Sharpen Penetration Testing with Cyber Threat Intelligence
We hope our readers are proficient with figures. Let’s dive into some statistics. In 2022, security incidents amounted to a staggering $10 billion in costs, with over 850,000 reported cases. Focusing on ransomware, an attack increasingly favored by cyber criminals, we observe a significant upward trend. In 2021, there were 1,706 ransomware incidents. These figures were sourced from ransomware.live, a website our readers might find informative. Looking at the current state of affairs, this year’s incident reports are surpassing those of the last two years. Hence, the pertinent question now is not if we will face an attack, but rather when it will occur.
Cyber Threat Intelligence (CTI) is a relatively new field, largely drawing inspiration from military domains. Apologize for painting a rather bleak picture at the beginning of writing, but the good news, CTI exists to assist us on this challenging journey. If the question is no longer whether we will be attacked, but when, therefore, it is crucial to be proactive and anticipate future threats. CTI, in a nutshell, aggregates information from various sources such as public records, system and device logs, honeypots, and, notably, from more covert channels like hacker forums, dark web sites, and Telegram channels. However, CTI is not just about gathering a plethora of data; it is about refining and presenting it in a way that is both timely and actionable for busy cybersecurity teams who do not have time to sift through a mountain of information.
Let’s apply a fundamental economic principle to the realm of cybersecurity. A core principle of economics states that while human demands are infinite, resources are finite. This concept is equally applicable in cybersecurity. Although the realm of cyber threats and risks is boundless, our resources to counter them are not. Therefore, it is essential to understand, assess, and prioritize these risks. It is not just about recognizing the presence of risks; the key is to determine their relevance to our organization. Cyber Threat Intelligence (CTI) acts as a sieve, filtering out and refining information pertinent to our company and assets. From our perspective, this is a crucial aspect. CTI provides a clear view of potential threats relevant to our organization and keeps us informed about the evolution of both existing and new threats.

Sharpen Penetration Testing with Cyber Threat Intelligence
But, what about penetration testing? Stop glorifying CTI, come to the question of why you are discussing CTI and pentesting in the same article. Regarding penetration testing, its objective is to identify potential vulnerabilities before they are exploited by hackers or malicious actors. Organizations typically conduct internal penetration tests on a regular basis, or at the very least, engage in annual penetration testing services provided by external firms. Certain regulations mandate regular penetration testing, including but not limited to:
- FDA: The Food and Drug Administration obliges medical device manufacturers to adhere to security risk reduction guidelines and undergo frequent tests to guarantee the safety and efficacy of their devices.
- HIPAA: The Health Insurance Portability and Accountability Act of 1996 demands healthcare providers safeguard medical record privacy and security. It requires both technical and non-technical assessments for data security.
- PCI DSS: The Payment Card Industry Data Security Standard insists that entities dealing with branded credit cards perform vulnerability assessments and penetration tests at least biannually to maintain network security and integrity.
- SOC 2: Service Organization Control 2 certification mandates technology service organizations comply with five standards – security, availability, processing integrity, confidentiality, and privacy. They must undergo external audits, including penetration testing, every six months.
- FINRA: The Financial Industry Regulatory Authority, a non-profit overseeing cybersecurity in financial organizations like securities firms, expects the implementation of robust penetration testing programs, often involving third-party agencies.
During a penetration test, the task extends beyond merely identifying vulnerabilities. It is about demonstrating their exploitability and confirming their authenticity. Additionally, it involves assigning a priority level to each finding, determining what needs to be remediated and in what timeframe. The AppScan team leverages their understanding of cyber threats to enhance the toolkit available to penetration testers. As for whether a penetration tester requires an in-depth knowledge of these threats, the answer is a definitive yes. Being aware of the existing cyber threats is vital for a penetration tester to be highly effective. However, what adds to the complexity of their role is this very need for comprehensive threat knowledge.
The Synergy Between CTI and Penetration Testing: Enhancing Efficiency and Effectiveness
How does current threat intelligence empower penetration testers to maximize their efficiency and the utility of their tools?
A penetration test typically unfolds in three phases, beginning with the pre-test stage, which involves establishing the scope and objectives. During this initial phase, CTI (Cyber Threat Intelligence) can be invaluable, providing data-driven insights from real-world threats to inform decision-making and focus testing efforts more effectively.
