence emphasizes this risk, underscoring the potential for a complete site takeover.
Simultaneously, a new danger emerges as malicious actors exploit a fabricated WordPress vulnerability patch to distribute backdoor malware. Unsuspecting users may unwittingly install the very threat they aim to guard against, assuming it is a legitimate security fix.
This article outlines these latest challenges in WordPress security and the tactics deployed by threat actors.
Vulnerability Details
At the root of the vulnerability lies the WP_HTML_Token class, introduced with WordPress 6.4 to enhance HTML parsing in the block editor. The issue stems from its __destruct method, triggered automatically after PHP processes a request.
The method utilizes call_user_func, executing a function provided through the on_destroy property, with the bookmark_name property as an argument.
Exploiting an existing Object Injection vulnerability provides attackers with control over both the function and argument, allowing arbitrary code execution on the compromised WordPress site. The repercussions encompass unauthorized access, leading to data theft, site defacement, and potential malware distribution to users – essentially resulting in a full site takeover.
Recognizing the severity, WordPress labels this a “Remote Code Execution vulnerability” in its security release note, and states that while this vulnerability is not directly exploitable in the core, its severity significantly escalates when combined with specific plugins, particularly in multisite installations.
Object Injection vulnerabilities, often challenging due to the absence of effective POP chains, escalate in risk when an easy-to-exploit POP chain emerges, according to Wordfence. Although WordPress Core lacks known object injection vulnerabilities, they are pervasive in plugins and themes, amplifying associated risks.
How Did WordPress Patch the Vulnerability?
WordPress 6.4.2 incorporates a new method, __wakeup, which patches the vulnerability. This method guarantees that any serialized object with the WP_HTML_Token class throws an error upon unserialization, thwarting the execution of the __destruct function.
While most sites automatically update to WordPress 6.4.2, Wordfence advises to manually verify the update.
WordPress Update and Additional Recommendations
In response to this recent vulnerability, prioritize the following actions to safeguard your website:
- Update to Version 6.4.2: Regardless of your current version (6.4 or 6.4.1), update promptly to benefit from the patch addressing the identified vulnerability.
- Keep Plugins and Themes Updated: Regularly update all plugins and themes to their latest versions to fortify against all potential vulnerabilities, including object injection vulnerabilities.
- Regular Vulnerability Scans: Conduct routine scans to promptly detect and address any vulnerabilities on your website.
Phishing Alert: Security Patch for Non-Existent WordPress Vulnerability (CVE-2023-45124)
A deceptive security alert has surfaced, falsely addressing a non-existent Remote Code Execution (RCE) vulnerability within WordPress. Rather than offering an actual fix, the scheme creates an admin user and introduces a backdoor into compromised sites.
In the campaign, the attackers send a phishing e-mail, posing as the WordPress team. The e-mail alleges an update for an RCE vulnerability, tracked as CVE-2023-45124 – which is not a valid CVE. The recipients are urged to download a supposed patch plugin, which, upon installation, adds a malicious administrator user (wpsecuritypatch) and transmits site credentials to wpgate[.]zip.
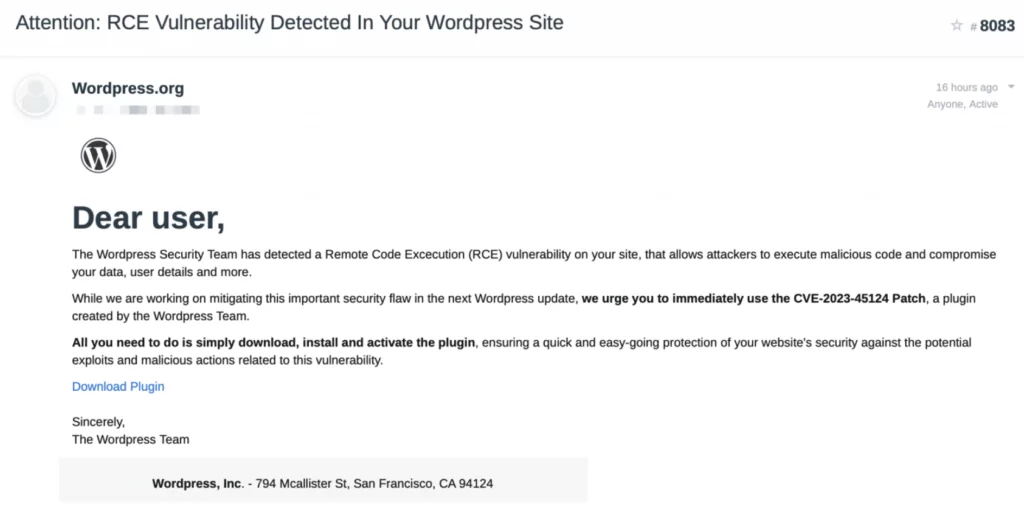
This malicious plugin also downloads a separate backdoor (wp-autoload.php) from wpgate[.]zip, providing attackers persistence and full control over the site and server account. Researchers warn that the backdoor can enable future malicious activities. Attackers can utilize it to inject ads, redirect users to harmful sites, employ it for DDoS attacks, or pilfer billing information.
Users who install and activate the plugin receive a notification that the CVE-2023-45124 has been successfully patched. They are then encouraged to propagate the fake patch to other potentially vulnerable users, possibly initiating a malicious cycle.
This scheme emphasizes the need for vigilance against unexpected security alerts, urging users to verify communications to safeguard their WordPress installations.
Detailed analysis of the campaign is available on Patchstack.
