Newly Emerged Ransom Threats: Big Head and Rancoz
July is the official Ransomware Awareness Month and it serves as a poignant reminder of the ever-growing danger presented by ransomware attacks. In line with this dedicated month, this blog post focuses on two newly discovered ransomware strains: Big Head and Rancoz.
By examining the unique characteristics and potential impact of these strains, our goal is to raise awareness and emphasize the critical need for robust defenses and proactive cybersecurity measures.
For additional suggestions and information, we recommend checking out our blog post titled “How to Detect & Prevent Ransomware Attacks (2023 CISO Edition).”
Big Head Ransomware Distributed via Malvertising Poses as Windows Updates
Researchers have analyzed a newly discovered ransomware strain called “Big Head.” Big Head is currently spreading via malvertising campaigns, in which unsuspecting users are duped into installing fraudulent Windows updates and Microsoft Word installers.
Two samples had been analyzed by Fortinet; researchers from Trend Micro examined these two and an additional one they sampled during their investigation. The first sample utilizes a backdoor as part of its infection process, the second a trojan spy and an information stealer, and the third a file infector.
The findings also indicate that all three samples originate from a single ransomware operator.
Infection Chain of Big Head Ransomware
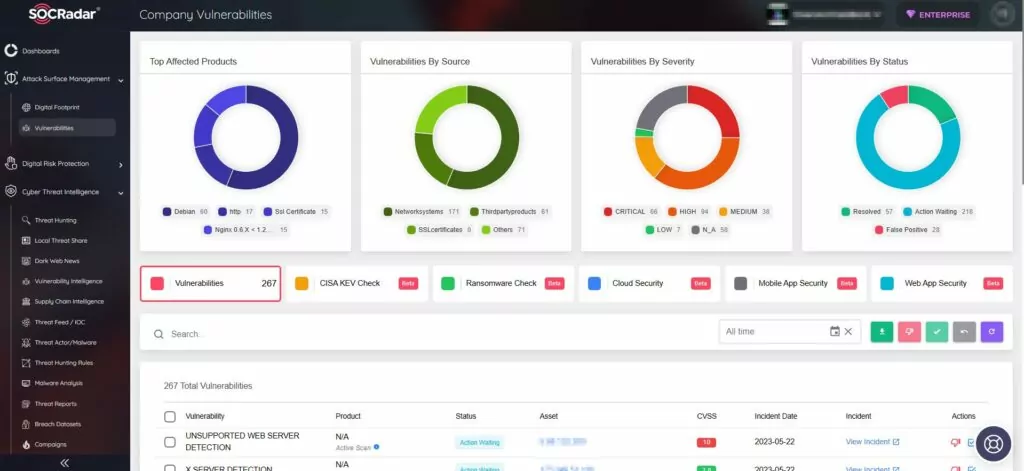
The Big Head ransomware infiltrates systems with three AES-encrypted files. One file spreads the malware, another communicates with a Telegram bot, and the third file encrypts data and displays a fake Windows update.
The ransomware employs tactics like creating a registry autorun key, overwriting files, modifying system attributes, and terminating certain processes after execution, and each victim receives a unique ID.
The ransomware deletes shadow copies and appends a “.poop” extension to encrypted files to hinder system recovery. Critical directories such as Windows, Recycle Bin, Program Files, Temp, Program Data, Microsoft, and App Data are excluded from encryption to maintain system functionality.
While encrypting, Big Head terminates Task Manager (taskmgr), SQL-related processes, and other processes to prevent interference. Throughout encryption, the ransomware masquerades as a legitimate Windows update, displaying a deceptive screen to hide its malicious acts. After encryption, it drops a ransom note and alters the victim’s wallpaper.
Big Head Avoids Encrypting Systems in CIS Countries
Investigation revealed that the Big Head ransomware checks for virtual environments and also the system language. The ransomware initiates encryption only if the language is not that of the Commonwealth of Independent States (CIS); according to Trend Micro, if the user’s system language matches the Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz, Armenian, Georgian, Tatar, or Uzbek country codes, the malware will terminate itself.
Variants of Big Head Ransomware: Data Theft and File Infection Features
Trend Micro also analyzed two other variants of Big Head, noting some differences compared to the standard version.
The second variant combines ransomware capabilities with data theft features, collecting sensitive information from the victim’s system, including browsing history, directories, drivers, running processes, product keys, active networks, and capturing screenshots.
The third variant incorporates a file infector named “Neshta,” which inserts malicious code into executables on the compromised system. The purpose of this behavior remains unclear, but Trend Micro’s analysts say it could be an attempt to evade detection mechanisms relying on signature-based methods.
Big Head Ransomware: Simple yet Evolving Threat
Big Head is not considered a sophisticated ransomware strain, its encryption methods and evasion techniques are relatively straightforward and easy to detect.
It appears to target people who can be deceived by simple tricks, such as fake Windows updates or lack an understanding of necessary cybersecurity precautions.
Multiple variants indicate that Big Head’s creators are continuously developing and refining the malware, experimenting with different approaches to determine the most effective methods.
Find the latest updates about Big Head Ransomware on SOCRadar platform.
