
Major Cyber Attacks in Review: July 2024
July 2024 has been marked by a series of high-impact cyber attacks, affecting millions of individuals and numerous organizations. Amidst numerous threat activities, the effects of the Snowflake breach also continue, with several significant incidents related to it surfacing this month.
From financial data breaches to ransomware attacks on healthcare and thefts from cryptocurrency platforms, here are the major incidents that have shaped this month’s cybersecurity landscape.
HealthEquity Data Breach Exposed Sensitive Information of 4.3 Million Americans
In a significant security breach, HealthEquity, a provider of health savings accounts (HSAs), flexible spending accounts (FSAs), health reimbursement arrangements (HRAs), and retirement plans, reported that over 4.3 million Americans’ personal information has been compromised. The breach was caused by threat actors exploiting a partner’s compromised credentials to steal sensitive health data.
The compromised data mainly consists of sign-up information for accounts and benefits administered by HealthEquity, including contact details, employee and employer information, health card and plan details, and prescription information. However, not all data categories were affected for every member.
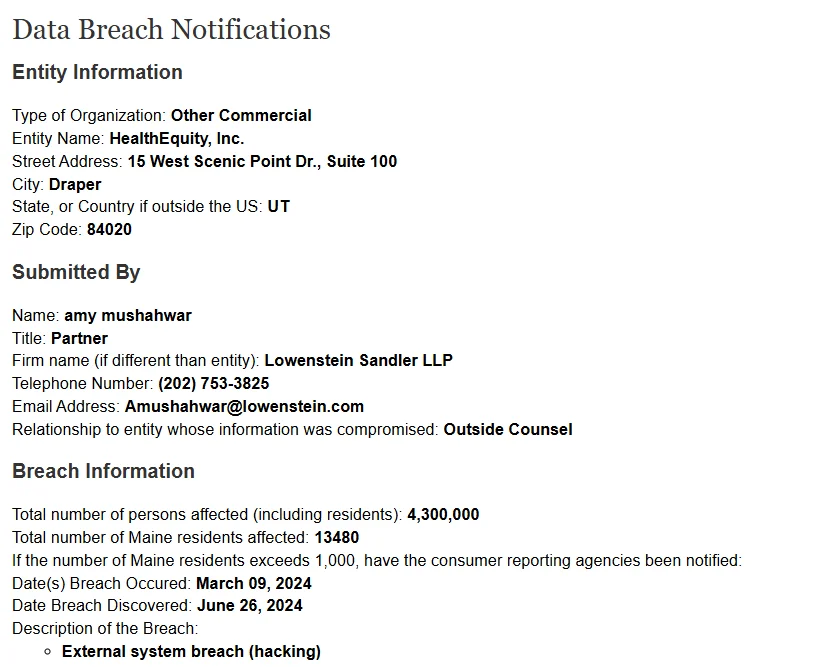
HealthEquity breach filing (Maine.gov)
HealthEquity became aware of the anomaly on March 25, with the investigation continuing until June 10. The company confirmed unauthorized access to protected health information and personally identifiable information stored outside its core systems.
To date, HealthEquity has not detected any misuse of the compromised information.
MediSecure Data Breach Affected 12.9 Million Australians
It was confirmed that in one of the largest data breaches in Australian history, at least 12.9 million individuals’ personal data was stolen in a ransomware attack on MediSecure, an eScript provider. The breach, which persisted until November 2023, was confirmed in May 2024.

Read MediSecure’s statement on the breach here
MediSecure, which facilitates electronic prescriptions and dispensing, reported the loss of 6.5 terabytes of data, including full names, phone numbers, dates of birth, home addresses, Medicare numbers, and medication details. Despite the magnitude of the breach, the company has been unable to identify specific individuals affected due to the complexity and financial constraints of the task.
The breach has raised significant concerns about Australia’s cybersecurity infrastructure. Compounding the issue, MediSecure went into voluntary administration in June after losing its primary government contract.
