
Major Cyber Attacks in Review: April 2024
April 2024 witnessed major cyber attacks targeting sectors from government bodies to technology firms, emphasizing the ever-present and escalating threats in the digital world.
Incidents included a significant ransom demand following the breach of the UAE government, a massive data leak at Dell, and a targeted attack by Russian hackers on Ukrainian infrastructure.
This blog post will delve into the top cyber attacks of April 2024, offering insights into the current threat landscape and drawing lessons to enhance future cybersecurity measures.
Alleged Breach of UAE Government, Hackers Demand $8.9 Million Ransom
A claim by a threat actor with an alias ‘UAE’ about a massive data breach involving the United Arab Emirates government has raised concern.
The hacker threatened to leak the data unless a ransom of 150 bitcoins (approximately $8.9 million) was paid.
The message was also shared by The Five Families on Telegram, enunciating the danger of the data leak as it may entice other threat actors.
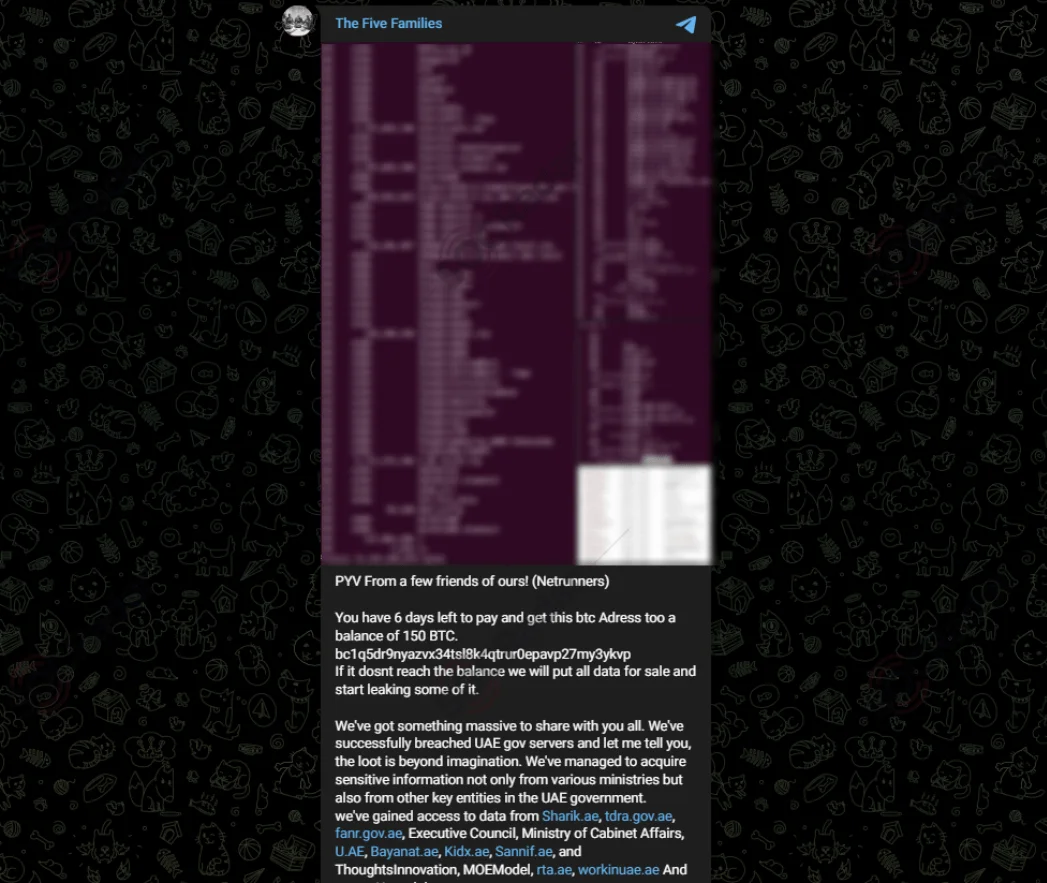
The Five Families’ Telegram post about the UAE breach (SOCRadar Dark Web News)
The alleged victims include major UAE government bodies, ministries, and key government initiatives like Sharik.ae, tdra.gov.ae, fanr.gov.ae, the Executive Council, Ministry of Cabinet Affairs, U.AE, Bayanat.ae, Kidx.ae, Sannif.ae, ThoughtsInnovation, MOEModel, rta.ae, workinuae.ae, and some AI modules.
As of the latest update on May 8, the threat actors have announced a 14-day extension to their ransom demand deadline. However, this extension came at a cost, as they released a 1.9GB sample of the data. Importantly, the contents of the leaked samples include a thousand users’ records, among other data.
