
Microsoft Patches Power Pages Zero-Day (CVE-2025-24989) & Recent PAN-OS Flaw (CVE-2025-0111) Joins CISA KEV
Two major security flaws pose a serious exploitation risk for organizations using Microsoft Power Pages and Palo Alto Networks PAN-OS firewalls.
Microsoft has addressed a high-severity issue in Power Pages, CVE-2025-24989, that allows unauthorized users to bypass registration controls and elevate privileges. Meanwhile, CISA has added CVE-2025-0111, a file read vulnerability in PAN-OS, to its Known Exploited Vulnerabilities (KEV) Catalog, highlighting active exploitation and urging immediate remediation.
To mitigate the risks posed by the reported exploitation attempts, organizations must immediately patch these vulnerabilities, restrict access to critical systems, and keep an eye out for any suspicious activity.
Microsoft Zero-Day in Power Pages (CVE-2025-24989) Fixed
Microsoft has addressed a high-severity vulnerability, CVE-2025-24989 (CVSS 8.2), in Power Pages, a SaaS-based web development platform.
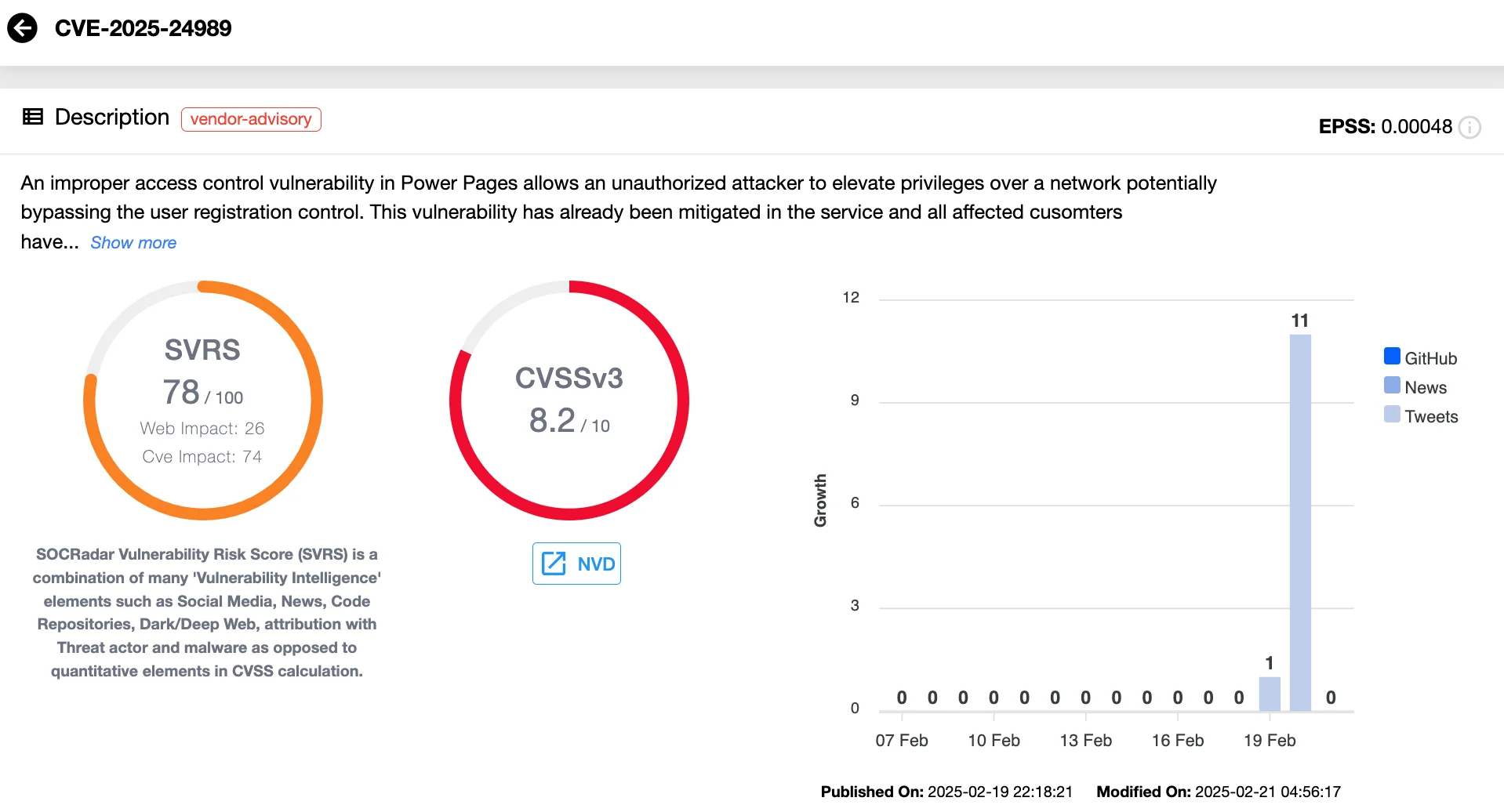
CVE-2025-24989 (SOCRadar Vulnerability Intelligence)
This flaw stems from improper access controls, allowing attackers to elevate privileges and bypass user registration controls, potentially leading to unauthorized access to sensitive data.
