
New DDoS Service, Windows 0-Day Exploit, and US Credit Cards Sale
Discover the latest findings by SOCRadar’s Dark Web Team. A new DDoS service promises extended attacks, challenging defenses from Cloudflare and Akamai. Meanwhile, unauthorized network access sales target companies across the US, UK, and Europe. A database of Latin American personnel recruitment emerges, and an alarming request seeks American doctors’ data. Additionally, a high-stakes sale offers a potent 0-day exploit for Microsoft Windows, while a trove of US credit cards hits the market.
Receive a Free Dark Web Report for Your Organization:
A New DDoS Service is Detected
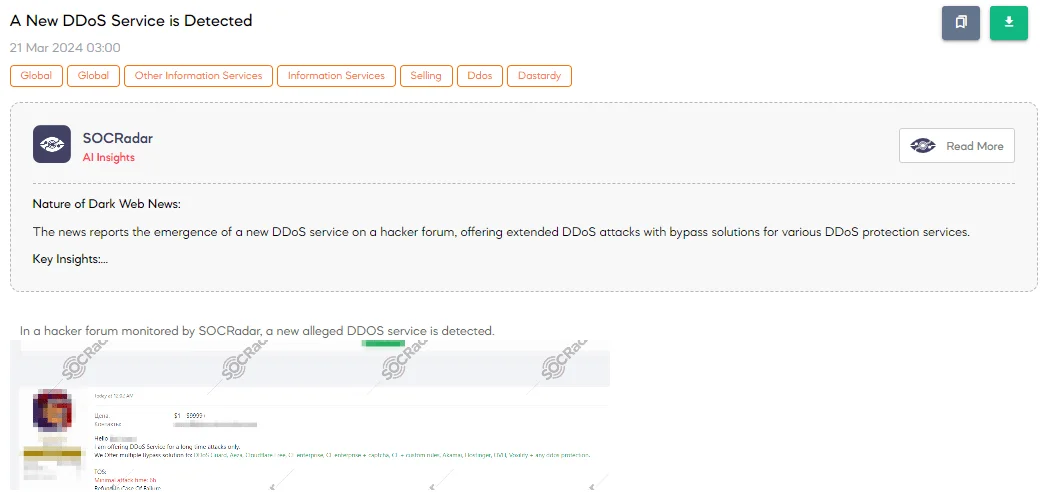
A New DDoS Service is Detected
The SOCRadar Dark Web Team identified a hacker forum post advertising a new DDoS (Distributed Denial-of-Service) service aimed at long-duration attacks. The service claims to bypass various DDoS protection mechanisms from companies like Cloudflare, Akamai, and OVH, among others. Offering features include a minimum attack time of 6 hours, refunds for unsuccessful attacks, escrow payment options, and a free 5-10 minute trial.
Unauthorized Network Accesses Sale is Detected for Multiple Companies
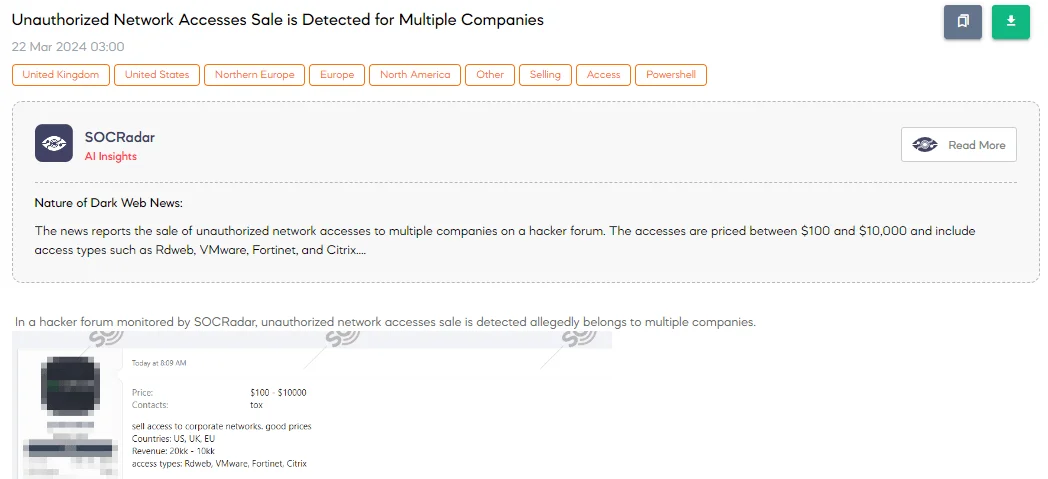
Unauthorized Network Accesses Sale is Detected for Multiple Companies
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to sell unauthorized access to multiple companies across the US, UK, and EU networks. The companies targeted reportedly have revenues ranging from $20 million to $10 billion. The threat actor offers access to various network types, including Rdweb, VMware, Fortinet, and Citrix, with prices between $100 and $10,000.
