
Microsoft May 2024 Patch Tuesday Highlights: 61 CVEs, Actively Exploited Zero-Days (CVE-2024-30051, CVE-2024-30040)
In Microsoft’s May 2024 Patch Tuesday, the tech giant has rolled out fixes for 61 security vulnerabilities, marking another significant update that users and administrators should pay close attention to.
Among the newly disclosed vulnerabilities, a single vulnerability affecting SharePoint has been tagged critical on Microsoft advisories; more importantly, two of the other vulnerabilities are currently being exploited as zero-days, which have promptly been added to the Known Exploited Vulnerabilities (KEV) Catalog.
This month’s patch addresses a diverse array of vulnerabilities, spanning from Remote Code Executions (RCE) which make up the bulk, to Elevation of Privilege (EoP) and Information Disclosure issues. The patches also cover less common but equally critical areas such as spoofing, Denial-of-Service (DoS), security feature bypass, Cross-Site Scripting (XSS), and tampering vulnerabilities.
- 26 Remote Code Execution (RCE) Vulnerabilities
- 17 Elevation of Privilege (EoP) Vulnerabilities
- 7 Information Disclosure Vulnerabilities
- 4 Spoofing Vulnerabilities
- 3 Denial of Service (DoS) Vulnerabilities
- 2 Security Feature Bypass Vulnerabilities
- 1 Cross-site Scripting (XSS) Vulnerability
- 1 Tampering Vulnerability
As Microsoft aims to strengthen defenses against potential cyberattacks with these updates, we aim to offer a comprehensive overview of the entire update, examining the risks associated with ongoing zero-day exploits, critical vulnerabilities, and the products at risk.
What Are the Zero-Day Vulnerabilities Addressed in May 2024 Patch Tuesday?
In May 2024 Patch Tuesday, Microsoft tackled two important zero-day vulnerabilities that have been actively exploited in the wild, identified as CVE-2024-30051 and CVE-2024-30040. These vulnerabilities could allow attackers to elevate privileges on the system and execute arbitrary code.
CVE-2024-30040 (CVSS: 8.8): This vulnerability involves a Security Feature Bypass within the MSHTML (Trident) engine used by Microsoft Windows.
It has been exploited in the wild, where attackers have utilized social engineering tactics such as spear-phishing via email, social media, or instant messaging, tricking users into opening specially crafted documents that trigger malicious code execution on the victim’s system.
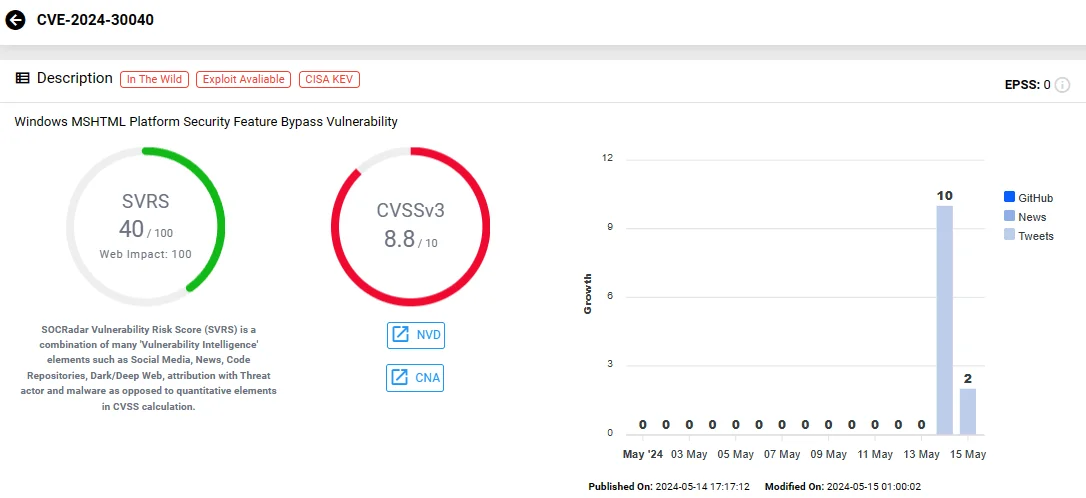
Vulnerability card of CVE-2024-30040 (SOCRadar Vulnerability Intelligence)
CVE-2024-30051 (CVSS: 7.8): This vulnerability is an Elevation of Privilege (EoP) issue in Microsoft Windows’s DWM Core Library.
