MGM Resorts Hacked by BlackCat Affiliate, ‘Scattered Spider’
A cybercriminal gang employing a combination of impersonation and malware is the prime suspect behind the cyberattack that crippled the operations of MGM Resorts.
MGM Resorts is a hospitality giant with numerous hotels and casinos in Las Vegas and prestigious properties across the US, including Mandalay Bay, the Bellagio, the Cosmopolitan, and the Aria.
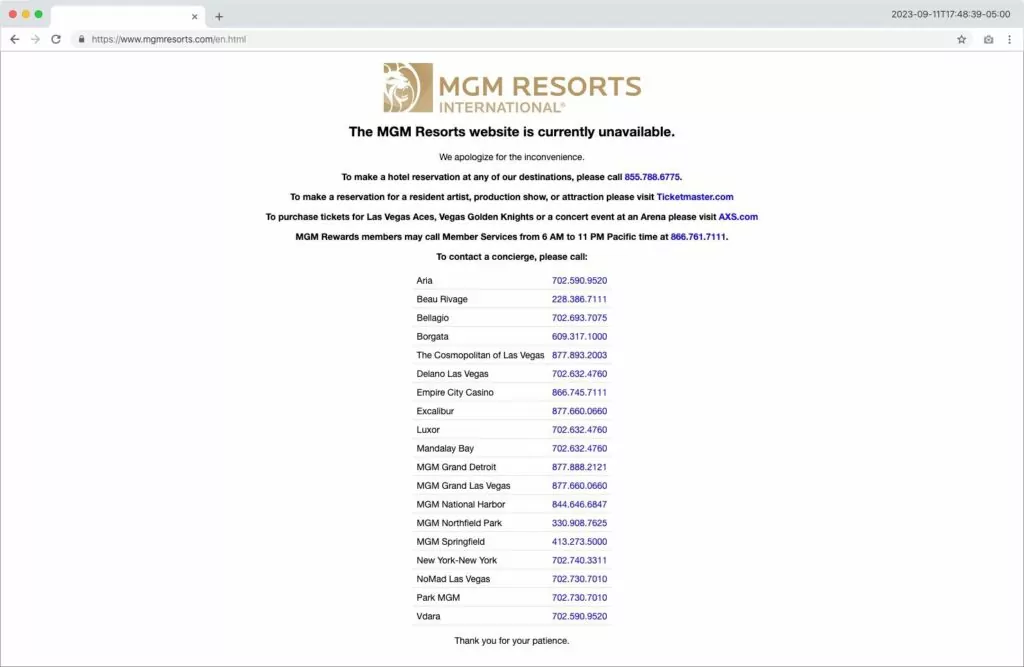
In response to the breach, MGM Resorts had to shut down significant portions of its internal networks, leading to widespread chaos. Electronic winnings transfers slowed down, and access cards for thousands of hotel rooms ceased to function.
The intrusion took place precisely a month after the DEFCON hackers’ conference, held at Mandalay Bay.
How Did Scattered Spider Breach MGM Resorts? BlackCat Gang Claims the Attack
The cyberattack on MGM Resorts on September 10, 2023, has been attributed to a threat group known as “Scattered Spider.” According to reports, this group infiltrated MGM’s systems by conducting searches for employees on LinkedIn and then impersonating the IT help desk.

The aftermath of this attack had a significant impact, leading to disturbances throughout the company’s vast network of more than 30 hotels and casinos worldwide, persisting for an extended duration.
