
Major Leaks: Twitch, Thai Honda, and Erasmus+ Data Allegedly Exposed
The SOCRadar Dark Web Team continues to monitor the hacker underground; recent findings include the alleged sale of Thai Honda’s customer database, which exposed personal information from millions of customers. Furthermore, a breach of Erasmus+ participant data, a DoorDash leak involving 1.5 million transaction records, and the alleged sale of Twitch user credentials have emerged. Also, a new recruitment post is targeting individuals in the EU banking sector for unauthorized SWIFT payment file modifications, highlighting the ongoing and evolving cybercrime landscape.
Receive a Free Dark Web Report for Your Organization:
Alleged Customer Database of Thai Honda is on Sale
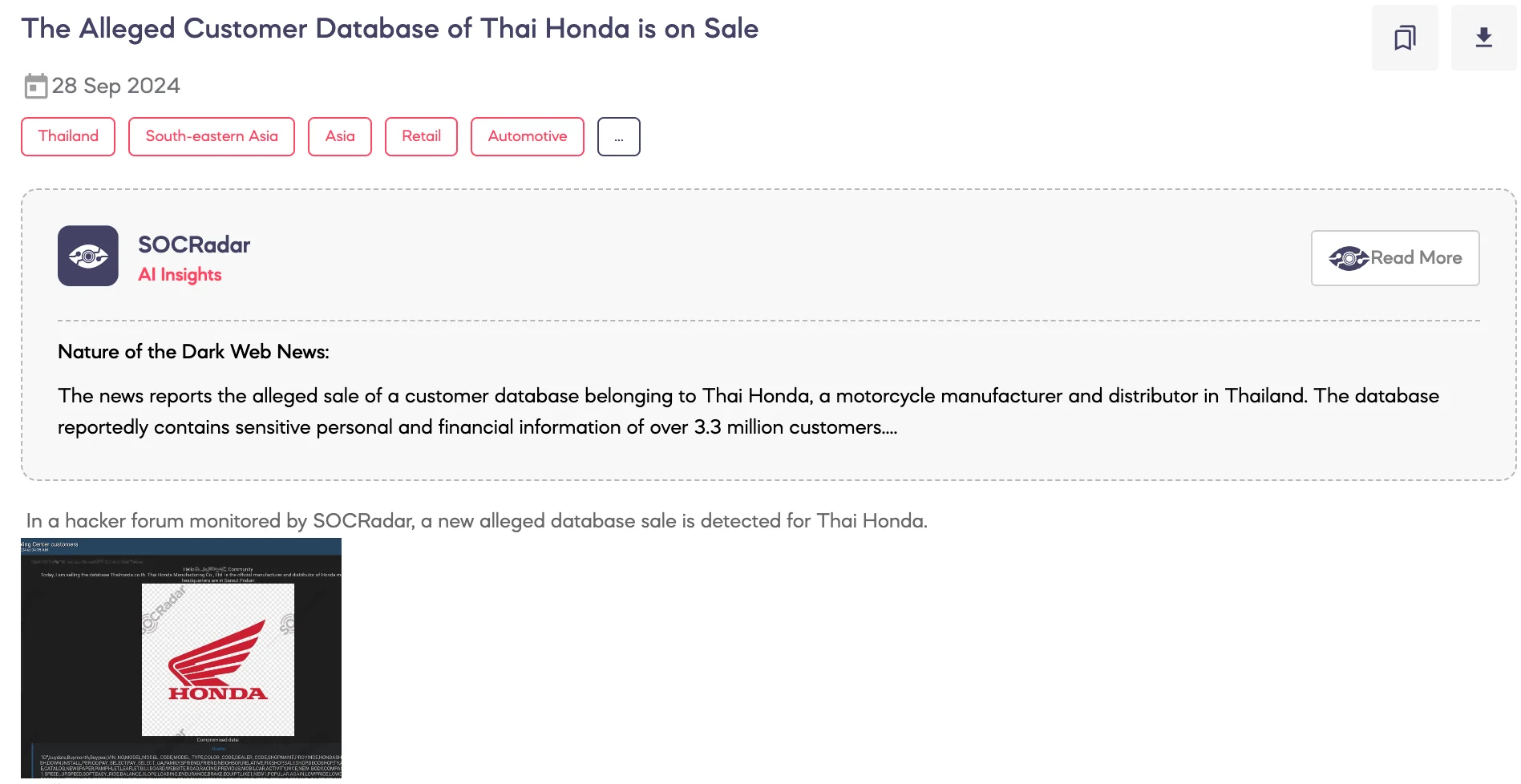
SOCRadar Dark Web Team detected a post advertising the sale of the alleged customer database of Thai Honda Manufacturing Co., Ltd., the official manufacturer and distributor of Honda motorcycles in Thailand.