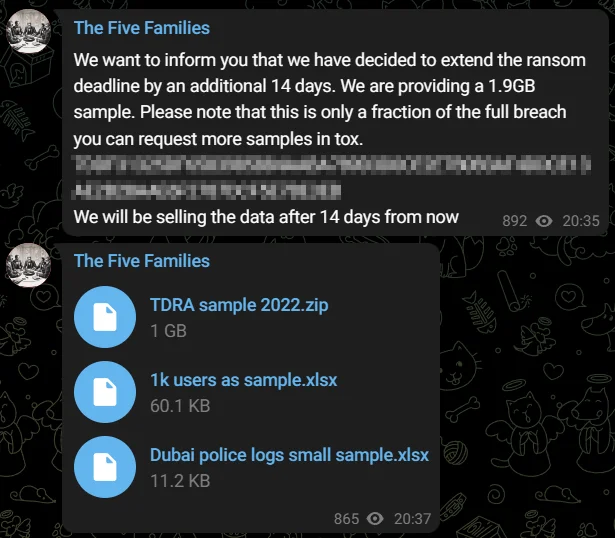
Threat actors have leaked sample data from the alleged UAE breach
FBCS Data Breach Affects 1.9 Million People
The debt collection agency FBCS fell victim to a significant cybersecurity incident in late April 2024, experiencing a data breach that impacted an estimated 1.9 million individuals.

FBCS is a collection agency, operating within the U.S.
The severity of the breach is substantial, with the company indicating that personal information – including names, addresses, and Social Security numbers – could potentially be at risk.
The discovery of the breach came about when FBCS detected unauthorized activity within their network. Upon detecting this suspicious activity, the company launched a thorough investigation. In an effort to bring the culprits to justice and further understand the circumstances surrounding the breach, the company is actively cooperating with law enforcement agencies.
Alleged Sale of Dell Customer Database on Hacking Forum: 49 Million Records Involved
In late April 2024, a potentially significant cybersecurity incident surfaced involving Dell. A threat actor claimed to have obtained and subsequently listed for sale a database containing 49 million records on a hacking forum.
This database allegedly included detailed customer information from purchases made between 2017 and 2024, raising serious concerns about data integrity and privacy.
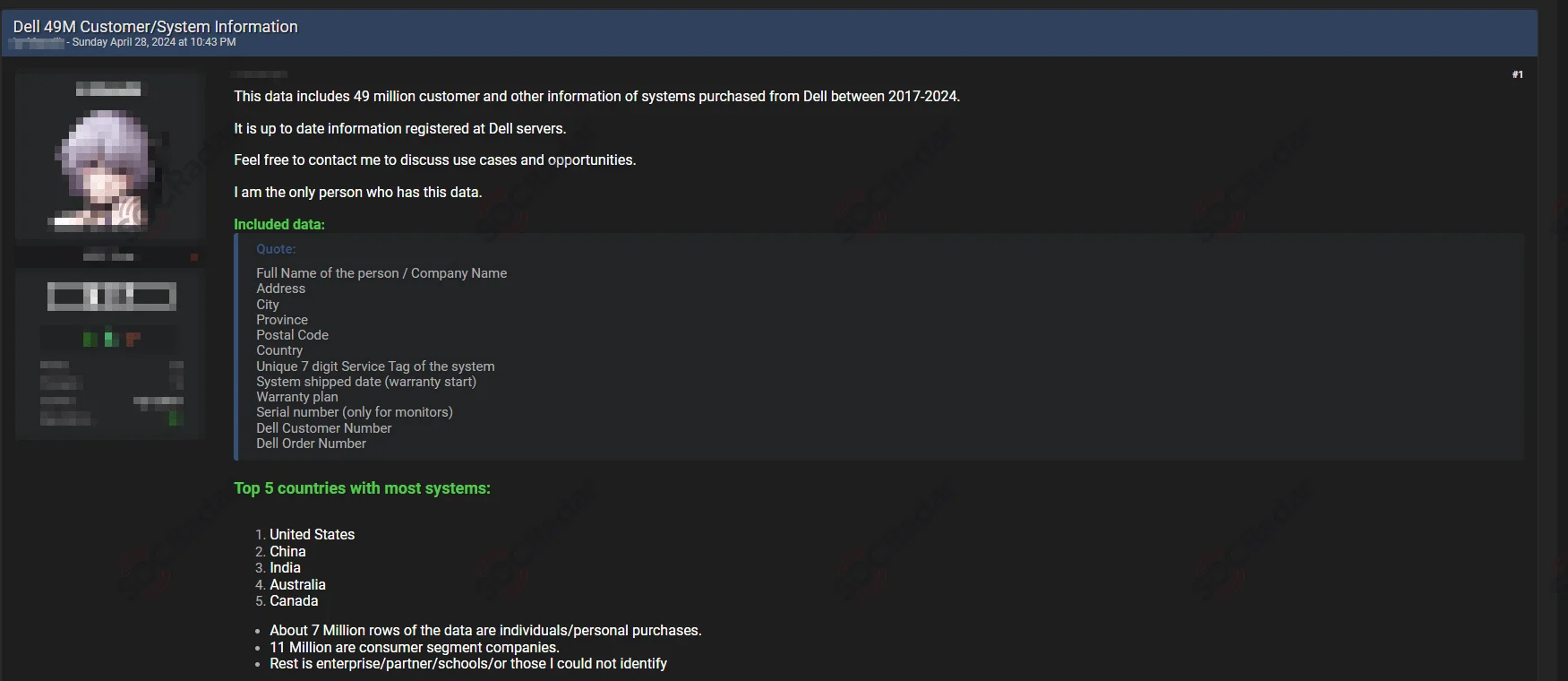
Threat actor’s post on the alleged Dell breach (SOCRadar Dark Web News)
The data put up for sale encompassed full names, company names, addresses, and uniquely identifiable information such as 7-digit service tags, warranty plans and start dates, and serial numbers for monitors. It also includes customer and order numbers, with about 7 million records related to individual personal purchases and 11 million from consumer segment companies.
The threat actor’s assertion that they are the sole possessor of this data hints at the possibility of their direct involvement in the breach. However, the exclusivity of the claim also leaves room for skepticism regarding the authenticity of the data.