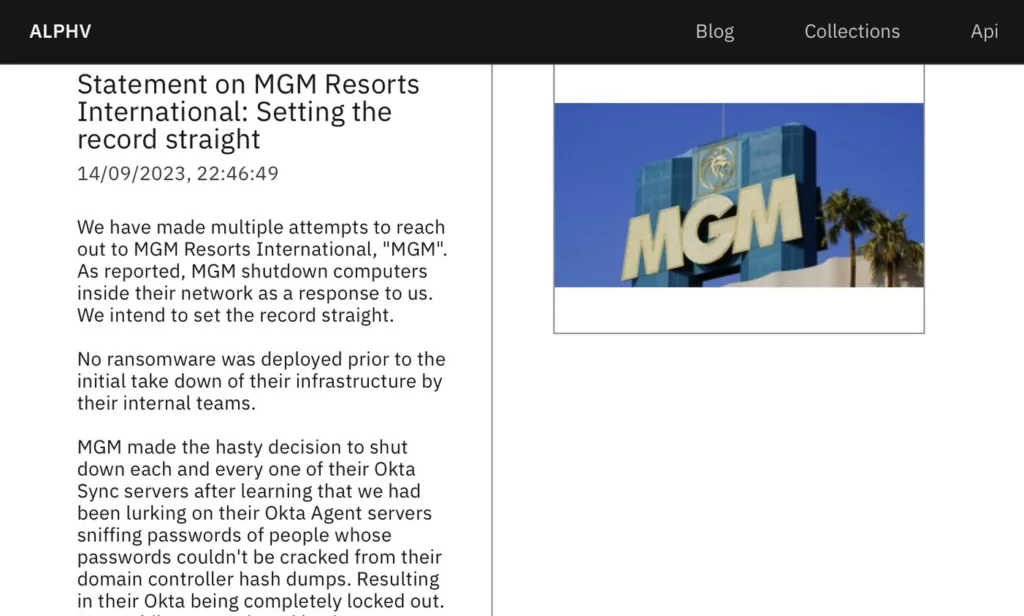
Furthermore, Scattered Spider has been identified as an affiliate of the BlackCat/ALPHV ransomware, as the ransomware group took responsibility for breaching MGM Resorts in a lengthy message posted on their website.
They asserted that they had gained access to MGM Resorts’ Okta and Azure environments starting on September 8, 2023, obtaining administrator privileges and thereby gaining extensive access to the company’s systems.
Caesars Entertainment Was Also Targeted
Scattered Spider also recently targeted Caesars Entertainment and reportedly extracted a significant ransom. This series of cyberattacks began with Caesars Entertainment as the initial victim in late August, followed by MGM Resorts as the second target.
While unofficial reports suggest the ransom paid by Caesars Entertainment could amount to as much as $30 million, the company has not officially confirmed the precise ransom figure.
Both MGM Resorts and Caesars Entertainment have promptly submitted disclosures to the Security and Exchange Commission (SEC) following the ransomware attacks on their casino enterprises. Caesars’ SEC filing, dated September 14, acknowledges an unauthorized actor successfully exfiltrated the company’s loyalty program database on September 7. The database contained sensitive data, including Social Security numbers (SSN) and driver’s license numbers for a substantial number of members.
In contrast to MGM Resorts, which continues to grapple with system outages, Caesars reported to the SEC that their customer-facing operations, including physical properties and online gaming applications, remain unaffected and operational.
As previously noted, the MGM intrusion occurred one month after the DEFCON hackers’ conference. It is worth highlighting that Crowdstrike is also going to be hosting its cyber convention, Fal.Con 2023, at Caesars Palace from September 18 to 21. There is speculation within the internet community that the cyberattacks may be linked to these conventions, though it is essential to emphasize that this notion lacks concrete evidence and remains a matter of conjecture.
Who Is Scattered Spider? (Roasted 0ktapus, UNC3944)
Scattered Spider, also known as Roasted 0ktapus or UNC3944, is a relatively new player in the ransomware landscape, and comprises hackers purportedly based in the U.S. and U.K.
CrowdStrike revealed that Scattered Spider employs a blend of credential phishing and social engineering tactics to acquire one-time password (OTP) codes. Another tactic the group uses is multifactor authentication (MFA) notification fatigue.
The group gathers information for impersonation attacks from social media profiles. Subsequently, they utilize misleading phone calls directed at employees and help desks with the intent of pilfering login credentials.
Once obtaining the login credentials, Scattered Spider avoids using distinctive malware, opting instead for a variety of legitimate remote management tools to maintain persistent access.
A report indicates that a recent phishing campaign by this group compromised 9,931 accounts across over 136 organizations, including Riot Games, Reddit, Twilio, and Cloudflare.
The group has employed these same techniques in their attacks on MGM and numerous other Western companies, all with the aim of receiving ransom payments.
Monitor Threat Activity with SOCRadar
Understanding and tracking threat actors is an ongoing effort, as they use an ever-changing set of tools and tactics. Using SOCRadar’s Threat Actor Tracking, you can constantly monitor threat actor and malware activities and stay ahead of potential threats. Furthermore, you can access detailed information about threat actors, including their targeted vulnerabilities, affiliations with other actors, and indicators of compromise.