
Malicious Chrome Extensions Could Affect More Than 1.4 Million Users
McAfee researchers discovered several malicious Google Chrome extensions. The total download count for the extensions is over 1.4 million. The extensions are capable of tracking and stealing browser activity.
The malicious extensions are listed as:
- Netflix Party
- Netflix Party 2
- Full Page Screenshot Capture – Screenshotting
- AutoBuy Flash Sales
These extensions offer different functionalities to users, but their malicious activity is very similar. They track when users visit shopping websites.
On the web app, manifest.json loads a multifunctional script named B0.js, which sends the browsing data to the hacker’s domain (langhort[.]com) via a POST request. This data includes base64 encoded URL, user ID, location, and an encoded referral URL.
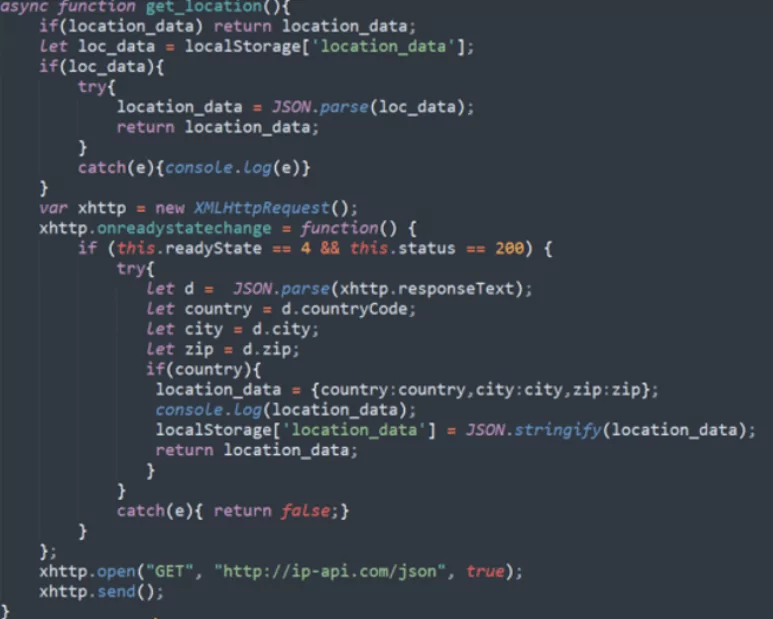
This compromises user privacy and allows extensions to modify their cookie to add the referrer link, extensions’ owner is paid a certain amount for the referrals.
The visited URL is checked against a list of websites to see if the extension’s owner has an active affiliation with the website. If they do, the server replies to B0.js and embeds the referral link as an iframe on the legitimate website.
McAfee has shared a video demonstrating how malicious activity is carried out.
Some of the extensions delay malicious activity to prevent early detection. Even if a user is not actively affected by these extensions, security experts advise deleting them as soon as possible.
2.5M Student Loan Accounts’ Data Exposed Due to Nelnet Servicing Breach
After threat actors broke into the servers of technology services provider Nelnet Servicing, information for over 2.5 million people with student loans from Oklahoma Student Loan Authority (OSLA) and EdFinancial was disclosed.
To provide online access to student loans, OSLA, and EdFinancial leverage technology services from Nelnet Servicing, including a web portal.
The following details were revealed:
- Full name
- Social Security Number
- Physical address
- Phone number
- Email address
Threat actors accessing this data may use it for social engineering, impersonation, phishing attacks, and other scams.
Nelnet Servicing has notified OSLA and EdFinancial, notifying their customers, of a sample notification letter to the impacted parties. The letters state that the incident did not reveal financial account numbers or other payment-related data.
EdFinancial and OSLA provide affected individuals free 24-month Experian identity theft protection service access.
It’s advised to review bank account statements and order a credit report. In high-risk situations, freezing your credit should be an option. The notices that have been provided include instructions on how to do that.
A Streaming Service Discloses a Data Breach that Affected 7.5M Users
A data breach affecting millions of users has been confirmed by the Russian media streaming service “START” (start.ru). The platform administrators revealed that hackers broke into their network and took a database for the year 2021, which they then used to distribute samples online.
The stolen database contains the following information:
- Usernames
- Email addresses
- Phone numbers
The fact that it cannot be used to take over accounts makes it uninteresting to most hackers, according to START.
Financial data, bank card information, browsing history, or user passwords were not affected because they were not stored in the database.
In a Telegram message, START stated that they had already patched the vulnerability and blocked access to the data.
On August 28, when a 72GB MongoDB JSON dump containing the personal data of over 44 million people started to circulate via a social network, the first reports of a START data breach surfaced.
Some entries in this list relate to testing accounts. But 7,455,926 separate email addresses are included in the dump, which is probably close to the number of persons exposed.
Users who registered the service after September 22, 2022, are unaffected by this occurrence. Because the records are up to current as of that date.
One difference between START’s announcement and the leaked dump is that the latter includes information that has not been published in the platform’s official statement, such as md5crypt-hashed passwords, IP addresses, login logs, and subscription details.



