Microsoft has already applied fixes at the service level and has privately notified affected customers. Still, admins should review activity logs, check for unauthorized privilege escalations, and enforce Multi-Factor Authentication (MFA) for enhanced security. For more information, refer to Microsoft’s advisory.
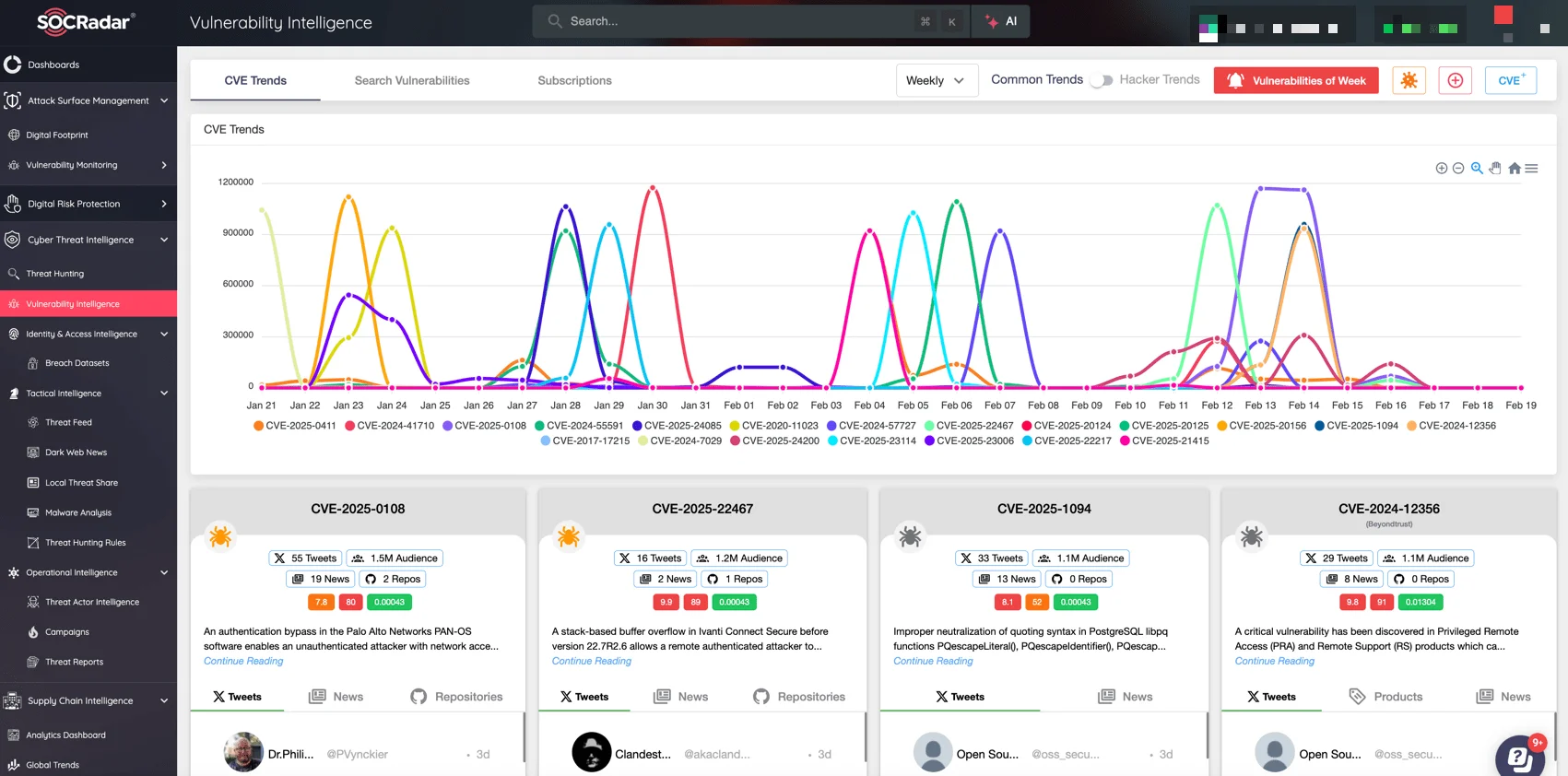
By integrating SOCRadar’s capabilities, security teams can ensure that patches are deployed quickly and exposure to cybercriminal activity is minimized.
With vulnerabilities like those in PAN-OS and Power Pages emerging regularly, organizations need a proactive approach to risk management. SOCRadar’s Vulnerability Intelligence, part of its Cyber Threat Intelligence module, helps security teams track new vulnerabilities, assess risk levels, and receive actionable insights for prioritizing remediation.
PAN-OS File Read Vulnerability Added to CISA KEV Catalog