Database of Recruitment of Personnel in Latin America and Mexico is on Sale
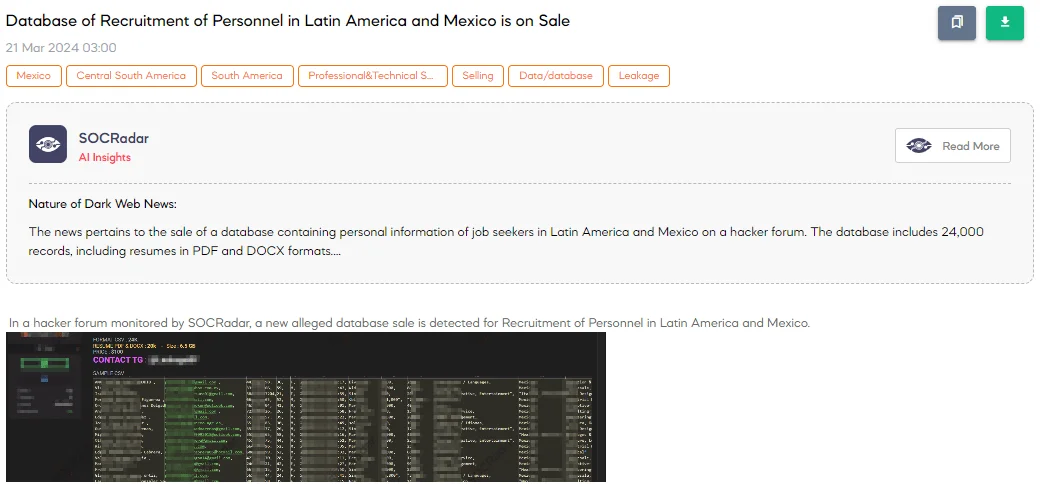
Database of Recruitment of Personnel in Latin America and Mexico is on Sale
The SOCRadar Dark Web Team has detected a post on a hacker forum advertising the sale of a database containing recruitment information for personnel in Latin America and Mexico. The database includes 24,000 records, dumped on March 20, 2024, and features CSV formats and 20,000 resumes in PDF and DOCX formats, amounting to 6.5 GB of data, all priced at $100.
Data Purchasing Announcement is Detected for American Doctors
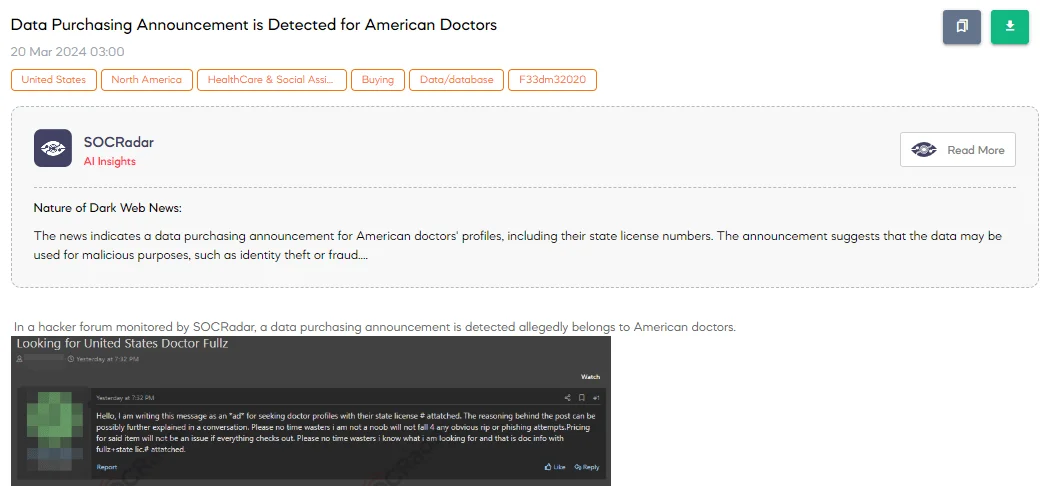
Data Purchasing Announcement is Detected for American Doctors
The SOCRadar Dark Web Team detected a post on a hacker forum that a threat actor was seeking to purchase the personal and professional data of American doctors, specifically targeting profiles that include state license numbers. This request highlights a clear intent to acquire sensitive information for potentially malicious purposes, emphasizing the demand for comprehensive data sets (fullz) attached with state license numbers.
