
Notorious Ransomware Gangs on Attack Spree
Powered by DarkMirror™
In the dark web summary of the previous week, we talked about the victims that the Clop ransomware group has repeatedly revealed. Probably they also inspired other threat actors because we saw various ransomware attack announcements last week.
LockBit, the most active gang in recent years, targeted the tax services of the Republic of Korea, while the rising ransomware group Play announced that it attacked BMW. The surprise was that a new player had entered the threat landscape. This threat actor, named Money Message, targeted Biman Bangladesh Airlines.
Find out if your data has been exposed.
The New Ransomware Victim of Play: BMW France

On March 28, the SOCRadar dark web team detected that BMW France was added to the list of victims by the Play ransomware gang. The threat actor claims to have intercepted private and personal data, customer documents, contracts, financial information, etc.
The New Ransomware Victim of Money Message: Biman Bangladesh Airlines
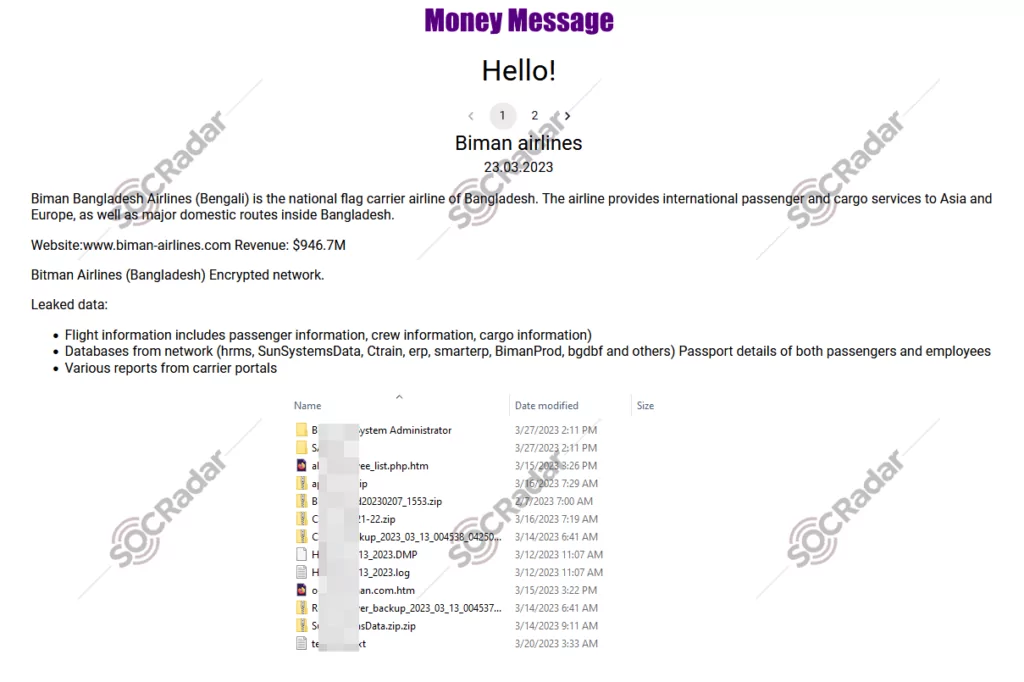
On March 30, SOCRadar detected a post about Biman Bangladesh Airlines being targeted by a new ransomware group, Money Message. The attackers claim to have accessed sensitive data, including flight information such as passenger, crew, and cargo details, databases on the network, passport details of passengers and employees, and various reports from carrier portals. Researchers also claimed that the Money Message ransomware group demanded million-dollar ransoms from their victims to prevent the release of the stolen data and provide them with a decryptor.