In the actual testing phase of penetration testing, the team can employ tactics, techniques, and procedures used by recent threat groups or Advanced Persistent Threats (APTs) to conduct tests that closely mimic real-world scenarios. Post-test, the penetration testing team can leverage Cyber Threat Intelligence (CTI) to highlight recent and relevant risks by using CTI as a perfect filter. This assists the development team in prioritizing detected vulnerabilities by providing context on threat groups. For instance, the team can assess whether a detected vulnerability is common in attack groups’ arsenals, if there is a publicly available exploit kit, or any mentions of the vulnerability in dark web hacker forums or Telegram channels. This approach ensures a more comprehensive and informed response to potential security threats.
To further light up the process, let’s incorporate application security tools into the equation. These tools serve as the essential part of penetration testing, enhancing the process far beyond mere automation. With their incorporation and customization of the latest attack techniques, these tools refine and bolster the capabilities of penetration testing teams. This integration not only streamlines the testing process but also ensures that the team is equipped with the most advanced and effective methods for identifying vulnerabilities.
Consider this: an average Dynamic Application Security Testing (DAST) tool may contain hundreds of security checks. But what if you’re faced with the urgent need to scan all your websites within an hour for a newly discovered vulnerability? Here’s a more tangible example: vulnerabilities in Apache Struts, specifically OGNL injections, a type of template injection vulnerability. Suppose the Cybersecurity and Infrastructure Security Agency (CISA) releases a notification about a new vulnerability. In such a scenario, you have only an hour to determine whether your systems are affected. Instead of sifting through over a hundred security checks, it is more efficient to focus solely on this specific vulnerability, giving it precedence over others. This approach was also crucial during the Log4j Injection vulnerabilities and the MOVEit cases, where ransomware attackers exploited these vulnerabilities extensively. The ability to customize AppSec tools to concentrate on immediate, significant threats is not just a convenience but a necessity in such situations. CTI is here with its wisdom to guide you through.
Understanding the preferences of threat actors allows for better prioritization of vulnerabilities. If you’re aware of a specific vulnerability being exploited frequently by attackers, especially those targeting your industry or your company specifically, you might choose to prioritize this over other issues rather than trying to find reflected XSSes or missing HTTP security headers (though these are important too, it’s a matter of prioritization). In short, Cyber Threat Intelligence (CTI) aids in identifying the critical areas of focus. It guides you on which vulnerabilities to scrutinize within your systems. Short of the story, you can tailor your Dynamic Application Security Testing (DAST) tool to align with this vital intelligence, sharpening your defense mechanisms more effectively against the most pertinent threats.
Penetration testing can generally be categorized into two main types: proactive and reactive testing. Proactive testing involves scrutinizing vulnerabilities and new releases of internal software to prevent potential breaches. Reactive testing, on the other hand, involves scanning (indeed attacking too) the infrastructure for both new and known vulnerabilities.
Having knowledge about actual vulnerabilities exploited in the wild cannot be overstated. A fundamental question arises: how crucial is it to acquire this information promptly? For a penetration tester, understanding the nature of current attacks is essential to perform their role effectively. They need to determine the urgency of fixing a vulnerability, identify the affected assets, and implement solutions swiftly.
Attack Surface Management and Its Role in Cybersecurity
Curious readers who have been holding their breath up to this point, you can take a breath conveniently now, here is another point.
While individuals can stay informed about new threats through blogs and similar sources, this approach doesn’t match the depth of a comprehensive threat intelligence product. A critical question arises: how does a research team, with the aid of tools, sift through threat intelligence to find what is relevant to a specific organization? Here we can see that Cyber Threat Intelligence (CTI) necessitates a holistic strategy to accurately filter threats. This requires the support of complementary tools. This is where a comprehensive approach, or what is known as Extended Cyber Threat Intelligence, becomes crucial.
Converting data to an intelligence product through cyber threat intelligence should not be just about providing information, it is rather elaborating, contextualizing, and sharing the information in a timely manner and actionable format. As an important part of the Extended Threat Intelligence of SOCRadar, the Attack Surface Management module involves discovering your publicly accessible assets and alerting you about their existence. This means identifying public repositories, exposed dashboards, and similar assets.
This approach is particularly vital when a new vulnerability emerges. When it occurs, it is essential to know whether this vulnerability is relevant to your digital assets. If a vulnerable product or component is identified within your asset list, you can then take appropriate actions.

Attack Surface Management, Dall-E
To underscore the importance of this approach, consider the wisdom of Sun Tzu, the ancient Chinese philosopher and author of “The Art of War.” He said that to triumph in battle, one must know both themselves and their enemy. This principle is fundamental to success in warfare. Similarly, in the realm of cybersecurity, CTI aids in understanding adversaries – their tactics, techniques, and procedures (TTPs). But what about self-awareness? How well do you know your own organization?
