
New Apple Zero-Day in WebKit Received a Fix (CVE-2024-23222)
[Update] January 24, 2024: “Apple WebKit Zero-Day CVE-2024-23222 Enters CISA KEV Catalog”
Apple has issued security updates to address the first 2024 zero-day vulnerability affecting its products. The vulnerability, CVE-2024-23222 (CVSS: 7.5), is defined as a type confusion flaw in WebKit, Apple’s web browser engine.
According to Apple’s security advisory, the vulnerability could allow attackers to execute arbitrary code while the victim device processes maliciously crafted web content.
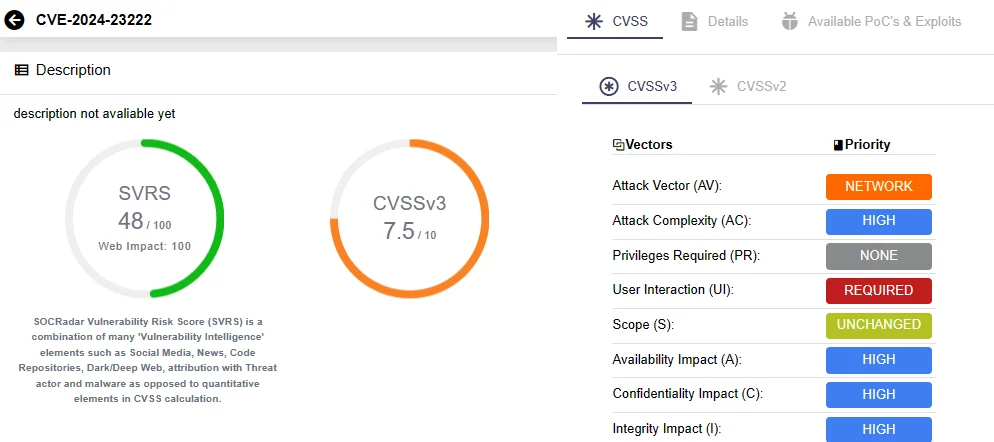
Details of CVE-2024-23222 on SOCRadar Vulnerability Intelligence
As a zero-day vulnerability, CVE-2024-23222 is currently being exploited in the wild; no further information is available as to whether a specific threat actor is targeting this vulnerability.
Vulnerability Intelligence feature of SOCRadar can help you keep track of security vulnerabilities and exploitation trends. It provides actionable insights and context about vulnerabilities, which speeds up the assessment and verification processes for improved cybersecurity measures.
View CVE trends and updates via SOCRadar’s Vulnerability Intelligence
Which Apple Products Are Affected by CVE-20234-23222?
CVE-20234-23222 is known to affect the following Apple products:
- iPhone 8, iPhone 8 Plus, iPhone X, iPad 5th generation, iPad Pro 9.7-inch, and iPad Pro 12.9-inch 1st generation, iPhone XS and later
- iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later
- Macs running macOS Monterey and later
- Apple TV HD and Apple TV 4K (all models)
Apply the Fix for New Apple WebKit Zero-Day Vulnerability, CVE-20234-23222
Apple has addressed the identified type confusion vulnerability by implementing enhanced checks. The fix is included in the updates for iOS 16.7.5 and later, iPadOS 16.7.5 and later, macOS Monterey 12.7.3 and later, and tvOS 17.3 and later.
While the exploitation of this zero-day vulnerability may have been limited to targeted attacks, it is strongly advised that all users immediately install the provided security updates in order to prevent any exploitation attempts.
In a proactive move, Apple has also issued patches for two older zero-days, CVE-2023-42916 and CVE-2023-42917, affecting WebKit. Although these vulnerabilities were addressed in November and backported to older Apple devices in December, Apple has now extended the fixes to other older devices with the iOS 15.8.1 security update.
You can search for other Apple vulnerabilities and access comprehensive details about them through Vulnerability Intelligence. This includes a timeline of events, exploit availability, vulnerabilities’ prevalence assessed by the specialized SVRS score, and the likelihood of exploitation determined by the newly incorporated EPSS scores.
