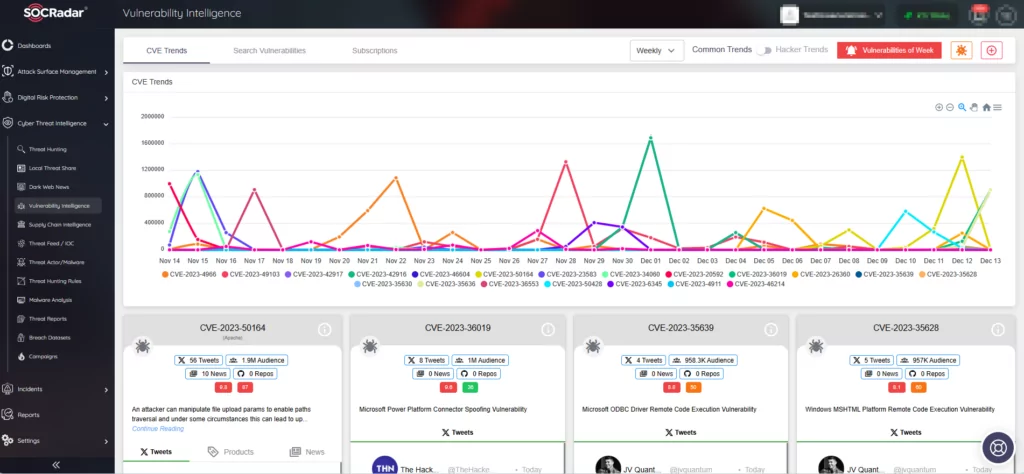
Microsoft’s December 2023 Patch Tuesday Tackles 36 Vulnerabilities, 3 Critical, and a Non-Microsoft Zero-Day
Microsoft has released its December 2023 Patch Tuesday, addressing a total of 36 security vulnerabilities. Among these, three were classified with critical severity in Microsoft advisories.
In addition to resolving the 36 Microsoft vulnerabilities, the update also includes six non-Microsoft CVEs. While five of these impact Microsoft Edge, there is also a zero-day vulnerability affecting various AMD processors.
The December 2023 Patch Tuesday addresses the following vulnerability types:
- 11 Elevation of Privilege (EoP) Vulnerabilities
- 8 Remote Code Execution (RCE) Vulnerabilities
- 4 Spoofing Vulnerabilities
- 7 Information Disclosure Vulnerabilities
- 5 Denial of Service (DoS) Vulnerabilities
- 1 Cross-Site Scripting (XSS) Vulnerability
It is important to note that, in comparison to prior months, there are noticeably fewer vulnerabilities in the Microsoft Patch Tuesday update for December 2023.
Critical Vulnerabilities Patched in December 2023 Patch Tuesday
CVE-2023-36019 (CVSS Score: 9.6): This vulnerability is a spoofing issue that impacts the Microsoft Power Platform Connector. An attacker can manipulate a malicious link, application, or file to make it appear as a legitimate one, deceiving the victim to have them interact with it, leading to compromise. While the vulnerability resides in the web server, the execution of malicious scripts occurs in the victim’s browser.
CVE-2023-35630 (CVSS Score: 8.8): This vulnerability in Internet Connection Sharing (ICS) poses a potential risk of Remote Code Execution (RCE). To exploit it, the attacker needs to manipulate the option->length field in a DHCPv6 DHCPV6_MESSAGE_INFORMATION_REQUEST input message. Although the vulnerability is critical, its exploitation is confined to systems within the same network segment as the attacker and cannot extend across multiple networks.
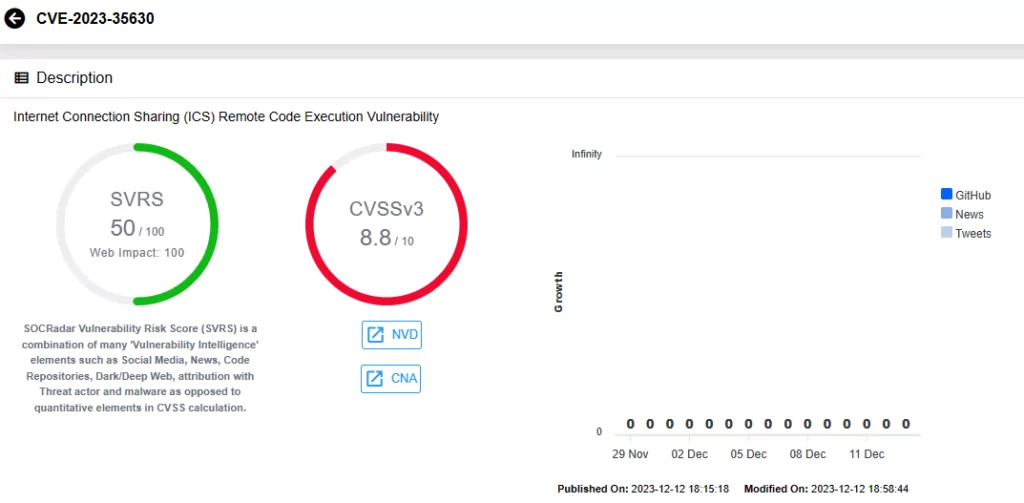
CVE-2023-35641 (CVSS Score: 8.8): It is the second critical RCE vulnerability affecting ICS. An attacker would need to send a maliciously crafted DHCP message to a server that runs the ICS service to exploit it. This attack is limited to systems connected to the same network segment as the attacker. Its exploitation is also confined to systems within the same network segment as the attacker.
