
New Bank Log Service, TP-Link Zero-Day, Wizz Air Data Leak, and D2C Fraud Scheme
Hacker forums continue to see a high level of cybercriminal activity, and this week, SOCRadar’s Dark Web Team discovered a number of new threats. Key discoveries include a bank login log service offering access to compromised financial accounts, as well as a zero-day RCE exploit targeting TP-Link routers. Meanwhile, a hacker claims to have leaked 5GB of corporate documents from Wizz Air, exposing operational and regulatory records.
Additionally, a new illicit cash-out service has surfaced, allegedly facilitating unauthorized withdrawals from platforms like Square and Chime. These findings underscore the evolving tactics of cybercriminals targeting financial, corporate, and infrastructure systems.
SOCRadar Dark Web News: Key highlights of this week’s detected threat actor activities
Receive a Free Dark Web Report for Your Organization:
New Log Service is Detected for Bank Logins
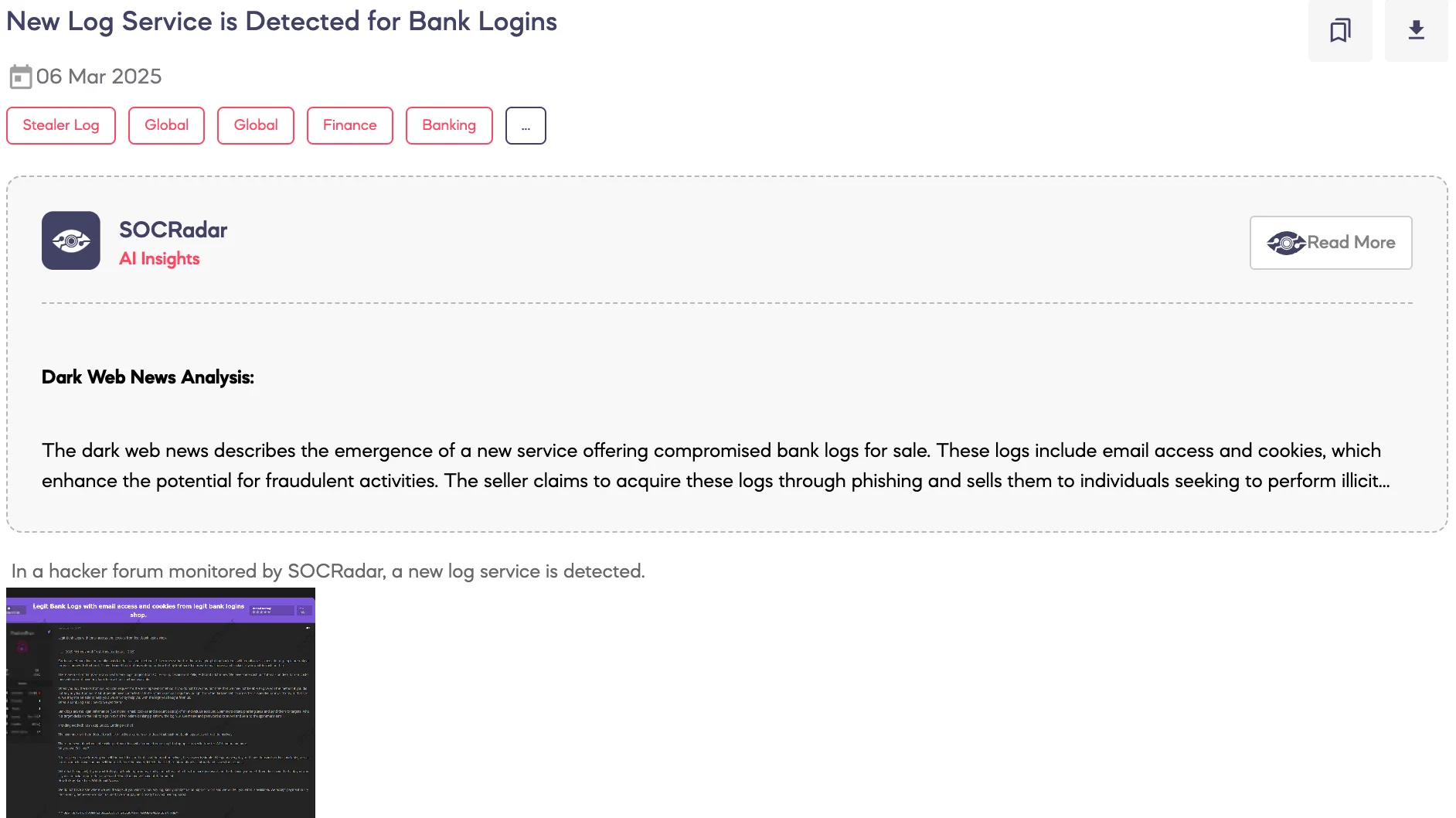
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be offering a new log service for bank account credentials. According to the threat actor’s statements, the service provides access to bank account logins, email access, and session cookies, allegedly obtained through phishing campaigns targeting online banking users.
