
Major Cyber Attacks in Review: November 2022
Although the industry was relatively quiet last month, information is always valuable to both threat actors and us; in fact, it is vital. Helping you to protect sensitive data, whether it be financial, personal, or organizational, is a key service provided by SOCRadar.
Our researchers found many of the major cyberattacks in November included theft or leak of data. You can read more in our blog post.
7.2M Users’ Information Affected by Whoosh Data Breach
The Russian scooter rental service Whoosh has reported a data breach after hackers started to sell a database containing the personal information of 7.2 million users on a hacking forum.
The stolen data allegedly includes promotion codes, payment card information, and partial user identification. Threat actors can use these codes to gain access to the service for free.
In statements published earlier this month in Russian media, the firm announced the cyberattack but stated that its IT specialists had successfully stopped it.
Over $11M Stolen from Banks and Telcos by OPERA1ER

A threat group known as OPERA1ER has used hacking tools to steal at least $11 million from African banks and telecommunications service providers.
According to the researchers, once a victim network has been breached, hackers may use the infrastructure to launch attacks on other targets.
Hackers Expose Information of 9.7M Medibank Customers

Hackers thought to be related to the ex-REvil gang demanded a ransom from Medibank, a private insurance company based in Australia, but Medibank refused to pay.
About 9.7 million customers’ names, birthdates, addresses, phone numbers, and email addresses, as well as those of some of their authorized representatives, were accessed. 24 hours after the threat, attackers posted the documents on the dark web.
Daixin Ransomware Gang Steals 5 Million AirAsia Employees’ and Passengers’ Data
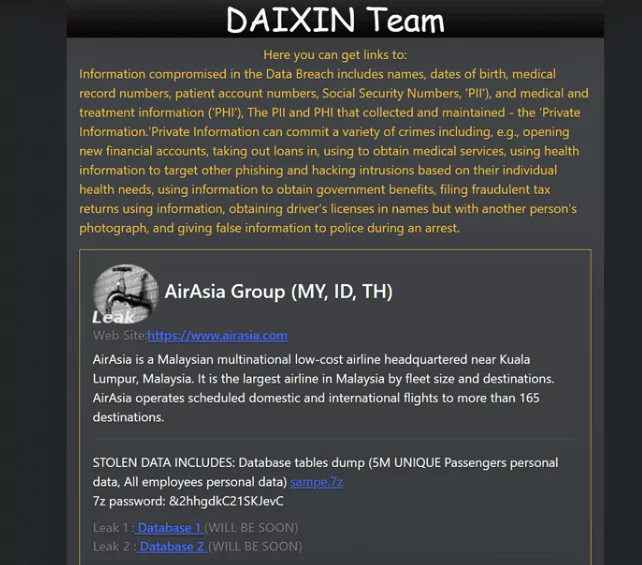
On its data leak portal, the cybercriminal organization Daixin Team has published sample data from the Malaysian low-cost airline AirAsia.
The threat actors allegedly claim that they have access to the personal information of all of the company’s employees and five million distinct passengers.
The samples uploaded to the leak site include employee personal information, passenger information, and booking IDs.
487M WhatsApp Users’ Phone Numbers on Sale

A threat actor offered 487 million WhatsApp users’ phone numbers for sale. The database, which was allegedly created this year, contained phone numbers from users in 84 countries, with most of the records belonging to users in Egypt, Italy, and the United States.
Stolen Twitter User Data Leaked

In August, a flaw in Twitter was exploited, resulting in threat actors obtaining 5.4 million Twitter users’ account information. The database was leaked on a hacker forum in November, making it freely available to every threat actor. The exposed database includes usernames, names, biographies, addresses, email addresses, and phone numbers.
A $28M Hot Wallet Hack Causes Deribit Cryptocurrency Exchange to Halt Withdrawals

On November 1, Deribit exchange reported that its hot wallet had been compromised. After suffering a $28 million hot wallet hack, major cryptocurrency derivatives exchange has stopped accepting withdrawals.
Since Deribit’s reserves cover losses, the exchange highlighted that client funds are secure. Additionally, some sections of Deribit’s website were down after the incident, but Deribit claims it was unrelated to the hack.
The LockBit Ransomware Gang Offers to Sell Continental Files for $50M

Continental, a German multinational auto parts manufacturer, was hacked, as claimed by the LockBit ransomware gang.
According to reports, there was about 40TB worth of stolen data. Some people who are familiar with the case have speculated that the encrypted data could include the board of directors of Continental presentations, draft resolutions, and minutes of supervisory board meetings.
After Continental declined to pay the ransom, LockBit 3.0 is said to have listed the data for sale on its dark web blog for $50 million.
DraftKings’ Customers Fell Victim to Credential Stuffing

DraftKings, a sports betting website, lost $300,000 in a suspected credential stuffing attack. The incident was discovered after some of the company’s clients noticed strange activity in their accounts. DraftKings claimed no proof of a breach and suggested that a credential stuffing attack might have occurred due to reused passwords.



