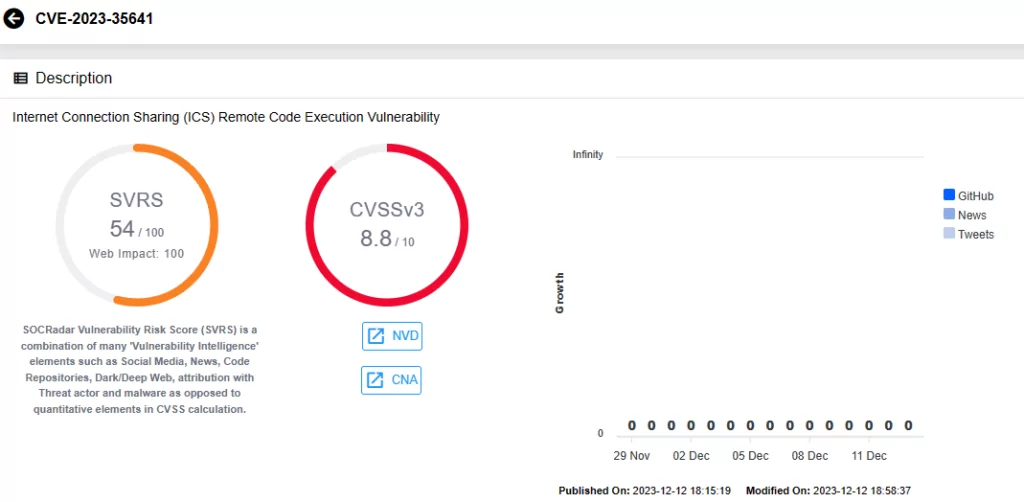
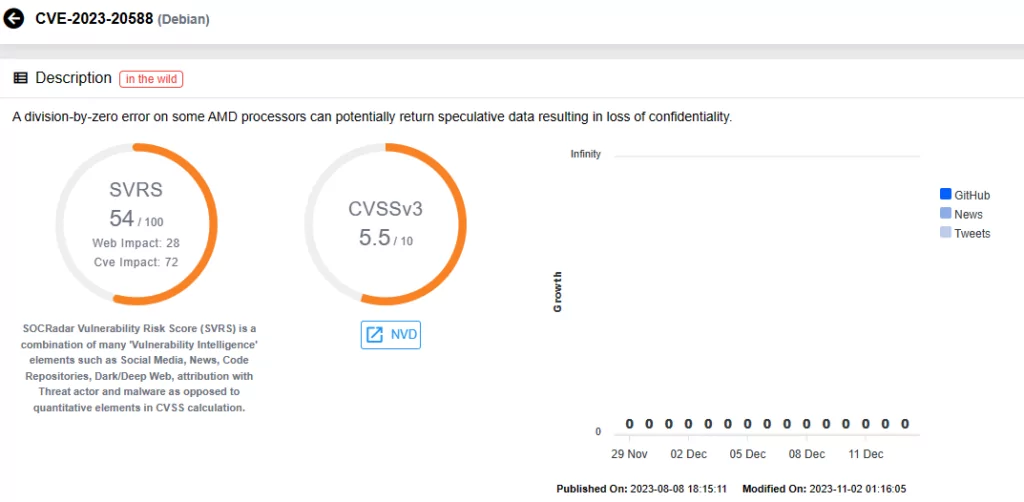
The Zero-Day Vulnerability of December 2023 Patch Tuesday (CVE-2023-20588)
Microsoft has issued a security update addressing the CVE-2023-20588 zero-day vulnerability affecting certain AMD processors.
This vulnerability, republished as a non-Microsoft CVE as part of December 2023 Patch Tuesday, involves a division-by-zero error on select AMD processors, potentially revealing speculative data and leading to a loss of confidentiality. AMD initially published an advisory about this vulnerability in August 2023.
The vulnerability carries a medium CVSS score of 5.5, and AMD assesses its potential impact as low, given that local access is required for exploitation.
CVE-2023-20588 affects the following products:
- AMD EPYC™ 7001 Processors (Datacenter)
- AMD Athlon™ 3000 Series Processors with Radeon™ Graphics (Desktop)
- AMD Ryzen™ 3000 Series Processors with Radeon™ Graphics (Desktop)
- AMD Athlon™ PRO 3000 Series Processors with Radeon™ Vega Graphics (Mobile)
- AMD Ryzen™ PRO 3000 Series Processors with Radeon™ Vega Graphics (Mobile)
A mitigation method is also available for the CVE-2023-20588 vulnerability, if patching is not feasible. AMD notes that developers can mitigate this issue by making sure that no privileged data is employed in division operations before altering privilege boundaries.
Nevertheless, we strongly advise promptly applying the patches to secure your environment and bolster your overall security posture. For more information on the vulnerabilities addressed in the December 2023 Patch Tuesday update, see Microsoft’s Release Note.
Elevate Your Security Posture with SOCRadar
By seamlessly integrating SOCRadar into your security strategy, you can fortify your defense mechanisms and proactively counter emerging threats, protecting system integrity and brand reputation.
The External Attack Surface Management module equips organizations with tools to swiftly identify, assess, and mitigate vulnerabilities. The Company Vulnerabilities page within the EASM module of SOCRadar offers crucial insights into vulnerabilities affecting your assets.
Additionally, the Vulnerability Intelligence feature enhances security measures by consistently monitoring and tracking security vulnerabilities. With the Vulnerability Intelligence feature, you can search for vulnerabilities, access detailed information about them, and monitor associated activities, including hacker trends.