The initial forum post has since been removed, and just recently, Dell has issued warnings to its customers about a data breach.
Although it remains unclear whether this data sale post is related to the security incident Dell has disclosed, the company assures customers that the risk is minimal due to the nature of the information involved.
The company is still investigating the incident, which involved a portal with customer purchase information and a database containing limited types of information, such as names, physical addresses, hardware details, and various order specifics.
Russian Sandworm Hackers Targeted 20 Critical Infrastructure Organizations in Ukraine
The notorious Russian hacker group Sandworm, also identified as APT44, has launched a significant cyber offensive against Ukraine, targeting around 20 critical infrastructure facilities across the country.
The group’s primary objective was to disrupt operations at energy, water, and heating suppliers in ten regions, exploiting weak cybersecurity practices to breach these systems.
Sandworm’s activities are believed to be part of a broader strategy to enhance the impact of potential Russian missile strikes on the targeted infrastructure facilities. This assessment comes from the Ukrainian Computer Emergency Response Team (CERT-UA), which reported about these attacks in mid-April.
In response to these cyber threats, CERT-UA carried out a series of counter-cyber attack operations from March 7 to March 15, 2024. These operations involved notifying the affected enterprises, removing the malware from their systems, and implementing enhanced security measures to prevent future attacks.

Learn more about ‘Sandworm’ on SOCRadar’s APT Profile
Over a Million Customer Records Compromised in PandaBuy Data Breach
Two threat actors, “Sanggiero” and “IntelBroker,” tied to the CyberNiggers threat group, breached an online shopping platform named PandaBuy, resulting in the leak of data belonging to over a million customers.
The breach allegedly contained over 3 million records and involved the exploitation of a vulnerability, granting access to a wealth of personal information, including names, usernames, emails, login IPs, order data, and addresses.