This exactly what Attack Surface Management does. They assist in cataloging your assets, identifying vulnerabilities, assessing their exposure, and detecting any misconfigurations. This comprehensive self-assessment is critical in strengthening your organization’s defenses and preparing for potential cybersecurity battles.
A Chain is as Strong as Its Weakest Link: Supply Chain and Vulnerabilities
Once you have identified your assets, the next step is to understand their complexities. Typical assets, particularly software or applications, are built on multiple dependencies provided by various vendors. It is well acknowledged that a chain is only as strong as its weakest link. This raises important questions: How robust are your vendors, and business partners? Are they susceptible to vulnerabilities? If a key vendor experiences a vulnerability, it is likely that this issue will impact you soon after. Are you prepared for this possibility? Have you taken all the necessary precautions and steps to safeguard against such vulnerabilities?
Supply Chain Intelligence, Dall-E
This aspect of cybersecurity underscores the importance of not just knowing your own system’s strengths and weaknesses, but also those of your vendors. Keeping abreast of their security posture is crucial in maintaining the integrity of your supply chain and, by extension, your own cybersecurity defenses.
SOCRadar’s Supply Chain Intelligence plays a crucial role in cybersecurity. It is imperative to analyze your dependencies and the entirety of your supply chain. The Cyber Threat Intelligence (CTI) tool you utilize should be capable of alerting you whenever there is a vulnerability in any of your vendors, who form a part of your supply chain. This allows you to subscribe to updates from specific vendors, keeping you informed about emerging issues in their systems.
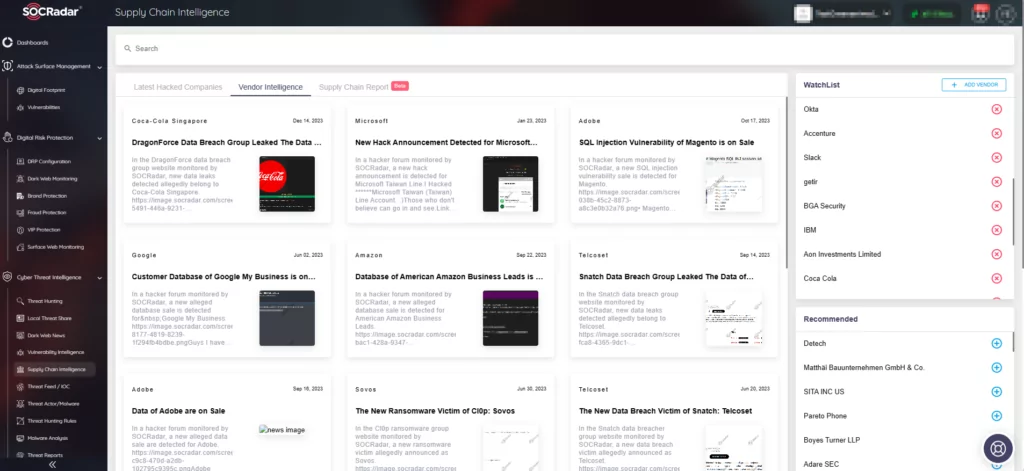
Add vendors to the WatchList on SOCRadar’s Supply Chain Intelligence
Moving on to Vulnerability Intelligence, which is an integral part of a holistic cybersecurity approach, It is essential to be aware of new vulnerabilities as they appear, understand their prevalence, and how to prioritize them effectively. According to a research from Ponemon Institute and Rezilion, despite an average backlog of over 100,000 vulnerabilities, only 15% can be realistically exploited. This statistic is significant and deserves attention. Merely 15% of the vulnerabilities cataloged in the backlog experience exploitation, leaving the remaining 85% to generate attention without being actively exploited. What does this imply? It offers valuable insight for prioritizing vulnerabilities. This additional knowledge aids in the prioritization of newly detected issues, allowing for more informed and strategic decision-making in managing cybersecurity risks.
