Microsoft Alerts of RCE and DoS Vulnerabilities in Perforce Server: CVE-2023-45849, CVE-2023-35767, CVE-2023-45319, CVE-2023-5759
During a security review of its game development studios, Microsoft found four vulnerabilities in Perforce Helix Core Server. These vulnerabilities could be remotely exploited by unauthenticated attackers to cause Denial-of-Service (DoS) or potentially grant an attacker full control of a system.
The Perforce Helix Core Server, also known as ‘Perforce Server,’ serves as a source code management platform widely utilized across diverse industries, including gaming, government, military, technology, and retail.
Microsoft reported vulnerabilities to Perforce in late August, which began investigating and reserved the CVE IDs by late October. Perforce released the patches addressing the four vulnerabilities in early November 2023.
Details of Perforce Server Vulnerabilities (CVE-2023-35767, CVE-2023-45319, CVE-2023-5759, and CVE-2023-45849)
A critical vulnerability, CVE-2023-45849 (CVSS score 9.8), grants unauthenticated attackers the ability to execute code from LocalSystem – a highly privileged Windows OS account designated for system functions. This account level facilitates access to local resources, system files, and the modification of registry settings. The vulnerability stems from the mishandling of the user-bgtask RPC command by the server. In its default configuration, Perforce Server allows unauthenticated attackers to remotely execute various commands, including PowerShell scripts, as LocalSystem.
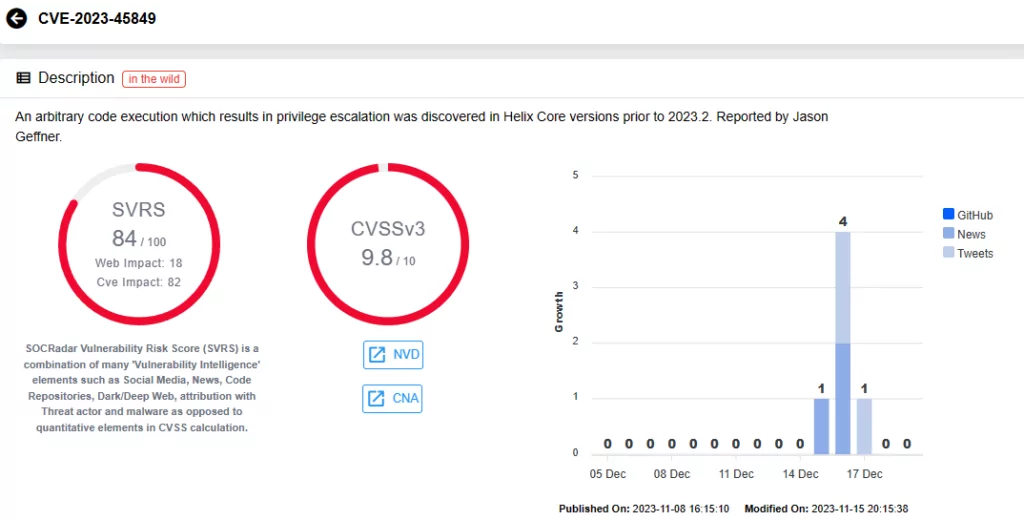
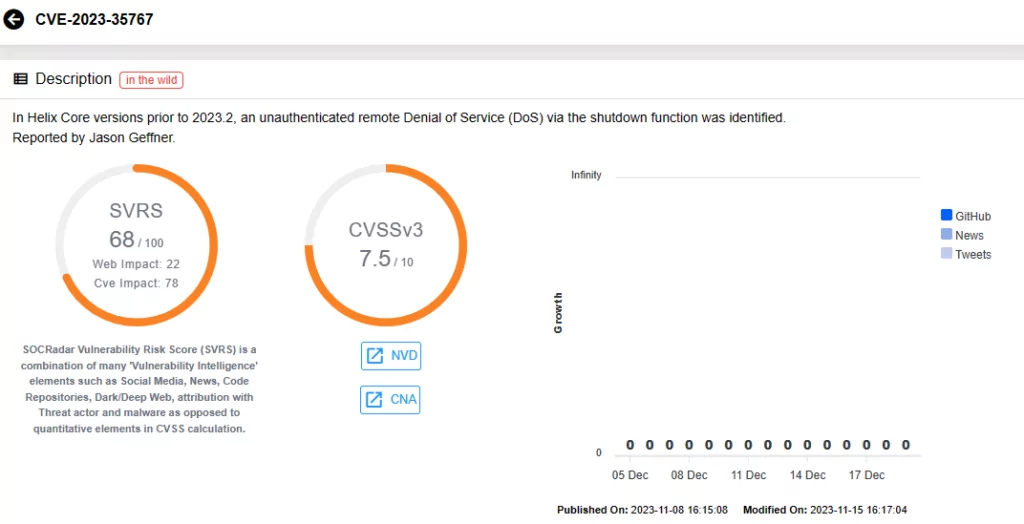
The other three vulnerabilities, which can allow for Denial-of-Service (DoS) attacks, all carry CVSS scores of 7.5:
CVE-2023-35767 and CVE-2023-45319 enable an unauthenticated attacker to induce DoS through remote commands, while the last vulnerability, CVE-2023-5759, can be exploited via RPC header.
Microsoft has not identified any instances of these vulnerabilities being exploited in the wild. Nevertheless, it is crucial to remain vigilant, as attackers can exploit the critical vulnerability (CVE-2023-45849) to install backdoors, access sensitive information, change system settings, and potentially take complete control of a system running a vulnerable Perforce Server version, as well as pivot to connected infrastructure. Consequently, the potential impact of CVE-2023-45849 extends beyond the vulnerable component, posing a risk to software supply chains.
SOCRadar XTI provides real-time alerts and comprehensive Vulnerability Intelligence to proactively address critical vulnerabilities. This service keeps organizations informed about vulnerabilities targeted by threat actors, offering actionable insights to streamline responses. Access vulnerability updates and details, including SVRS scores, through the Vulnerability Intelligence feature for a better understanding of their popularity and likelihood of exploitation.
How to Secure Perforce Server Against the Vulnerabilities?
Microsoft, despite not detecting any active exploitation attempts, strongly recommends users to update Perforce Server to version 2023.1/2513900 to avoid risk of exploitation.
Microsoft also advises following Perforce’s guidance and implementing security measures such as:
- Regularly monitor and apply patches for third-party software.
- Utilize a VPN and/or an IP allow-list to restrict communication with your Perforce Server.
- Issue TLS certificates to verified Perforce users and deploy a TLS termination proxy in front of the Perforce Server to validate client TLS certificates before allowing connections.
- Log all access to your Perforce instance, both through network appliances and the server itself.
- Configure alert systems to promptly notify IT administrators and the security team in case of process crashes.
- Employ network segmentation to limit the potential for attackers to pivot within your network.
How Can SOCRadar Help?
Leverage SOCRadar’s Attack Surface Management (ASM) for ongoing monitoring of your digital assets against emerging threats. This module provides detailed insights into your asset inventory and ensures timely alerts for potential security vulnerabilities affecting your organizational assets.