
Over 1,000 Zimbra Servers Compromised by Auth Bypass Vulnerability
Zimbra Collaboration Suite (ZCS) was found to have an actively exploited authentication bypass vulnerability. The vulnerability is tracked as CVE-2022-37042 and considered high severity.
The vulnerability has just been added to CISA’s list of Known Exploited Vulnerabilities along with CVE-2022-27925. CVE-2022-27925 is an RCE vulnerability, but it requires authentication that could be bypassed after the exploitation of CVE-2022-37042.
Following a successful exploit, the attackers can set up web shells and acquire persistence.
Detailed Explanation of Vulnerabilities
The vulnerability CVE-2022-27925 exists in ZCS’ mboximport functionality and permits arbitrary file upload that could result in remote code execution.
The vulnerability description indicated that its exploitation required valid administrator credentials in addition to being remotely executable. This made it harder for attackers to infiltrate a ZCS instance and carry out widespread exploitation. There are indications of remote exploitation. However, there is no proof the attackers have the required authenticated administrative sessions.
CVE-2022-37042 exists in ZCS’ MailboxImportServlet and enables bypass authentication. It was discovered that it could be exploited in a chain with CVE-2022-27925 to achieve unauthenticated remote code execution, this way, there would be no need for valid administrator credentials when accessing mboximport.
At first, Volexity tested the request without an administrator authentication token. Even though the request had failed, the web shell content had been placed in the correct location. According to an incident log, the attacker failed the request and received a 401 status code when uploading their web shell. An attacker can exploit the vulnerability by simply setting the appropriate parameters in the URL.
Is It Exploited Widely?
Evidence was found through numerous research that CVE-2022-27925 was being widely exploited using the authentication bypass as early as the end of June 2022.
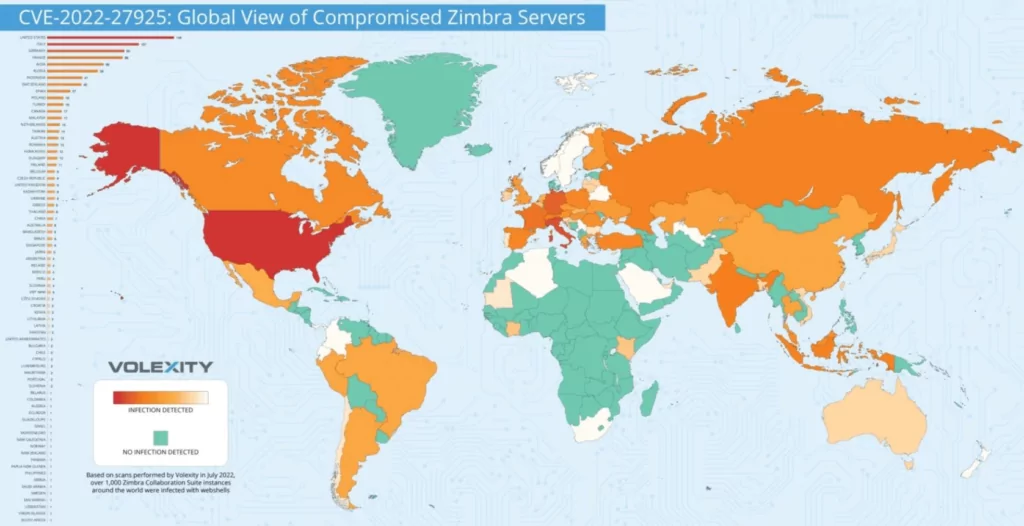
It was initially used by threat actors interested in espionage, but later it was taken by other threat actors and used in mass-exploitation attempts.
Over 1,000 ZCS compromised and backdoored instances have been found worldwide, but the actual number is probably higher. These ZCS instances are part of a wide range of international organizations, including governmental agencies, military sections, multibillion-dollar corporations, etc.
Zimbra Issued Patches to Address the Flaws
Zimbra has provided fixes for CVE-2022-37042 and CVE-2022-27925. It is advised to apply the latest patches if you use versions older than Zimbra 8.8.15 patch 33 or Zimbra 9.0.0 patch 26.
Volexity said web shells could be verified by comparing JSP files on ZCS against default install and shared a repository showing valid JSP files on the latest Zimbra versions.
Check Zimbra’s Security Center for details and updates.




