$230 Million Was Stolen in WazirX Crypto Security Breach
Attackers bypassed the defenses of the India-based cryptocurrency exchange WazirX, stealing over $230 million. Multiple suspicious transactions were detected, and the funds were transferred to an unauthorized address.
The breach targeted WazirX’s Safe Multisig wallet on Ethereum, operated by Liminal. Attackers exploited a discrepancy between Liminal’s interface data and transaction contents, allowing them to alter the payload and gain control.

For more insights into the latest crypto security threats, explore SOCRadar’s 2024 Cryptocurrency & NFT Threat Landscape Report
Rite Aid Data Breach Affected 2.2 Million People
Rite Aid, a leading pharmacy chain in the US, reported a data breach that compromised the personal information of about 2.2 million individuals during a ransomware attack on June 6, 2024.
The RansomHub ransomware group claimed responsibility and demanded a ransom, setting a leak timer for July 26. The attackers claimed to have obtained over 10 GB of customer information, totaling around 45 million lines of data, including names, addresses, driver’s license numbers, dates of birth, and Rite Aid rewards numbers.
Rite Aid discovered the breach on June 20 and initiated an investigation. The stolen data is reportedly limited to purchases made between June 6, 2017, and July 30, 2018, including names, addresses, dates of birth, and driver’s license or other ID document numbers.
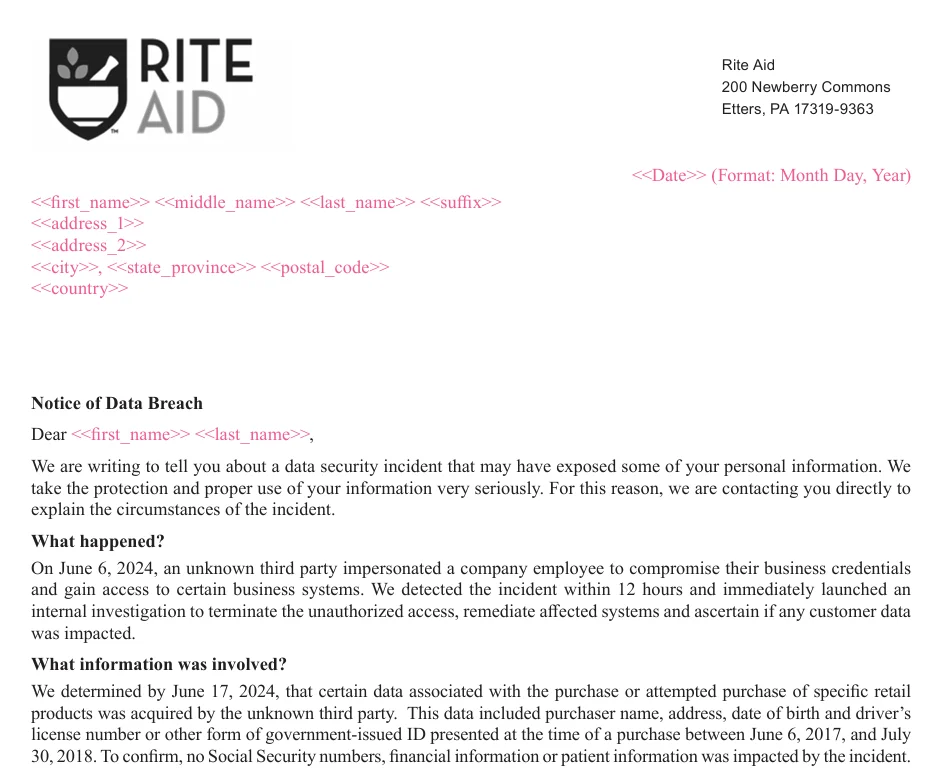
Rite Aid’s breach notification (Maine.gov)
AT&T Data Breach Exposed Phone Records of Millions
In April, AT&T experienced a significant data breach, compromising the phone records of nearly all its customers; the issue led AT&T to notify approximately 110 million affected customers.