It was both exploited in the wild and publicly disclosed before a patch was made available, highlighting the urgency of its remediation.
Attackers exploiting this vulnerability could gain SYSTEM privileges on a compromised system, typically after achieving initial access through less privileged accounts.
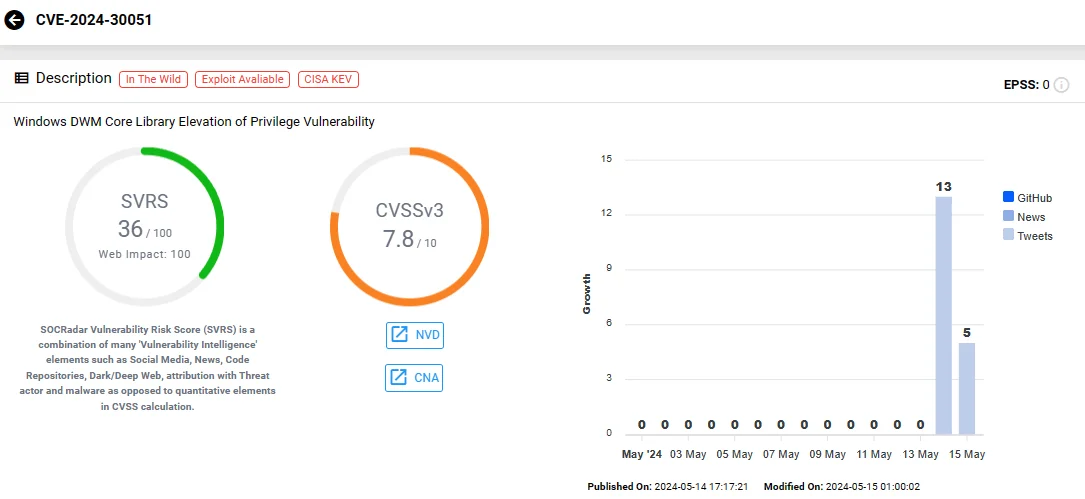
Vulnerability card of CVE-2024-30051 (SOCRadar Vulnerability Intelligence)
Further complicating the risk is the association of CVE-2024-30051 with QakBot, a sophisticated and continuously evolving malware threat.
What is the QakBot (QBot) Malware?
Originally designed as a credential stealer, QakBot has expanded its capabilities to function as a potent backdoor access tool for deploying secondary payloads. The malware’s longevity and evolution prove its persistence.
It was notably prevalent throughout 2023 and continues to be a significant threat in 2024, with new variants employing deceptive tactics, such as fake Adobe installer popups, to trick users into executing the malware.
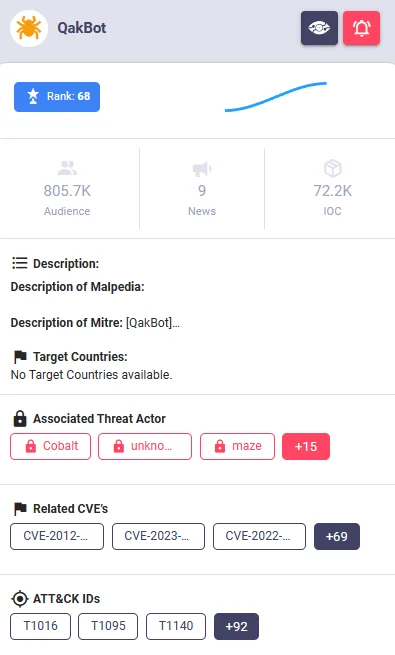
QakBot search results in SOCRadar’s Threat Actor Intelligence page, Malware tab
CISA Cautions Organizations to Patch Microsoft Zero-Day Vulnerabilities
Both Microsoft zero-day vulnerabilities, CVE-2024-30051 and CVE-2024-30040, have been added to the Known Exploited Vulnerabilities (KEV) Catalog immediately upon disclosure and patch availability.