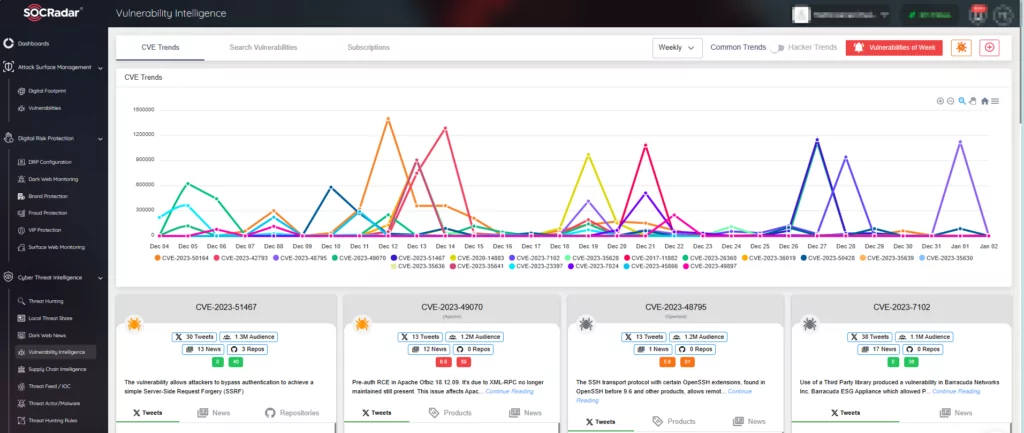
SOCRadar’s Vulnerability Intelligence
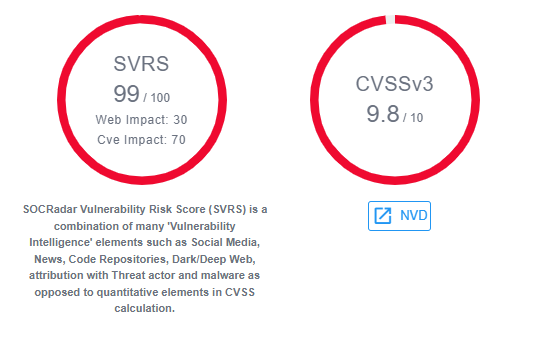
In SOCRadar, we provide a unique scoring system, the SOCRadar Vulnerability Risk Score (SVRS). This system evaluates the level of discussion surrounding a vulnerability across various platforms like social media, hacker forums, and Telegram channels, and much more. Additionally, it assesses whether there are any publicly available exploits for the vulnerability. By considering the broader context and adopting a holistic approach, this system enables users to prioritize vulnerabilities more effectively. The importance of this knowledge is not debatable, especially at the most crucial step of penetration testing where we report outcomes to the clients. The report will guide decision-makers with supported data.
The scope of penetration testing should expand beyond just your organization to include the supply chain. While it might not be commonplace for penetration testers to examine supplier infrastructure directly, due to the need for specific approvals from vendors, there are other ways to address these dependencies. A critical tool in this regard is Software Composition Analysis (SCA), which helps identify the libraries used.
A proficient penetration testing tool should be capable of actively or passively analyzing your application to, at the very least, fingerprint the system’s dependencies. Understanding these dependencies or the broader supply chain is a vital step. The next part involves checking for outdated components, such as an old library, and whether they contain any known issues. This is where a penetration tester’s role becomes crucial, often referred to as vulnerability mapping. Penetration testing is not always about reinventing the wheel; sometimes, it is about identifying an outdated yet critical component that can be exploited to gain unauthorized access. The revelation of such vulnerabilities can lead to a system compromise, underlining the importance of keeping systems updated.
Therefore, security teams must be diligent in maintaining updated systems, and penetration testing tools should include features that aid in this process. Overall, penetration testing operations should not only focus on immediate vulnerabilities but also examine dependencies and components within the applications and systems.
Conclusion: Last, but Not Least
In conclusion, this article has illuminated the critical synergy between Cyber Threat Intelligence (CTI) and penetration testing in fortifying cyber defenses. As we have explored, CTI is not just a collection of data but a refined tool that transforms information into actionable intelligence, guiding cybersecurity professionals in prioritizing and addressing the most relevant threats. The increasing sophistication and frequency of cyber attacks, as exemplified by the rising numbers in ransomware incidents, underline the urgency of adopting a proactive stance in cybersecurity.
The role of penetration testing, enhanced by CTI, is pivotal in this landscape. It goes beyond identifying vulnerabilities to understanding and simulating real-world attack scenarios, thereby enabling organizations to anticipate and thwart potential breaches effectively. This process, enriched with CTI insights, elevates penetration testing from a routine exercise to a strategic endeavor that aligns with the latest threat landscape.
Moreover, we delved into the realms of Attack Surface Management and Supply Chain Intelligence, emphasizing the importance of comprehensive self-assessment and vigilance in supply chain security. These aspects are crucial in understanding and mitigating risks in an interconnected digital ecosystem.
In essence, this article serves as a clarion call for integrating CTI into the core of cybersecurity practices. It’s a strategy that not only heightens the effectiveness of penetration testing but also ensures that organizations are equipped to face the ever-evolving cyber threats with informed, targeted, and timely responses. As cyber threats become more complex and pervasive, the fusion of CTI with penetration testing emerges as a beacon of guidance, empowering cybersecurity professionals to protect their digital fortresses with enhanced precision and foresight.