While the newly patched Microsoft zero-day vulnerability draws significant attention, Palo Alto Networks’ CVE-2025-0111 (CVSS 6.5), a file read vulnerability in PAN-OS, has been added to the CISA Known Exploited Vulnerabilities (KEV) Catalog, emphasizing another active exploitation risk. Organizations using PAN-OS firewalls should address this issue immediately, as CISA has set a remediation due date of March 13, 2025.
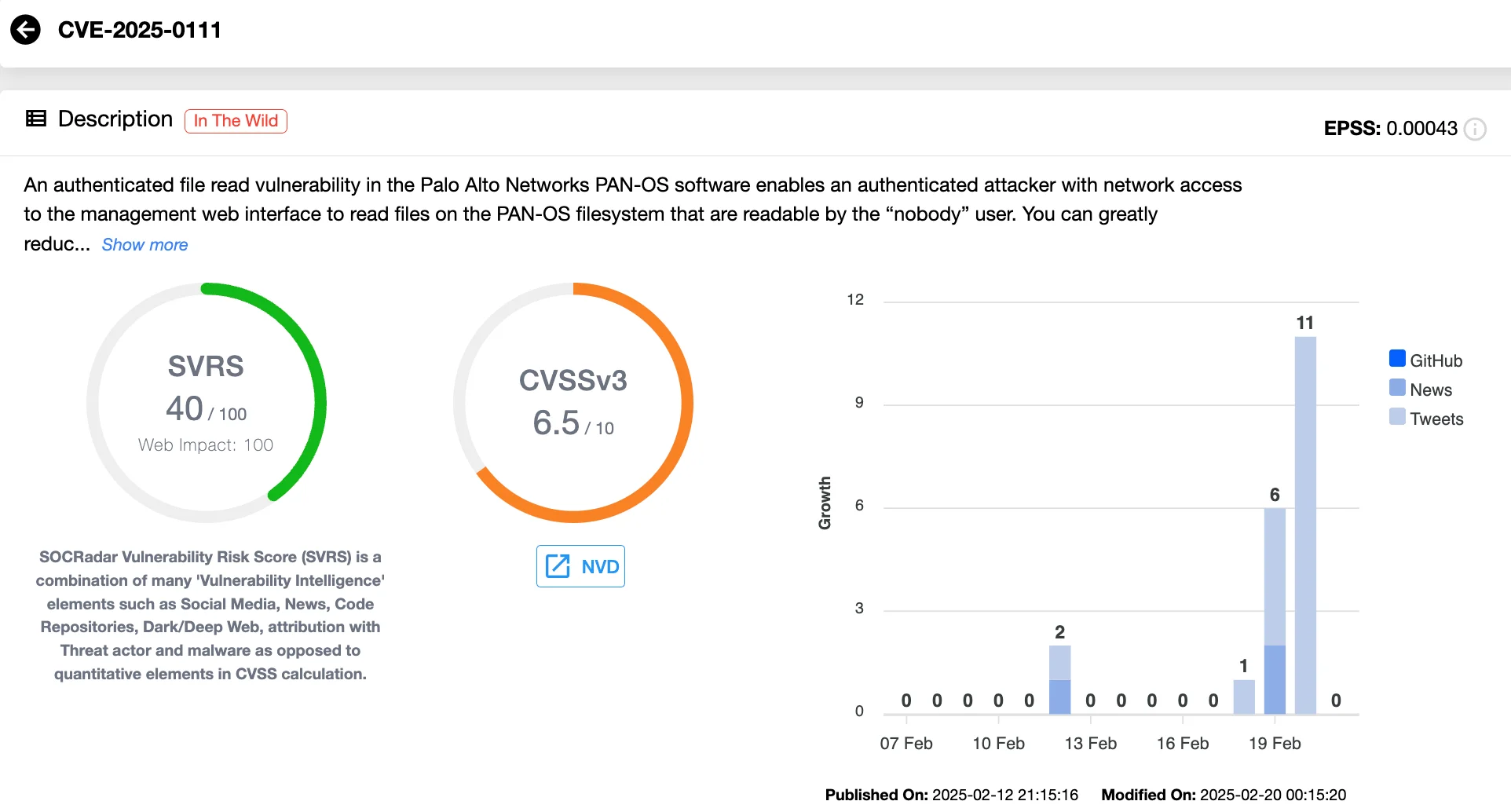
CVE-2025-0111 (SOCRadar Vulnerability Intelligence)
In addition to this, CVE-2025-0108 (CVSS 8.8) remains a significant concern. This authentication bypass flaw allows unauthenticated attackers to exploit the PAN-OS management web interface, invoking PHP scripts that could compromise system integrity and confidentiality. Palo Alto Networks has observed attackers chaining CVE-2025-0108 with other vulnerabilities, including CVE-2024-9474 and CVE-2025-0111, to target unpatched systems.
Organizations should promptly apply updated patches, as Palo Alto Networks has recently expanded fix availability for multiple PAN-OS versions. Reviewing firewall configurations, restricting management interface access, and monitoring for unauthorized activity are critical steps in mitigating these threats.
For full patching details and official recommendations, refer to Palo Alto Networks’ advisories:
Strengthen Your Security with SOCRadar’s Attack Surface Management
The discovery and active exploitation of CVE-2025-0108 in PAN-OS and CVE-2025-24989 in Microsoft Power Pages reinforce the urgency of patching vulnerabilities quickly and implementing access restrictions.
To effectively manage evolving cyber threats, organizations need continuous visibility into their external-facing assets. SOCRadar’s Attack Surface Management (ASM) module provides real-time monitoring of digital assets, detecting misconfigurations, cloud exposures, and vulnerabilities before they can be exploited.