The Cybersecurity and Infrastructure Security Agency (CISA) mandates federal agencies to apply the patches by June 4, 2024
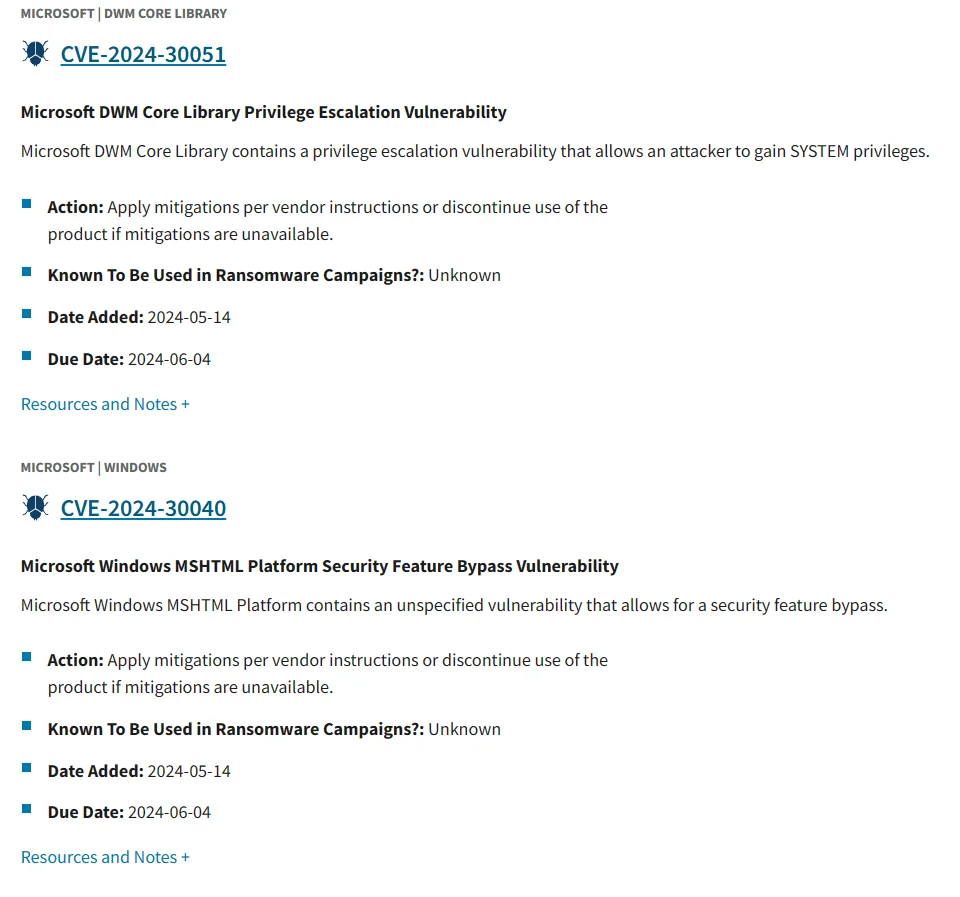
The KEV Catalog includes the most recently disclosed Microsoft zero-day vulnerabilities (CISA)
What is CVE-2024-30044? Details of the Critical Microsoft SharePoint Vulnerability
Among the vulnerabilities addressed in Microsoft’s May 2024 Patch Tuesday, CVE-2024-30044 is the only instance tagged as critical. Classified with a CVSS score of 8.8, this Remote Code Execution (RCE) vulnerability affects Microsoft SharePoint Server and requires immediate attention due to the severity of the threat it presents.