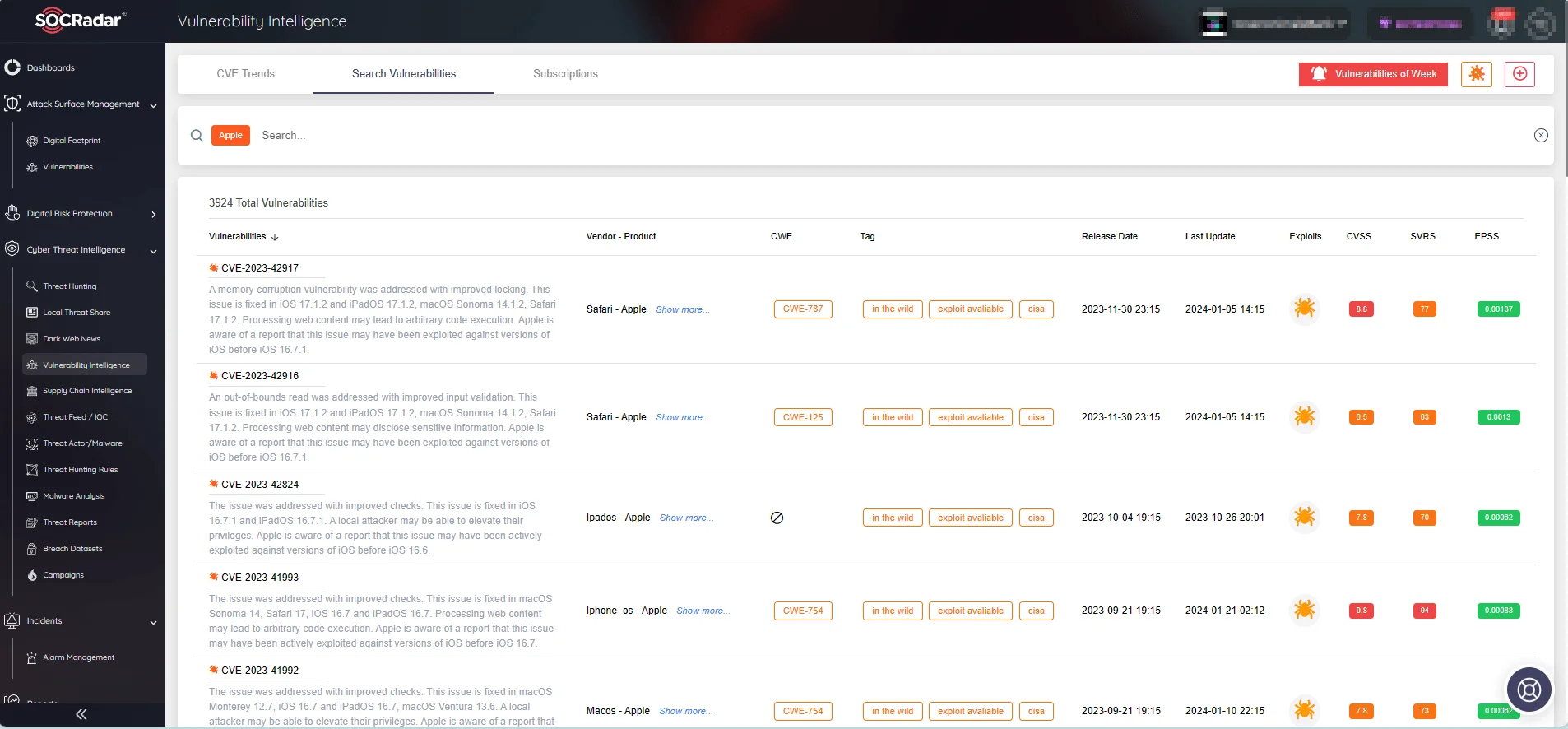
Apple vulnerabilities on SOCRadar Vulnerability Intelligence
Apple WebKit Zero-Day CVE-2024-23222 Enters CISA KEV Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has added the recently discovered Apple WebKit zero-day vulnerability, CVE-2024-23222, to its Known Exploited Vulnerabilities (KEV) Catalog in response to its ongoing exploitation.
Under BOD 22-01, the KEV Catalog is specifically curated to address risks within the Federal Civilian Executive Branch (FCEB) agencies. These agencies are expected to patch the vulnerability by the deadline set for February 13, 2024.
However, the implications extend beyond FCEB agencies, and all organizations are strongly encouraged to prioritize the resolution of vulnerabilities listed in the KEV Catalog. By doing so, organizations can effectively mitigate risks and minimize exposure to potential cyberattacks.




