According to the threat actor’s claims, the leaked data includes detailed customer records such as purchase information, vehicle details, and personal data of 3.3 million Wing Center customers, 38,000 Honda Big Wing customers, and 5,000 Cub House customers. The breach reportedly occurred in September 2024.
The database is being sold for $10,000 in XMR cryptocurrency, with the threat actor offering to remove the data if contacted by Thai Honda staff.
Database of Erasmus+ is Allegedly Leaked
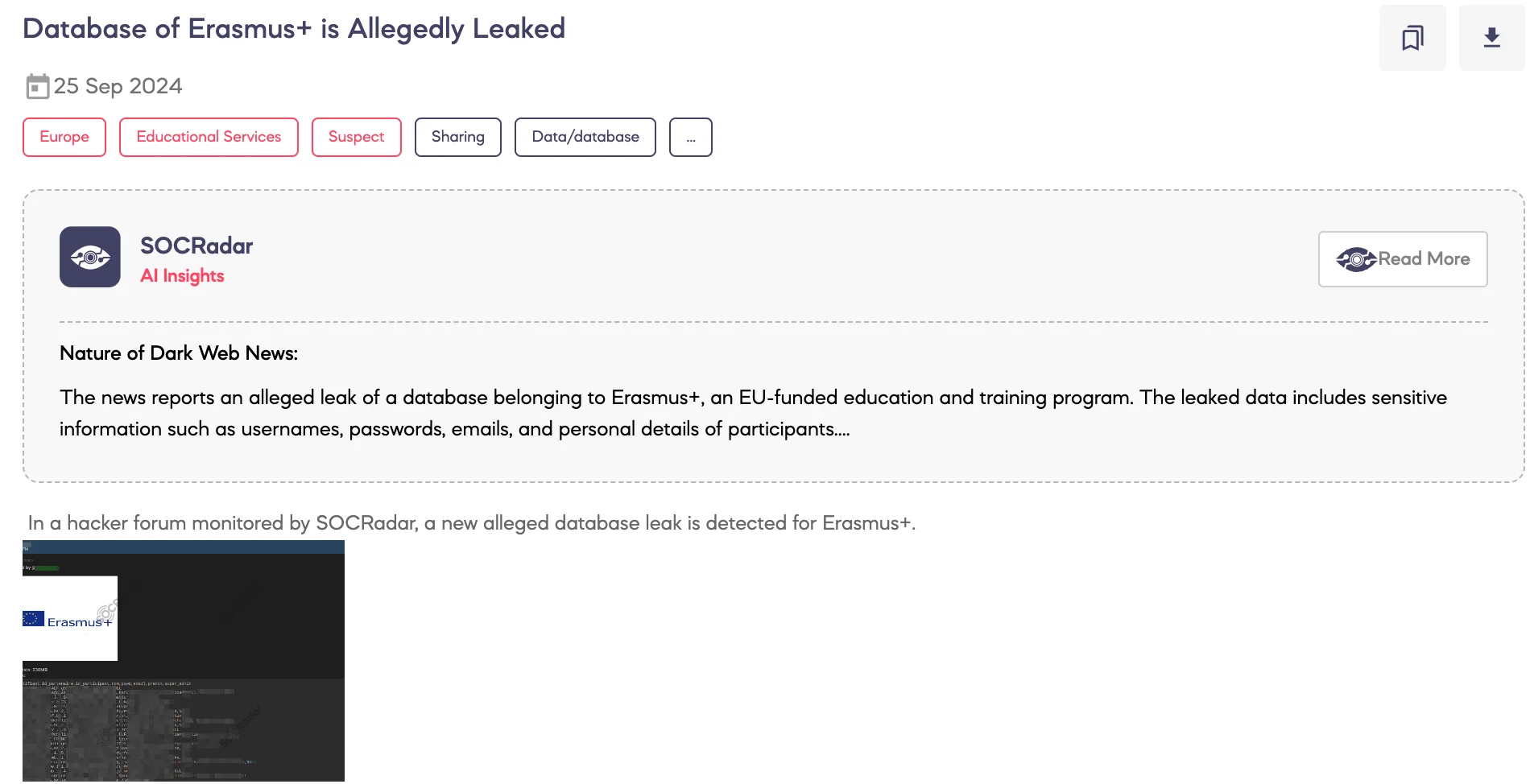
SOCRadar Dark Web Team detected an alleged database leak related to Erasmus+, the EU’s educational exchange program.
According to the threat actor’s claims, the leak contains 230MB of sensitive data, including participant identifiers, partner IDs, names, passwords, email addresses, and administrative details. A sample of the compromised data was shared, indicating a potential breach of personal information.