The post outlines various fraudulent use cases for the compromised credentials, including credit card top-ups, and other unauthorized financial activities. The threat actor claims that the logs are acquired in bulk through spamming techniques and are sold directly via encrypted messaging platforms, with payments accepted exclusively in cryptocurrency.
Additionally, the post includes a list of financial institutions for which the actor claims to have account logs and payment card details, including Barclays, Lloyds Bank, NatWest, HSBC, and Santander UK. The actor also states that pre-orders for specific banks and balances are available if the requested credentials are not immediately in stock.
Alleged 0-Day RCE Exploit is on Sale for TP-Link
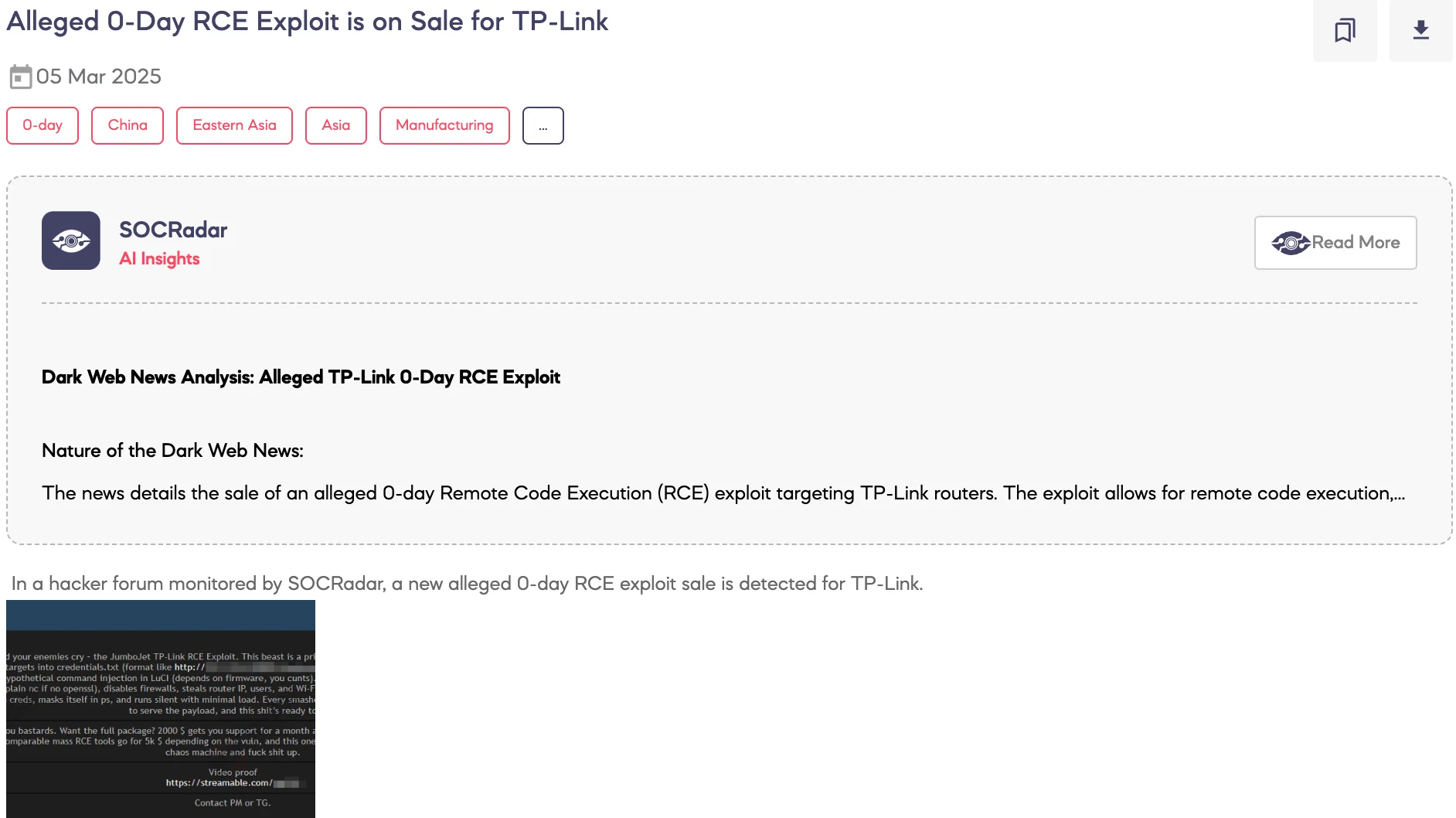
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a zero-day Remote Code Execution (RCE) exploit allegedly targeting TP-Link routers. According to the threat actor’s statements, the exploit enables unauthorized remote access, persistence mechanisms, network propagation, and data exfiltration.
