
New Remote Access Trojan (RAT) named Borat on the Darknet Markets
Threat actors are developing more advanced attack techniques every day. They even help non-technical attackers by publishing toolkits. With these toolkits, anyone can easily access victims’ systems remotely, perform DDoS attacks or deploy ransomware.
Borat, the Remote Access Trojan (RAT), recently discovered by cybersecurity experts, is one of these all-in-one kits. Borat provides operators with full access and remote control of infected systems. It is stated that Borat RAT has functions that can be easily used even by users without technical qualifications. There is no clarity on whether it is currently distributed free of charge or offered for sale.
What are the Features of Borat RAT?
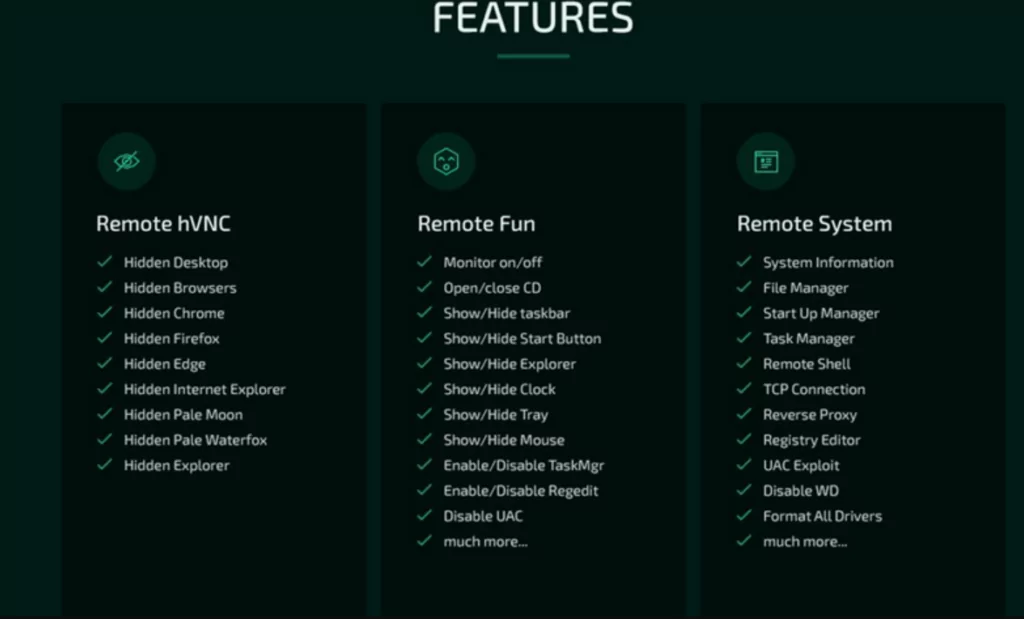
Through Borat, threat actors can gain full control of victim’s mouse and keyboard and also access files and network points. Borat’s comes as a package with a builder, malware modules, and server certificate and provides the following features:
|
Keylogging |
Monitoring and storing victim’s keystrokes with “keylogger.exe” module. |
|
Ransomware |
Installing ransomware on the victim’s system and generating a ransom note. |
|
Redirect garbage traffic to the target server using the resources of the compromised machine. |
|
|
Audio recording |
Recording audio by accessing the victim’s microphone and storing it in a “.wav” file. |
|
Webcam recording |
Accessing victim’s webcam and recording video. |
|
Remote desktop |
Starting a remote desktop for performing file operations, using devices, executing codes, launching applications, etc. |
|
Reverse proxy |
Hiding the identity of the remote access user. |
|
Device information |
Gaining basic system information. |
|
Process hollowing |
Avoiding detection by injecting malware code into legitimate processes. |
|
Stealing credentials stored in Chromium-based web browsers. |
|
|
Discord token stealing |
Stealing victim’s Discord tokens. |
Cybersecurity experts underline that Borat RAT is a powerful threat that can perform many malicious activities on a device.
Such tools can be distributed through “.exe” files or files that look like cracks for games and applications. Experts recommend not to download anything from torrent sites or unreliable sites.
How to Protect Yourself from Remote Access Trojans like Borat?
Using RATs, threat actors can access sensitive data and cause financial damage to both individuals and organizations. A multi-layered security approach and awareness are needed as RATs like Borat hide in legitimate actions.
You can take the following precautions to protect against remote desktops:
- Use strong passwords.
- Update all your software (including the operating system) regularly.
- Make adjustments to your firewall to limit access.
- Enable network-level authentication.
- Limit users who can log in using a remote desktop.
- Use two-factor authentication.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.


