Threat Actor Claims to Have Breached DoorDash, Allegedly Exposing 1.5 Million Rows of Data
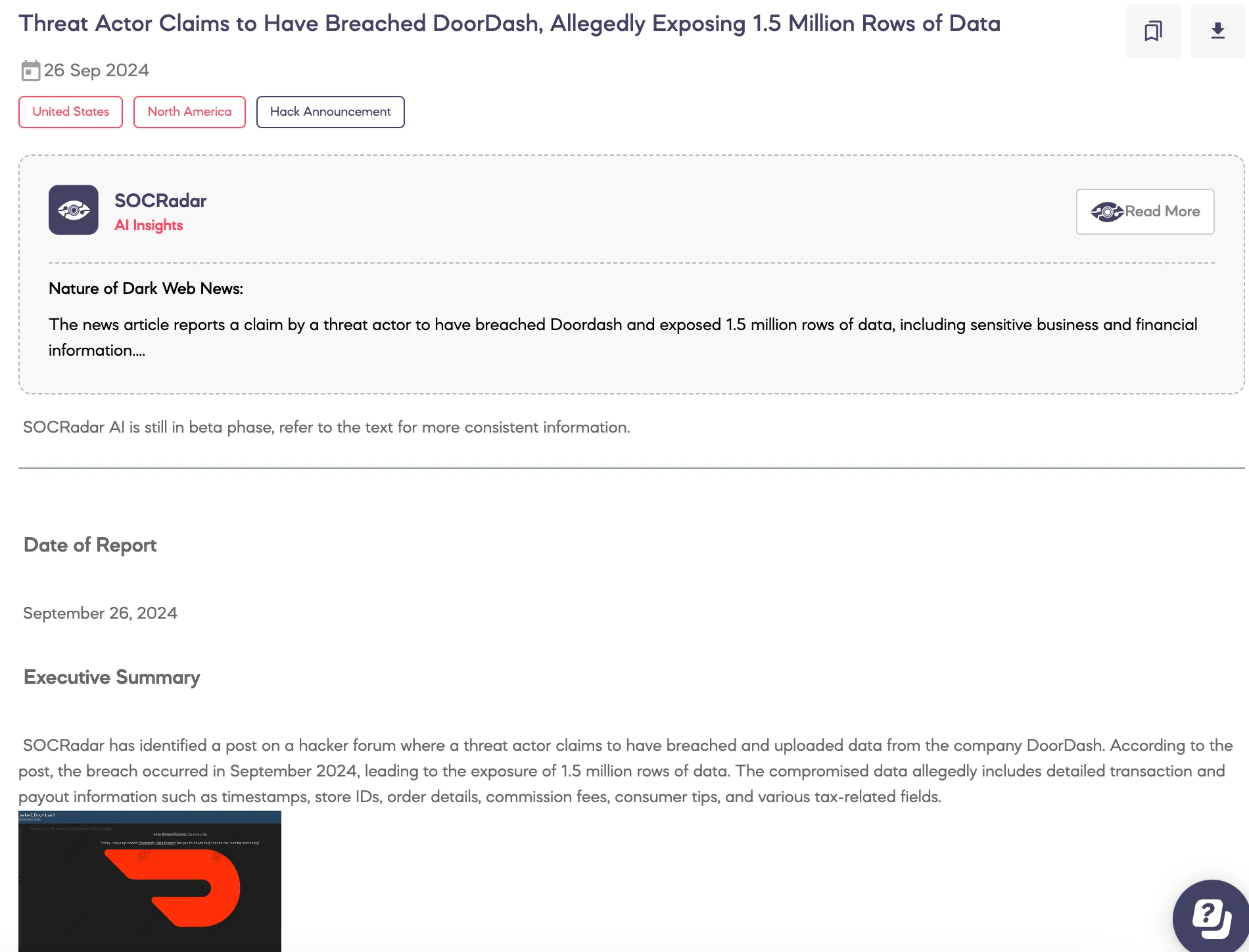
SOCRadar has identified a post on a hacker forum where a threat actor claims to have breached and uploaded data from the company DoorDash. According to the post, the breach occurred in September 2024, leading to the exposure of 1.5 million rows of data. The compromised data allegedly includes detailed transaction and payout information such as timestamps, store IDs, order details, commission fees, consumer tips, and various tax-related fields.
