
Microsoft and VMware Warn of Ongoing Chromeloader Malware Campaign
Microsoft and VMware cautioned users about a widely spread Chromeloader malware campaign. The malware is said to have evolved and become more threatening.
Microsoft has posted an alert on Twitter about an active click fraud campaign that utilized Chromeloader, attributed to threat actor DEV-0796.
Chromeloader detections peaked in May this year. The malware is a browser hijacker with adware functionalities; it modifies web traffic and promotes unwanted, malicious search results to the user. It has been observed dropping malicious extensions, node-WebKit, and ransomware. As per malware’s activity, the user could become a victim of fraud or hacking.
New Variations
A technical report by VMware outlines the various Chromeloader variations that have recently been used.
In an example where the threat actors imitated OpenSubtitles, they switched from the typical resources.bat file to one called properties.bat, which is used to install the malware and establish persistence with registry keys.
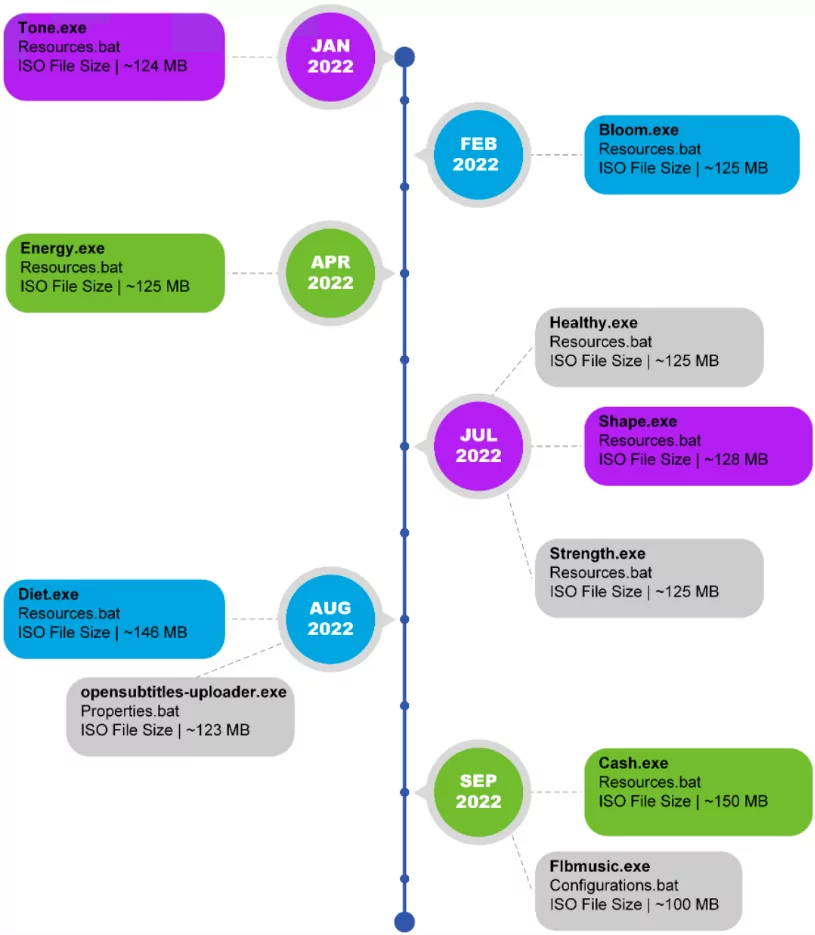
The most recent variant is Flbmusic[.]exe, which impersonates the FLB Music player and has an Electron runtime that enables the malware to load extra modules for network communication and port eavesdropping.
For some variants, the attacks became a little more severe; when the ZipBomb is launched, the malware overloads the user’s system with data and destroys it.
Dropping Malware
Malicious advertising, browser reroutes, and YouTube comments are used to spread ISO files that install the ChromeLoader malware. The attack requires user interaction.
Since Microsoft started blocking Office macros by default, ISO files have grown in popularity as a means of spreading malware. Furthermore, ISOs are an effective approach to spread numerous malware files simultaneously in Windows 10 and later versions as, upon double-clicking, they are automatically mounted as a CDROM under a new drive letter.