CVE-2022-40684 Exploit Sale is Detected for Fortinet VPN
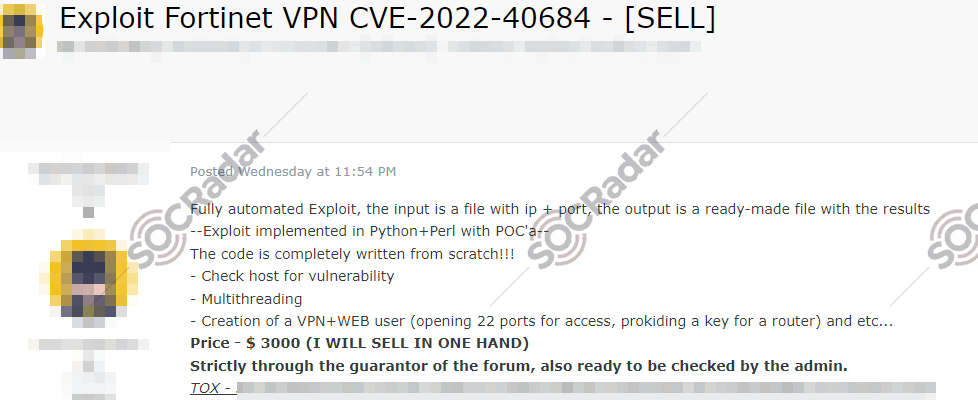
SOCRadar detected a new post that the threat actor claims developed a fully automated exploit tool for CVE-2022-40684 (CVSS score: 9.6) in Python and Perl that checks for vulnerabilities on a host and performs multi-threading. The threat actor claims that the tool can create a VPN and web user, open ports for access, and provide a key for a router. The threat actor also claims that the code is original and written from scratch. The price of the tool is $3000. The communication method provided is a Tox ID.
The New Ransomware Victim of Lockbit 3.0: Korea National Tax Service
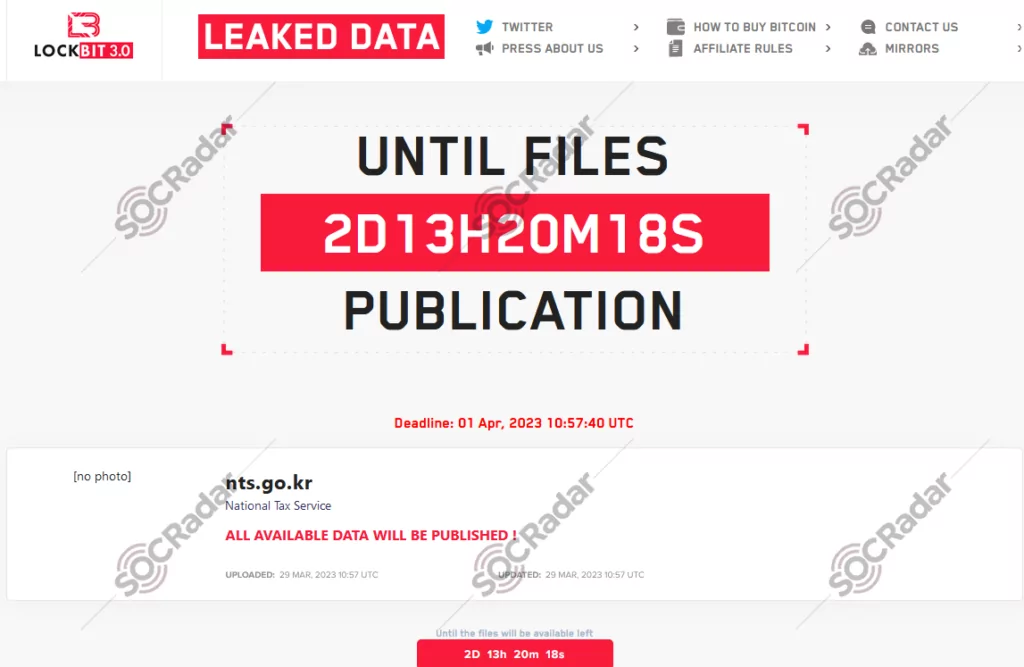
On March 29, a SOCRadar researcher detected a post claiming that LockBit ransomware successfully breached the South Korean National Tax Service’s data. LockBit remains highly active as a ransomware group with a reputation for targeting various organizations worldwide.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