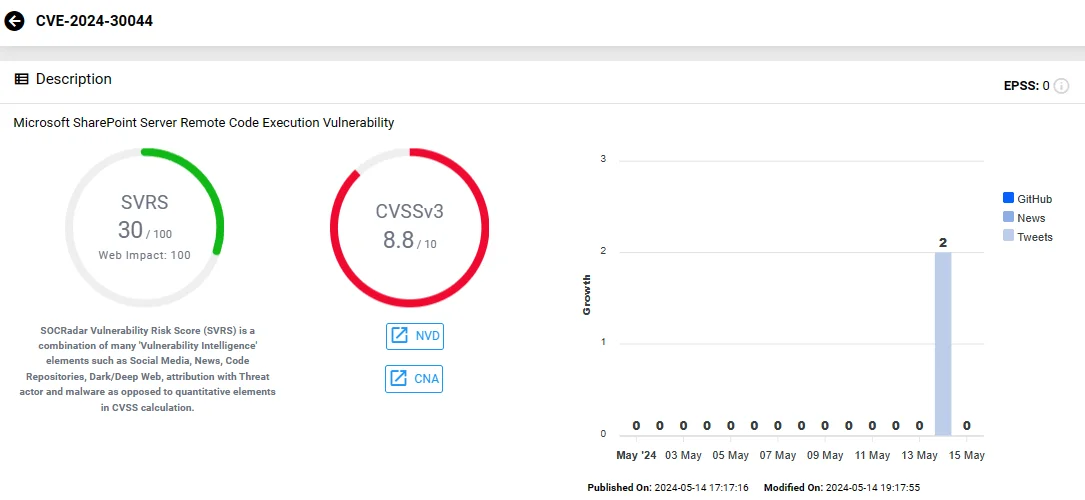
Vulnerability card of CVE-2024-30044 (SOCRadar Vulnerability Intelligence)
The exploitation process of CVE-2024-30044 involves a two-step attack vector.
Initially, an attacker must have authenticated access to the vulnerable SharePoint Server with ‘Site Owner’ permissions. It is a relatively high level of access, which implies that the attacker might already have substantial control or insider access. Then;
- Step 1: The attacker has to upload a specially crafted file to the SharePoint Server. This malicious file would be structured to set the stage for the second phase of the attack.
- Step 2: With the malicious file in place, the attacker then has to send specially crafted API requests to the SharePoint Server. These requests can trigger the deserialization of the file’s parameters.
Upon successful exploitation, the attacker could execute arbitrary code in the context of the SharePoint Server.
Which Vulnerabilities Are ‘More Likely’ to Be Exploited?
Like previous updates, the May 2024 Patch Tuesday updates also include several vulnerabilities labeled as ‘more likely to be exploited.’ Since there are no workarounds available for these vulnerabilities, it is important to apply the official patches promptly to reduce the risk of exploitation.
The high-risk vulnerabilities notably include the critical SharePoint vulnerability, CVE-2024-30044, along with the following list of vulnerabilities:
- CVE-2024-29996 (CVSS: 7.8) – Windows Common Log File System Driver
- CVE-2024-30025 (CVSS: 7.8) – Windows Common Log File System Driver
- CVE-2024-30032 (CVSS: 7.8) – Windows DWM Core Library
- CVE-2024-30035 (CVSS: 7.8) – Windows DWM Core Library
- CVE-2024-30038 (CVSS: 7.8) – Windows Win32K – ICOMP
- CVE-2024-30049 (CVSS: 7.8) – Windows Win32K – ICOMP
- CVE-2024-30037 (CVSS: 7.5) – Windows Common Log File System Driver
- CVE-2024-30034 (CVSS: 5.5) – Windows Cloud Files Mini Filter Driver
- CVE-2024-30050 (CVSS: 5.4) – Windows Mark of the Web (MOTW)
Failing to address these vulnerabilities can leave systems open to attacks that could compromise sensitive data, disrupt operations, and inflict substantial reputational and financial damage.
Adhering to recommended updates and monitoring security advisories are key steps for organizations looking to maintain a strong cybersecurity posture. Microsoft’s detailed Release Notes for the May 2024 Patch Tuesday can provide further insights and guidance on these updates.
SOCRadar XTI for Vulnerability Management
Every year, thousands of new vulnerabilities emerge, expanding the arsenal of threat actors in their pursuit of cyber intrusions. Keeping up with these threats and maintaining your organization’s security posture is becoming increasingly significant to evade exploitation risks.