The threat actor claims it can inject RCE via a LuCI vulnerability, establish an AES-256 encrypted backdoor, disable firewall protections, extract router credentials, and scan local networks for further compromise. The base script is offered for $1,000, while a full package with support is priced at $2,000. A video demonstration and contact details via private messaging and Telegram are provided in the post.
Alleged Documents of Wizz Air are Leaked
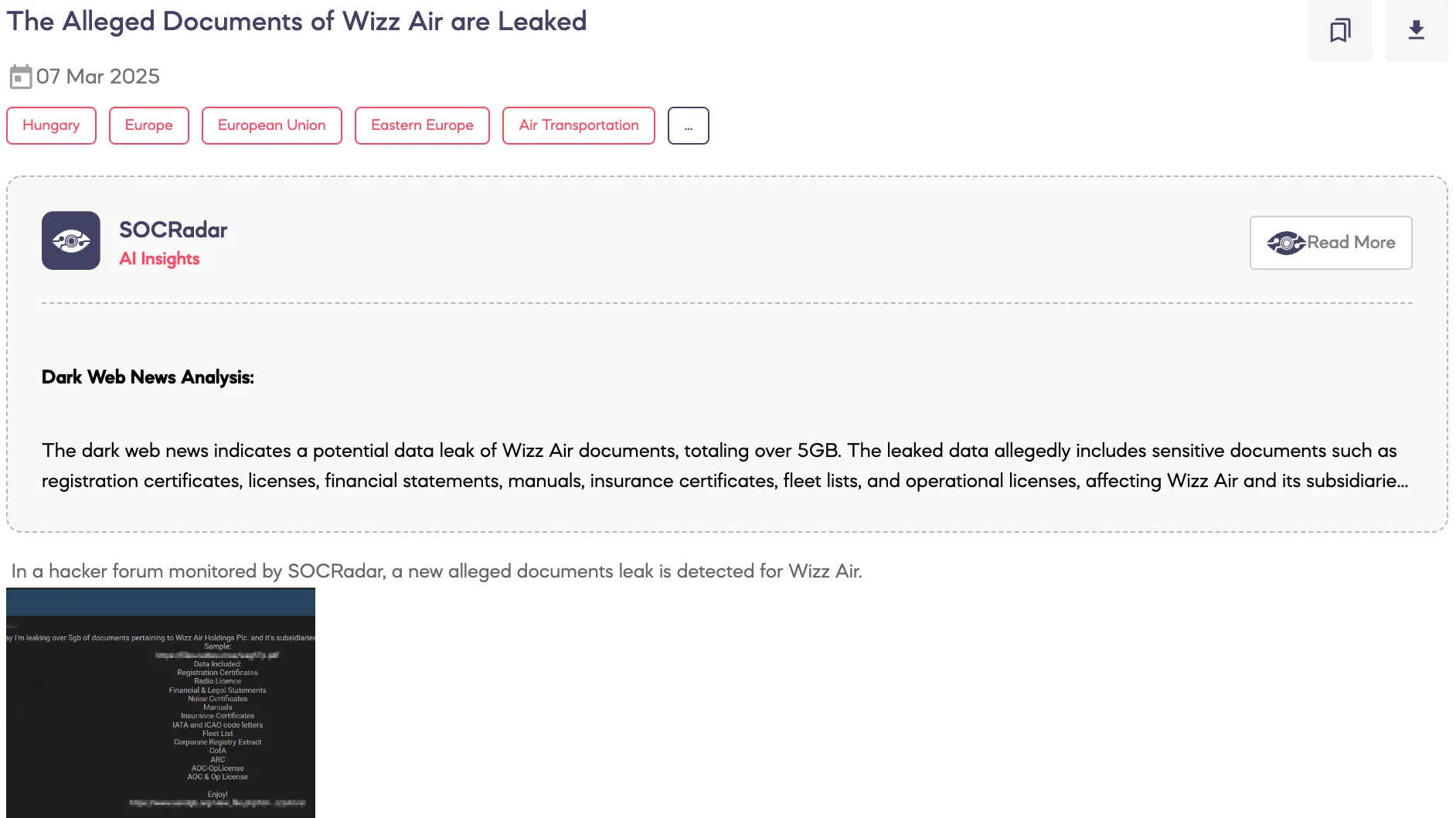
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked over 5GB of documents allegedly belonging to Wizz Air Holdings Plc. and its subsidiaries, including Wizz Air Hungary, Wizz Air Malta, Wizz Air Abu Dhabi, and Wizz Air UK. According to the threat actor’s statements, the dataset includes corporate, regulatory, and operational documents such as financial records, certificates, fleet information, and operational licenses. A sample of the alleged documents has been shared, though the method of data acquisition has not been disclosed.
