
MailChimp Breached Shortly After Twilio Incident
DigitalOcean became aware of a breach after MailChimp suddenly suspended its account on August 8. A recent security breach at MailChimp allowed users’ email addresses to be accessed, and some affected customers even had an unauthorized password reset.
The company’s customer alerts email account was compromised as part of the security incident within MailChimp, which meant for DigitalOcean and their clients that confirmations, password reset, notifications, and other transactional emails were not getting through to their intended recipients.
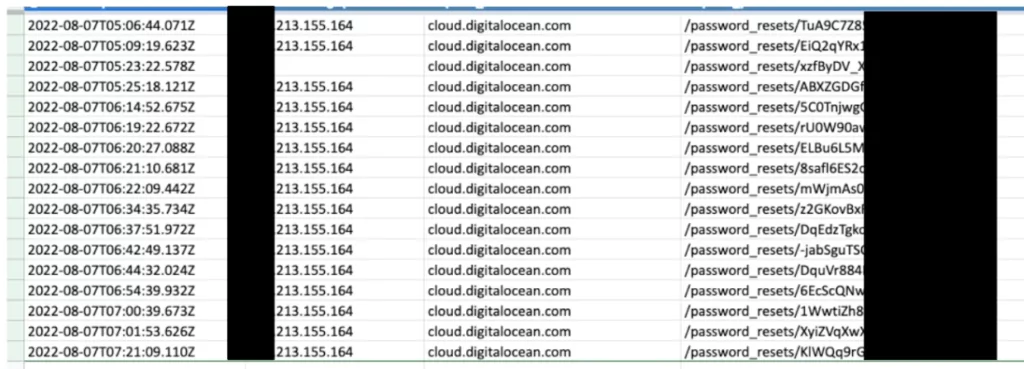
On the same day, a customer reported DigitalOcean that they had an unauthorized password reset as well. Following an investigation, they discovered that on August 7, an unauthorized email address with the @arxxwalls[.]com domain –a domain abused in phishing campaigns – had been added to their MailChimp account.
Extra Authentication is the Key Factor
According to MailChimp’s statement, the incident is crypto-related. The attacker had compromised MailChimp’s internal tooling to reset passwords but failed to reset accounts that enabled 2FA.
The company has migrated its email services from MailChimp and said they informed customers and secured the affected accounts after the incident.
Twilio Was Targeted in a Recent Phishing Attack
Another data breach was experienced by Twilio, a cloud communications firm, at the beginning of the month. As a result of an SMS phishing attack targeted at Twilio employees, threat actors could gain unauthorized access to 125 instances of customer data.
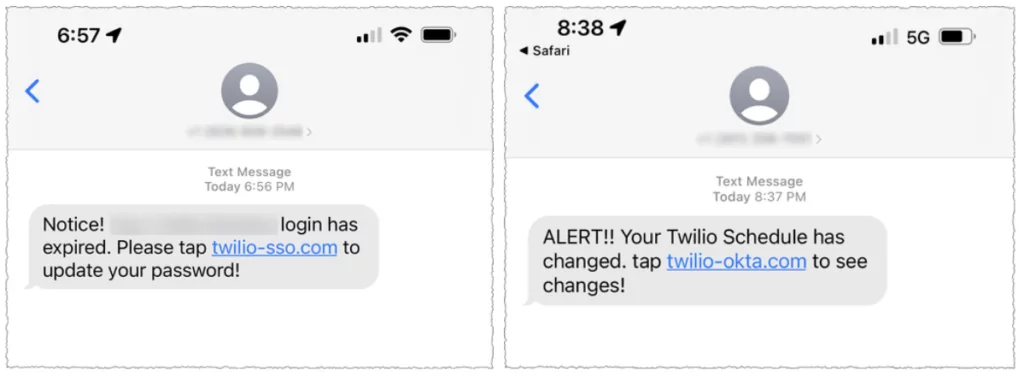
The threat actors had convinced the employees to enter a fake sign-in page in attacks where they impersonated Twilio’s IT department and asked employees to change their passwords or check their schedule through SMS.
1,900 Signal Numbers Leaked
Twilio said in the incident report that they had worked with US carriers and hosting providers to shut the TAs accounts, but the incident soon caused another. 1,900 Signal phone numbers, which supply phone verification services from Twilio, were exposed too.
According to Signal’s investigation, accessing Twilio’s customer support console could make it possible for the attackers to see the SMS verification code needed to sign up for the service. The Signal PIN prevents access to contact lists and profile data, but the TAs could have tried to register phone numbers to other devices.
Risk of Being Targeted in a Chain Attack
Recent events mentioned in this blog might not be sufficient to pinpoint the extent of the impact phishing attacks -or account compromise in general- can have. However, such cyberattack campaigns occur often and must be addressed.
Without implementing proper security solutions for organizational assets, there is always a risk of being compromised by a third party or becoming a target in a chain attack.
A cyberattack experience could be only a click away. An additional authentication method (2FA/MFA) is essential for every account in the digital environment.

