To help organizations stay ahead and secure their digital assets, SOCRadar XTI offers a suite of tools, including the Attack Surface Management (ASM) and Vulnerability Intelligence features. These services are designed to enhance an organization’s ability to detect, assess, and mitigate vulnerabilities effectively and provide essential support in the ongoing battle against cyber threat actors.
Utilize SOCRadar’s Attack Surface Management (ASM) module to receive timely alerts about threats to your organizational assets; stay ahead of security vulnerabilities and exploitation.
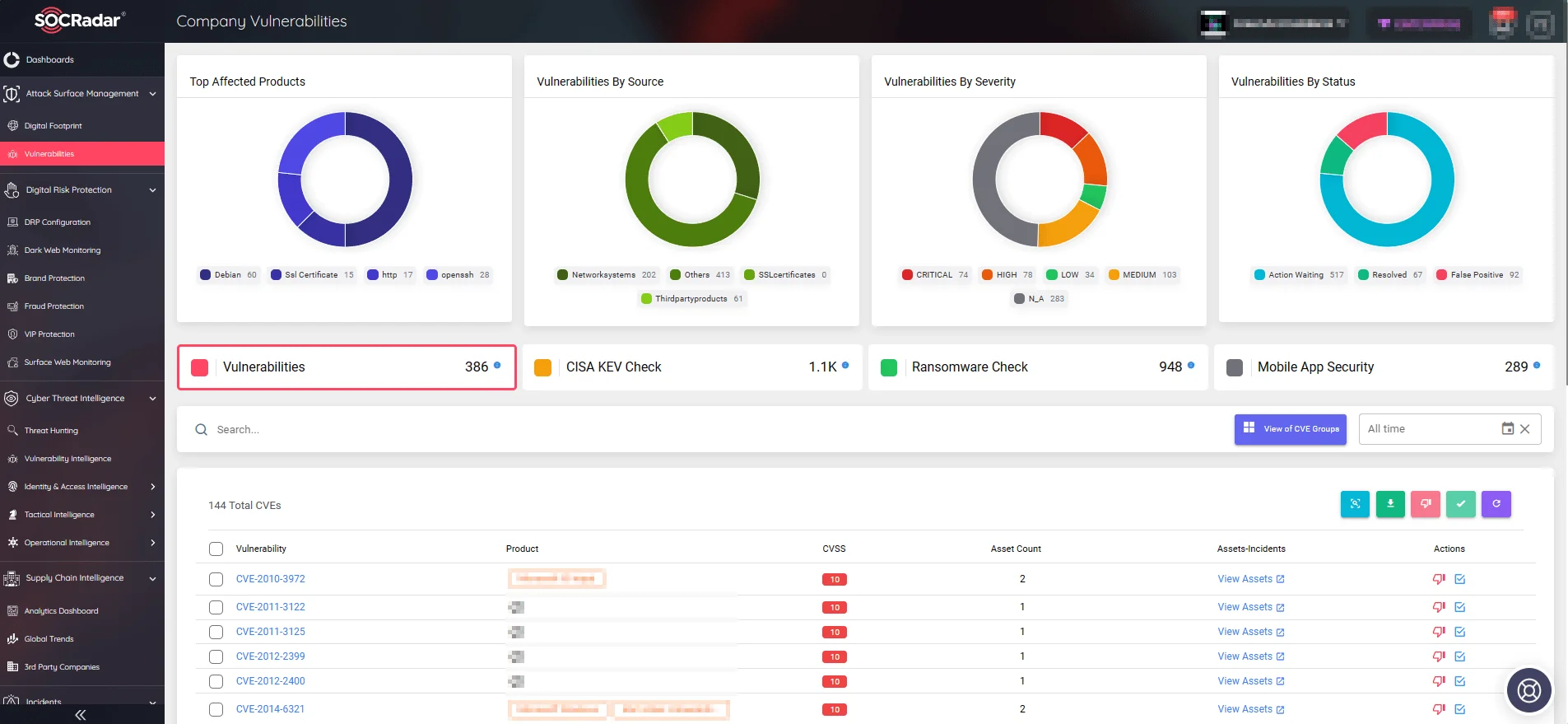
View Company Vulnerabilities and take quick actions through the ASM module (SOCRadar)
With the Vulnerability Intelligence feature, you can search for vulnerabilities, view detailed information about them, and track related activities such as exploitation and hacker trends.