Hackers accessed and copied call logs stored on a third-party cloud platform, stealing millions of phone numbers, calling and text records, and location-related data.
The breach, which affected data from May 1, 2022, to October 31, 2022, also impacted customers of other carriers using AT&T’s network. Fortunately, the stolen data did not include the content of calls or texts, but rather metadata such as phone numbers involved, the count of calls and texts, and call durations.
The breach was attributed to John Erin Binns, a US-based hacker operating from Turkey, linked to the ShinyHunters group. Binns claimed that AT&T paid a $370,000 ransom in May to ensure the stolen data was deleted, a claim verified by Wired through blockchain tracking tools.

AT&T notified approximately 110 million customers due to the April data breach (Image from Wikimedia)
Learn the details of this incident on our Snowflake Breach blog post.
Evolve Bank & Trust Data Breach Exposed Personal Information of 7.6 Million
Evolve Bank & Trust informed over 7.6 million individuals that their personal information was compromised in a LockBit ransomware attack. The bank confirmed the breach on July 1, following the ransomware gang’s online leak of the stolen data after a ransom went unpaid.
The attackers accessed names, Social Security numbers, bank account numbers, and contact information for most personal banking customers and those of its Open Banking partners. This breach affected 7,640,112 individuals, who will now receive 24 months of free credit monitoring and identity protection services.
Evolve Bank began sending notifications to affected individuals, explaining that the ransomware attack occurred on May 29, with attackers having access to the network since at least February. The bank assured customers that there was no evidence of accessed funds and no new unauthorized activity since May 31.
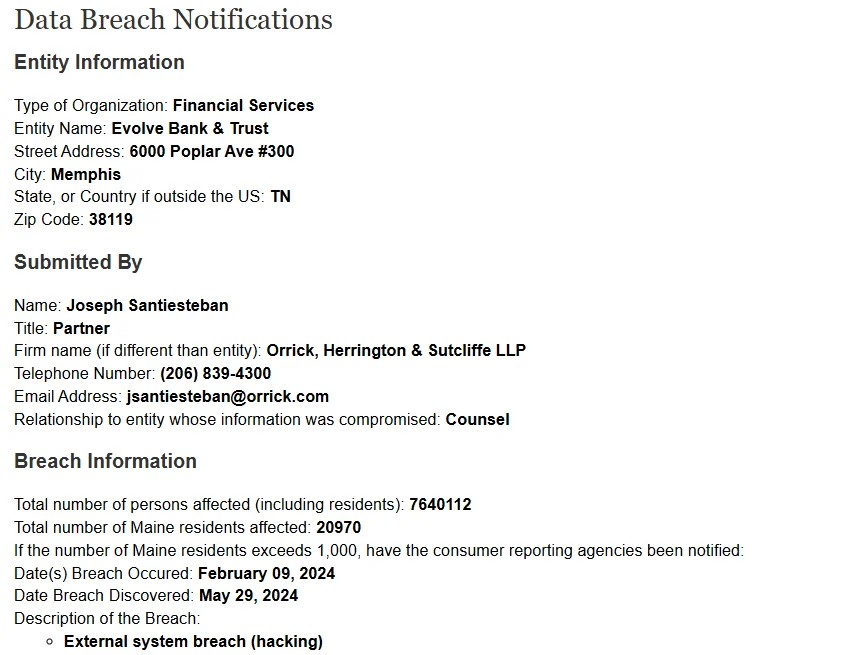
Evolve Bank & Trust breach filing (Maine.gov)
ShinyHunters Allegedly Released High-Profile Individuals’ Data from Neiman Marcus; Celebrity Leaks
In July, ShinyHunters claimed to have stolen 193 million barcodes, including Taylor Swift tickets, valued at nearly $23 billion. They demanded $8 million for the data, hinting at more leaks involving 30 million tickets for 65,000 events.