D2C Cash Out Service is Detected
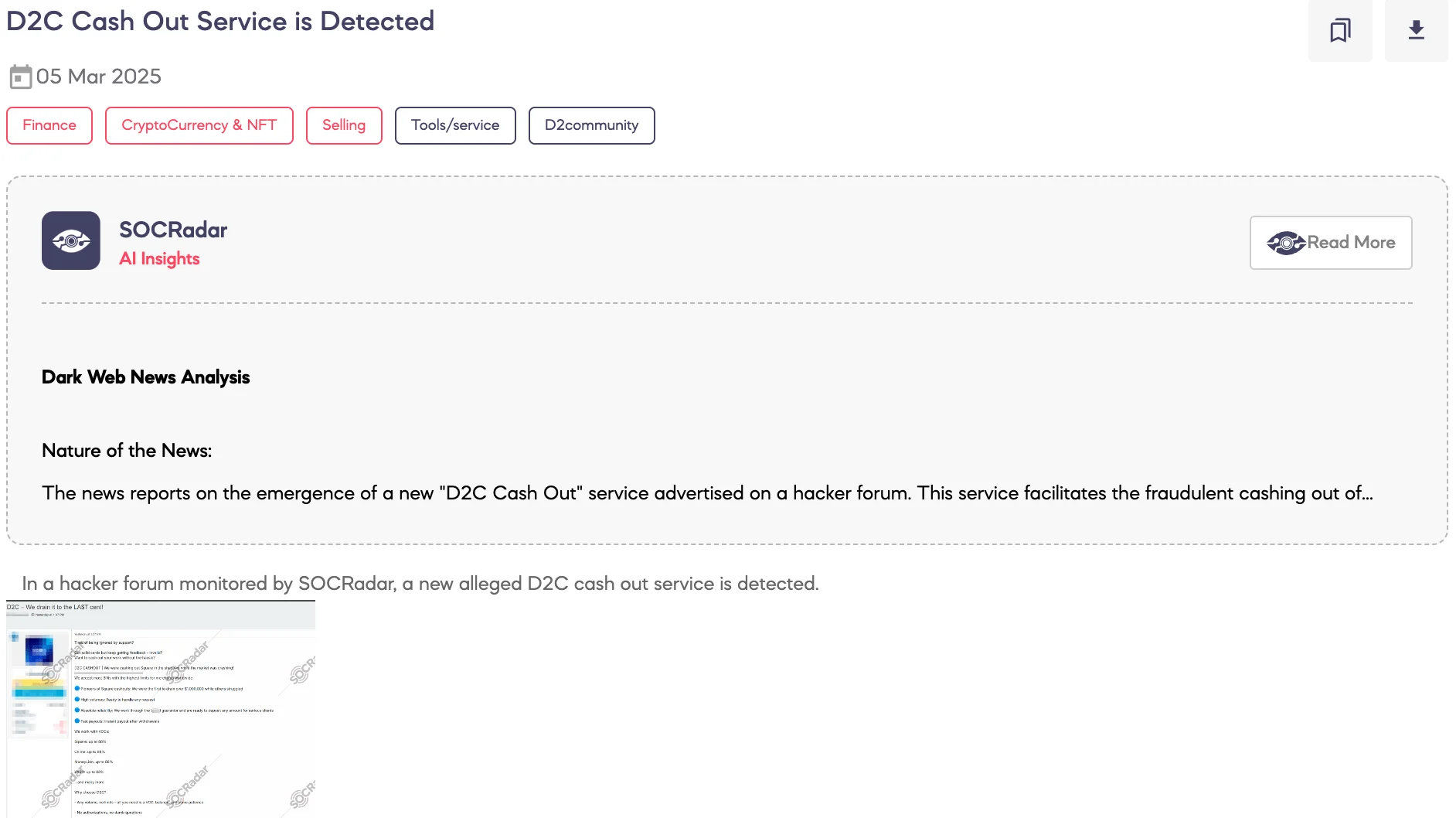
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be offering a cash-out service called D2C. According to the threat actor’s statements, the service specializes in exploiting financial platforms such as Square, Chime, MoneyLion, and VARO to facilitate unauthorized withdrawals. The threat actor claims to have previously exfiltrated over $1,000,000 through Square transactions while maintaining a high-volume operation with instant payouts.
The service allegedly operates with pre-configured POS terminals, multiple merchant IDs, and a proprietary payment processing gateway to disguise fraudulent transactions as legitimate bank payments. The actor states that virtual credit cards (VCCs) are accepted, with a payout rate of up to 88%. Contact is facilitated via Telegram, and the service claims to be available 24/7.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.


