Another Novel Ransomware: Rancoz
The Rancoz ransomware emerged a few months ago and has gained attention due to its recent victims, with the most recent data leak on TOR occurring in mid-June.
According to the information available on their TOR site, the first recorded Rancoz attack took place in November 2022.
The group behind Rancoz follows a similar pattern as other ransomware groups, encrypting files on compromised computers, stealing data, and extorting money from their victims. As of now, there is no evidence to suggest that Rancoz is widespread.
After the Rancoz ransomware is launched, it searches through and encrypts files on the computer’s local drives. The encrypted files are marked with a file extension of “.rec_rans,” and a ransom note called “HOW_TO_RECOVERY_FILES.txt” is placed in the compromised system.
The ransom note contains the URL of the Rancoz data leak site and the attacker’s contact email address.
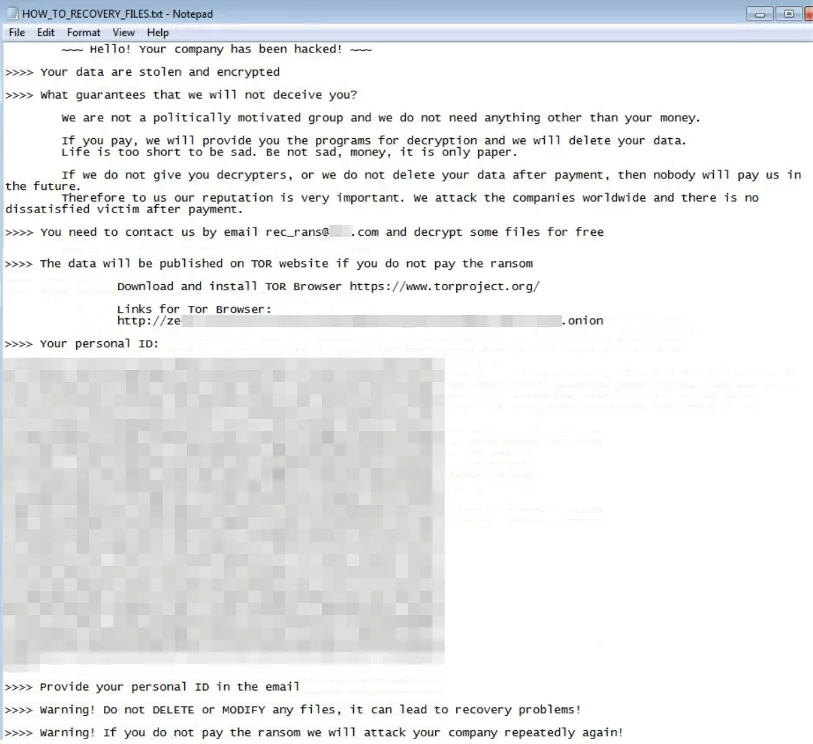
The ransomware also changes the desktop wallpaper to display the ransom note, further urging the victims to comply.
Furthermore, the ransomware deletes shadow copies and alters registry keys, intentionally complicating the process of recovering files and establishing remote server connections for the victims.
- Command to delete shadow copies: “/c vssadmin.exe Delete Shadows /All /Quiet”
- Command to delete the registry key: “HKEY_CURRENT_USERSoftwareMicrosoftTerminal Server ClientDefault”
- Command to reset the registry key: “HKEY_CURRENT_USERSoftwareMicrosoftTerminal Server ClientServers”
Deleting these registry keys can prevent victims from connecting to remote backup servers for file recovery.
Exposing Victims and Ongoing Distribution
At the time of writing, Rancoz had three known victims from the United States and Canada listed on their data leak site, where the threat actor exposed a substantial amount of stolen data.
It’s important to note that some ransomware groups remove company listings from leak sites after receiving the ransom, so there may be additional unlisted victims.
Rancoz ransomware samples have been submitted to a public file scanning service from multiple countries, including the United States, India, France, and Lithuania, between May and June. This suggests an ongoing distribution of the same Rancoz ransomware sample.
Potential Connections Between Rancoz and Buddy Ransomware
FortiGuard Labs has identified a potential connection between Rancoz and the Buddy ransomware based on similarities in their ransom notes, desktop wallpaper replacement, and compilation dates. Another ransomware sample may also be related, although it differs in certain aspects, such as the absence of a TOR site link in the ransom note.
These similarities are not uncommon, as many ransomware variants are built upon existing code. Therefore, it is likely that the same developer is responsible for creating Rancoz and other related ransomware variants.
Find Indicators of Compromise on SOCRadar
SOCRadar continuously monitors threat actors and malware, offering comprehensive insights encompassing their latest mentions, activities, and indicators of compromise (IOCs). Leveraging the Threat Actor Tracking feature of SOCRadar, users can access this information.
By harnessing the power of SOCRadar, organizations can obtain actionable intelligence and define use cases more effectively to facilitate the detection and prevention of malicious activities, bolstering their cybersecurity defenses.
Furthermore, SOCRadar’s External Attack Surface Management (EASM) functionality provides timely alerts regarding potential threats to digital assets, ensuring your organization is not exposed to attacks.