Sp1d3rHunters followed up on July 5, 2024, by offering 170,000 barcodes for upcoming Taylor Swift shows during “Celebrity Leak Week 1.” They also demanded $2 million from Ticketmaster to prevent the release of data on 680 million users and over 30 million event barcodes, including tickets for major events like P!nk, Sting, F1 racing, MLB, and NFL.
Later, with a post named “Celebrity Leak Week 2,” Sp1d3rHunters released additional data from the Neiman Marcus breach, featuring high-profile individuals like Biden, Trump, Kylie Jenner, and Elon Musk.
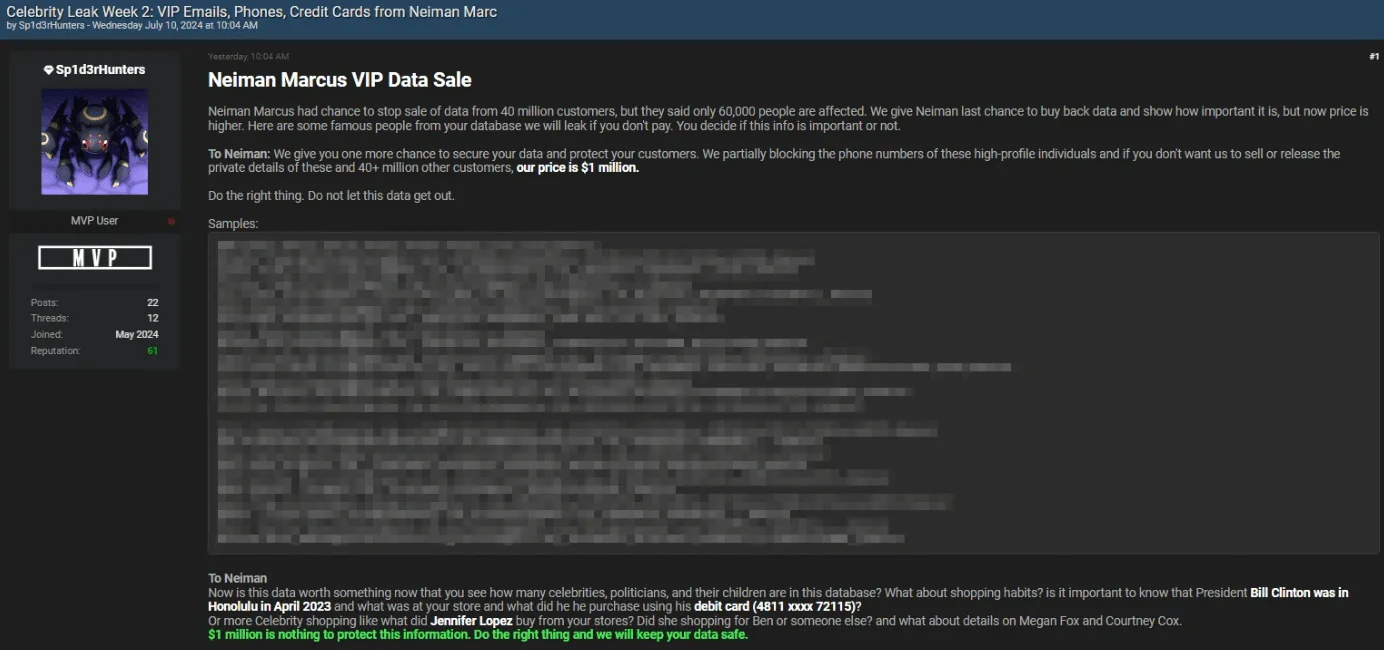
Threat actor’s post: Celebrity Leak Week 2 – Neiman Marcus VIP Data Sale
Late in June, ShinyHunters had leaked an alleged database from Neiman Marcus, exposing data for 40 million customers. With the latest allegations, threat actors threatened to release more sensitive data unless Neiman Marcus paid a $1 million ransom.