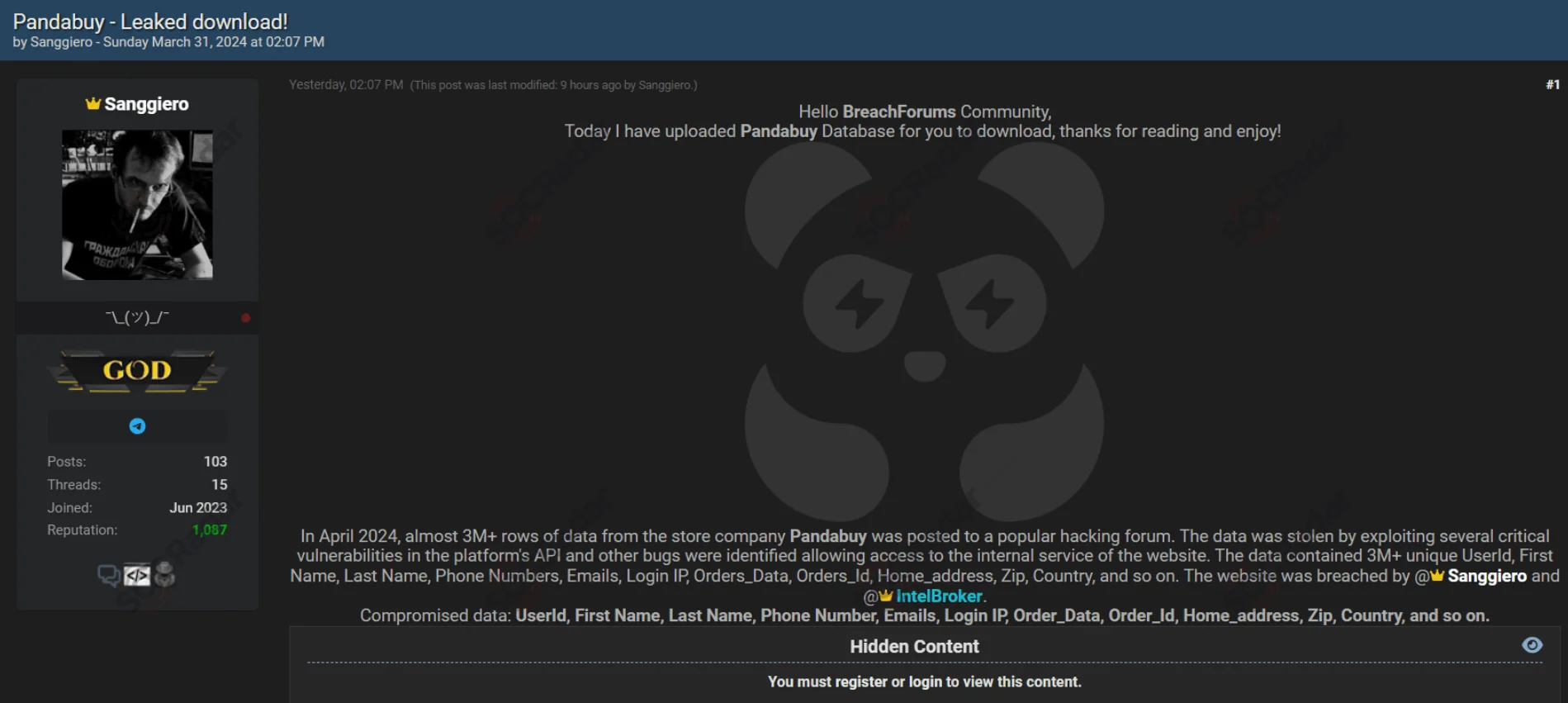
Threat actor’s post (SOCRadar Dark Web News)
To confirm the severity of the breach, data breach service Have I Been Pwned (HIBP) identified nearly 1.35 million valid accounts affected.
The same threat actors were also involved in alleged breaches of HSBC and Barclays banks’ security systems in early April 2024. These breaches resulted in the compromise of extensive datasets, which included hundreds of thousands to over a million lines of data across various files, containing critical banking operation details, transaction records, account details, and user notifications.
Build a Better Security Posture with SOCRadar
In today’s digital landscape, it is challenging to pinpoint what dangers your organization may face or where the next threat will emerge. By adopting advanced security tools and features, your organization can better safeguard its digital environment.
SOCRadar improves your security operations by offering a suite of advanced tools that accelerate vulnerability detection and provide insights for proactive measures. These capabilities are specifically designed to improve your organization’s ability to detect and respond to threats, significantly strengthening its cybersecurity posture.
Some of the key features offered by SOCRadar are:
- Attack Surface Management: This feature enables the discovery, classification, and monitoring of digital assets. It identifies and prioritizes vulnerabilities, aiding in the early detection of security issues and providing visibility into potential attack vectors.
- Vulnerability Intelligence: SOCRadar’s Vulnerability Intelligence collects and analyzes information about security vulnerabilities, presenting it in an insightful format that guides remediation efforts.
- Supply Chain Intelligence: This feature monitors and analyzes the security posture of an organization’s supply chain. It assesses the risk posed by third-party vendors to maintain the integrity of the supply chain and prevent disruptions and compromises.
- Dark Web Monitoring: Scanning the dark web to detect leaks of sensitive information, including customer, employee, and corporate data, it offers insights into potential future threats.
SOCRadar’s Dark Web Monitoring
Apply for the Free Edition to explore how SOCRadar XTI can enhance your cybersecurity stance:


