0-day Exploit of Microsoft Windows is on Sale
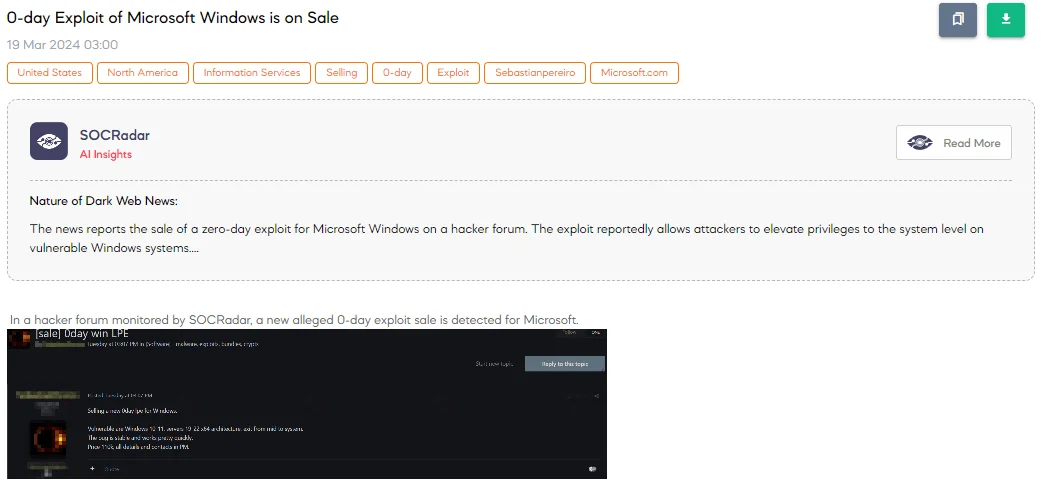
0-day Exploit of Microsoft Windows is on Sale
The SOCRadar Dark Web Team discovered a hacker forum post advertising the sale of a new 0-day exploit targeting Microsoft Windows, including versions 10 and 11 and Server versions 2019 to 2022, all on x64 architecture. Described as a Local Privilege Escalation (LPE) bug, it allows attackers to elevate privileges from mid-level to system-level quickly and reliably. The asking price for this exploit is $110,000.
97K Credit Cards Belonging to the United States are on Sale
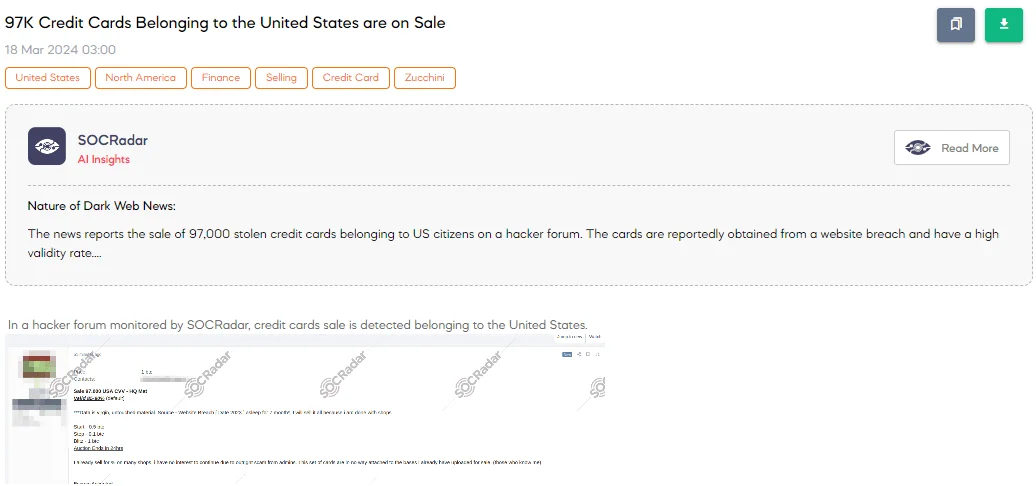
97K Credit Cards Belonging to the United States are on Sale
The SOCRadar Dark Web Team detected a post on a hacker forum advertising the sale of 97,000 credit cards from the United States, with a price starting at 0.5 Bitcoin and a “Blitz” buyout option of 1 Bitcoin. The sale is set to end within 24 hours. The threat actor claims this data, sourced from a 2023 website breach that remained undetected for seven months, is fresh and previously unexploited. They indicate a validity rate of 85-90% for the cards.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.



