Twilio Authy Data Breach Exposed 33 Million Phone Numbers
The SOCRadar Dark Web Team discovered a hacker forum post by ShinyHunters, claiming to have leaked a database from Twilio Authy that affects 33 million phone numbers. The threat actor asserted they breached Twilio Authy and Segment, exposing account IDs, phone numbers, device locks, account statuses, and device counts.
Twilio later confirmed that an unsecured API endpoint enabled threat actors to verify the phone numbers of millions of Authy multi-factor authentication users, leading to this significant data exposure.
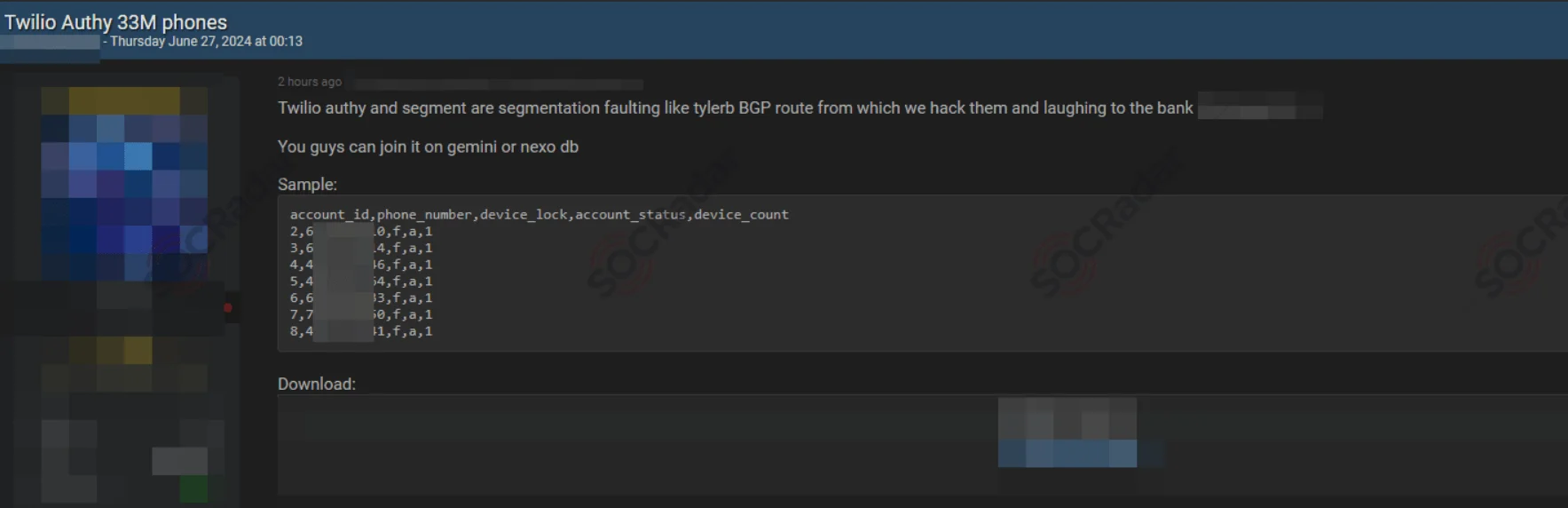
Threat actor’s post about the Twilio breach
Prudential Financial Data Breach Affected 2.5 Million People
Prudential Financial revealed that a data breach in February compromised the personal information of over 2.5 million individuals. Detected on February 5, a day after a suspected cybercrime group accessed its systems, the breach targeted administrative data and employee/contractor accounts.
The BlackCat (ALPHV) ransomware gang claimed responsibility for the attack on February 13.

Learn the operations and TTPs of BlackCat Ransomware (ALPHV) on SOCRadar’s Dark Web Profile
Initially, in a March filing with the Maine Attorney General’s Office, Prudential reported that over 36,000 individuals had their personal information, including names and driver’s license numbers, stolen. However, a later update disclosed that the breach actually impacted 2,556,210 people.


