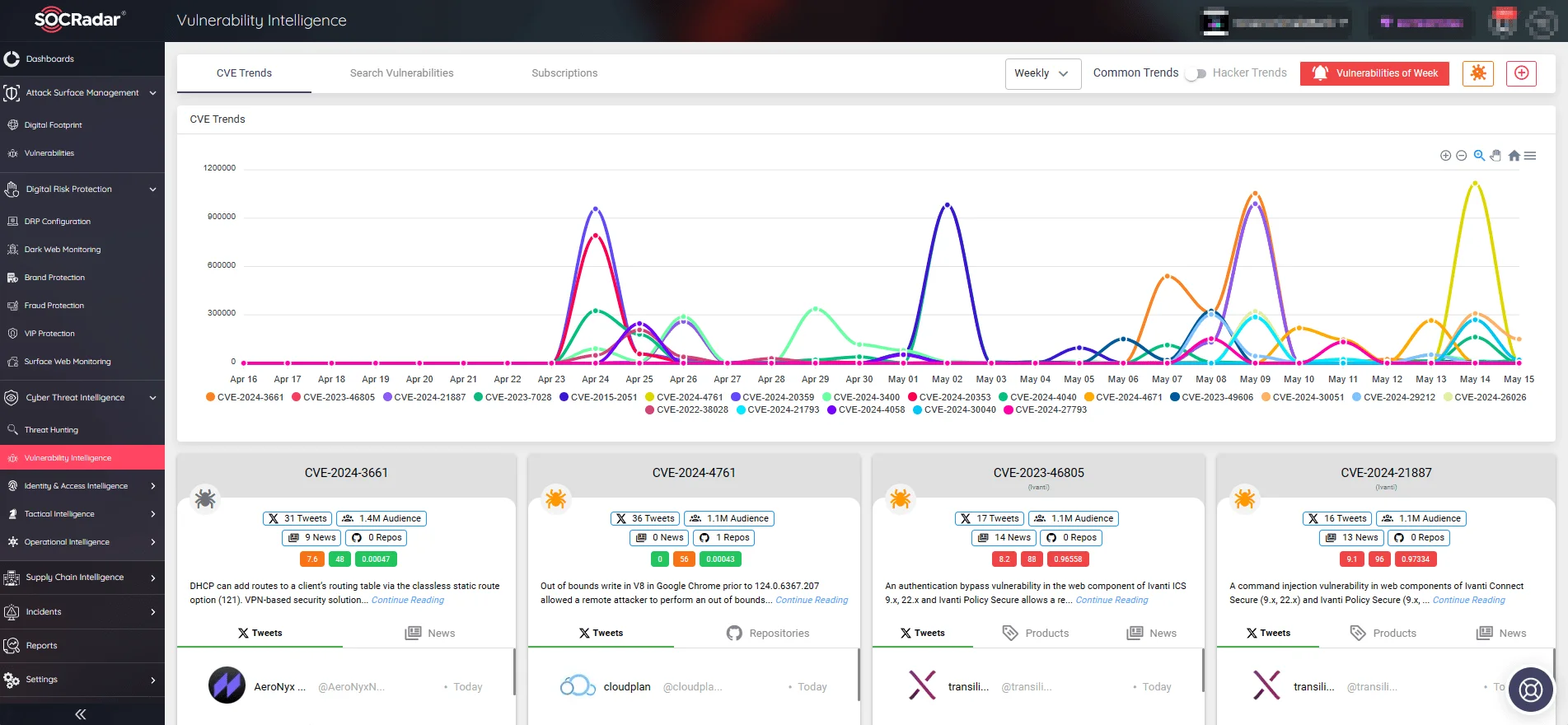
Track emerging vulnerabilities and hacker trends via Vulnerability Intelligence (SOCRadar)
With the Free Edition, you can check out the SOCRadar XTI platform’s vulnerability management features:




