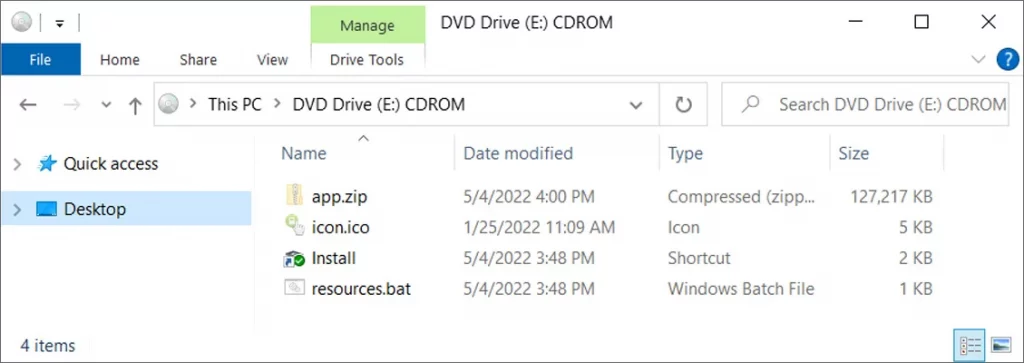
Four files are frequently seen in ChromeLoader ISOs:
- ZIP package holding the malware,
- ICON file,
- A batch file (often called Resources.bat) that installs the malware
- Windows shortcut that runs the batch program
What’s worse is that current Chromeloader variations have been observed spreading the Enigma ransomware using an HTML file.
A dated ransomware variant called Enigma uses a JavaScript-based installer and an embedded executable so that it can be started right from the default browser.
Following the completion of the encryption, the .enigma filename extension is applied to the files, and the ransomware drops a readme.txt file giving instructions.
Chromeloader Malware IoCs
Adware hijacks are a typical case. Chromeloader stands out with its prevalence. It is advised to use trusted sources only and never click a URL without ensuring that it is secure.
Check for indicators of compromise to avoid installation of the malware.
C2 Servers:
- betasymbolic[.]com
- krestinaful[.]com
- tobepartou[.]com
- tobedirectuke[.]com
- eandworldw[.]com
- etobepartou[.]com
- kfareputfeabl[.]com
- blesasmetot[.]com
- siwoulukdlik[.]com
- sforourcompa[.]com
Installer Servers:
- brokenna[.]work
- etterismype[.]co
- idwhitdoe[.]work
- ithconsukultin[.]com
- learnataloukt[.]xyz
- rsonalrecom[.]co
- yflexibilituky[.]co
- yeconnected[.]com
- ableawid[.]com
- airplanegoobly[.]com
- baganmalan[.]com
- balljoobly[.]com
- balokyalokd[.]com
- boogilooki[.]com
- bookimooki[.]com
- carfunusme[.]com
- carmoobly[.]com
- chairtookli[.]com
- chookiebooki[.]com
- choopinookie[.]com
- ckgrounda[.]com
- computermookili[.]com
- dubifunme[.]com
- dudesurfbeachfun[.]com
- exkcellent[.]com
- funbeachdude[.]com
- ketobepar[.]com
- kooblniplay[.]com
- letfunhapeme[.]com
- lookiroobi[.]com
- lookitoogi[.]com
- madorjabl[.]com
- malanbagam[.]com
- mokkilooki[.]com
- myeducatio[.]com
- nakasulba[.]com
- ndinterper[.]com
- ndworldwi[.]com
- nookiespooti[.]com
- oempafnyfi[.]com
- saveifmad[.]com
- siwoulukdli[.]com
- slootni[.]com
- sonalskills[.]com
- tabletoobly[.]com
- toogimoogi[.]com
- toukfarep[.]com
- uiremukent[.]com
- ukrawinrusyes[.]com
- utfeablea[.]com
- voobmijump[.]com
- xoomitsleep[.]com
- yalfnbagan[.]com
- yalokmalos2[.]com
- yescoolservmate[.]com
- yourretyeq[.]com
- tcaukthw[.]com
- tooblycars[.]com
- koooblycar[.]com
- rooblimyooki[.]com
- yooblygoobnku[.]com
- playkooblni[.]com
- rockslootni[.]com
- muendakere[.]xyz
- mployeesihigh[.]xyz
- adiingsinsp[.]xyz
- ajorinryeso[.]xyz
- ktyouexpec[.]xyz
- learnataloukt[.]xyz
- ngwitheaam[.]xyz
- ptonnervent[.]xyz
- ukmlasttyye[.]xyz
- ukseseem[.]xyz
- withyourret[.]xyz


