Indicators of Compromise (IOCs) related to the campaign are listed below:
File in Webroot:
- wp-autoload.php
(SHA-256 Hash: ffd5b0344123a984d27c4aa624215fa6452c3849522803b2bc3a6ee0bcb23809)
Malicious Domains:
- en-gb-wordpress[.]org
- wpgate[.]zip
Plugin:
- wpress-security-wordpress
Hidden Administrative User:
- wpsecuritypatch
How Can SOCRadar Help?
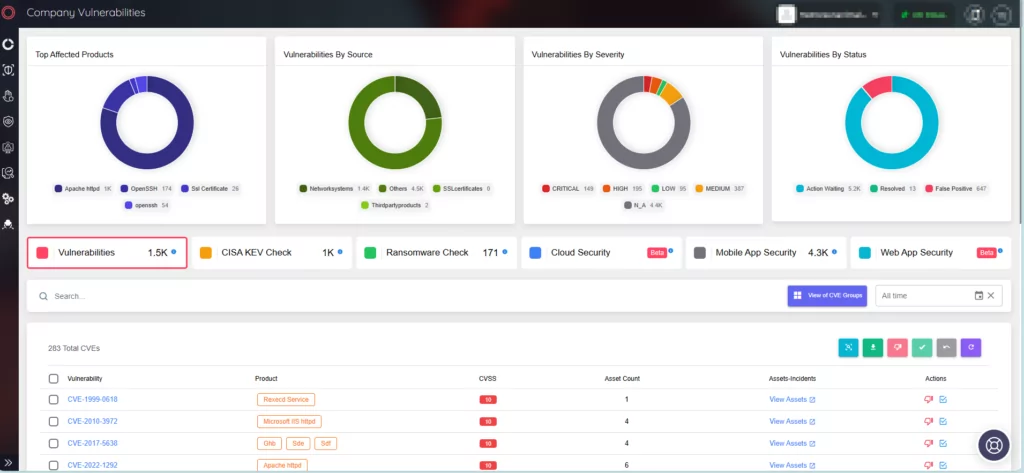
With SOCRadar’s Attack Surface Management, you can ensure continuous monitoring of your digital assets and receive timely alerts for emerging vulnerabilities or security threats.
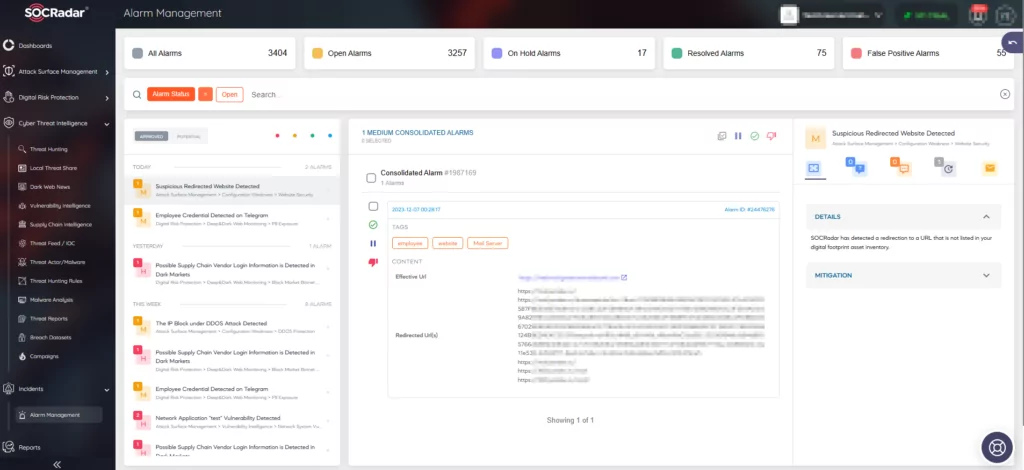
Alarms can be easily managed through the platform, providing quick insights into threats affecting your organization and improving the response process.
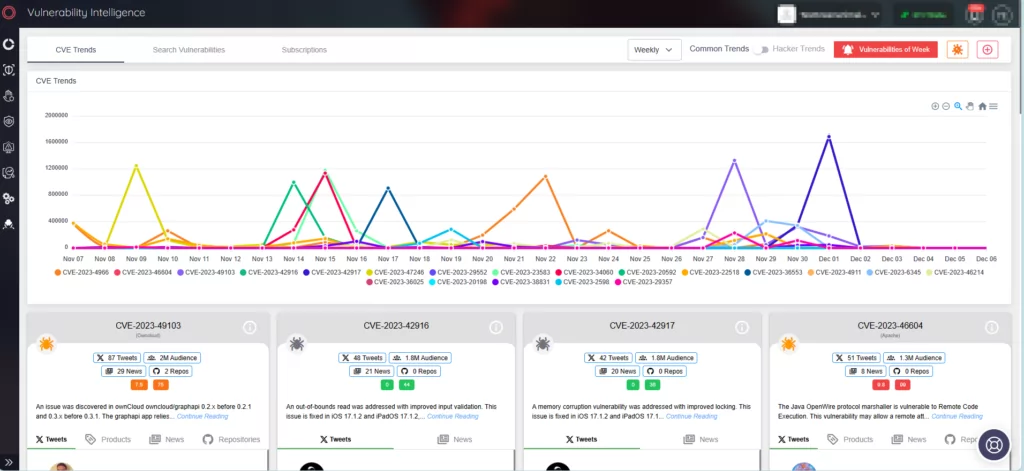
In addition, the Vulnerability Intelligence dashboard provides a comprehensive view of global vulnerability trends, enabling informed CVE patching prioritization.