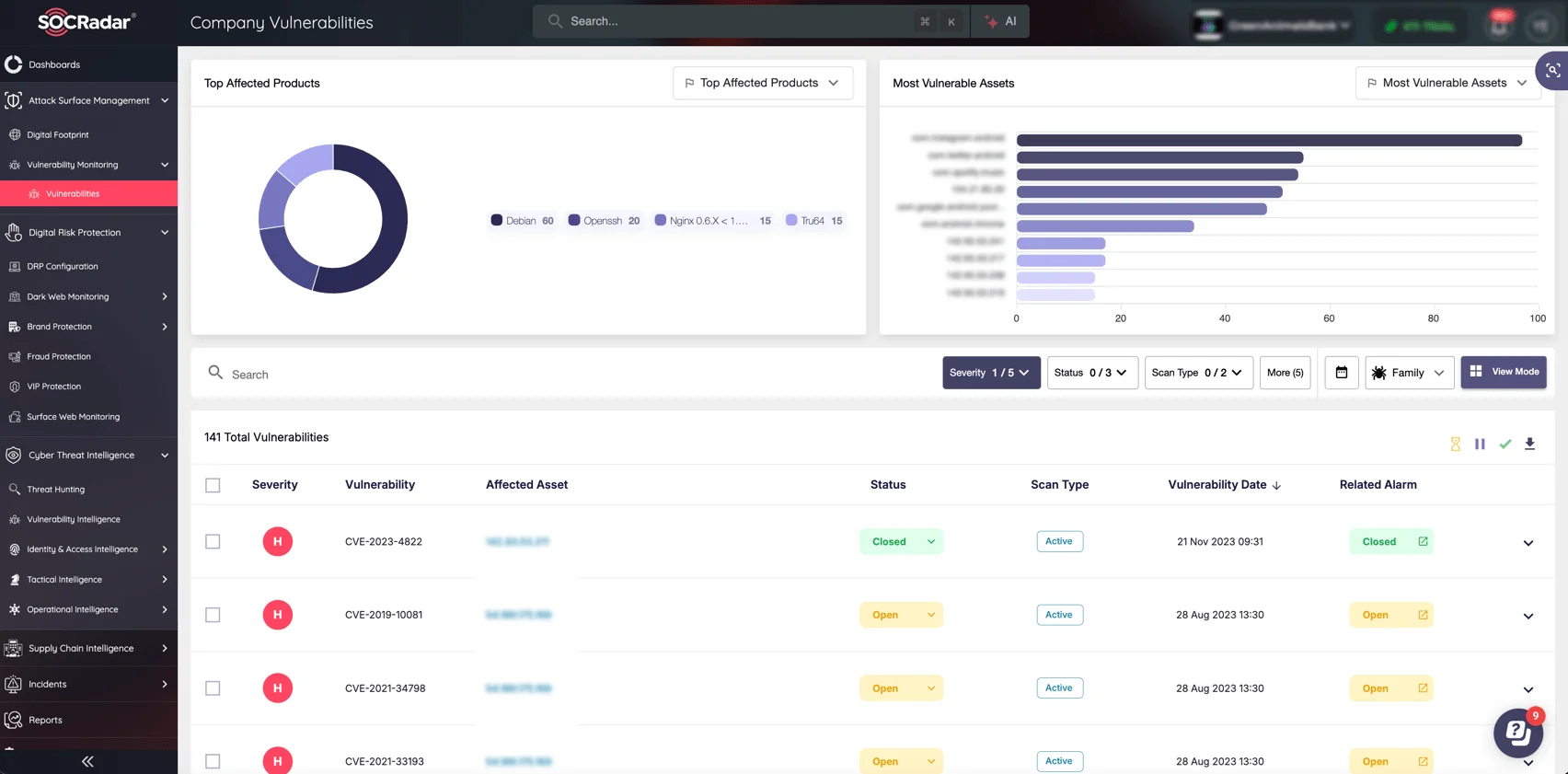
By leveraging SOCRadar’s ASM module, your business can minimize its attack surface, strengthen security posture, and prevent exploitation before it happens.
With automated asset discovery, risk classification, and timely alerts, SOCRadar ASM enables security teams to stay ahead of potential attack vectors. Its integration with threat intelligence ensures that organizations remain informed about emerging vulnerabilities like CVE-2025-0108 and CVE-2025-24989, allowing them to take proactive security measures.




