New Recruitment Post is Detected
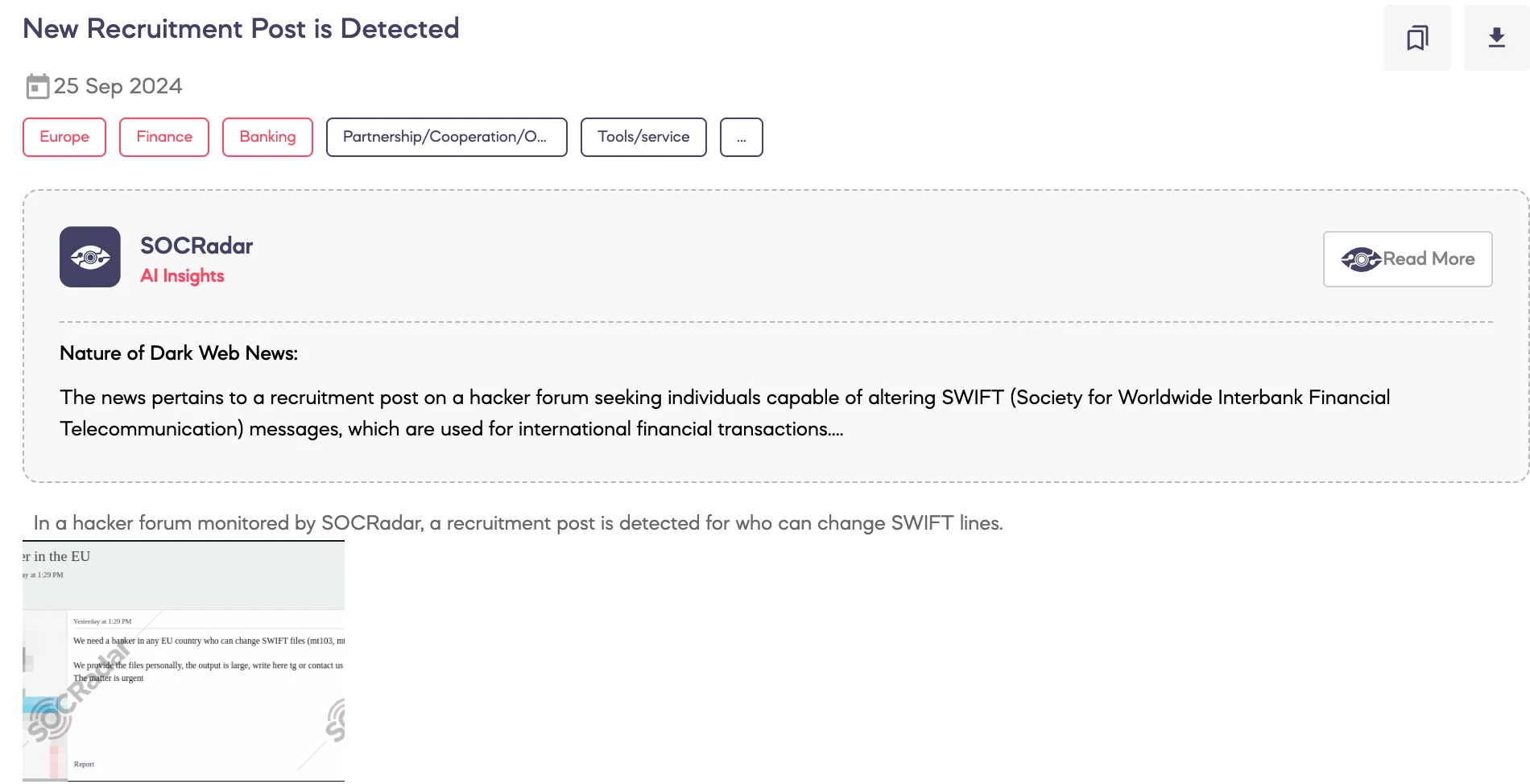
SOCRadar Dark Web Team has detected a recruitment post seeking individuals within the banking sector of EU countries who possess the capability to modify SWIFT files, specifically MT103 and MT199.
MT103 is a standardized proof of payment document used in the SWIFT network for international money transfers. It details the sender, processing institutions, amount, fees, and other transaction information.
MT199 is an interbank message used for free-format communication between banks, often related to private transactions, to indicate readiness to proceed with a financial operation.
The threat actor claims to personally provide the necessary files, indicating that the potential output from such actions could be substantial. Interested parties are encouraged to contact the threat actor via Telegram or through direct communication, with the post emphasizing the urgency of the request.
The Alleged Customer Database of Twitch is Leaked
SOCRadar Dark Web Team detected a post on a hacker forum advertising the alleged leak of a Twitch customer database.
According to the threat actor’s claims, the database contains 526,000 user credentials, including usernames and passwords. Twitch, a popular live-streaming platform primarily used for gaming, allows users to stream content and interact with their audience in real time.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.

































